Hi, I would also like to see OpenWRT running on the TL-ER7206. It's one of the few devices with an SFP port and I also don't mind that it doesn't have a wifi interface. Is there anything I can help with?
Any update on ER7206 using OpenWrt?
Also interested in OpenWrt for the ER7206.
As per the little brother of the ER7206, the ER605 and its recent success with being included as limited support, I would be keen to see the ER7206 getting similar treatment.
I have one of each of the 7206v2 and 605v2. I can see some good work has already happened on the 7206, but seems to have stalled? Looking at the 605 progress, it seems that much of the problem was related to a strange layout of MTD partitions used by the stock firmware. @chill1Penguin assisted with some code to reformat into a layout that was friendlier, then load openwrt-initramfs-compact.bin, then allow a sysupgrade 23.05.3. This works well, though reverting to stock requires restore from a full MTD backup. Is it possible some of these techniques could be used to provide support for this model too?
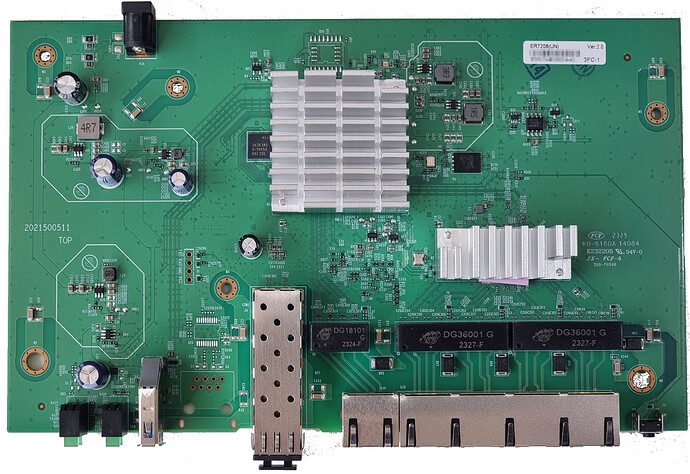
Can we add a device wiki page for this? Here are some images of it to get things started.
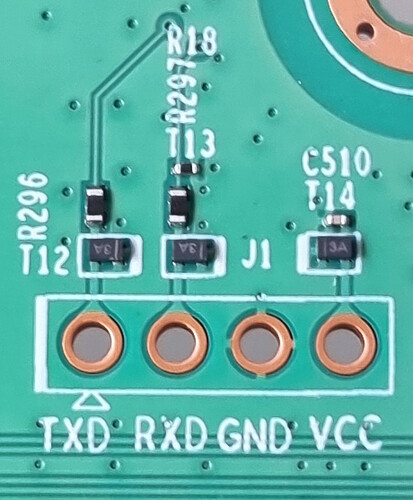
UART measured at 3.3v. (Looks like no pads required to solder bridges to make it work like the 605 had). Should be very easy to connect.
I can see folks have already contributed things from the v1 of this model, but mine is a v2. Is there anything I can upload here that would help?
Getting root on the ER7206 via SSH.
Following on from @richh 's discovery here, which worked on 605, I wanted to test it on the 7206. My first attempts failed, but I was running on current firmware (2.1.2 from memory). I downgraded to the oldest I could find which was 2.0.1 Build 20230705 Rel.75930. Now root access via SSH on a stock ER7206 works. There is also a very helpful page here that uses the same calcs linked above that may be easier.
One thing I noticed is that this is not the same shell that was seen on the 605 (showed the OpenWRT Barrier Breaker splash screen in early versions until they removed the splash in later versions). On the ER7206 it seems to be a different shell altogether. It looks like this:
login as: root
root@192.168.0.1's password:
>help
Commands available:
help Show available commands
exit Exit from current mode
enable Turn on privileged commands
disable Turn off privileged commands
>
using enable, a deeper shell is possible, however this still seems to be limited:
#help
Commands available:
help Show available commands
exit Exit from current mode
enable Turn on privileged commands
disable Turn off privileged commands
configure Enter configuration mode
show system-info Display system information.
show history Display command history.
show interface switchport Display interface switch port information.
show interface vlan Display interface VLAN information.
show arp Display ARP entry information.
show ikev1 policy Display ikev1 module entry information.
show ikev2 policy Display ikev2 module entry information.
show transform-set Display transform-set module entry information.
show crypto map Display map module entry information.
show crypto ipsec sa Display the SA information of the established IPSec.
show all ikev1 policy Display all ikev1 module entry information.
show all ikev2 policy Display all ikev2 module entry information.
show all transform-set Display all transform-set module entry information.
show all crypto map Display all map module entry information.
show ip rip Display RIP interface information.
show ip ospf Display ospf information.
show ip ospf database Display the database information of OSPF.
show ip ospf neighbor Display OSPF neighbor table information.
show ip ospf interface Display the interface information of OSPF.
show ip route static Display entry information of static IP route.
show ip http configuration Display http configuration.
show network Display OSPF network information.
show nat virtual-server Display the entry information of NAT virtual-server.
show nat one-to-one Display the entry information of one-to-one NAT.
show nat alg Display the entry information of NAT ALG.
show snmp-server Display SNMP server configuration.
show ssh configuration Display SSH configuration information.
ping Ping ip address.
tracert traceroute ip address.
clear history Clear previously run commands.
reboot Reboot device.
I had been hoping for the sort of shell access I'd got from the 605, but it seems different here. Anything useful I can do from here?
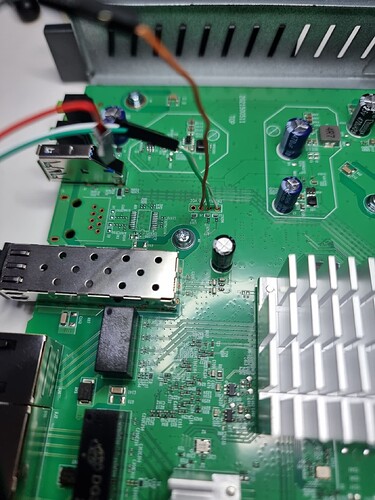
Got UART hooked up - solderless ![]() .
.
I am assuming that @bdherouville had already done much the same , so I don't want to retread any ground, but was hoping I could share in case this can assist any others, or can help to get this supported.
Is the serial dump since power-on useful at all to share here? Otherwise, is there anything useful I should be looking for that I can check and post?
The partition on the MTD may be the same or similar to the ER605.
[ 0.936350] 19 fixed-partitions partitions found on MTD device nmbm_spim_nand
[ 0.943483] Creating 19 MTD partitions on "nmbm_spim_nand":
[ 0.949050] 0x000000000000-0x000000100000 : "BL2"
[ 0.954383] 0x000000100000-0x000000180000 : "u-boot-env"
[ 0.960230] 0x000000180000-0x000000380000 : "Factory"
[ 0.965801] 0x000000380000-0x000000580000 : "FIP"
[ 0.971033] 0x000000580000-0x000002880000 : "ubi"
[ 0.976346] 0x000002880000-0x000004b80000 : "ubi.b"
[ 0.981844] 0x000004b80000-0x000006980000 : "database"
[ 0.987560] 0x000006980000-0x0000069a0000 : "support-list"
[ 0.993571] 0x0000069a0000-0x0000073a0000 : "user-config"
[ 0.999525] 0x0000073a0000-0x0000073c0000 : "partition-table"
[ 1.005826] 0x0000073c0000-0x0000073e0000 : "device-info"
[ 1.011783] 0x0000073e0000-0x000007400000 : "device-info.b"
[ 1.017904] 0x000007400000-0x000007420000 : "tddp"
[ 1.023235] 0x000007420000-0x000007440000 : "tddp.b"
[ 1.028820] 0x000007440000-0x000007640000 : "extra-para-ubi"
[ 1.035028] 0x000007640000-0x000007660000 : "firmware-info"
[ 1.041191] 0x000007660000-0x000007680000 : "firmware-info.b"
[ 1.047506] 0x000007680000-0x000007880000 : "log"
[ 1.052790] 0x000007880000-0x000007a80000 : "log.b"
Thanks,
I can try some tests if someone can help me.
Regards
I was able to get full root access through the ssh by following the instructions here: https://github.com/chill1Penguin/er605v2_openwrt_install/, in the install instructions.
Just type enable and then debug. The password is generated by the same generator for the 605.
My ER7206 is on firmware 1.4.1 Build 20240117 Rel.57421 and the password that worked was on the "v2.1.2 and below:" field. Got the MAC address by running 'show system-info' in the limited shell.
My dumps :
Octeon evb7000_sff(ram)# env print
autoload=n
baudrate=115200
boardname=evb7000_sff
bootcmd=ubi readvol 0x82200000 bootloader.b;go 0x82200000
bootdelay=1
bootli=bootoctlinux $loadaddr coremask=0xffff numcores=2 rootfstype=squashfs,jffs2 noinitrd console=ttyS0,115200 board=OSG-PRO mtdparts=spi32766.0:2M(bootloader),8M(kernel),15M(rootfs),128K(device-info),64K(support-list),576K(firmware-info),128K(tddp),128K(log),5M(rootfs_data),32M@0x000000(firmware)
diphy=mii device mdio-octeon0;mii write 0 0 0x1940;mii write 1 0 0x1940;mii write 2 0 0x1940;mii write 3 0 0x1940;mii write 4 0 0x1940;
dram_size_mbytes=512
enphy=mii device mdio-octeon0;mii write 0 0 0x1140;mii write 1 0 0x1140;mii write 2 0 0x1140;mii write 3 0 0x1140;mii write 4 0 0x1140;
env_addr=1ddf0000
env_size=10000
eth1addr=02:4d:7a:4f:7a:01
eth2addr=02:4d:7a:4f:7a:02
ethact=octeth1
ethaddr=02:4d:7a:4f:7a:00
flash_base_addr=1dc00000
flash_size=2000000
ipaddr=192.168.0.10
loadaddr=0x20000000
mtddevname=firmware
mtddevnum=0
mtdids=nand0=octeon_nand0
mtdparts=mtdparts=octeon_nand0:126M(firmware),2M(panic-oops)
numcores=2
octeon_failsafe_mode=0
octeon_ram_mode=1
partition=nand0,0
resetenv=sf probe;sf erase 0x1f0000 0x10000
serial#=unknown
serverip=192.168.0.146
stderr=serial
stdin=serial,pci,bootcmd
stdout=serial
ver=U-Boot 2013.07 (Build time: Jun 17 2021 - 23:05:41)
Octeon evb7000_sff(ram)# mtdparts
device nand0 <octeon_nand0>, # parts = 2
#: name size offset mask_flags
0: firmware 0x07e00000 0x00000000 0
1: panic-oops 0x00200000 0x07e00000 0
active partition: nand0,0 - (firmware) 0x07e00000 @ 0x00000000
defaults:
mtdids : nor0=octeon_nor0
mtdparts: octeon_nor0:2560k(bootloader)ro,2m(kernel),3520k(cramfs),64k(environment)ro
root@ER7206:~# cat /proc/mtd
dev: size erasesize name
mtd0: 00300000 00010000 "bootloader-factory"
mtd1: 00010000 00010000 "device-info"
mtd2: 00010000 00010000 "tddp"
mtd3: 00010000 00010000 "extra-para.b"
mtd4: 00010000 00010000 "extra-para"
mtd5: 000c0000 00010000 "log"
mtd6: 07e00000 00020000 "firmware"
mtd7: 00200000 00020000 "panic-oops"
mtd8: 0003e000 0001f000 "partition-table"
mtd9: 0003e000 0001f000 "support-list"
mtd10: 0017f000 0001f000 "bootloader.b"
mtd11: 001a6993 0001f000 "kernel.b"
mtd12: 01000000 0001f000 "rootfs.b"
mtd13: 00000083 0001f000 "firmware-info.b"
mtd14: 00a0d000 0001f000 "rootfs_data.b"
mtd15: 0017f000 0001f000 "bootloader"
mtd16: 001a68f2 0001f000 "kernel"
mtd17: 01000000 0001f000 "rootfs"
mtd18: 00000083 0001f000 "firmware-info"
mtd19: 00a0d000 0001f000 "rootfs_data"
And I did a full mtd backup. I will then try to flash the er605 firmware...
And I end on this message :
Read 0 bytes from volume bootloader.b to 82200000
No size specified -> Using max size (1568768)
## Starting application at 0x82200000 ...
ERROR! CONFIG_SYS_FLASH_BASE address 0x1dc00000 does not match device tree range address 0x1f400000 for cs 0!
early_board_init():322 ...
...
argv[24]: gluebi.name=rootfs_data,rootfs_data.b
## No elf image at address 0x20000000
Octeon evb7000_sff(ram)#
The way to restore the original firmware is the following :
Connect the LAN port to a 192.168.0.0/24 network
Power while holding the reset button and wait to the ethernet ports turns on.
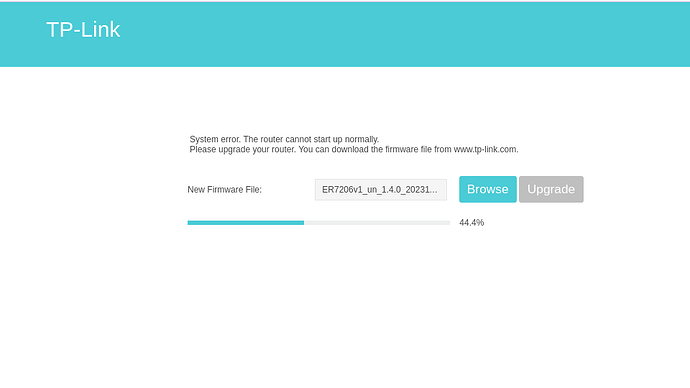
Go to 192.168.0.1 recovery page and upload a stock firmware from tp-link website.
I fixed the address and I end on a loading kernel
Octeon evb7000_sff(ram)# bootm 0x21000000
## Loading kernel from FIT Image at 21000000 ...
Using 'config-1' configuration
Trying 'kernel-1' kernel subimage
Description: MIPS OpenWrt Linux-6.6.41
Type: Kernel Image
Compression: lzma compressed
Data Start: 0x210000e4
Data Size: 5611213 Bytes = 5.4 MiB
Architecture: MIPS
OS: Linux
Load Address: 0x20000000
Entry Point: 0x20000000
Hash algo: crc32
Hash value: 9f188e13
Hash algo: sha1
Hash value: a472523e7e39a7be5b6e39736eebadc6f1772859
Verifying Hash Integrity ... crc32+ sha1+ OK
## Loading fdt from FIT Image at 21000000 ...
Using 'config-1' configuration
Trying 'fdt-1' fdt subimage
Description: MIPS OpenWrt tplink_er7206-v1 device tree blob
Type: Flat Device Tree
Compression: uncompressed
Data Start: 0x2155a0f4
Data Size: 11509 Bytes = 11.2 KiB
Architecture: MIPS
Hash algo: crc32
Hash value: 65731261
Hash algo: sha1
Hash value: 3f9fa8e56052d6f0513ca1aa7e0b120c148e05a2
Verifying Hash Integrity ... crc32+ sha1+ OK
Booting using the fdt blob at 0x2155a0f4
Uncompressing Kernel Image ... OK
Starting kernel ...
the repo i'm working on : https://github.com/bdherouville/openwrt_er7206-v1
After diging the logs I found that the ER7206 has the same CPU as Itus Router. https://openwrt.org/toh/itus_networks/itus_networks_shield : "Cavium CN7020 AAP 1.2"
But then I'm lost on how to enable this device on openwrt, it's beyond my knolwedge
Note:
ER605 v1/v2: MediaTek MT7621 (ramips target)
ER7206 v1: Cavium Octeon CN7xxx (octeon target)
ER7206 v2: MediaTek MT798x (mediatek target)
ER7206 v1 seems to have a RTL8367S switch and connected via SGMII, but it's not supported on the DSA driver (rtl8365mb) in Linux Kernel.
I try to move to Octeon folder tree but the way support is implemented gives me headaches. Any help around there ?
did u manage to get it to work?