After clarifying the setup of the first AP, here is the second device.
Hardware wise this is a PoE device with only one ethernet port aka sinlge port device.
The AP is working, but I can't remember how I managed to set it up like this. ![]()
It is running the latest software 23.05.0-RC3.
It is set up as a dumb AP but there is a setting that can't be found in the how-tos.
The guest wifi will not working if the setup is done only according to the guide.
I would like to learn what is different and why.
My guess is that the misconfiguration is due to the missing wan interface - but I might be wrong.
That's the reason for this thread.
The problem with the guest wifi is as follows:
If a client connects to the guest wifi it will obtain a correct IP in the guest IP range,
but it will not have an internet connection.
It seems the DNS can't be reached. So there must be a routing issue.
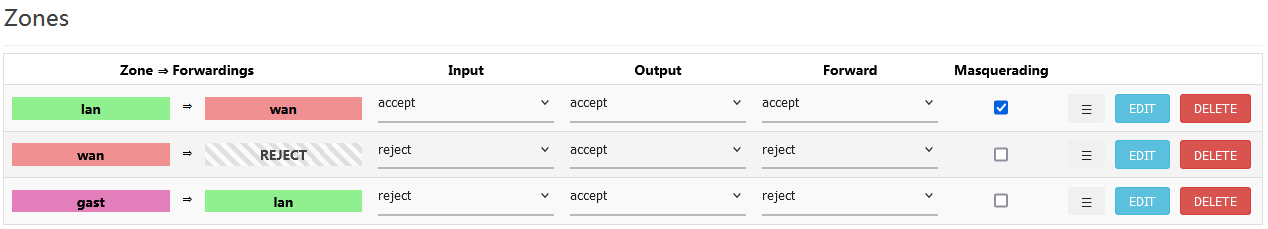
Here are the zone settings:
They are the same as on the other AP, but this device has different hardware.
No switch, no wan zone.
Here are the firewall settings:
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
config zone
option name 'gast'
option output 'ACCEPT'
option forward 'REJECT'
option input 'REJECT'
option family 'ipv4'
list network 'GAST'
config rule
option name 'Gast DHCP'
option src 'gast'
option dest_port '67 68'
option target 'ACCEPT'
option family 'ipv4'
list proto 'udp'
config rule
option name 'Gast DNS'
option src 'gast'
option target 'ACCEPT'
option family 'ipv4'
option dest_port '53'
config rule
option src 'gast'
option dest 'lan'
list dest_ip '192.168.158.0/24'
option target 'DROP'
option family 'ipv4'
option name 'Gast block nach Privat'
list proto 'all'
config rule
option family 'ipv4'
option src 'gast'
option target 'DROP'
option name 'Gast block AP-Config GUI+SSH'
option dest_port '80 22'
config forwarding
option src 'gast'
option dest 'lan'
config forwarding
option src 'lan'
option dest 'gast'
Traffic rules to allow DHCP and DNS traffic are in place.
Once the below route is added to the network config, the issue is solved.
Due to my lacking knowledge I can't judge if this is a good and secure solution.
config route 'net'
option interface 'lan'
option target '0.0.0.0/0'
option netmask '255.255.255.0'
option gateway '192.168.158.1'
Q1: Is this static route the only configuration option? Why?
Q2:Can the routing be done with zone configuration like on the other AP?
I wonder why there is little information on this matter. I searched the net before posting, but to no avail.