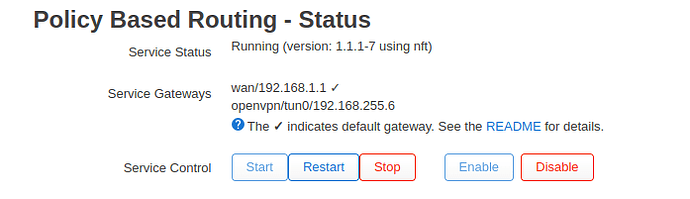
In my country, I cannot access medium.com. As a developer, I try to access medium via OpenVPN and normal websites using wan (using Policy Based Routing).
I tested with whoer.net, and it still has a VPN IP, but I still cannot access to medium.
I just think that It is similar to connecting to OpenVPN on my phone, I can access blocked websites
where did I do wrong?
Here are some images (Newbie cannot post more than one image)
https://ibb.co/P1JCwYx
https://ibb.co/yB14D6V
https://ibb.co/9G8VTSY
https://ibb.co/0mLMqP3
After some research, I think that I got DNS leak (checked on https://dnsleaktest.com/), but I still have not resolved this problem ![]()
Here is my current config
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd35:d028:6e7f::/48'
option packet_steering '1'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.10.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
option dns_metric '10'
option peerdns '0'
list dns '8.8.8.8'
list dns '1.1.1.1'
list dns '8.8.4.4'
list dns '1.0.0.1'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
option peerdns '0'
list dns '2001:4860:4860::8888'
list dns '2001:4860:4860::8844'
config interface 'openvpn'
option proto 'none'
option device 'tun0'
/etc/config/pbr
config pbr 'config'
option enabled '1'
option verbosity '2'
option strict_enforcement '1'
option resolver_set 'none'
option ipv6_enabled '0'
list ignored_interface 'vpnserver'
list ignored_interface 'wgserver'
option boot_timeout '30'
option rule_create_option 'add'
option procd_reload_delay '1'
option webui_show_ignore_target '0'
list webui_supported_protocol 'all'
list webui_supported_protocol 'tcp'
list webui_supported_protocol 'udp'
list webui_supported_protocol 'tcp udp'
list webui_supported_protocol 'icmp'
config include
option path '/usr/share/pbr/pbr.user.aws'
option enabled '0'
config include
option path '/usr/share/pbr/pbr.user.netflix'
option enabled '0'
config policy
option name 'Plex/Emby Local Server'
option interface 'wan'
option src_port '8096 8920 32400'
option enabled '0'
config policy
option name 'Plex/Emby Remote Servers'
option interface 'wan'
option dest_addr 'plex.tv my.plexapp.com emby.media app.emby.media tv.emby.media'
option enabled '0'
config policy
option name 'Domains using openvpn'
option dest_addr 'whoer.net medium.com dnsleaktest.com ipleak.net'
option interface 'openvpn'
/etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
config zone
option name 'openvpn'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'openvpn'
option masq '1'
config forwarding
option src 'lan'
option dest 'openvpn'
/etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option filter_aaaa '0'
option filter_a '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
Note:
gateway in pbr: 192.168.1.1 is the main router connected directly with the ISP.
I don't understand these can you help me check the problem?
Thank you very much. I took two days with this stuck ![]()
ip address show; ip route show table all
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1504 qdisc mq state UP group default qlen 1000
link/ether 50:64:2b:12:30:b4 brd ff:ff:ff:ff:ff:ff
inet6 fe80::5264:2bff:fe12:30b4/64 scope link
valid_lft forever preferred_lft forever
3: wan@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 50:64:2b:12:30:b3 brd ff:ff:ff:ff:ff:ff
inet 192.168.0.222/24 brd 192.168.0.255 scope global wan
valid_lft forever preferred_lft forever
inet6 fd85:26ed:1eab:0:5264:2bff:fe12:30b3/64 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fd85:26ed:1eab::9d2/128 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fe80::5264:2bff:fe12:30b3/64 scope link
valid_lft forever preferred_lft forever
4: lan2@eth0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue master br-lan state LOWERLAYERDOWN group default qlen 1000
link/ether 50:64:2b:12:30:b4 brd ff:ff:ff:ff:ff:ff
5: lan1@eth0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue master br-lan state LOWERLAYERDOWN group default qlen 1000
link/ether 50:64:2b:12:30:b4 brd ff:ff:ff:ff:ff:ff
8: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 50:64:2b:12:30:b4 brd ff:ff:ff:ff:ff:ff
inet 192.168.10.1/24 brd 192.168.10.255 scope global br-lan
valid_lft forever preferred_lft forever
inet6 fd85:26ed:1eab:4::1/62 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fd35:d028:6e7f::1/60 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fe80::5264:2bff:fe12:30b4/64 scope link
valid_lft forever preferred_lft forever
9: phy0-ap0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP group default qlen 1000
link/ether 50:64:2b:12:30:b5 brd ff:ff:ff:ff:ff:ff
inet6 fe80::5264:2bff:fe12:30b5/64 scope link
valid_lft forever preferred_lft forever
10: phy1-ap0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP group default qlen 1000
link/ether 50:64:2b:12:30:b6 brd ff:ff:ff:ff:ff:ff
inet6 fe80::5264:2bff:fe12:30b6/64 scope link
valid_lft forever preferred_lft forever
11: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN group default qlen 500
link/none
inet 192.168.255.6 peer 192.168.255.5/32 scope global tun0
valid_lft forever preferred_lft forever
inet6 fe80::1686:d522:2235:c76a/64 scope link stable-privacy
valid_lft forever preferred_lft forever
default via 192.168.0.1 dev wan table pbr_wan
192.168.10.0/24 dev br-lan table pbr_wan proto kernel scope link src 192.168.10.1
default via 192.168.255.6 dev tun0 table pbr_openvpn
192.168.10.0/24 dev br-lan table pbr_openvpn proto kernel scope link src 192.168.10.1
default via 192.168.0.1 dev wan proto static src 192.168.0.222
192.168.0.0/24 dev wan proto kernel scope link src 192.168.0.222
192.168.10.0/24 dev br-lan proto kernel scope link src 192.168.10.1
192.168.255.5 dev tun0 proto kernel scope link src 192.168.255.6
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
local 192.168.0.222 dev wan table local proto kernel scope host src 192.168.0.222
broadcast 192.168.0.255 dev wan table local proto kernel scope link src 192.168.0.222
local 192.168.10.1 dev br-lan table local proto kernel scope host src 192.168.10.1
broadcast 192.168.10.255 dev br-lan table local proto kernel scope link src 192.168.10.1
local 192.168.255.6 dev tun0 table local proto kernel scope host src 192.168.255.6
fd35:d028:6e7f::/64 dev br-lan proto static metric 1024 pref medium
unreachable fd35:d028:6e7f::/48 dev lo proto static metric 2147483647 pref medium
fd85:26ed:1eab::/48 from fd85:26ed:1eab::9d2 via fe80::fa1a:67ff:fe88:6651 dev wan proto static metric 512 pref medium
fd85:26ed:1eab::/48 from fd85:26ed:1eab::/64 via fe80::fa1a:67ff:fe88:6651 dev wan proto static metric 512 pref medium
fd85:26ed:1eab::/48 from fd85:26ed:1eab:4::/62 via fe80::fa1a:67ff:fe88:6651 dev wan proto static metric 512 pref medium
fd85:26ed:1eab::/64 dev wan proto static metric 256 pref medium
unreachable fd85:26ed:1eab::/64 dev lo proto static metric 2147483647 pref medium
fd85:26ed:1eab:4::/64 dev br-lan proto static metric 1024 pref medium
unreachable fd85:26ed:1eab:4::/62 dev lo proto static metric 2147483647 pref medium
fe80::/64 dev eth0 proto kernel metric 256 pref medium
fe80::/64 dev phy0-ap0 proto kernel metric 256 pref medium
fe80::/64 dev br-lan proto kernel metric 256 pref medium
fe80::/64 dev phy1-ap0 proto kernel metric 256 pref medium
fe80::/64 dev wan proto kernel metric 256 pref medium
fe80::/64 dev tun0 proto kernel metric 256 pref medium
local ::1 dev lo table local proto kernel metric 0 pref medium
anycast fd35:d028:6e7f:: dev br-lan table local proto kernel metric 0 pref medium
local fd35:d028:6e7f::1 dev br-lan table local proto kernel metric 0 pref medium
anycast fd85:26ed:1eab:: dev wan table local proto kernel metric 0 pref medium
local fd85:26ed:1eab::9d2 dev wan table local proto kernel metric 0 pref medium
local fd85:26ed:1eab:0:5264:2bff:fe12:30b3 dev wan table local proto kernel metric 0 pref medium
anycast fd85:26ed:1eab:4:: dev br-lan table local proto kernel metric 0 pref medium
local fd85:26ed:1eab:4::1 dev br-lan table local proto kernel metric 0 pref medium
anycast fe80:: dev eth0 table local proto kernel metric 0 pref medium
anycast fe80:: dev br-lan table local proto kernel metric 0 pref medium
anycast fe80:: dev phy0-ap0 table local proto kernel metric 0 pref medium
anycast fe80:: dev phy1-ap0 table local proto kernel metric 0 pref medium
anycast fe80:: dev wan table local proto kernel metric 0 pref medium
anycast fe80:: dev tun0 table local proto kernel metric 0 pref medium
local fe80::1686:d522:2235:c76a dev tun0 table local proto kernel metric 0 pref medium
local fe80::5264:2bff:fe12:30b3 dev wan table local proto kernel metric 0 pref medium
local fe80::5264:2bff:fe12:30b4 dev eth0 table local proto kernel metric 0 pref medium
local fe80::5264:2bff:fe12:30b4 dev br-lan table local proto kernel metric 0 pref medium
local fe80::5264:2bff:fe12:30b5 dev phy0-ap0 table local proto kernel metric 0 pref medium
local fe80::5264:2bff:fe12:30b6 dev phy1-ap0 table local proto kernel metric 0 pref medium
multicast ff00::/8 dev eth0 table local proto kernel metric 256 pref medium
multicast ff00::/8 dev br-lan table local proto kernel metric 256 pref medium
multicast ff00::/8 dev phy0-ap0 table local proto kernel metric 256 pref medium
multicast ff00::/8 dev phy1-ap0 table local proto kernel metric 256 pref medium
multicast ff00::/8 dev wan table local proto kernel metric 256 pref medium
multicast ff00::/8 dev tun0 table local proto kernel metric 256 pref medium
ip rule show; ip -6 rule show; nft list ruleset
0: from all lookup local
30000: from all fwmark 0x10000/0xff0000 lookup pbr_wan
30001: from all fwmark 0x20000/0xff0000 lookup pbr_openvpn
32766: from all lookup main
32767: from all lookup default
0: from all lookup local
32766: from all lookup main
4200000000: from fd85:26ed:1eab:4::1/62 iif br-lan unreachable
table inet fw4 {
set pbr_openvpn_4_dst_ip_cfg066ff5 {
type ipv4_addr
flags interval
counter
auto-merge
comment "Domains using openvpn"
elements = { 23.239.16.110 counter packets 0 bytes 0, 95.85.16.212 counter packets 1225 bytes 119003,
104.26.4.133 counter packets 142 bytes 25353, 104.26.5.133 counter packets 0 bytes 0,
127.0.0.1 counter packets 36 bytes 2758, 172.67.74.128 counter packets 0 bytes 0 }
}
chain input {
type filter hook input priority filter; policy drop;
iifname "lo" accept comment "!fw4: Accept traffic from loopback"
ct state established,related accept comment "!fw4: Allow inbound established and related flows"
tcp flags syn / fin,syn,rst,ack jump syn_flood comment "!fw4: Rate limit TCP syn packets"
iifname "br-lan" jump input_lan comment "!fw4: Handle lan IPv4/IPv6 input traffic"
iifname "wan" jump input_wan comment "!fw4: Handle wan IPv4/IPv6 input traffic"
iifname "tun0" jump input_openvpn comment "!fw4: Handle openvpn IPv4/IPv6 input traffic"
jump handle_reject
}
chain forward {
type filter hook forward priority filter; policy drop;
ct state established,related accept comment "!fw4: Allow forwarded established and related flows"
iifname "br-lan" jump forward_lan comment "!fw4: Handle lan IPv4/IPv6 forward traffic"
iifname "wan" jump forward_wan comment "!fw4: Handle wan IPv4/IPv6 forward traffic"
iifname "tun0" jump forward_openvpn comment "!fw4: Handle openvpn IPv4/IPv6 forward traffic"
jump handle_reject
}
chain output {
type filter hook output priority filter; policy accept;
oifname "lo" accept comment "!fw4: Accept traffic towards loopback"
ct state established,related accept comment "!fw4: Allow outbound established and related flows"
oifname "br-lan" jump output_lan comment "!fw4: Handle lan IPv4/IPv6 output traffic"
oifname "wan" jump output_wan comment "!fw4: Handle wan IPv4/IPv6 output traffic"
oifname "tun0" jump output_openvpn comment "!fw4: Handle openvpn IPv4/IPv6 output traffic"
}
chain prerouting {
type filter hook prerouting priority filter; policy accept;
iifname "br-lan" jump helper_lan comment "!fw4: Handle lan IPv4/IPv6 helper assignment"
}
chain handle_reject {
meta l4proto tcp reject with tcp reset comment "!fw4: Reject TCP traffic"
reject comment "!fw4: Reject any other traffic"
}
chain syn_flood {
limit rate 25/second burst 50 packets return comment "!fw4: Accept SYN packets below rate-limit"
drop comment "!fw4: Drop excess packets"
}
chain input_lan {
jump accept_from_lan
}
chain output_lan {
jump accept_to_lan
}
chain forward_lan {
jump accept_to_wan comment "!fw4: Accept lan to wan forwarding"
jump accept_to_openvpn comment "!fw4: Accept lan to openvpn forwarding"
jump accept_to_lan
}
chain helper_lan {
}
chain accept_from_lan {
iifname "br-lan" counter packets 948 bytes 78778 accept comment "!fw4: accept lan IPv4/IPv6 traffic"
}
chain accept_to_lan {
oifname "br-lan" counter packets 5 bytes 920 accept comment "!fw4: accept lan IPv4/IPv6 traffic"
}
chain input_wan {
meta nfproto ipv4 udp dport 68 counter packets 0 bytes 0 accept comment "!fw4: Allow-DHCP-Renew"
icmp type echo-request counter packets 0 bytes 0 accept comment "!fw4: Allow-Ping"
meta nfproto ipv4 meta l4proto igmp counter packets 0 bytes 0 accept comment "!fw4: Allow-IGMP"
meta nfproto ipv6 udp dport 546 counter packets 0 bytes 0 accept comment "!fw4: Allow-DHCPv6"
ip6 saddr fe80::/10 icmpv6 type . icmpv6 code { mld-listener-query . no-route, mld-listener-report . no-route, mld-listener-done . no-route, mld2-listener-report . no-route } counter packets 0 bytes 0 accept comment "!fw4: Allow-MLD"
icmpv6 type { destination-unreachable, time-exceeded, echo-request, echo-reply, nd-router-solicit, nd-router-advert } limit rate 1000/second counter packets 2 bytes 320 accept comment "!fw4: Allow-ICMPv6-Input"
icmpv6 type . icmpv6 code { packet-too-big . no-route, parameter-problem . no-route, nd-neighbor-solicit . no-route, nd-neighbor-advert . no-route, parameter-problem . admin-prohibited } limit rate 1000/second counter packets 58 bytes 3976 accept comment "!fw4: Allow-ICMPv6-Input"
jump reject_from_wan
}
chain output_wan {
jump accept_to_wan
}
chain forward_wan {
icmpv6 type { destination-unreachable, time-exceeded, echo-request, echo-reply } limit rate 1000/second counter packets 0 bytes 0 accept comment "!fw4: Allow-ICMPv6-Forward"
icmpv6 type . icmpv6 code { packet-too-big . no-route, parameter-problem . no-route, parameter-problem . admin-prohibited } limit rate 1000/second counter packets 0 bytes 0 accept comment "!fw4: Allow-ICMPv6-Forward"
meta l4proto esp counter packets 0 bytes 0 jump accept_to_lan comment "!fw4: Allow-IPSec-ESP"
udp dport 500 counter packets 0 bytes 0 jump accept_to_lan comment "!fw4: Allow-ISAKMP"
jump reject_to_wan
}
chain accept_to_wan {
meta nfproto ipv4 oifname "wan" ct state invalid counter packets 5 bytes 200 drop comment "!fw4: Prevent NAT leakage"
oifname "wan" counter packets 1551 bytes 296828 accept comment "!fw4: accept wan IPv4/IPv6 traffic"
}
chain reject_from_wan {
iifname "wan" counter packets 20 bytes 2447 jump handle_reject comment "!fw4: reject wan IPv4/IPv6 traffic"
}
chain reject_to_wan {
oifname "wan" counter packets 0 bytes 0 jump handle_reject comment "!fw4: reject wan IPv4/IPv6 traffic"
}
chain input_openvpn {
jump reject_from_openvpn
}
chain output_openvpn {
jump accept_to_openvpn
}
chain forward_openvpn {
jump reject_to_openvpn
}
chain accept_to_openvpn {
meta nfproto ipv4 oifname "tun0" ct state invalid counter packets 0 bytes 0 drop comment "!fw4: Prevent NAT leakage"
oifname "tun0" counter packets 16 bytes 2178 accept comment "!fw4: accept openvpn IPv4/IPv6 traffic"
}
chain reject_from_openvpn {
iifname "tun0" counter packets 0 bytes 0 jump handle_reject comment "!fw4: reject openvpn IPv4/IPv6 traffic"
}
chain reject_to_openvpn {
oifname "tun0" counter packets 0 bytes 0 jump handle_reject comment "!fw4: reject openvpn IPv4/IPv6 traffic"
}
chain dstnat {
type nat hook prerouting priority dstnat; policy accept;
}
chain srcnat {
type nat hook postrouting priority srcnat; policy accept;
oifname "wan" jump srcnat_wan comment "!fw4: Handle wan IPv4/IPv6 srcnat traffic"
oifname "tun0" jump srcnat_openvpn comment "!fw4: Handle openvpn IPv4/IPv6 srcnat traffic"
}
chain srcnat_wan {
meta nfproto ipv4 masquerade comment "!fw4: Masquerade IPv4 wan traffic"
}
chain srcnat_openvpn {
meta nfproto ipv4 masquerade comment "!fw4: Masquerade IPv4 openvpn traffic"
}
chain raw_prerouting {
type filter hook prerouting priority raw; policy accept;
}
chain raw_output {
type filter hook output priority raw; policy accept;
}
chain mangle_prerouting {
type filter hook prerouting priority mangle; policy accept;
jump pbr_prerouting comment "Jump into pbr prerouting chain"
}
chain mangle_postrouting {
type filter hook postrouting priority mangle; policy accept;
jump pbr_postrouting comment "Jump into pbr postrouting chain"
}
chain mangle_input {
type filter hook input priority mangle; policy accept;
jump pbr_input comment "Jump into pbr input chain"
}
chain mangle_output {
type route hook output priority mangle; policy accept;
jump pbr_output comment "Jump into pbr output chain"
}
chain mangle_forward {
type filter hook forward priority mangle; policy accept;
iifname "wan" tcp flags syn tcp option maxseg size set rt mtu comment "!fw4: Zone wan IPv4/IPv6 ingress MTU fixing"
oifname "wan" tcp flags syn tcp option maxseg size set rt mtu comment "!fw4: Zone wan IPv4/IPv6 egress MTU fixing"
jump pbr_forward comment "Jump into pbr forward chain"
}
chain pbr_forward {
}
chain pbr_input {
}
chain pbr_output {
}
chain pbr_prerouting {
ip daddr @pbr_openvpn_4_dst_ip_cfg066ff5 goto pbr_mark_0x020000 comment "Domains using openvpn"
}
chain pbr_postrouting {
}
chain pbr_mark_0x010000 {
counter packets 0 bytes 0 meta mark set meta mark & 0xff01ffff | 0x00010000
return
}
chain pbr_mark_0x020000 {
counter packets 1403 bytes 147114 meta mark set meta mark & 0xff02ffff | 0x00020000
return
}
}
head -v -n -0 /etc/resolv.* /tmp/resolv.* /tmp/resolv.*/*
==> /etc/resolv.conf <==
search lan
nameserver 127.0.0.1
nameserver ::1
==> /tmp/resolv.conf <==
search lan
nameserver 127.0.0.1
nameserver ::1
==> /tmp/resolv.conf.d <==
head: /tmp/resolv.conf.d: I/O error
==> /tmp/resolv.conf.d/resolv.conf.auto <==
# Interface wan
nameserver 192.168.0.1
search lan
# Interface wan6
nameserver fd85:26ed:1eab::1
after changing DHCP option 6, I still got DNS leak ![]()
Did you reboot your clients and checked that they have the DNS servers you have set and not the router as DNS server?
I use a different solution to use a hotplug script to replace the DNS servers with the OpenVPN pushed or WireGuard DNS servers after the interface is up and also make a route through the VPN for said servers.
Drawback is that all clients now use a DNS server via the tunnel, but advantage is that you still have local name resolution and are sure there is no DNS leak ![]()
Can you share your solution? Only DNS query will go to the DNS server of VPN tunnel is okay
My solution is based on the link of @vgaetera but it also makes sure that the used DNS servers are routed via the VPN ![]()
But it is a Work in Progress
@egc @vgaetera I tried both solutions, but It is not working, it may be caused by uci -q get dhcp.@dnsmasq[0].resolvfile return empty.
In the solution of @egc, it says: Sun Nov 12 16:40:15 2023 user.warn ovpn-up-update-resolv-5[24166]: No VPN DNS servers found, using default servers!
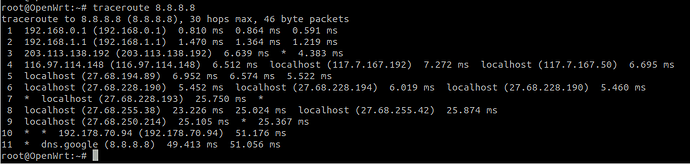
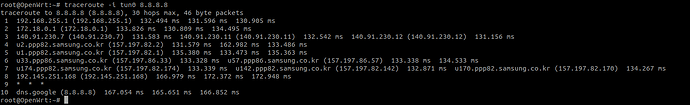
Give output of traceroute 8.8.8.8
It looks like your VPN server does not push DNS server are you using your own VPN server?
All commercial VPN servers should push DNS servers
No problem you can just set DNS server to use in the openvpn.conf file with:
dhcp-option DNS 9.9.9.9
If everything works you should see 9.9.9.9 used as DNS server, the log should show:
"Exclusively using OpenVPN DNS server(s) from $VPN_RESOLVF"
and ip ro should show a route for 9.9.9.9 via the VPN
Note some browser will use their own DNS servers so you might want to read up on DNS hijacking .
Sorry, the idea is to determine interface, not to specify it. But from your output conclusion is evident: 'default' route is via wan, not tun.
Yes, I just want to route some blocked websites via OpenVPN, other websites are still accessible via Wan, default is wan
What is 'DNS leak' in your case, and what is your aim?
I own my VPN server run in docker(https://github.com/kylemanna/docker-openvpn), here is my VPN current config, I see that it has a push DHCP option. I must change to 9.9.9.9 or not ??
I also tried a free OpenVPN server and still got DNS leaks:frowning:
openvpn.conf
server 192.168.255.0 255.255.255.0
verb 3
key /etc/openvpn/pki/private/public_ip.key
ca /etc/openvpn/pki/ca.crt
cert /etc/openvpn/pki/issued/public_ip.crt
dh /etc/openvpn/pki/dh.pem
tls-auth /etc/openvpn/pki/ta.key
key-direction 0
keepalive 10 60
persist-key
persist-tun
proto udp
# Rely on Docker to do port mapping, internally always 1194
port 1194
dev tun0
status /tmp/openvpn-status.log
user nobody
group nogroup
comp-lzo no
### Route Configurations Below
route 192.168.254.0 255.255.255.0
### Push Configurations Below
push "block-outside-dns"
push "dhcp-option DNS 8.8.8.8"
push "dhcp-option DNS 8.8.4.4"
push "comp-lzo no"
OK, but OpenVPN-client is running on the router with OpenWRT?