Hi gang, first thanks for polite and helpful forums, I've enjoyed reading through as I've worked through setting up my Linksys WRT3200ACM with OpenWrt 18.06.4, and getting it connected to Mullvad VPN using Wireguard. Finally everything works great!
Sometimes I would like the router NOT to go through the Mullvad Wireguard VPN. For example, when connected to the VPN, my up and down speeds tend to be about 70 Mbps / 10 Mbps, resp, and so if I have a huge file to download, it would be nice to have an easy way to have the router pass my network traffic directly through my ISP without VPN overhead. That allows me much greater speeds, of course it also allows my ISP to peek through my packets, but that's life sometimes.
What might be the easiest / fastest way to reconfigure things temporarily so my network traffic goes directly through my ISP without VPN overhead, which I can subsequently revert back to a normal state where all traffic goes through the VPN?
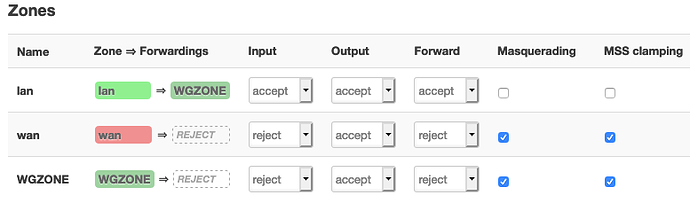
In my scenario, I use Mullvad VPN with the Wireguard protocol. Mullvad's OpenWrt configuration instructions are here. Given my very limited network knowledge, I think the crux of things is the firewall setup as follows:
Here, I've modified things so that the lan traffic no longer forwards to a WAN destination, but instead to a new 'WGZONE' destination. WGZONE subsequently utilizes a new WGINTERFACE, wherein the WireGuard VPN protocol utilizes the Mullvad VPN servers.
So it seems like I could simply pop into here and temporarily revert lan to forward to its original WAN destination, to go around the VPN? Probably obviously, I'm in over my head here. In my ideal world, I'd have a shiny button I could click in the OpenWrt UI to disable VPN for 10 minutes (for example). A ssh script would be next best I believe.
One concern is whether I would need to restart any/all of the interfaces, which could be time consuming and perhaps require a router reboot, all of which are undesirable unless required.
Any suggestions are appreciated! Thank you for your help.
Edit: A complication is use of a VPN watchdog cronjob shell script that pings the VPN every 10 minutes and if failure, reboots the router... so this would need to be temporarily disabled as well, either by modifying its cron entry, or by having the script be aware of when "VPN bypass mode" is on.