taven
July 25, 2020, 7:58pm
1
Important Information
I'm using (just) cloudflare's DoH DNS server using https-dns-proxy as per this documentation .
This is my configuration when running uci show dhcp; uci show https-dns-proxy:
dhcp.@dnsmasq[0]=dnsmasq
dhcp.@dnsmasq[0].domainneeded='1'
dhcp.@dnsmasq[0].localise_queries='1'
dhcp.@dnsmasq[0].rebind_protection='1'
dhcp.@dnsmasq[0].rebind_localhost='1'
dhcp.@dnsmasq[0].expandhosts='1'
dhcp.@dnsmasq[0].authoritative='1'
dhcp.@dnsmasq[0].readethers='1'
dhcp.@dnsmasq[0].leasefile='/tmp/dhcp.leases'
dhcp.@dnsmasq[0].localservice='1'
dhcp.@dnsmasq[0].domain='edenia'
dhcp.@dnsmasq[0].local='/edenia/'
dhcp.@dnsmasq[0].sequential_ip='1'
dhcp.@dnsmasq[0].localuse='1'
dhcp.@dnsmasq[0].server='/openwrt.pool.ntp.org/1.0.0.1' '/openwrt.pool.ntp.org/1.1.1.1' '127.0.0.1#5053'
dhcp.@dnsmasq[0].noresolv='1'
dhcp.@dnsmasq[0].doh_backup_noresolv='-1'
dhcp.@dnsmasq[0].doh_backup_server='/openwrt.pool.ntp.org/1.0.0.1' '/openwrt.pool.ntp.org/1.1.1.1' '1.0.0.1#53' '1.1.1.1#53'
dhcp.lan=dhcp
dhcp.lan.interface='lan'
dhcp.lan.start='100'
dhcp.lan.leasetime='12h'
dhcp.lan.limit='150'
dhcp.lan.netmask='255.255.0.0'
dhcp.lan.ra='server'
dhcp.lan.dhcpv6='server'
dhcp.lan.ra_management='1'
dhcp.wan=dhcp
dhcp.wan.interface='wan'
dhcp.wan.ignore='1'
dhcp.odhcpd=odhcpd
dhcp.odhcpd.maindhcp='0'
dhcp.odhcpd.leasefile='/tmp/hosts/odhcpd'
dhcp.odhcpd.leasetrigger='/usr/sbin/odhcpd-update'
dhcp.odhcpd.loglevel='4'
https-dns-proxy.config=main
https-dns-proxy.config.update_dnsmasq_config='*'
https-dns-proxy.@https-dns-proxy[0]=https-dns-proxy
https-dns-proxy.@https-dns-proxy[0].bootstrap_dns='1.1.1.1,1.0.0.1'
https-dns-proxy.@https-dns-proxy[0].resolver_url='https://cloudflare-dns.com/dns-query'
https-dns-proxy.@https-dns-proxy[0].listen_addr='127.0.0.1'
https-dns-proxy.@https-dns-proxy[0].listen_port='5053'
This is the nslookup:
❯ nslookup medium.com
Server: portal.edenia
Address: fd4c:8745:4f50::1
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
*** Request to portal.edenia timed-out
Potentially Relevant Information
portal.edenia is exclusively the DHCP and DNS server and the gateway is housed on 192.168.1.1.
portal.edenia has only 58.24 MB total R.A.M and around 7 MB left unused on average.
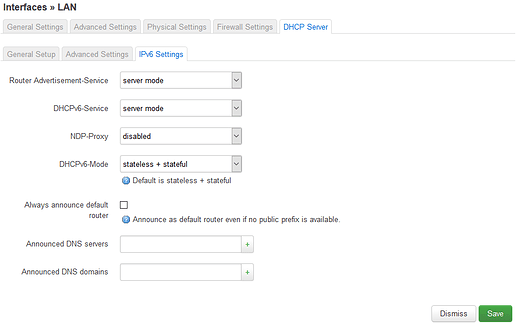
portal.edenia does not have DNS server explicity set on the IPv4 or IPv6 DHCP server settings as seen below:
Problem
How do I fix the issue of DNS timing out?
Please, run all commands from the troubleshooting section and post the output.
date; for HOST in $(uci get system.ntp.server); do nslookup ${HOST}; done
taven
July 29, 2020, 1:54am
3
Here is the output of all the commands in order as per the troubleshooting section in addition to the NTP debugs you requested:
root@portal:~# /etc/init.d/log restart; /etc/init.d/dnsmasq restart; /etc/init.d/https-dns-proxy restart
udhcpc: started, v1.30.1
udhcpc: sending discover
udhcpc: no lease, failing
root@portal:~# logread -e dnsmasq; netstat -l -n -p | grep -e dnsmasq
Wed Jul 29 07:12:33 2020 daemon.info dnsmasq[1377]: exiting on receipt of SIGTERM
Wed Jul 29 07:12:34 2020 user.notice dnsmasq: DNS rebinding protection is active, will discard upstream RFC1918 responses!
Wed Jul 29 07:12:34 2020 user.notice dnsmasq: Allowing 127.0.0.0/8 responses
Wed Jul 29 07:12:39 2020 daemon.info dnsmasq[7930]: started, version 2.80 cachesize 150
Wed Jul 29 07:12:39 2020 daemon.info dnsmasq[7930]: DNS service limited to local subnets
Wed Jul 29 07:12:39 2020 daemon.info dnsmasq[7930]: compile time options: IPv6 GNU-getopt no-DBus no-i18n no-IDN DHCP no-DHCPv6 no-Lua TFTP no-conntrack no-ipset no-auth no-DNSSEC no-ID loop-detect inotify dumpfile
Wed Jul 29 07:12:39 2020 daemon.info dnsmasq-dhcp[7930]: DHCP, IP range 192.168.0.100 -- 192.168.0.249, lease time 12h
Wed Jul 29 07:12:39 2020 daemon.info dnsmasq[7930]: using local addresses only for domain test
Wed Jul 29 07:12:39 2020 daemon.info dnsmasq[7930]: using local addresses only for domain onion
Wed Jul 29 07:12:39 2020 daemon.info dnsmasq[7930]: using local addresses only for domain localhost
Wed Jul 29 07:12:39 2020 daemon.info dnsmasq[7930]: using local addresses only for domain local
Wed Jul 29 07:12:39 2020 daemon.info dnsmasq[7930]: using local addresses only for domain invalid
Wed Jul 29 07:12:39 2020 daemon.info dnsmasq[7930]: using local addresses only for domain bind
Wed Jul 29 07:12:39 2020 daemon.info dnsmasq[7930]: using nameserver 127.0.0.1#5053
Wed Jul 29 07:12:39 2020 daemon.info dnsmasq[7930]: using nameserver 1.1.1.1#53 for domain openwrt.pool.ntp.org
Wed Jul 29 07:12:39 2020 daemon.info dnsmasq[7930]: using nameserver 1.0.0.1#53 for domain openwrt.pool.ntp.org
Wed Jul 29 07:12:39 2020 daemon.info dnsmasq[7930]: using local addresses only for domain edenia
Wed Jul 29 07:12:39 2020 daemon.info dnsmasq[7930]: read /etc/hosts - 4 addresses
Wed Jul 29 07:12:40 2020 daemon.info dnsmasq[7930]: read /tmp/hosts/odhcpd - 2 addresses
Wed Jul 29 07:12:40 2020 daemon.info dnsmasq[7930]: read /tmp/hosts/dhcp.cfg01411c - 2 addresses
Wed Jul 29 07:12:40 2020 daemon.info dnsmasq-dhcp[7930]: read /etc/ethers - 0 addresses
Wed Jul 29 07:12:41 2020 daemon.info dnsmasq[7930]: exiting on receipt of SIGTERM
Wed Jul 29 07:12:41 2020 user.notice dnsmasq: DNS rebinding protection is active, will discard upstream RFC1918 responses!
Wed Jul 29 07:12:41 2020 user.notice dnsmasq: Allowing 127.0.0.0/8 responses
Wed Jul 29 07:12:46 2020 daemon.info dnsmasq[8045]: started, version 2.80 cachesize 150
Wed Jul 29 07:12:46 2020 daemon.info dnsmasq[8045]: DNS service limited to local subnets
Wed Jul 29 07:12:46 2020 daemon.info dnsmasq[8045]: compile time options: IPv6 GNU-getopt no-DBus no-i18n no-IDN DHCP no-DHCPv6 no-Lua TFTP no-conntrack no-ipset no-auth no-DNSSEC no-ID loop-detect inotify dumpfile
Wed Jul 29 07:12:46 2020 daemon.info dnsmasq-dhcp[8045]: DHCP, IP range 192.168.0.100 -- 192.168.0.249, lease time 12h
Wed Jul 29 07:12:46 2020 daemon.info dnsmasq[8045]: using local addresses only for domain test
Wed Jul 29 07:12:46 2020 daemon.info dnsmasq[8045]: using local addresses only for domain onion
Wed Jul 29 07:12:46 2020 daemon.info dnsmasq[8045]: using local addresses only for domain localhost
Wed Jul 29 07:12:46 2020 daemon.info dnsmasq[8045]: using local addresses only for domain local
Wed Jul 29 07:12:46 2020 daemon.info dnsmasq[8045]: using local addresses only for domain invalid
Wed Jul 29 07:12:46 2020 daemon.info dnsmasq[8045]: using local addresses only for domain bind
Wed Jul 29 07:12:46 2020 daemon.info dnsmasq[8045]: using nameserver 1.1.1.1#53
Wed Jul 29 07:12:46 2020 daemon.info dnsmasq[8045]: using nameserver 1.0.0.1#53
Wed Jul 29 07:12:46 2020 daemon.info dnsmasq[8045]: using nameserver 1.1.1.1#53 for domain openwrt.pool.ntp.org
Wed Jul 29 07:12:46 2020 daemon.info dnsmasq[8045]: using nameserver 1.0.0.1#53 for domain openwrt.pool.ntp.org
Wed Jul 29 07:12:46 2020 daemon.info dnsmasq[8045]: using local addresses only for domain edenia
Wed Jul 29 07:12:46 2020 daemon.warn dnsmasq[8045]: no servers found in /tmp/resolv.conf.auto, will retry
Wed Jul 29 07:12:46 2020 daemon.info dnsmasq[8045]: read /etc/hosts - 4 addresses
Wed Jul 29 07:12:46 2020 daemon.info dnsmasq[8045]: read /tmp/hosts/odhcpd - 2 addresses
Wed Jul 29 07:12:46 2020 daemon.info dnsmasq[8045]: read /tmp/hosts/dhcp.cfg01411c - 2 addresses
Wed Jul 29 07:12:46 2020 daemon.info dnsmasq-dhcp[8045]: read /etc/ethers - 0 addresses
Wed Jul 29 07:12:47 2020 daemon.info dnsmasq[8045]: exiting on receipt of SIGTERM
Wed Jul 29 07:12:47 2020 user.notice dnsmasq: DNS rebinding protection is active, will discard upstream RFC1918 responses!
Wed Jul 29 07:12:47 2020 user.notice dnsmasq: Allowing 127.0.0.0/8 responses
Wed Jul 29 07:12:50 2020 daemon.info dnsmasq[8180]: started, version 2.80 cachesize 150
Wed Jul 29 07:12:50 2020 daemon.info dnsmasq[8180]: DNS service limited to local subnets
Wed Jul 29 07:12:50 2020 daemon.info dnsmasq[8180]: compile time options: IPv6 GNU-getopt no-DBus no-i18n no-IDN DHCP no-DHCPv6 no-Lua TFTP no-conntrack no-ipset no-auth no-DNSSEC no-ID loop-detect inotify dumpfile
Wed Jul 29 07:12:50 2020 daemon.info dnsmasq-dhcp[8180]: DHCP, IP range 192.168.0.100 -- 192.168.0.249, lease time 12h
Wed Jul 29 07:12:50 2020 daemon.info dnsmasq[8180]: using local addresses only for domain test
Wed Jul 29 07:12:50 2020 daemon.info dnsmasq[8180]: using local addresses only for domain onion
Wed Jul 29 07:12:50 2020 daemon.info dnsmasq[8180]: using local addresses only for domain localhost
Wed Jul 29 07:12:50 2020 daemon.info dnsmasq[8180]: using local addresses only for domain local
Wed Jul 29 07:12:50 2020 daemon.info dnsmasq[8180]: using local addresses only for domain invalid
Wed Jul 29 07:12:50 2020 daemon.info dnsmasq[8180]: using local addresses only for domain bind
Wed Jul 29 07:12:50 2020 daemon.info dnsmasq[8180]: using nameserver 127.0.0.1#5053
Wed Jul 29 07:12:50 2020 daemon.info dnsmasq[8180]: using nameserver 1.1.1.1#53 for domain openwrt.pool.ntp.org
Wed Jul 29 07:12:50 2020 daemon.info dnsmasq[8180]: using nameserver 1.0.0.1#53 for domain openwrt.pool.ntp.org
Wed Jul 29 07:12:50 2020 daemon.info dnsmasq[8180]: using local addresses only for domain edenia
Wed Jul 29 07:12:50 2020 daemon.info dnsmasq[8180]: read /etc/hosts - 4 addresses
Wed Jul 29 07:12:50 2020 daemon.info dnsmasq[8180]: read /tmp/hosts/odhcpd - 2 addresses
Wed Jul 29 07:12:50 2020 daemon.info dnsmasq[8180]: read /tmp/hosts/dhcp.cfg01411c - 2 addresses
Wed Jul 29 07:12:50 2020 daemon.info dnsmasq-dhcp[8180]: read /etc/ethers - 0 addresses
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 8180/dnsmasq
tcp 0 0 192.168.2.1:53 0.0.0.0:* LISTEN 8180/dnsmasq
tcp 0 0 ::1:53 :::* LISTEN 8180/dnsmasq
tcp 0 0 fd4c:8745:4f50::1:53 :::* LISTEN 8180/dnsmasq
tcp 0 0 fe80::4aee:cff:feec:c003:53 :::* LISTEN 8180/dnsmasq
udp 0 0 127.0.0.1:53 0.0.0.0:* 8180/dnsmasq
udp 0 0 192.168.2.1:53 0.0.0.0:* 8180/dnsmasq
udp 0 0 0.0.0.0:67 0.0.0.0:* 8180/dnsmasq
udp 0 0 ::1:53 :::* 8180/dnsmasq
udp 0 0 fd4c:8745:4f50::1:53 :::* 8180/dnsmasq
udp 0 0 fe80::4aee:cff:feec:c003:53 :::* 8180/dnsmasq
root@portal:~# logread -e https-dns-proxy; netstat -l -n -p | grep -e https-dns
udp 0 0 127.0.0.1:5053 0.0.0.0:* 8190/https-dns-prox
root@portal:~# pgrep -f -a dnsmasq; pgrep -f -a https-dns-proxy
8180 /usr/sbin/dnsmasq -C /var/etc/dnsmasq.conf.cfg01411c -k -x /var/run/dnsmasq/dnsmasq.cfg01411c.pid
8190 /usr/sbin/https-dns-proxy -a 127.0.0.1 -p 5053 -b 1.1.1.1,1.0.0.1 -r https://cloudflare-dns.com/dns-query -u nobody -g nogroup -4
root@portal:~# uci show dhcp; uci show https-dns-proxy
dhcp.@dnsmasq[0]=dnsmasq
dhcp.@dnsmasq[0].domainneeded='1'
dhcp.@dnsmasq[0].localise_queries='1'
dhcp.@dnsmasq[0].rebind_protection='1'
dhcp.@dnsmasq[0].rebind_localhost='1'
dhcp.@dnsmasq[0].expandhosts='1'
dhcp.@dnsmasq[0].authoritative='1'
dhcp.@dnsmasq[0].readethers='1'
dhcp.@dnsmasq[0].leasefile='/tmp/dhcp.leases'
dhcp.@dnsmasq[0].localservice='1'
dhcp.@dnsmasq[0].domain='edenia'
dhcp.@dnsmasq[0].local='/edenia/'
dhcp.@dnsmasq[0].sequential_ip='1'
dhcp.@dnsmasq[0].localuse='1'
dhcp.@dnsmasq[0].server='/openwrt.pool.ntp.org/1.0.0.1' '/openwrt.pool.ntp.org/1.1.1.1' '127.0.0.1#5053'
dhcp.@dnsmasq[0].noresolv='1'
dhcp.@dnsmasq[0].doh_backup_noresolv='-1'
dhcp.@dnsmasq[0].doh_backup_server='/openwrt.pool.ntp.org/1.0.0.1' '/openwrt.pool.ntp.org/1.1.1.1' '1.0.0.1#53' '1.1.1.1#53'
dhcp.lan=dhcp
dhcp.lan.interface='lan'
dhcp.lan.start='100'
dhcp.lan.leasetime='12h'
dhcp.lan.limit='150'
dhcp.lan.netmask='255.255.0.0'
dhcp.lan.ra='server'
dhcp.lan.dhcpv6='server'
dhcp.lan.ra_management='1'
dhcp.wan=dhcp
dhcp.wan.interface='wan'
dhcp.wan.ignore='1'
dhcp.odhcpd=odhcpd
dhcp.odhcpd.maindhcp='0'
dhcp.odhcpd.leasefile='/tmp/hosts/odhcpd'
dhcp.odhcpd.leasetrigger='/usr/sbin/odhcpd-update'
dhcp.odhcpd.loglevel='4'
https-dns-proxy.config=main
https-dns-proxy.config.update_dnsmasq_config='*'
https-dns-proxy.@https-dns-proxy[0]=https-dns-proxy
https-dns-proxy.@https-dns-proxy[0].bootstrap_dns='1.1.1.1,1.0.0.1'
https-dns-proxy.@https-dns-proxy[0].resolver_url='https://cloudflare-dns.com/dns-query'
https-dns-proxy.@https-dns-proxy[0].listen_addr='127.0.0.1'
https-dns-proxy.@https-dns-proxy[0].listen_port='5053'
root@portal:~# date; for HOST in $(uci get system.ntp.server); do nslookup ${HOST}; done
Wed Jul 29 07:16:26 IST 2020
Server: 127.0.0.1
Address: 127.0.0.1#53
Name: 0.openwrt.pool.ntp.org
Address 1: 157.119.108.165
Address 2: 95.216.192.15
Address 3: 104.211.76.226
Address 4: 49.207.184.110
*** Can't find 0.openwrt.pool.ntp.org: No answer
Server: 127.0.0.1
Address: 127.0.0.1#53
Name: 1.openwrt.pool.ntp.org
Address 1: 13.126.27.131
Address 2: 172.105.40.191
Address 3: 139.59.15.185
Address 4: 103.134.252.11
*** Can't find 1.openwrt.pool.ntp.org: No answer
Server: 127.0.0.1
Address: 127.0.0.1#53
Name: 2.openwrt.pool.ntp.org
Address 1: 5.103.139.163
Address 2: 5.189.141.35
Address 3: 95.216.192.15
Address 4: 139.59.55.93
Address 5: 2a01:4f9:c010:1625::1
Address 6: 2606:4700:f1::123
Address 7: 2606:4700:f1::1
Address 8: 2001:1600:4:1::f
Server: 127.0.0.1
Address: 127.0.0.1#53
Name: 3.openwrt.pool.ntp.org
Address 1: 5.103.139.163
Address 2: 162.159.200.1
Address 3: 139.59.55.93
Address 4: 13.126.27.131
*** Can't find 3.openwrt.pool.ntp.org: No answer
root@portal:~#
Any help appreciated!
1 Like
nslookup example.org 127.0.0.1
nslookup example.org 127.0.0.1#5053
nslookup cloudflare-dns.com 127.0.0.1
nslookup cloudflare-dns.com 127.0.0.1#5053
nslookup cloudflare-dns.com 1.1.1.1
nslookup cloudflare-dns.com 1.0.0.1
What does this say?
taven
July 29, 2020, 3:39am
5
Here ya go
root@portal:~# nslookup openwrt.org 127.0.0.1
Server: 127.0.0.1
Address: 127.0.0.1#53
Name: openwrt.org
Address 1: 139.59.209.225
Address 2: 2a03:b0c0:3:d0::1af1:1
root@portal:~# nslookup openwrt.org 127.0.0.1#5053
Server: 127.0.0.1
Address: 127.0.0.1#5053
Name: openwrt.org
Address 1: 139.59.209.225
Address 2: 2a03:b0c0:3:d0::1af1:1
root@portal:~# nslookup cloudflare-dns.com 127.0.0.1
Server: 127.0.0.1
Address: 127.0.0.1#53
Name: cloudflare-dns.com
Address 1: 104.16.249.249
Address 2: 104.16.248.249
Address 3: 2606:4700::6810:f8f9
Address 4: 2606:4700::6810:f9f9
root@portal:~# nslookup cloudflare-dns.com 127.0.0.1#5053
Server: 127.0.0.1
Address: 127.0.0.1#5053
Name: cloudflare-dns.com
Address 1: 104.16.248.249
Address 2: 104.16.249.249
Address 3: 2606:4700::6810:f9f9
Address 4: 2606:4700::6810:f8f9
root@portal:~# nslookup cloudflare-dns.com 1.1.1.1
Server: 1.1.1.1
Address: 1.1.1.1#53
Name: cloudflare-dns.com
Address 1: 104.16.249.249
Address 2: 104.16.248.249
Address 3: 2606:4700::6810:f8f9
Address 4: 2606:4700::6810:f9f9
root@portal:~# nslookup cloudflare-dns.com 1.0.0.1
Server: 1.0.0.1
Address: 1.0.0.1#53
Name: cloudflare-dns.com
Address 1: 104.16.248.249
Address 2: 104.16.249.249
Address 3: 2606:4700::6810:f9f9
Address 4: 2606:4700::6810:f8f9
Thank you for helping me btw!
1 Like
It seems working from OpenWrt.
taven
July 29, 2020, 3:51am
7
Yes it's confusing me as well! Here is what happens when I renew lease on my laptop:
❯ ipconfig /release
Windows IP Configuration
No operation can be performed on Ethernet while it has its media disconnected.
No operation can be performed on Local Area Connection* 9 while it has its media disconnected.
Ethernet adapter Ethernet:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . : lan
Ethernet adapter vEthernet (WSL):
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::7c7f:e0bc:c631:e25%47
IPv4 Address. . . . . . . . . . . : 172.20.48.1
Subnet Mask . . . . . . . . . . . : 255.255.240.0
Default Gateway . . . . . . . . . :
Wireless LAN adapter Local Area Connection* 9:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Wireless LAN adapter Local Area Connection* 10:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Wireless LAN adapter Wi-Fi:
Connection-specific DNS Suffix . :
IPv6 Address. . . . . . . . . . . : fd4c:8745:4f50::53d
IPv6 Address. . . . . . . . . . . : fd4c:8745:4f50:0:181f:3c35:281b:203c
Temporary IPv6 Address. . . . . . : fd4c:8745:4f50:0:9ae:5180:1215:722
Link-local IPv6 Address . . . . . : fe80::181f:3c35:281b:203c%17
❯ ipconfig /renew
Windows IP Configuration
No operation can be performed on Ethernet while it has its media disconnected.
No operation can be performed on Local Area Connection* 9 while it has its media disconnected.
No operation can be performed on Local Area Connection* 10 while it has its media disconnected.
Ethernet adapter Ethernet:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . : lan
Ethernet adapter vEthernet (WSL):
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::7c7f:e0bc:c631:e25%47
IPv4 Address. . . . . . . . . . . : 172.20.48.1
Subnet Mask . . . . . . . . . . . : 255.255.240.0
Default Gateway . . . . . . . . . :
Wireless LAN adapter Local Area Connection* 9:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Wireless LAN adapter Local Area Connection* 10:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Wireless LAN adapter Wi-Fi:
Connection-specific DNS Suffix . : edenia
IPv6 Address. . . . . . . . . . . : fd4c:8745:4f50::53d
IPv6 Address. . . . . . . . . . . : fd4c:8745:4f50:0:181f:3c35:281b:203c
Temporary IPv6 Address. . . . . . : fd4c:8745:4f50:0:9ae:5180:1215:722
Link-local IPv6 Address . . . . . : fe80::181f:3c35:281b:203c%17
IPv4 Address. . . . . . . . . . . : 192.168.0.199
Subnet Mask . . . . . . . . . . . : 255.255.0.0
Default Gateway . . . . . . . . . : 192.168.2.1
❯ ipconfig /all
Windows IP Configuration
Host Name . . . . . . . . . . . . : Edenia
Primary Dns Suffix . . . . . . . :
Node Type . . . . . . . . . . . . : Hybrid
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
DNS Suffix Search List. . . . . . : edenia
Ethernet adapter Ethernet:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . : lan
Description . . . . . . . . . . . : Realtek PCIe GbE Family Controller
Physical Address. . . . . . . . . : 04-D4-C4-78-E1-F9
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
Ethernet adapter vEthernet (WSL):
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Hyper-V Virtual Ethernet Adapter
Physical Address. . . . . . . . . : 00-15-5D-18-89-70
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
Link-local IPv6 Address . . . . . : fe80::7c7f:e0bc:c631:e25%47(Preferred)
IPv4 Address. . . . . . . . . . . : 172.20.48.1(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.240.0
Default Gateway . . . . . . . . . :
DHCPv6 IAID . . . . . . . . . . . : 788534621
DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-24-95-3E-60-04-D4-C4-78-E1-F9
DNS Servers . . . . . . . . . . . : fec0:0:0:ffff::1%1
fec0:0:0:ffff::2%1
fec0:0:0:ffff::3%1
NetBIOS over Tcpip. . . . . . . . : Enabled
Wireless LAN adapter Local Area Connection* 9:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Microsoft Wi-Fi Direct Virtual Adapter
Physical Address. . . . . . . . . : 82-91-33-06-72-B1
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
Wireless LAN adapter Local Area Connection* 10:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Microsoft Wi-Fi Direct Virtual Adapter #2
Physical Address. . . . . . . . . : C2-91-33-06-72-B1
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
Wireless LAN adapter Wi-Fi:
Connection-specific DNS Suffix . : edenia
Description . . . . . . . . . . . : Realtek 8821CE Wireless LAN 802.11ac PCI-E NIC
Physical Address. . . . . . . . . : 80-91-33-06-72-B1
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
IPv6 Address. . . . . . . . . . . : fd4c:8745:4f50::53d(Preferred)
Lease Obtained. . . . . . . . . . : Wednesday, July 29, 2020 7:10:16 AM
Lease Expires . . . . . . . . . . : Saturday, September 4, 2156 3:44:47 PM
IPv6 Address. . . . . . . . . . . : fd4c:8745:4f50:0:181f:3c35:281b:203c(Preferred)
Temporary IPv6 Address. . . . . . : fd4c:8745:4f50:0:9ae:5180:1215:722(Preferred)
Link-local IPv6 Address . . . . . : fe80::181f:3c35:281b:203c%17(Preferred)
IPv4 Address. . . . . . . . . . . : 192.168.0.199(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.0.0
Lease Obtained. . . . . . . . . . : Wednesday, July 29, 2020 9:16:14 AM
Lease Expires . . . . . . . . . . : Wednesday, July 29, 2020 9:16:16 PM
Default Gateway . . . . . . . . . : 192.168.2.1
DHCP Server . . . . . . . . . . . : 192.168.2.1
DHCPv6 IAID . . . . . . . . . . . : 41980211
DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-24-95-3E-60-04-D4-C4-78-E1-F9
DNS Servers . . . . . . . . . . . : fd4c:8745:4f50::1
192.168.2.1
fd4c:8745:4f50::1
NetBIOS over Tcpip. . . . . . . . : Enabled
1 Like
Make sure this matches the IPv4 and IPv6 addresses on OpenWrt.
Are you sure it is not 192.168.2.1?
taven
July 29, 2020, 4:07am
9
Looks like it matches:
root@portal:~# ifconfig
br-lan Link encap:Ethernet HWaddr 48:EE:0C:EC:C0:03
inet addr:192.168.2.1 Bcast:192.168.255.255 Mask:255.255.0.0
inet6 addr: fe80::4aee:cff:feec:c003/64 Scope:Link
inet6 addr: fd4c:8745:4f50::1/60 Scope:Global
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:107603683 errors:0 dropped:57915 overruns:0 frame:0
TX packets:107081150 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:141529497410 (131.8 GiB) TX bytes:142879032389 (133.0 GiB)
eth1 Link encap:Ethernet HWaddr 48:EE:0C:EC:C0:03
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:107605206 errors:0 dropped:0 overruns:10 frame:0
TX packets:107081154 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:1302554645 (1.2 GiB) TX bytes:1145110593 (1.0 GiB)
Interrupt:4
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:99888 errors:0 dropped:0 overruns:0 frame:0
TX packets:99888 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:11026253 (10.5 MiB) TX bytes:11026253 (10.5 MiB)
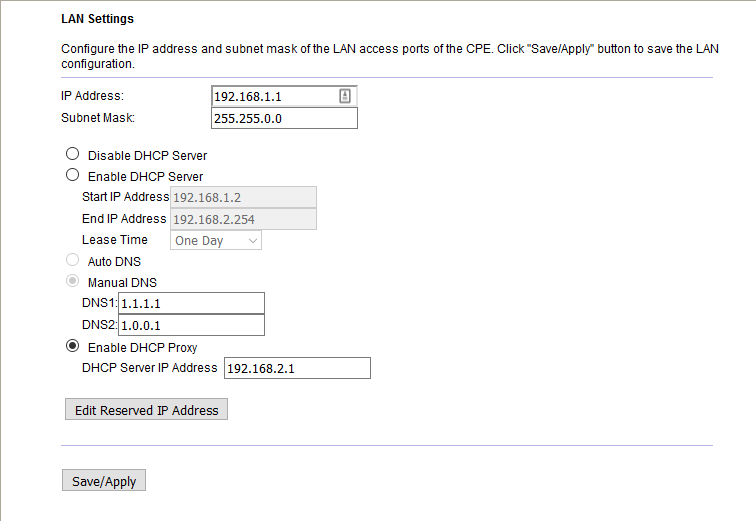
Well the main router (that provides WiFi) is the only one hooked up to Fiber. So the gateway has to be 192.168.1.1 but DHCP is by OpenWrt through LAN. Here is a screenshot of main router config setting for this:
1 Like
Let's check from the client:
ipconfig /flushdns
nslookup example.org
nslookup example.org 192.168.2.1
nslookup example.org fd4c:8745:4f50::1
taven
July 29, 2020, 11:03pm
11
Here it is:
❯ ipconfig /flushdns
Windows IP Configuration
Successfully flushed the DNS Resolver Cache.
❯ nslookup openwrt.org
Server: portal.edenia
Address: fd4c:8745:4f50::1
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
*** Request to portal.edenia timed-out
❯ nslookup openwrt.org 192.168.2.1
Server: portal.edenia
Address: 192.168.2.1
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
*** Request to portal.edenia timed-out
❯ nslookup openwrt.org fd4c:8745:4f50::1
Server: portal.edenia
Address: fd4c:8745:4f50::1
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
*** Request to portal.edenia timed-out
1 Like
Hm, let's check network and firewall configuration:
uci show network; uci show firewall; \
ip a; ip r s t all; ip ru; ip -6 ru; \
iptables-save; ip6tables-save
taven
July 30, 2020, 2:39am
13
Thank you so much for helping me out! Here are the results you requested:
root@portal:~# uci show network; uci show firewall; \
> ip a; ip r s t all; ip ru; ip -6 ru; \
> iptables-save; ip6tables-save
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fd4c:8745:4f50::/48'
network.lan=interface
network.lan.type='bridge'
network.lan.proto='static'
network.lan.ip6assign='60'
network.lan.netmask='255.255.0.0'
network.lan.ipaddr='192.168.2.1'
network.lan.gateway='192.168.1.1'
network.lan.ifname='eth1'
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].network='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].network='wan' 'wan6'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 48:ee:0c:ec:c0:02 brd ff:ff:ff:ff:ff:ff
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master br-lan state UP qlen 1000
link/ether 48:ee:0c:ec:c0:03 brd ff:ff:ff:ff:ff:ff
4: wlan0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 48:ee:0c:ec:c0:02 brd ff:ff:ff:ff:ff:ff
5: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 48:ee:0c:ec:c0:03 brd ff:ff:ff:ff:ff:ff
inet 192.168.2.1/16 brd 192.168.255.255 scope global br-lan
valid_lft forever preferred_lft forever
inet6 fd4c:8745:4f50::1/60 scope global
valid_lft forever preferred_lft forever
inet6 fe80::4aee:cff:feec:c003/64 scope link
valid_lft forever preferred_lft forever
default via 192.168.1.1 dev br-lan
192.168.0.0/16 dev br-lan scope link src 192.168.2.1
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
0: from all lookup local
32766: from all lookup main
4200000001: from all iif lo lookup unspec 12
4200000005: from all iif br-lan lookup unspec 12
# Generated by iptables-save v1.8.3 on Thu Jul 30 08:06:30 2020
*nat
:PREROUTING ACCEPT [101658:22282070]
:INPUT ACCEPT [1731:131262]
:OUTPUT ACCEPT [19213:1322852]
:POSTROUTING ACCEPT [58066:6600516]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
-A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
-A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
-A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
-A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
-A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
-A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
-A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
-A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Thu Jul 30 08:06:30 2020
# Generated by iptables-save v1.8.3 on Thu Jul 30 08:06:30 2020
*mangle
:PREROUTING ACCEPT [3127412:281066468]
:INPUT ACCEPT [90399:20258876]
:FORWARD ACCEPT [2975937:243933714]
:OUTPUT ACCEPT [102483:11821509]
:POSTROUTING ACCEPT [3075879:255287910]
COMMIT
# Completed on Thu Jul 30 08:06:30 2020
# Generated by iptables-save v1.8.3 on Thu Jul 30 08:06:30 2020
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
-A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
-A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
-A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
-A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
-A FORWARD -m comment --comment "!fw3" -j reject
-A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
-A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
-A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
-A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
-A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
-A syn_flood -m comment --comment "!fw3" -j DROP
-A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
-A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
-A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
-A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
-A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
-A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
-A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
-A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
-A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
-A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
-A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
-A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
COMMIT
# Completed on Thu Jul 30 08:06:30 2020
# Generated by ip6tables-save v1.8.3 on Thu Jul 30 08:06:30 2020
*mangle
:PREROUTING ACCEPT [30193:2609624]
:INPUT ACCEPT [27310:2224474]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [23857:3036198]
:POSTROUTING ACCEPT [23856:3036102]
COMMIT
# Completed on Thu Jul 30 08:06:30 2020
# Generated by ip6tables-save v1.8.3 on Thu Jul 30 08:06:30 2020
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
-A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
-A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
-A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
-A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
-A FORWARD -m comment --comment "!fw3" -j reject
-A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
-A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
-A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
-A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp6-port-unreachable
-A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
-A syn_flood -m comment --comment "!fw3" -j DROP
-A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
-A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
-A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
-A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
-A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 128 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
-A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 129 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
-A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 1 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
-A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 2 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
-A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 3 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
-A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 4/0 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
-A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 4/1 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
-A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
-A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
-A zone_wan_input -s fc00::/6 -d fc00::/6 -p udp -m udp --dport 546 -m comment --comment "!fw3: Allow-DHCPv6" -j ACCEPT
-A zone_wan_input -s fe80::/10 -p ipv6-icmp -m icmp6 --icmpv6-type 130/0 -m comment --comment "!fw3: Allow-MLD" -j ACCEPT
-A zone_wan_input -s fe80::/10 -p ipv6-icmp -m icmp6 --icmpv6-type 131/0 -m comment --comment "!fw3: Allow-MLD" -j ACCEPT
-A zone_wan_input -s fe80::/10 -p ipv6-icmp -m icmp6 --icmpv6-type 132/0 -m comment --comment "!fw3: Allow-MLD" -j ACCEPT
-A zone_wan_input -s fe80::/10 -p ipv6-icmp -m icmp6 --icmpv6-type 143/0 -m comment --comment "!fw3: Allow-MLD" -j ACCEPT
-A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 128 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
-A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 129 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
-A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 1 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
-A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 2 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
-A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 3 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
-A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 4/0 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
-A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 4/1 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
-A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 133 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
-A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 135 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
-A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 134 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
-A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 136 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
-A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
-A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
-A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
COMMIT
# Completed on Thu Jul 30 08:06:30 2020
root@portal:~#
1 Like
I've checked the configs twice, and although I see no major problems, some sort of race condition is possible, so it is best to use split DNS mode:
# Remove incorrect options
uci -q delete dhcp.lan.netmask
# Enable split DNS mode and restore DNS-related defaults
uci -q delete dhcp.@dnsmasq[0].localuse
uci -q delete dhcp.@dnsmasq[0].server
uci -q delete dhcp.@dnsmasq[0].doh_backup_noresolv
uci -q delete dhcp.@dnsmasq[0].doh_backup_server
uci set dhcp.@dnsmasq[0].resolvfile="/tmp/resolv.conf.auto"
uci commit dhcp
/etc/init.d/dnsmasq restart
/etc/init.d/odhcpd restart
# Restore default resolvers
ln -f -s /tmp/resolv.conf.auto /tmp/resolv.conf
ln -f -s /tmp/resolv.conf /etc/resolv.conf
uci -q delete network.lan.dns
uci add_list network.lan.dns="1.1.1.1"
uci add_list network.lan.dns="1.0.0.1"
uci commit network
/etc/init.d/network restart
/etc/init.d/sysntpd restart
# Reinstall and reconfigure the packages
opkg update
opkg --force-reinstall install dnsmasq https-dns-proxy ca-bundle
while uci -q delete https-dns-proxy.@https-dns-proxy[0]; do :; done
uci set https-dns-proxy.dns="https-dns-proxy"
uci set https-dns-proxy.dns.bootstrap_dns="1.1.1.1,1.0.0.1"
uci set https-dns-proxy.dns.resolver_url="https://cloudflare-dns.com/dns-query"
uci set https-dns-proxy.dns.listen_addr="127.0.0.1"
uci set https-dns-proxy.dns.listen_port="5053"
uci commit https-dns-proxy
/etc/init.d/https-dns-proxy restart
 :
: