lmc
February 7, 2024, 11:49am
1
Hello all,
I tried to find a precise answer by myself but after an amount of time searching online and reading documentation here I am.
dnsmasq, providing only dhcp as the DNS port is set to zero
Unbound DNS as a DNS server for the plan.
So, with that in mind and without going into the details, dnsmasq is working perfectly as DHCP server and unbound is working perfectly as DNS server.
But, I am interested to find out an answer for the next questions:
Is dnsmasq adding a static DNS<>host entry somewhere that could be read by unbound to resolve A and PTR records associated to the hosts in the lan based on the DHCP information and hostname used there?
If no....
Installed:
# opkg list-installed | egrep -i unbound
libunbound - 1.17.1-1
luci-app-unbound - git-23.338.81752-6612893
luci-i18n-unbound-en - git-24.034.32907-d24e3be
unbound-anchor - 1.17.1-1
unbound-checkconf - 1.17.1-1
unbound-control - 1.17.1-1
unbound-daemon - 1.17.1-1
unbound-host - 1.17.1-1
root@OpenWrt:/etc# opkg list-installed | egrep -i dns
dnsmasq - 2.86-16
rpcd-mod-rrdns - 20170710
I am missing something but I don't know exactly what.
You have 3 documented choices from the Unbound package README (How to: Integrate with DHCP):
# Unbound Recursive DNS Server with UCI
<!-- markdownlint-disable -->
## Unbound Description
[Unbound](https://www.unbound.net/) is a validating, recursive, and caching DNS resolver. The C implementation of Unbound is developed and maintained by [NLnet Labs](https://www.nlnetlabs.nl/). It is based on ideas and algorithms taken from a java prototype developed by Verisign labs, Nominet, Kirei and ep.net. Unbound is designed as a set of modular components, so that also DNSSEC (secure DNS) validation and stub-resolvers (that do not run as a server, but are linked into an application) are easily possible.
## Package Overview
OpenWrt default build uses [dnsmasq](http://www.thekelleys.org.uk/dnsmasq/docs/dnsmasq-man.html) for DNS forwarding and DHCP. With a forward only resolver, dependence on the upstream recursors may be cause for concern. They are often provided by the ISP, and some users have switched to public DNS providers. Either way may result in problems due to performance, "snoop-vertising", hijacking (MiM), and other causes. Running a recursive resolver or resolver capable of TLS may be a solution.
Unbound may be useful on consumer grade embedded hardware. It is fully DNSSEC and TLS capable. It is _intended_ to be a recursive resolver only. NLnet Labs [NSD](https://www.nlnetlabs.nl/projects/nsd/) is _intended_ for the authoritative task. This is different than [ISC Bind](https://www.isc.org/downloads/bind/) and its inclusive functions. Unbound configuration effort and memory consumption may be easier to control. A consumer could have their own recursive resolver with 8/64 MB router, and remove potential issues from forwarding resolvers outside of their control.
This package builds on Unbounds capabilities with OpenWrt UCI. Not every Unbound option is in UCI, but rather, UCI simplifies the combination of related options. Unbounds native options are bundled and balanced within a smaller set of choices. Options include resources, DNSSEC, access control, and some TTL tweaking. The UCI also provides an escape option and works at the raw `unbound.conf` level.
## HOW TO: Ad Blocking
The UCI scripts will work with [net/adblock](https://github.com/openwrt/packages/blob/master/net/adblock/files/README.md), if it is installed and enabled. Its all detected and integrated automatically. In brief, the adblock scripts create distinct local-zone files that are simply included in the unbound conf file during UCI generation. If you don't want this, then disable adblock or reconfigure adblock to not send these files to Unbound.
A few tweaks may be needed to enhance the realiability and effectiveness. Ad Block option for delay time may need to be set for upto one minute (adb_triggerdelay), because of boot up race conditions with interfaces calling Unbound restarts. Also many smart devices (TV, microwave, or refigerator) will also use public DNS servers either as a bypass or for certain connections in general. If you wish to force exclusive DNS to your router, then you will need a firewall rule for example:
**/etc/config/firewall**:
```
show original
I would personally choose the parallel dnsmasq option.
lmc
February 7, 2024, 1:14pm
3
Exactly, I was using and testing Parallel dnsmasq.setup
Now, with dnsmasq running on 5353 I go to another computer in the same lan and I was doing nslookup with "set port=5353" but... here is windows...
C:\Windows\System32>nslookup -port=5353
Default Server: UnKnown
Address: 192.168.14.1
> www.google.com
Server: UnKnown
Address: 192.168.14.1
Non-authoritative answer:
Name: www.google.com
Addresses: 2a00:1450:400b:c02::6a
2a00:1450:400b:c02::69
2a00:1450:400b:c02::93
2a00:1450:400b:c02::63
209.85.203.99
209.85.203.106
209.85.203.147
209.85.203.104
209.85.203.105
209.85.203.103
>
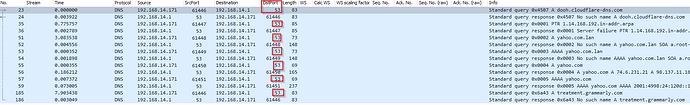
hehe, but here is wireshark...
So basically nslookup with "set port=" or "--port=" does not work, misleading me.
Ok, with that info I can go back to work on the setup. Thanks for the info and the quick response.
system
February 17, 2024, 1:14pm
4
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.