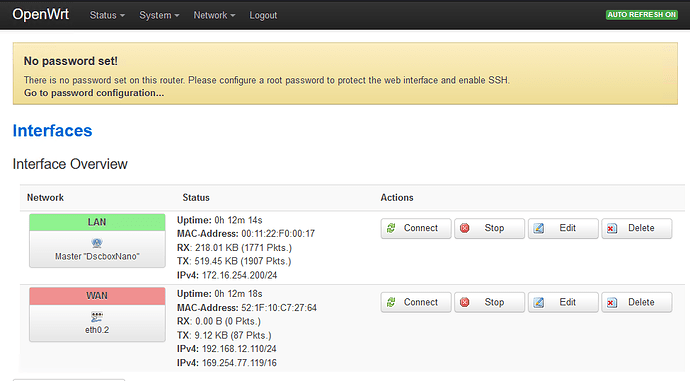
Hello, dear developpers,
I am trying to recreate a firmware on a 2015's router model we want to sell (model is :Ralink MT7620a V22SG)
We don't have the original source files so, I used an imagebuilder version close to what is originally installed.
The firmware is copied without apparent errors via sysupgrade, I manage to get the LAN working and to use the lucy application.
I am getting an issue with the WAN interface that seems to be running but, when doing "ping 8.8.8.8", I get 100% packet loss, and the connection doesn't seems to work.
I tried to modify the configuration files many times but I still have the issue. Thank you by advance, if someone have an idea that could clarify my understanding of the problem.
Configuration files, drivers are the same as the original one, so, I can't figure out what is wrong with the compilation.
Best Regards.
Here are some complementary informations :
//********************* SYSTEM BOARD ************************************************
root@OpenWrt:/etc# ubus call system board
- Original firmware :
{
"kernel": "3.18.20",
"hostname": "OpenWrt",
"system": "Ralink MT7620A ver:2 eco:6",
"model": "Ralink MT7620a V22SG",
"release": {
"distribution": "OpenWrt",
"version": "Chaos Calmer",
"revision": "r46822",
"codename": "chaos_calmer",
"target": "ramips\/mt7620",
"description": "OpenWrt Chaos Calmer 15.05"
}
}
- Replacement firmware:
{
"kernel": "3.18.109",
"hostname": "OpenWrt",
"system": "MediaTek MT7620A ver:2 eco:6",
"model": "Ralink MT7620a V22SG High Power evaluation board",
"release": {
"distribution": "OpenWrt",
"version": "Chaos Calmer",
"revision": "r49632",
"codename": "chaos_calmer",
"target": "ramips\/mt7620",
"description": "OpenWrt Chaos Calmer 15.05.1"
}
}
//********************* DIAGNOSTICS ************************************************
root@OpenWrt:/# uci export network; uci export dhcp; uci export firewall; \
> head -n -0 /etc/firewall.user; \
> iptables-save -c; ip -4 addr ; ip -4 ro li tab all ; ip -4 ru; \
> ls -l /etc/resolv.* /tmp/resolv.* /tmp/resolv.*/* ; head -n -0 /etc/resolv.*
/tmp/resolv.* /tmp/resolv.*/*
{
"kernel": "3.18.109",
"hostname": "OpenWrt",
"system": "MediaTek MT7620A ver:2 eco:6",
"model": "Ralink MT7620a V22SG High Power evaluation board",
"release": {
"distribution": "OpenWrt",
"version": "Chaos Calmer",
"revision": "r49632",
"codename": "chaos_calmer",
"target": "ramips\/mt7620",
"description": "OpenWrt Chaos Calmer 15.05.1"
}
}
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd17:975b:bd8c::/48'
config interface 'lan'
option macaddr '00:11:22:F0:00:17'
option proto 'static'
option ipaddr '172.16.254.200'
option netmask '255.255.255.0'
option force_link '1'
config interface 'wan'
option macaddr '52:1F:10:C7:27:64'
option proto 'static'
option ipaddr '192.168.12.110'
option netmask '255.255.255.0'
option gateway '192.168.12.254'
option ifname 'eth0.2'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 3 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6t'
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option start '257'
option limit '2557'
option dhcpv6 'server'
option ra 'server'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fe80::/10'
option src_port '547'
option dest_ip 'fe80::/10'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config rule
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
# Generated by iptables-save v1.4.21 on Thu Jun 2 10:08:49 2022
*nat
:PREROUTING ACCEPT [227:31411]
:INPUT ACCEPT [116:7933]
:OUTPUT ACCEPT [241:16665]
:POSTROUTING ACCEPT [241:16665]
:delegate_postrouting - [0:0]
:delegate_prerouting - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[227:31411] -A PREROUTING -j delegate_prerouting
[264:17861] -A POSTROUTING -j delegate_postrouting
[264:17861] -A delegate_postrouting -m comment --comment "user chain for postrouting" -j postrouting_rule
[1:345] -A delegate_postrouting -o wlan0 -j zone_lan_postrouting
[23:1196] -A delegate_postrouting -o eth0.2 -j zone_wan_postrouting
[227:31411] -A delegate_prerouting -m comment --comment "user chain for prerouting" -j prerouting_rule
[227:31411] -A delegate_prerouting -i wlan0 -j zone_lan_prerouting
[0:0] -A delegate_prerouting -i eth0.2 -j zone_wan_prerouting
[1:345] -A zone_lan_postrouting -m comment --comment "user chain for postrouting" -j postrouting_lan_rule
[227:31411] -A zone_lan_prerouting -m comment --comment "user chain for prerouting" -j prerouting_lan_rule
[23:1196] -A zone_wan_postrouting -m comment --comment "user chain for postrouting" -j postrouting_wan_rule
[23:1196] -A zone_wan_postrouting -j MASQUERADE
[0:0] -A zone_wan_prerouting -m comment --comment "user chain for prerouting" -j prerouting_wan_rule
COMMIT
# Completed on Thu Jun 2 10:08:49 2022
# Generated by iptables-save v1.4.21 on Thu Jun 2 10:08:49 2022
*raw
:PREROUTING ACCEPT [1381:125309]
:OUTPUT ACCEPT [1320:264619]
:delegate_notrack - [0:0]
[1381:125309] -A PREROUTING -j delegate_notrack
COMMIT
# Completed on Thu Jun 2 10:08:49 2022
# Generated by iptables-save v1.4.21 on Thu Jun 2 10:08:49 2022
*mangle
:PREROUTING ACCEPT [1381:125309]
:INPUT ACCEPT [1148:95487]
:FORWARD ACCEPT [145:7540]
:OUTPUT ACCEPT [1320:264619]
:POSTROUTING ACCEPT [1465:272159]
:fwmark - [0:0]
:mssfix - [0:0]
[1381:125309] -A PREROUTING -j fwmark
[145:7540] -A FORWARD -j mssfix
[145:7540] -A mssfix -o eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "wan (mtu_fix)" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Thu Jun 2 10:08:49 2022
# Generated by iptables-save v1.4.21 on Thu Jun 2 10:08:49 2022
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:delegate_forward - [0:0]
:delegate_input - [0:0]
:delegate_output - [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[1148:95487] -A INPUT -j delegate_input
[145:7540] -A FORWARD -j delegate_forward
[1320:264619] -A OUTPUT -j delegate_output
[145:7540] -A delegate_forward -m comment --comment "user chain for forwarding" -j forwarding_rule
[0:0] -A delegate_forward -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
[145:7540] -A delegate_forward -i wlan0 -j zone_lan_forward
[0:0] -A delegate_forward -i eth0.2 -j zone_wan_forward
[0:0] -A delegate_forward -j reject
[480:32640] -A delegate_input -i lo -j ACCEPT
[668:62847] -A delegate_input -m comment --comment "user chain for input" -j input_rule
[526:52038] -A delegate_input -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
[18:936] -A delegate_input -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -j syn_flood
[142:10809] -A delegate_input -i wlan0 -j zone_lan_input
[0:0] -A delegate_input -i eth0.2 -j zone_wan_input
[600:42240] -A delegate_output -o lo -j ACCEPT
[720:222379] -A delegate_output -m comment --comment "user chain for output" -j output_rule
[717:221344] -A delegate_output -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
[3:1035] -A delegate_output -o wlan0 -j zone_lan_output
[0:0] -A delegate_output -o eth0.2 -j zone_wan_output
[0:0] -A reject -p tcp -j REJECT --reject-with tcp-reset
[0:0] -A reject -j REJECT --reject-with icmp-port-unreachable
[18:936] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -j RETURN
[0:0] -A syn_flood -j DROP
[3:1035] -A zone_lan_dest_ACCEPT -o wlan0 -j ACCEPT
[145:7540] -A zone_lan_forward -m comment --comment "user chain for forwarding" -j forwarding_lan_rule
[145:7540] -A zone_lan_forward -m comment --comment "forwarding lan -> wan" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -j zone_lan_dest_ACCEPT
[142:10809] -A zone_lan_input -m comment --comment "user chain for input" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "Accept port redirections" -j ACCEPT
[142:10809] -A zone_lan_input -j zone_lan_src_ACCEPT
[3:1035] -A zone_lan_output -m comment --comment "user chain for output" -j output_lan_rule
[3:1035] -A zone_lan_output -j zone_lan_dest_ACCEPT
[142:10809] -A zone_lan_src_ACCEPT -i wlan0 -j ACCEPT
[145:7540] -A zone_wan_dest_ACCEPT -o eth0.2 -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o eth0.2 -j reject
[0:0] -A zone_wan_forward -m comment --comment "user chain for forwarding" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "@rule[7]" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "@rule[8]" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -j zone_wan_dest_REJECT
[0:0] -A zone_wan_input -m comment --comment "user chain for input" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment Allow-DHCP-Renew -j ACCEPT
[0:0] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment Allow-Ping -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment Allow-IGMP -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "Accept port redirections" -j ACCEPT
[0:0] -A zone_wan_input -j zone_wan_src_REJECT
[0:0] -A zone_wan_output -m comment --comment "user chain for output" -j output_wan_rule
[0:0] -A zone_wan_output -j zone_wan_dest_ACCEPT
[0:0] -A zone_wan_src_REJECT -i eth0.2 -j reject
COMMIT
# Completed on Thu Jun 2 10:08:49 2022
/bin/ash: ip: not found
/bin/ash: ip: not found
/bin/ash: ip: not found
ls: /tmp/resolv.*/*: No such file or directory
lrwxrwxrwx 1 root root 16 Jun 2 10:02 /etc/resolv.conf -> /tmp/resolv.conf
-rw-r--r-- 1 root root 114 Jun 2 10:03 /tmp/resolv.conf
-rw-r--r-- 1 root root 0 Jun 2 10:02 /tmp/resolv.conf.auto
==> /etc/resolv.conf <==
# Generated by dhcpcd
# /etc/resolv.conf.head can replace this line
# /etc/resolv.conf.tail can replace this line
==> /tmp/resolv.conf <==
# Generated by dhcpcd
# /etc/resolv.conf.head can replace this line
# /etc/resolv.conf.tail can replace this line
==> /tmp/resolv.conf.auto <==
head: /tmp/resolv.*/*: No such file or directory
//********************* NETWORK CONFIGURATION ************************************************
root@OpenWrt:/# ifconfig
eth0 Link encap:Ethernet HWaddr EE:2A:D4:5D:9A:ED
inet addr:169.254.190.124 Bcast:169.254.255.255 Mask:255.255.0.0
inet6 addr: fe80::3d71:79b5:5b4f:11e/64 Scope:Link
inet6 addr: fe80::ec2a:d4ff:fe5d:9aed/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:106 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:12943 (12.6 KiB)
Interrupt:5
eth0.2 Link encap:Ethernet HWaddr 52:1F:10:C7:27:64
inet addr:192.168.12.110 Bcast:192.168.12.255 Mask:255.255.255.0
inet6 addr: fe80::501f:10ff:fec7:2764/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:80 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:0 (0.0 B) TX bytes:6484 (6.3 KiB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:384 errors:0 dropped:0 overruns:0 frame:0
TX packets:384 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:26112 (25.5 KiB) TX bytes:26112 (25.5 KiB)
wlan0 Link encap:Ethernet HWaddr 00:11:22:F0:00:17
inet addr:172.16.254.200 Bcast:172.16.254.255 Mask:255.255.255.0
inet6 addr: fe80::211:22ff:fef0:17/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:982 errors:0 dropped:0 overruns:0 frame:0
TX packets:1061 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:127441 (124.4 KiB) TX bytes:300943 (293.8 KiB)