Google announced support for DNS-over-HTTP/3
Please someone implement it in openwrt. And when you do, please make a GUI luci package too. ![]()
Great Link ... blockquoting some highlights
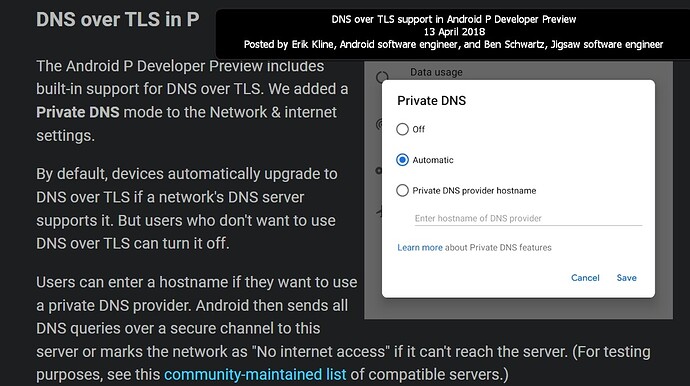
In Android 9.0, we announced the Private DNS feature, which uses DNS-over-TLS (DoT) to protect DNS queries when enabled and supported by the server. Unfortunately, DoT incurs overhead for every DNS request. An alternative encrypted DNS protocol, DNS-over-HTTPS (DoH), is rapidly gaining traction within the industry as DoH has already been deployed by most public DNS operators, including the Cloudflare Resolver and Google Public DNS. While using HTTPS alone will not reduce the overhead significantly, HTTP/3 uses QUIC, a transport that efficiently multiplexes multiple streams over UDP using a single TLS session with session resumption. All of these features are crucial to efficient operation on mobile devices.
DNS-over-HTTP/3 (DoH3) support was released as part of a Google Play system update, so by the time you’re reading this, Android devices from Android 11 onwards1 will use DoH3 instead of DoT for well-known2 DNS servers which support it. Which DNS service you are using is unaffected by this change; only the transport will be upgraded. In the future, we aim to support DDR which will allow us to dynamically select the correct configuration for any server. This feature should decrease the performance impact of encrypted DNS.
Is QUIC much more secure than TCP?
Oh great, more complexity piled upon complexity.
You can read as well as I can ![]() ... and that is not what I understood from the article and link.
... and that is not what I understood from the article and link.
I don't think @jow loves this very much.
Plus I enabled this on my android phone to "automatic"; rebooted and had no DNS at all ..
Web pages quickly gone up in smoke.
# The Internet just changed.
You better be aware of what just changed on the Internet. TCP is being replaced with QUIC. UDP is being used more and more instead of TCP. This affects your firewalls. It affects a lot of your network troubleshooting. HTTP/3 has been standardized. Everything is encrypted with QUIC - welcome to the new world of network troubleshooting and security.
Video link
https://www.youtube.com/watch?v=cdb7M37o9sU
// MENU //
00:00 - The Problem with TCP
00:12 - Introducing//Robin Marx
02:12 - Clean Ship, Clean House//RFCs
03:25 - HTTP Semantics//QUIC//HTTP/3
04:17 - Why the Hell Do We Need HTTP/3?
05:05 - Why QUIC?
08:35 - QUIC & TLS Integration
10:02 - Why Use UDP?
13:50 - Replacing TCP with QUIC
14:28 - Summary So Far
15:22 - Stream Multiplexing
15:40 - Head-of-line blocking
18:40 - Why This Slows Things Down
19:29 - How QUIC Does It Differently
20:58 - TCP vs QUIC//Packet Handling
23:11 - HTTP/3 Prioritization
25:25 - Stats//QUIC Isn't Going Anywhere
26:30 - Firewalls are almost useless
27:20 - Firewalls Blocking QUIC?
28:04 - QUIC & Other Protocols?
29:20 - IPv4 & IPv6//Different for QUIC?
29:54 - Challenges for QUIC's Growth
30:43 - Connection Migration
33:33 - What About Hackers?
36:32 - How Do I Get To Use QUIC?
38:28 - Large Companies Adopting QUIC
39:09 - The Internet is Too Centralized?
40:02 - Header Compression
41:55 - Server Push
43:47 - Practical Examples with Wireshark
50:34 - Thank You & How to Contact Robin
Sorry, but I missed that link. Can you put that up?
video link? I put the video link in Preformatted text
Which ever one you got that info from ....
Duhh see it now... it's in plain sight hidden in the preformatted text.
![]()
i already use ut with dnscrypt-proxy2 enable it in the settings.toml and after use browsers like chrome browse to about:flags and enable quic protocol.
if u cant set it up ill just copy paste my settings. its easy dont waste too much time on it. let me know if u get it set up
meanwhile while youre at it, enable some codec and hardware acceleration in the chrome settings lol. i think theyre faking their hardware acceleration considering how laggy chromium is compared to firefox on linux at least.
off topic but, about:gpu to check that.
still using dnscrypt proxy2?
cURL has this capability now but it's built without https3 support for OpenWrt for space.
If someone knows how to build it with support you'll have this in https-dns-proxy as well.
DNS over Dedicated QUIC Connections
Abstract
This document describes the use of QUIC to provide transport confidentiality for DNS. The encryption provided by QUIC has similar properties to those provided by TLS, while QUIC transport eliminates the head-of-line blocking issues inherent with TCP and provides more efficient packet-loss recovery than UDP. DNS over QUIC (DoQ) has privacy properties similar to DNS over TLS (DoT) specified in RFC 7858, and latency characteristics similar to classic DNS over UDP. This specification describes the use of DoQ as a general-purpose transport for DNS and includes the use of DoQ for stub to recursive, recursive to authoritative, and zone transfer scenarios.¶
is it different from dns over HTTP/3? VS dns over quic? Are these two things same?
https3 is the standard that evolved from Googles work on QUIC.
Different, as described in your links:
DNS-over-HTTP/3 has the overhead of HTTP but uses the QUIC transport for its features. Port 443, so harder to block.
DNS-over-QUIC uses QUIC directly. Port 853, easier to block.
443 udp - uncommon so easy to block
No, that's not ideal, as you would block HTTP/3 which is where things are heading.
Nice but unlikely to hit 100% any time soon.
For exemple corporate traffic is behind http proxies that don't support udp.
So I'm sure tcp 443 will still be used for backwards compatibility for at least a decade so you can block udp 443 and get 99% the access.
curl has experimental support: https://curl.se/docs/http3.html
Still, if someone wants to work on creating a Makefile to build all the dependencies, I'd welcome PR.
Perhaps I'm missing some important point, but this raises a few questions. I'll start with just one:
What's being requested here? That an OpenWRT router-based resolver/forwarder accept DNS-over-HTTP/3 requests from local clients? That it accept old-school port 53 requests and upstream them as DNS-over-HTTP/3?