After some frustration in trying to figure out what exactly PVID means
in relation to vlans and trunk usage in openwrt.
Thanx to jow in pointing out what it actually means ,
So I decided to poke further and find a use case where it can actually apply it in openwrt .
I decided to replicate and test a basic concept from cisco of Private vlans .
Having multiple layer 2 domains with restrictions on who they can talk to.
And now the ability to create multiple untagged vlans on a port without complaints
from luci is starting to make sense.
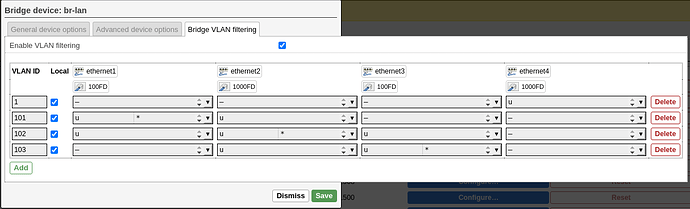
PVID concept In openwrt (and other switches?)
means an untagged ingress takes precedence over other existing untagged vlans on the port.
here is a basic Layer 2 setup.
I have not assigned any layer3 interfaces to these vlans. so 3 computers connected to
those 3 ports had ips set manualy just to test the layer2 concept.
port2 exists in both vlan101 , vlan102 and vlan103 but its ingress of untagged frames will always be
steered to PVID of 102.
port1 ingress will steer to vlan101
port3 ingress will steer to vlan103
and since port1 and port3 also exist in vlan102 untagged but not as PVID now they will
only receive frames in vlan102 but send on PVID defined vlan.
so now we have basic selective layer2 communication between port1 and port2,
and port3 and port2. but not between port1 and port3.
Intended usage of this setup could be access to a common resource such
as a server within the same subnet without the need for going trough firewall and
intervlan routing yet still segregating traffic
(and hopefully doing so at fastest switching speed possible without using cpu)
PS: It would be nice to hear of any other use cases of where PVID can be used.
thanx