Now that I've crossed the VLAN hurdle and have tagged/untagged the appropriate ports on my switches, I'm kind of wary about making firewall rules. I don't want to accidentally give the WAN access to something and expose my network.
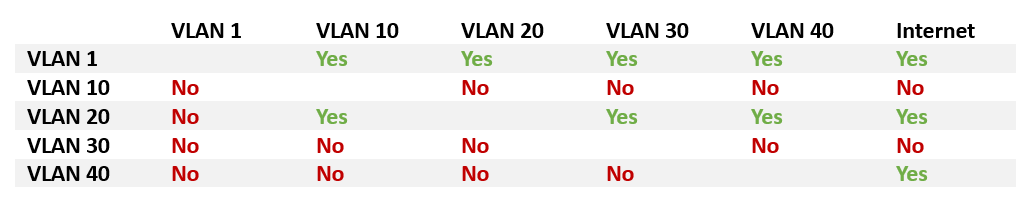
I have 5 VLANs: 1, 10, 20, 30, 40
I want VLAN 1 (Admin) to be able to see every other VLAN. I don't want other VLANs to be able to access/see devices on VLAN1
VLAN10 (CCTV) should be forbidden from accessing any VLAN, but I want VLAN1 and VLAN20 to be able to interact and see things.
VLAN 20 (Regular devices) should be able to see VLAN 10, VLAN 30, and VLAN 40.
VLAN 30 (IoT) should be barred from all VLANs entirely. No WAN access, either.
VLAN 40 (Guest) shouldn't be able to see any VLANs, but have internet browsing access.
I made a chart thingy to hopefully clear things up.
My issue is how the input/output/forward stuff works. I watched the recommended video on the OpenWrt wiki.
Say if I wanted VLAN1 to access VLAN10 but not vice versa, would I make a rule called VLAN1 and add VLAN10 to reject input and accept output? What about forward?
Also, what's the difference between "destination zones" and "covered networks"?
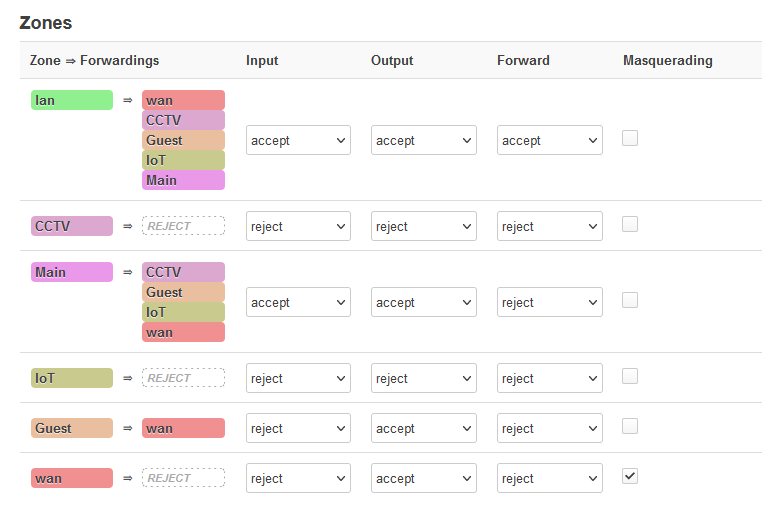
EDIT: I gave it a try without saving any changes. Is this right? Again, I'm antsy about WAN access.