I guess this is a piece of cake for you, but I am not able to find the problem (I have very little knowledge about networking)
I have 2 houses, A and B, connected by 2 Ubiquiti NSM5 radios in AP-WDS and Station-WDS mode, each one with a Linksys WRT1900AC router in separated network ranges.
I know double-NAT is something to be avoided, but I need to have different ranges as in each house I have a whole lot of clients (pcs, htpcs, nas, notebooks, smartphones, plugs, lights, tvs, plcs...) and I need them to be separated. The only machine I need to be accessed from the exterior is the NAS connected to Router A, so no problem for port forwarding/UPnP it as it is outside the Double-NAT.
My configuration is set as follows:
ONT --> Router A [192.168.13.1] --> Radio A [192.168.13.2] (............) Radio B [192.168.13.4 / 192.168.6.2] --> Router B [192.168.6.1 / 192.168.13.3]
ONT is connected from LAN1 port to Router A WAN port
Router A is connected from LAN1 port to Radio A LAN1 port
(Clients in House A are connected to Router A LAN ports 2 to 4)
Radio B is connected from LAN1 port to Router B WAN port
(Clients in House B are connected to Router B LAN ports 1 to 4)
So, Router A LAN1 port is "connected" (via the Radios) to Router B WAN port.
I have no problem accessing from House B to House A shared resources [192.168.6.X --> 192.168.13.X], but I cannot access from House A to House B [192.168.13.X -/-> 192.168.6.X]. I suspect it has something to do with firewall rules on Router B (the one where the Double-NAT is) but I cannot figure it out.
I thought allowing input/output traffic from WAN to LAN in Router B would fix it.
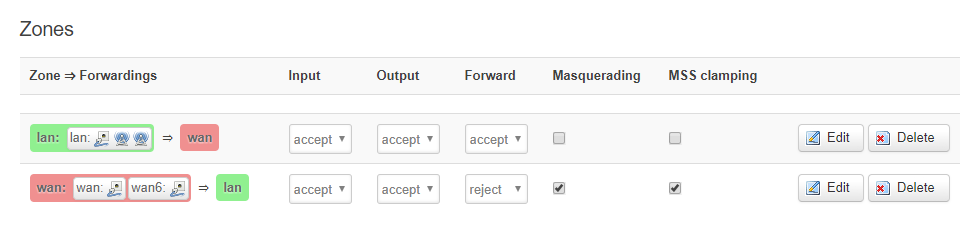
I also created manually the following rule to allow forward from any host in WAN to any host in LAN in Router B.

My /etc/config/network output
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd6a:13e6:5d77::/48'
config interface 'lan'
option force_link '1'
option type 'bridge'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.6.1'
option _orig_ifname 'eth0 wlan1'
option _orig_bridge 'true'
option ifname 'eth0'
option gateway '192.168.13.1'
option dns '8.8.8.8 8.8.4.4'
config interface 'wan'
option ifname 'eth1'
option _orig_ifname 'eth1'
option _orig_bridge 'false'
option proto 'static'
option ipaddr '192.168.13.3'
option netmask '255.255.255.0'
option gateway '192.168.13.1'
config interface 'wan6'
option ifname 'eth1'
option proto 'dhcpv6'
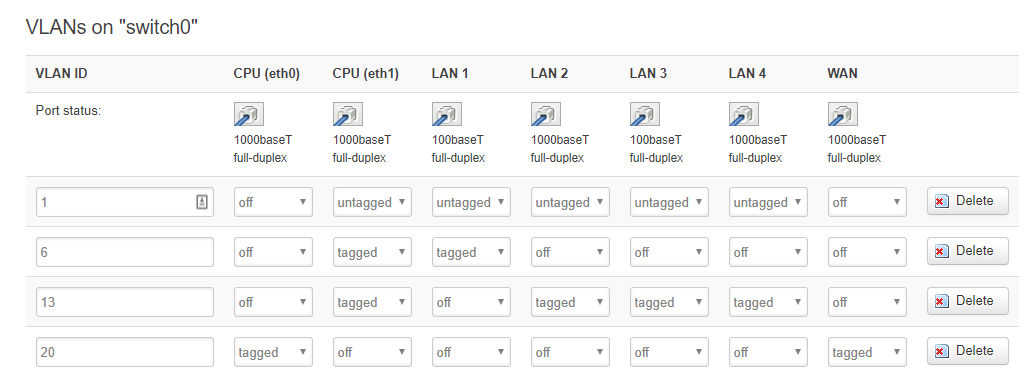
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 3 5'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6'
My /etc/config/firewall output
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option input 'ACCEPT'
option network 'wan wan6'
option forward 'REJECT'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fe80::/10'
option src_port '547'
option dest_ip 'fe80::/10'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config rule
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config forwarding
option dest 'lan'
option src 'wan'
config forwarding
option dest 'wan'
option src 'lan'
Thanks in advance.