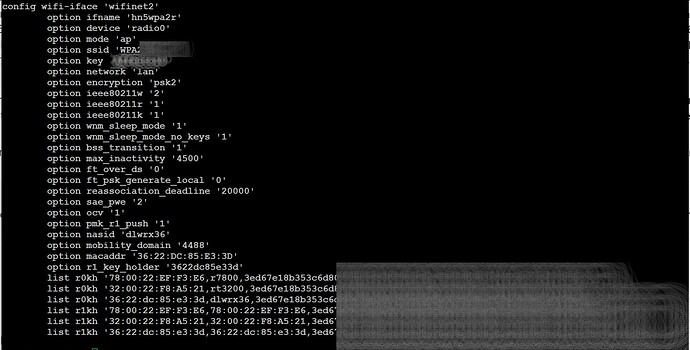
This is the config I ended up with (did it all on LuCi); this is the first AP:
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'Redacted SSID'
option key 'redactedpsk'
option encryption 'sae'
option ieee80211r '1'
option ft_over_ds '0'
option ft_psk_generate_local '0'
option nasid 'E8:9F:80:5D:37:2B'
option r1_key_holder 'E89F805D372B'
list r0kh 'E8:9F:80:5D:37:2B,E8:9F:80:5D:37:2B,0000000000000000000000000000000000000000000000000000000000000000'
list r0kh 'E8:9F:80:5D:37:2C,E8:9F:80:5D:37:2C,0000000000000000000000000000000000000000000000000000000000000000'
list r0kh 'E4:C3:2A:47:4A:3B,E4:C3:2A:47:4A:3B,0000000000000000000000000000000000000000000000000000000000000000'
list r1kh 'E8:9F:80:5D:37:2B,E8:9F:80:5D:37:2B,0000000000000000000000000000000000000000000000000000000000000000'
list r1kh 'E8:9F:80:5D:37:2C,E8:9F:80:5D:37:2C,0000000000000000000000000000000000000000000000000000000000000000'
list r1kh 'E4:C3:2A:47:4A:3B,E4:C3:2A:47:4A:3B,0000000000000000000000000000000000000000000000000000000000000000'
option reassociation_deadline '20000'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'Redacted SSID'
option key 'redactedpsk'
option encryption 'sae'
option ieee80211r '1'
option ft_over_ds '0'
option ft_psk_generate_local '0'
option nasid 'E8:9F:80:5D:37:2C'
option r1_key_holder 'E89F805D372C'
list r0kh 'E8:9F:80:5D:37:2C,E8:9F:80:5D:37:2C,0000000000000000000000000000000000000000000000000000000000000000'
list r0kh 'E8:9F:80:5D:37:2B,E8:9F:80:5D:37:2B,0000000000000000000000000000000000000000000000000000000000000000'
list r0kh 'E4:C3:2A:47:4A:3B,E4:C3:2A:47:4A:3B,0000000000000000000000000000000000000000000000000000000000000000'
list r1kh 'E8:9F:80:5D:37:2C,E8:9F:80:5D:37:2C,0000000000000000000000000000000000000000000000000000000000000000'
list r1kh 'E8:9F:80:5D:37:2B,E8:9F:80:5D:37:2B,0000000000000000000000000000000000000000000000000000000000000000'
list r1kh 'E4:C3:2A:47:4A:3B,E4:C3:2A:47:4A:3B,0000000000000000000000000000000000000000000000000000000000000000'
option reassociation_deadline '20000'
I tried to be clever and have the NAS ID the same as my BSSID and then r0kh and r1kh would be the same. The second AP:
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'Redacted SSID'
option encryption 'sae'
option key 'redactedpsk'
option ieee80211r '1'
option ft_over_ds '0'
option ft_psk_generate_local '0'
option nasid 'E4:C3:2A:47:4A:3B'
option reassociation_deadline '20000'
option r1_key_holder 'E4C32A474A3B'
list r0kh 'E4:C3:2A:47:4A:3B,E4:C3:2A:47:4A:3B,0000000000000000000000000000000000000000000000000000000000000000'
list r0kh 'E8:9F:80:5D:37:2C,E8:9F:80:5D:37:2C,0000000000000000000000000000000000000000000000000000000000000000'
list r0kh 'E8:9F:80:5D:37:2B,E8:9F:80:5D:37:2B,0000000000000000000000000000000000000000000000000000000000000000'
list r1kh 'E4:C3:2A:47:4A:3B,E4:C3:2A:47:4A:3B,0000000000000000000000000000000000000000000000000000000000000000'
list r1kh 'E8:9F:80:5D:37:2C,E8:9F:80:5D:37:2C,0000000000000000000000000000000000000000000000000000000000000000'
list r1kh 'E8:9F:80:5D:37:2B,E8:9F:80:5D:37:2B,0000000000000000000000000000000000000000000000000000000000000000'