Lynx
April 11, 2023, 3:34pm
1
I have an upstream router (br-lan: 192.168.0.1) and downstream router (wan: 192.168.0.2, br-lan: 192.168.1.1) - masquerading is disabled on the downstream router to avoid double NAT.
DNS queries from my downstream router to the upstream router work just fine, but DNS queries directed to 192.168.0.1 from LAN clients 192.168.1.x of the downstream router do not work, although such clients can ping 192.168.0.1. Using 'tcpdump' I think the upstream router sees the requests, but nothing happens.
Do you have a static route defined on the main router (192.168.1.0/24 via 192.168.0.2)?
Let's see your conifguration on your OpenWrt router:
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
1 Like
Lynx
April 11, 2023, 3:39pm
3
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
option ula_prefix ''
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.0.1'
config interface 'wan'
option proto 'modemmanager'
option device '/sys/devices/platform/1e1c0000.xhci/usb2/2-1'
option iptype 'ipv4v6'
option autoconnect '1'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
config route
option target '192.168.1.0/24'
option gateway '192.168.0.2'
option table 'main'
option interface 'lan'
config route
option target '192.168.2.0/24'
option gateway '192.168.0.2'
option table 'main'
option interface 'lan'
root@OpenWrt:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option name 'OpenWrt'
option dns '1'
option mac ''
option ip '192.168.0.2'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
option flow_offloading '1'
option flow_offloading_hw '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option mtu_fix '1'
option forward 'REJECT'
option masq '1'
list network 'wan'
list network 'wan6'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config forwarding
option src 'lan'
option dest 'wan'
Ok... this must be the main router. Everything looks okay here.
Can you post the config of the downstream router?
Lynx
April 11, 2023, 3:51pm
5
root@OpenWrt-1:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix ''
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option proto 'dhcp'
option device 'wan'
config interface 'wan6'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
option device 'wan'
config device
option type 'bridge'
option name 'br-guest'
option bridge_empty '1'
config interface 'guest'
option proto 'static'
option device 'br-guest'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
root@OpenWrt-1:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option localservice '1'
option ednspacket_max '1232'
option noresolv '1'
option localuse '1'
list server '127.0.0.1#5453'
list server '0::1#5453'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'guest'
option interface 'guest'
option start '100'
option limit '150'
option leasetime '12h'
config host
option mac ''
option ip '192.168.1.5'
config host
option mac ''
option ip '192.168.1.7'
root@OpenWrt-1:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option dest 'wan'
option src '*'
option start_time '21:00:00'
option stop_time '17:00:00'
option target 'REJECT'
option name 'Restrict-OpenWrt-GitHub'
list proto 'all'
list dest_ip '139.59.210.197'
list dest_ip '192.30.252.0/22'
list dest_ip '185.199.108.0/22'
list dest_ip '140.82.112.0/20'
list dest_ip '143.55.64.0/20'
list dest_ip '20.201.28.151/32'
list dest_ip '20.205.243.166/32'
list dest_ip '102.133.202.242/32'
list dest_ip '20.248.137.48/32'
list dest_ip '20.207.73.82/32'
list dest_ip '20.27.177.113/32'
list dest_ip '20.200.245.247/32'
list dest_ip '20.233.54.53/32'
option weekdays 'Mon Tue Wed Thu Fri'
option enabled '0'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'guest'
option output 'ACCEPT'
option forward 'REJECT'
list network 'guest'
option input 'REJECT'
config rule
option name 'Allow-GUEST-DNS'
option src 'guest'
option dest_port '53'
option target 'ACCEPT'
config rule
option name 'Allow-GUEST-DHCP'
list proto 'udp'
option src 'guest'
option dest_port '67'
option target 'ACCEPT'
config forwarding
option src 'guest'
option dest 'wan'
config redirect
option dest 'wan'
option target 'DNAT'
option name 'Guest-DNS-Hijack-Cloudflare'
option src 'guest'
option src_dport '53'
option dest_ip '1.1.1.1'
list src_mac ''
list src_mac ''
Looks like you have AGH or something else happening with your downstream router.... I'd look more into the configuration there. I'm not an expert on this aspect, though.
Lynx
April 11, 2023, 4:06pm
7
Just stubby - DNS to my downstream router goes via stubby. But I don't think that's what's preventing DNS requests from lan clients on 192.168.1.x from getting DNS responses from 192.168.0.1?
What are your 192.168.1.0/24 hosts using as their DNS? are they sending the queries to 192.168.1.1? (you can check this by looking at the network config on those devices).
Lynx
April 11, 2023, 4:09pm
9
Yes they are, but I thought I could just set 192.168.0.1 on a LAN client 192.168.1.x to use the upstream DNS (actually my ISP's DNS)? I tried nslookup from the downstream router 192.168.1.1 via 192.168.0.1 and that works. But not from 192.168.1.x clients. That makes me wonder if it's a firewall issue?
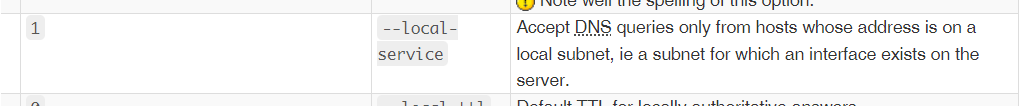
Try disabling dhcp.@dnsmasq[0].localservice on the upstream router.
2 Likes
Lynx
April 11, 2023, 4:16pm
11
That looks pretty promising:
DNS and DHCP configuration /etc/config/dhcp See also: DNS and DHCP examples, dnsmasq, odhcpd OpenWrt uses dnsmasq and odhcpd to serve DNS/DHCP and DHCPv6 by default. Roles Ports Packages Configuration DNS 53/UDP, 53/TCP dnsmasq ...
Lynx:
Yes they are,
So what is currently happening is that a host is sending its dns requests to 192.168.1.1 which in turn will send its requests to whatever that device has specified as the upstream dns (which is being affected by stubby).
In the absense of stubby or any other DNS configurations deviating from the default, your downstream router would simply foward the requests to the DNS advertised by the DHCP server upstream (which would be 192.168.0.1 based on the configuration we have seen). So all requests would simply go 192.168.1.x > 192.168.1.1 > 192.168.0.1 > ISP advertised DNS.
1 Like
Lynx
April 11, 2023, 4:22pm
13
Thanks @psherman . Maybe I can check my thinking with you to see if it makes sense. On my downstream router I have stubby set to send DNS requests out via CleanBrowsing Family Filter. Now this works great, but I've noticed that on my Microsoft Office 365 programs sometimes the 'Exchange Front Door' is getting set to an undesirable location (Germany). So my thinking was to make an override for the Microsoft domains on my downstream router that means those domains get sent out to the upstream router (and hence via my ISP's DNS servers). CleanBrowsing is there to block offensive content, but for Office365 I care about getting the best possible routing, and I think my ISP's DNS, Google or Cloudflare may be better for that. Does this seem reasonable?
I see that such selective domain-based DNS forwarding is facilitated in OpenWrt:
What the user did there was to advertise OpenDNS and hijack everything else.
Yes, force every device to use the OpenWrt and use the selective dns forwarding .
@dave14305 I've marked your post as the solution (many thanks!), since this made the requests work (albeit I am still unsure about whether what I have in mind above makes sense). I'd also value any thoughts you may have on the above.
system
April 21, 2023, 4:23pm
14
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.