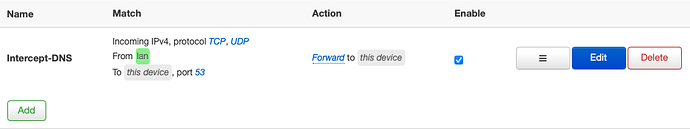
I've come across a few threads but haven't come to a solution to what I'm looking for. I have a Docker install of Pi-hole running on a cloud server. I'm attempting to point my OpenWrt router to this DNS.
Does the Pi-hole setup need to be running locally for this to work?
If the answer to #1 is no, how do I properly point to it on Luci?
1 Like
The CLI instructions differ from that of the LuCI instructions.
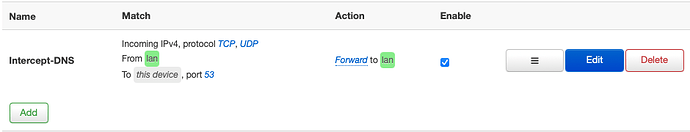
Should it look like this (CLI instructions):
Or like this (LuCI instructions):
1 Like
Yep, the screenshots were incorrect, I removed them.
2 Likes
vgaetera:
DNS redirection
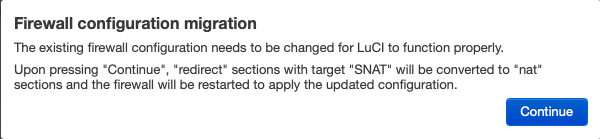
Receiving this on LuCI after following these steps:
Any ideas?
1 Like
Proceed, it should convert the rule to better match the LuCI interface.
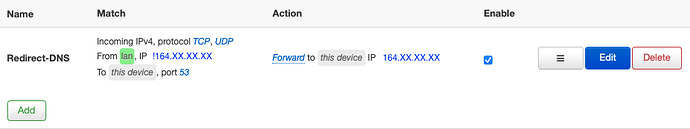
Looks a bit off to me, unless I'm not reading it correctly. However it does seem to be working okay now. No DNS leaks. Will monitor over the next few days. Thank you very much!
1 Like
Wait, you want to redirect traffic to a public IP outside your LAN.
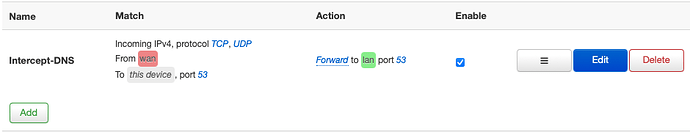
Yes exactly! Here's what the forward looks like now:
My question here is do I need to specify 53 for the internal port?
The instructions do not specify that.
vgaetera:
DNS hijacking
The issue I'm having here is with NAT6, specifically when restarting the firewall:
root@OpenWrt:~# /etc/init.d/firewall restart
Warning: Unable to locate ipset utility, disabling ipset support
* Flushing IPv4 filter table
* Flushing IPv4 nat table
* Flushing IPv4 mangle table
* Flushing IPv6 filter table
* Flushing IPv6 nat table
* Flushing IPv6 mangle table
* Flushing conntrack table ...
* Populating IPv4 filter table
* Rule 'Allow-DHCP-Renew'
* Rule 'Allow-Ping'
* Rule 'Allow-IGMP'
* Rule 'Allow-IPSec-ESP'
* Rule 'Allow-ISAKMP'
* Redirect 'Intercept-DNS'
* Forward 'lan' -> 'wan'
* Zone 'lan'
* Zone 'wan'
* Populating IPv4 nat table
* Redirect 'Intercept-DNS'
* Zone 'lan'
* Zone 'wan'
* Populating IPv4 mangle table
* Zone 'lan'
* Zone 'wan'
* Populating IPv6 filter table
* Rule 'Allow-DHCPv6'
* Rule 'Allow-MLD'
* Rule 'Allow-ICMPv6-Input'
* Rule 'Allow-ICMPv6-Forward'
* Rule 'Allow-IPSec-ESP'
* Rule 'Allow-ISAKMP'
* Forward 'lan' -> 'wan'
* Zone 'lan'
* Zone 'wan'
* Populating IPv6 nat table
Warning: fw3_ipt_rule_append(): Can't find target 'prerouting_lan_rule'
Warning: fw3_ipt_rule_append(): Can't find target 'postrouting_lan_rule'
Warning: fw3_ipt_rule_append(): Can't find target 'prerouting_wan_rule'
Warning: fw3_ipt_rule_append(): Can't find target 'postrouting_wan_rule'
Warning: fw3_ipt_rule_append(): Can't find target 'prerouting_rule'
Warning: fw3_ipt_rule_append(): Can't find target 'postrouting_rule'
* Zone 'lan'
* Zone 'wan'
* Populating IPv6 mangle table
* Zone 'lan'
* Zone 'wan'
* Set tcp_ecn to off
* Set tcp_syncookies to on
* Set tcp_window_scaling to on
* Running script '/etc/firewall.user'
* Running script '/etc/firewall.nat6'
iptables-save: unrecognized option: e
Look at manual page `iptables-save.8' for more information.
! Failed with exit code 1
1 Like
It looks like you've missed a symbol while copy-pasting.from the first cat to the EOF under it .entire block of code for NAT6 setup .
Looks like you were right, I must've missed something. Copied the entire block and got a better outcome besides the warnings about not finding targets:
root@OpenWrt:~# cat << "EOF" > /etc/firewall.nat6
> iptables-save -t nat \
> | sed -e "/\s[DS]NAT\s/d;/\sMASQUERADE$/d;/\s--match-set\s\S*/s//\06/" \
> | ip6tables-restore -T nat
> EOF
root@OpenWrt:~# cat << "EOF" >> /etc/sysupgrade.conf
> /etc/firewall.nat6
> EOF
root@OpenWrt:~# uci -q delete firewall.nat6
root@OpenWrt:~# uci set firewall.nat6="include"
root@OpenWrt:~# uci set firewall.nat6.path="/etc/firewall.nat6"
root@OpenWrt:~# uci set firewall.nat6.reload="1"
root@OpenWrt:~# uci commit firewall
root@OpenWrt:~# /etc/init.d/firewall restart
Warning: Unable to locate ipset utility, disabling ipset support
* Flushing IPv4 filter table
* Flushing IPv4 nat table
* Flushing IPv4 mangle table
* Flushing IPv6 filter table
* Flushing IPv6 nat table
* Flushing IPv6 mangle table
* Flushing conntrack table ...
* Populating IPv4 filter table
* Rule 'Allow-DHCP-Renew'
* Rule 'Allow-Ping'
* Rule 'Allow-IGMP'
* Rule 'Allow-IPSec-ESP'
* Rule 'Allow-ISAKMP'
* Redirect 'Intercept-DNS'
* Forward 'lan' -> 'wan'
* Zone 'lan'
* Zone 'wan'
* Populating IPv4 nat table
* Redirect 'Intercept-DNS'
* Zone 'lan'
* Zone 'wan'
* Populating IPv4 mangle table
* Zone 'lan'
* Zone 'wan'
* Populating IPv6 filter table
* Rule 'Allow-DHCPv6'
* Rule 'Allow-MLD'
* Rule 'Allow-ICMPv6-Input'
* Rule 'Allow-ICMPv6-Forward'
* Rule 'Allow-IPSec-ESP'
* Rule 'Allow-ISAKMP'
* Forward 'lan' -> 'wan'
* Zone 'lan'
* Zone 'wan'
* Populating IPv6 nat table
Warning: fw3_ipt_rule_append(): Can't find target 'prerouting_lan_rule'
Warning: fw3_ipt_rule_append(): Can't find target 'postrouting_lan_rule'
Warning: fw3_ipt_rule_append(): Can't find target 'prerouting_wan_rule'
Warning: fw3_ipt_rule_append(): Can't find target 'postrouting_wan_rule'
Warning: fw3_ipt_rule_append(): Can't find target 'prerouting_rule'
Warning: fw3_ipt_rule_append(): Can't find target 'postrouting_rule'
* Zone 'lan'
* Zone 'wan'
* Populating IPv6 mangle table
* Zone 'lan'
* Zone 'wan'
* Set tcp_ecn to off
* Set tcp_syncookies to on
* Set tcp_window_scaling to on
* Running script '/etc/firewall.user'
* Running script '/etc/firewall.nat6'
Also, any suggestion as to whether 53 should be used as the internal port?
1 Like
No need, the internal port is the same as the external one by default.
Great,
You can verify that it works like this:
iptables-save -c -t nat | grep -e Intercept-DNS
ip6tables-save -c -t nat | grep -e Intercept-DNS
Looks good
root@OpenWrt:~# iptables-save -c -t nat | grep -e Intercept-DNS
[0:0] -A zone_lan_prerouting -p tcp -m tcp --dport 53 -m comment --comment "!fw3: Intercept-DNS" -j REDIRECT --to-ports 53
[2789:191130] -A zone_lan_prerouting -p udp -m udp --dport 53 -m comment --comment "!fw3: Intercept-DNS" -j REDIRECT --to-ports 53
root@OpenWrt:~# ip6tables-save -c -t nat | grep -e Intercept-DNS
[4:336] -A zone_lan_prerouting -p tcp -m tcp --dport 53 -m comment --comment "!fw3: Intercept-DNS" -j REDIRECT --to-ports 53
[1846:166766] -A zone_lan_prerouting -p udp -m udp --dport 53 -m comment --comment "!fw3: Intercept-DNS" -j REDIRECT --to-ports 53
1 Like
vgaetera:
DNS redirection
Do I need to follow instructions for DNS redirection also?
No, that part is for redirecting to a local DNS server located in the same LAN.
1 Like
system
March 20, 2021, 11:14pm
17
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.