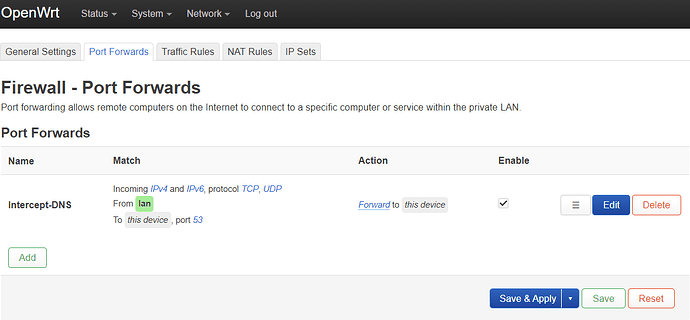
I'm trying to intercept the DNS traffic on the LAN on port 53:
However when I set on the computer a DNS server 1.1.1.1 or 8.8.8.8 then the DNS doesn't get intercepted.
How to solve this?
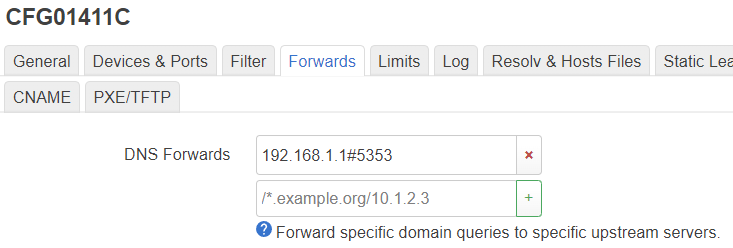
I'm using AdGuard Home on port 5353.
I followed these guides:
https://openwrt.org/docs/guide-user/services/dns/adguard-home
The guide on OpenWrt official website broke the opkg update functinality so I've used the other guide.
My router: GL.iNet GL-MT6000
OpenWrt version: 23.05.4
Yes the firewall rule is there.
But it still doesn't work.
DNS forwarded:
I suspect firewall doesn't work at all. Is there a quick test to check?
Delete your DNS forward. Enable query logging in dnsmasq configuration.
Run on your PC nslookup openwrt.org. 8.8.8.8 and see what is in the router log.
Which forward? The firewall forward or the DNS forward to port 5353?
Where I enable it in Luci?
I got:
Server: UnKnown
Address: 8.8.8.8
*** UnKnown can't find openwrt.org: Query refused
Look at your own screenshot, it is on the Log tab.
It's very very strange. So with the nslookup command output I know the firewall rule is working, but then how is Chrome successfully circumvent my local DNS? (It's only when a public DNS is set)
DoH enabled in the browser ?
You are right. It was enabled by default. So is it using port 443? But how did it work correctly on my TP-Link? With my TP-Link I blocked port 53 on all LAN local ips except the Raspberry Pi running Pi-hole...
What to do?
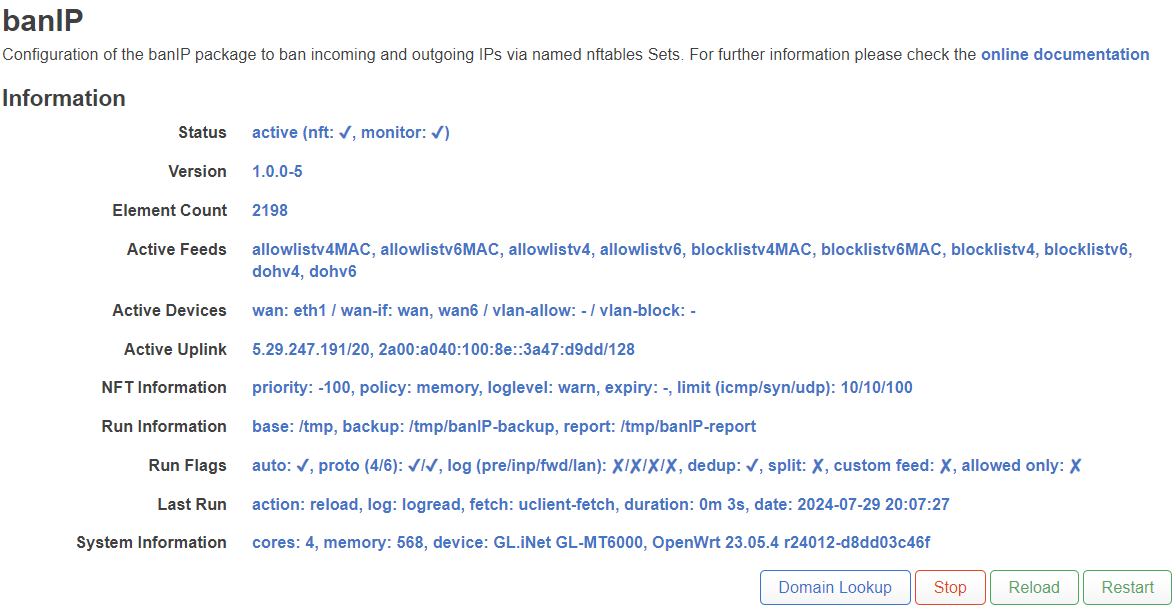
To block DoH, you need to create an ipset rule (or install banip) and import a public DoH server IP list.
So I can confirm that if I disable DoH in Chrome, the AdGuard Home is working correctly.
I installed banip and used the DoH list, but Chrome is still able to successfully obtain the Ip address of the domain.
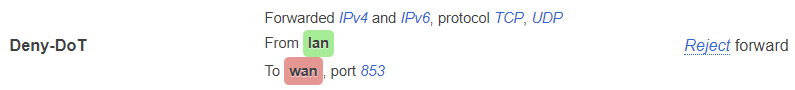
I also have a blocking rule for port 853:
What's going on here?
banip seems to be working?
So if I try to connect to https://1.1.1.1/ I get connection refused so... That means banip is working.
EDIT: I tried with 8.8.8.8 and got blocked.
But with 1.1.1.1 Chrome is able to circumvent the block.
Could be that on 1.1.1.1 there is some kind of new protocol, maybe UDP Quic (http3) ?
Then you need to tcpdump the browser traffic.
With Cloudflare 1.1.1.1 selected in Chrome it talks to chrome.cloudflare-dns.com, so you can try blocking that name or the IP addresses associated with it.
1 Like
I've installed Wireshark, it's opening a UDP connection to 2a06:98c1:52::3 (chrome.cloudflare-dns.com).
This IP is already on the list of banip. So ...
Damn!
Are you sure you fw rule includes both ipv6 and ipv4 ?
You can always block the FQDN too.
What rule? Isn't banip automatic?