Hi,
thank's for your help.
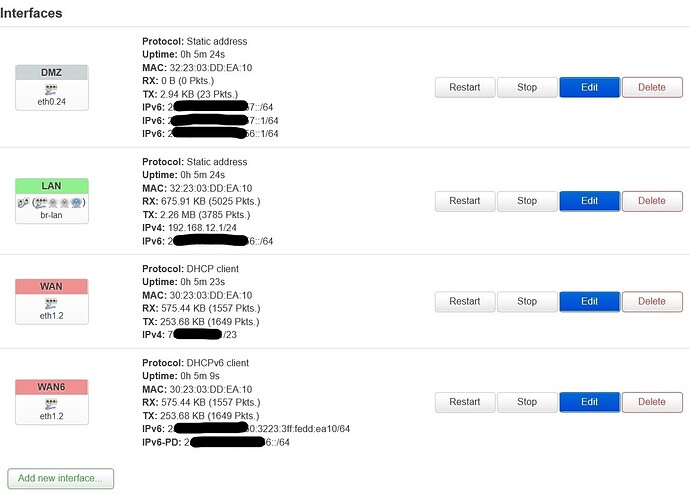
to be able to rollback, i delete everythink link to the DMZ.
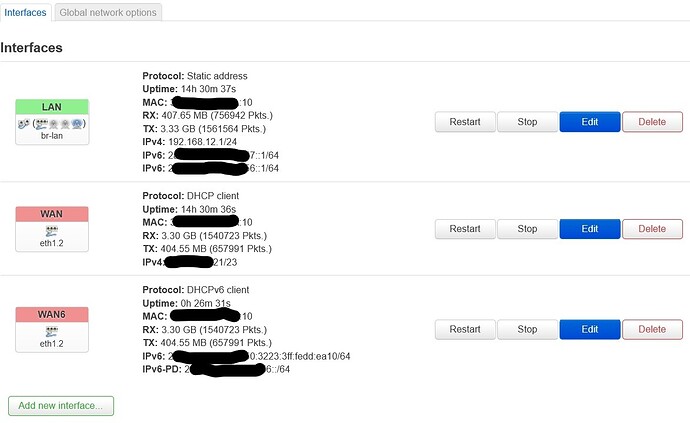
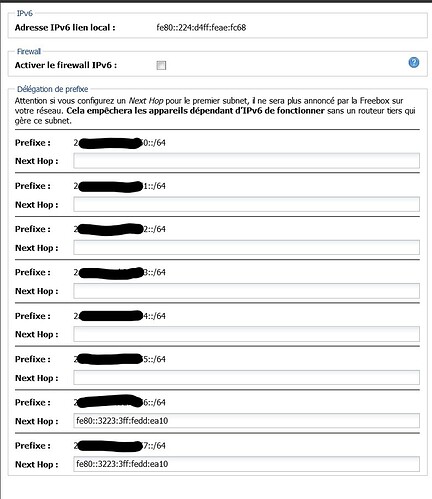
you will find first my current configuration and secondly the configuration after adding the second prefix under Interfaces » WAN6 » Advanced Settings » Custom delegated IPv6-prefix.
and also a screenshots.
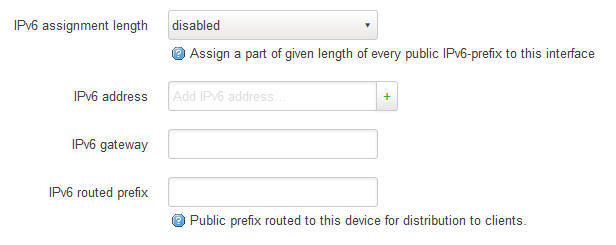
before adding the second prefix
{
"kernel": "4.14.221",
"hostname": "lorien",
"system": "ARMv7 Processor rev 1 (v7l)",
"model": "Linksys WRT3200ACM",
"board_name": "linksys,rango",
"release": {
"distribution": "OpenWrt",
"version": "19.07.7",
"revision": "r11306-c4a6851c72",
"target": "mvebu/cortexa9",
"description": "OpenWrt 19.07.7 r11306-c4a6851c72"
}
}
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '64'
option ipaddr '192.168.12.1'
config interface 'wan'
option ifname 'eth1.2'
option proto 'dhcp'
option peerdns '0'
config interface 'wan6'
option ifname 'eth1.2'
option proto 'dhcpv6'
option reqprefix 'auto'
option reqaddress 'try'
option peerdns '0'
list ip6prefix '2a00:xxx:yyy:zzz6::/64'
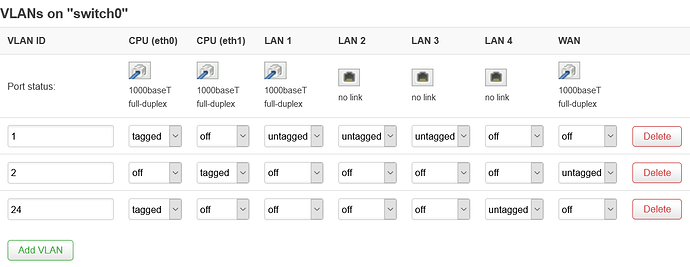
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '1 2 3 5t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6t'
option vid '2'
config route6
option interface 'wan6'
option target '2000::/3'
option gateway 'fe80::f6ca:e5ff:fe4c:58fb'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '0 5t'
option vid '24'
package dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option localservice '1'
option domain 'mydomaine.name'
option local '/mydomaine.name/'
list server '0::1#5453'
list server '127.0.0.1#5453'
option noresolv '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option dhcpv6 'server'
option ra 'server'
option ra_default '1'
option ra_management '2'
list dhcp_option '6,192.168.12.8,192.168.12.1'
list domain 'mydomaine.name'
list dns '2a00:xxx:yyy:zzz6::1208'
list dns '2a00:xxx:yyy:zzz6::1'
option leasetime '12h'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option mac '00:01:01:01:01:B5'
option dns '1'
option name 'moria'
option ip '192.168.12.12'
option hostid '1212'
option duid '000000089bc0b1b500089bc0b1b5'
config host
option mac '00:01:01:01:01:C9'
option dns '1'
option name 'mp620'
option ip '192.168.12.15'
option hostid '1215'
config domain
option name 'lorien'
option ip '2a00:xxx:yyy:zzz6::1'
config domain
option name 'moria'
option ip '2a00:xxx:yyy:zzz6::1212'
config cname
option cname 'ns0.mydomaine.name'
option target 'lorien.mydomaine.name'
config cname
option cname 'ns2.mydomaine.name'
option target 'imladris.mydomaine.name'
config cname
option cname 'nas0.mydomaine.name'
option target 'moria.mydomaine.name'
config host
option mac '00:01:01:01:01:42'
option dns '1'
option name 'imladris'
option hostid '1208'
option ip '192.168.12.8'
option duid '000000000000000000000000009c'
config cname
option cname 'ntp.mydomaine.name'
option target 'lorien.mydomaine.name'
config host
option mac '00:01:01:01:01:87'
option name 'lumbar'
option dns '1'
option ip '192.168.12.4'
option hostid '1204'
option duid '0000000000000000000000000027'
config cname
option cname 'mail.mydomaine.name'
option target 'lumbar.mydomaine.name'
config mxhost
option domain 'mydomaine.name'
option relay 'mail.mydomaine.name'
option pref '10'
config txt-record
config txt-record
config host
option mac '00:01:01:01:01:27'
option dns '1'
option name 'pelargir'
option ip '192.168.12.10'
option duid '000000000000000000000000009f'
option hostid '1210'
config cname
option cname 'photos.mydomaine.name'
option target 'pelargir.mydomaine.name'
config dhcp 'DMZ'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'DMZ'
option ra_management '2'
option ra 'server'
option dhcpv6 'server'
option dynamicdhcp '0'
list domain 'mydomaine.name'
list dns '2a00:xxx:yyy:zzz7::1'
option ra_default '1'
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 state UNKNOWN qlen 1000
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 532
inet6 fe80::3223:3ff:fedd:ea10/64 scope link
valid_lft forever preferred_lft forever
3: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 532
inet6 fe80::3023:3ff:fedd:ea10/64 scope link
valid_lft forever preferred_lft forever
8: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 2a00:xxx:yyy:zzz6::1/64 scope global
valid_lft forever preferred_lft forever
inet6 fe80::3023:3ff:fedd:ea10/64 scope link
valid_lft forever preferred_lft forever
10: eth1.2@eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 2a00:xxx:yyy:zzz0:3223:3ff:fedd:ea10/64 scope global dynamic
valid_lft 86012sec preferred_lft 86012sec
inet6 fe80::3223:3ff:fedd:ea10/64 scope link
valid_lft forever preferred_lft forever
11: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 fe80::3223:3ff:fedd:ea12/64 scope link
valid_lft forever preferred_lft forever
default from 2a00:xxx:yyy:zzz0::/64 via fe80::224:d4ff:feae:fc68 dev eth1.2 metric 512
2a00:xxx:yyy:zzz0::/64 dev eth1.2 metric 256
unreachable 2a00:xxx:yyy:zzz0::/64 dev lo metric 2147483647 error -113
2a00:xxx:yyy:zzz6::/64 dev br-lan metric 1024
unreachable 2a00:xxx:yyy:zzz6::/64 dev lo metric 2147483647 error -113
2000::/3 via fe80::f6ca:e5ff:fe4c:58fb dev eth1.2 metric 1024
fe80::/64 dev eth0 metric 256
fe80::/64 dev eth1.2 metric 256
fe80::/64 dev eth1 metric 256
fe80::/64 dev br-lan metric 256
fe80::/64 dev wlan0 metric 256
local ::1 dev lo table local metric 0
anycast 2a00:xxx:yyy:zzz0:: dev eth1.2 table local metric 0
local 2a00:xxx:yyy:zzz0:3223:3ff:fedd:ea10 dev eth1.2 table local metric 0
anycast 2a00:xxx:yyy:zzz6:: dev br-lan table local metric 0
local 2a00:xxx:yyy:zzz6::1 dev br-lan table local metric 0
anycast fe80:: dev eth1.2 table local metric 0
anycast fe80:: dev eth1 table local metric 0
anycast fe80:: dev eth0 table local metric 0
anycast fe80:: dev br-lan table local metric 0
anycast fe80:: dev wlan0 table local metric 0
local fe80::3023:3ff:fedd:ea10 dev eth0 table local metric 0
local fe80::3023:3ff:fedd:ea10 dev br-lan table local metric 0
local fe80::3223:3ff:fedd:ea10 dev eth1.2 table local metric 0
local fe80::3223:3ff:fedd:ea10 dev eth1 table local metric 0
local fe80::3223:3ff:fedd:ea12 dev wlan0 table local metric 0
ff00::/8 dev eth0 table local metric 256
ff00::/8 dev eth1.2 table local metric 256
ff00::/8 dev eth1 table local metric 256
ff00::/8 dev br-lan table local metric 256
ff00::/8 dev wlan0 table local metric 256
0: from all lookup local
32766: from all lookup main
4200000000: from 2a00:xxx:yyy:zzz6::1/64 iif br-lan lookup unspec unreachable
4200000001: from all iif lo lookup unspec 12
4200000008: from all iif br-lan lookup unspec 12
4200000010: from all iif eth1.2 lookup unspec 12
4200000010: from all iif eth1.2 lookup unspec 12
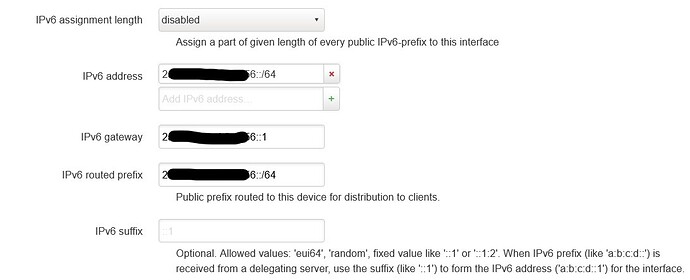
after adding the second prefix
{
"kernel": "4.14.221",
"hostname": "lorien",
"system": "ARMv7 Processor rev 1 (v7l)",
"model": "Linksys WRT3200ACM",
"board_name": "linksys,rango",
"release": {
"distribution": "OpenWrt",
"version": "19.07.7",
"revision": "r11306-c4a6851c72",
"target": "mvebu/cortexa9",
"description": "OpenWrt 19.07.7 r11306-c4a6851c72"
}
}
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '64'
option ipaddr '192.168.12.1'
config interface 'wan'
option ifname 'eth1.2'
option proto 'dhcp'
option peerdns '0'
config interface 'wan6'
option ifname 'eth1.2'
option proto 'dhcpv6'
option reqprefix 'auto'
option reqaddress 'try'
option peerdns '0'
list ip6prefix '2a01:e34:ecb2:a156::/64'
list ip6prefix '2a01:e34:ecb2:a157::/64'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '1 2 3 5t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6t'
option vid '2'
config route6
option interface 'wan6'
option target '2000::/3'
option gateway 'fe80::f6ca:e5ff:fe4c:58fb'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '0 5t'
option vid '24'
package dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option localservice '1'
option domain 'laumei.eu'
option local '/laumei.eu/'
list server '0::1#5453'
list server '127.0.0.1#5453'
option noresolv '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option dhcpv6 'server'
option ra 'server'
option ra_default '1'
option ra_management '2'
list dhcp_option '6,192.168.12.8,192.168.12.1'
list domain 'laumei.eu'
list dns '2a01:e34:ecb2:a156::1208'
list dns '2a01:e34:ecb2:a156::1'
option leasetime '12h'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option mac '00:08:9B:C0:B1:B5'
option dns '1'
option name 'moria'
option ip '192.168.12.12'
option hostid '1212'
option duid '000000089bc0b1b500089bc0b1b5'
config host
option mac '00:1E:8F:79:B7:C9'
option dns '1'
option name 'mp620'
option ip '192.168.12.15'
option hostid '1215'
config domain
option name 'lorien'
option ip '2a01:e34:ecb2:a156::1'
config domain
option name 'moria'
option ip '2a01:e34:ecb2:a156::1212'
config cname
option cname 'ns0.laumei.eu'
option target 'lorien.laumei.eu'
config cname
option cname 'ns2.laumei.eu'
option target 'imladris.laumei.eu'
config cname
option cname 'nas0.laumei.eu'
option target 'moria.laumei.eu'
config host
option mac 'DC:A6:32:BA:11:42'
option dns '1'
option name 'imladris'
option hostid '1208'
option ip '192.168.12.8'
option duid '00020000ab11bacce236fda9e49c'
config cname
option cname 'ntp.laumei.eu'
option target 'lorien.laumei.eu'
config host
option mac 'DC:A6:32:E2:7C:87'
option name 'lumbar'
option dns '1'
option ip '192.168.12.4'
option hostid '1204'
option duid '00020000ab11ce57e231f666c727'
config cname
option cname 'mail.laumei.eu'
option target 'lumbar.laumei.eu'
config mxhost
option domain 'laumei.eu'
option relay 'mail.laumei.eu'
option pref '10'
config txt-record
config txt-record
config host
option mac '90:E6:BA:F2:84:27'
option dns '1'
option name 'pelargir'
option ip '192.168.12.10'
option duid '00020000ab116e7fcbb95cf4cb9f'
option hostid '1210'
config cname
option cname 'photos.laumei.eu'
option target 'pelargir.laumei.eu'
config dhcp 'DMZ'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'DMZ'
option ra_management '2'
option ra 'server'
option dhcpv6 'server'
option dynamicdhcp '0'
list domain 'laumei.eu'
list dns '2a01:e34:ecb2:a157::1'
option ra_default '1'
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 state UNKNOWN qlen 1000
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 532
inet6 fe80::3223:3ff:fedd:ea10/64 scope link
valid_lft forever preferred_lft forever
3: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 532
inet6 fe80::3023:3ff:fedd:ea10/64 scope link
valid_lft forever preferred_lft forever
8: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 2a01:e34:ecb2:a157::1/64 scope global
valid_lft forever preferred_lft forever
inet6 2a01:e34:ecb2:a156::1/64 scope global
valid_lft forever preferred_lft forever
inet6 fe80::3023:3ff:fedd:ea10/64 scope link
valid_lft forever preferred_lft forever
10: eth1.2@eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 2a01:e34:ecb2:a150:3223:3ff:fedd:ea10/64 scope global dynamic
valid_lft 86340sec preferred_lft 86340sec
inet6 fe80::3223:3ff:fedd:ea10/64 scope link
valid_lft forever preferred_lft forever
11: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 fe80::3223:3ff:fedd:ea12/64 scope link
valid_lft forever preferred_lft forever
default from 2a01:e34:ecb2:a150::/64 via fe80::224:d4ff:feae:fc68 dev eth1.2 metric 512
2a01:e34:ecb2:a150::/64 dev eth1.2 metric 256
unreachable 2a01:e34:ecb2:a150::/64 dev lo metric 2147483647 error -113
2a01:e34:ecb2:a156::/64 dev br-lan metric 1024
unreachable 2a01:e34:ecb2:a156::/64 dev lo metric 2147483647 error -113
2a01:e34:ecb2:a157::/64 dev br-lan metric 1024
unreachable 2a01:e34:ecb2:a157::/64 dev lo metric 2147483647 error -113
2000::/3 via fe80::f6ca:e5ff:fe4c:58fb dev eth1.2 metric 1024
fe80::/64 dev eth0 metric 256
fe80::/64 dev eth1.2 metric 256
fe80::/64 dev eth1 metric 256
fe80::/64 dev br-lan metric 256
fe80::/64 dev wlan0 metric 256
local ::1 dev lo table local metric 0
anycast 2a01:e34:ecb2:a150:: dev eth1.2 table local metric 0
local 2a01:e34:ecb2:a150:3223:3ff:fedd:ea10 dev eth1.2 table local metric 0
anycast 2a01:e34:ecb2:a156:: dev br-lan table local metric 0
local 2a01:e34:ecb2:a156::1 dev br-lan table local metric 0
anycast 2a01:e34:ecb2:a157:: dev br-lan table local metric 0
local 2a01:e34:ecb2:a157::1 dev br-lan table local metric 0
anycast fe80:: dev eth1.2 table local metric 0
anycast fe80:: dev eth1 table local metric 0
anycast fe80:: dev eth0 table local metric 0
anycast fe80:: dev br-lan table local metric 0
anycast fe80:: dev wlan0 table local metric 0
local fe80::3023:3ff:fedd:ea10 dev eth0 table local metric 0
local fe80::3023:3ff:fedd:ea10 dev br-lan table local metric 0
local fe80::3223:3ff:fedd:ea10 dev eth1.2 table local metric 0
local fe80::3223:3ff:fedd:ea10 dev eth1 table local metric 0
local fe80::3223:3ff:fedd:ea12 dev wlan0 table local metric 0
ff00::/8 dev eth0 table local metric 256
ff00::/8 dev eth1.2 table local metric 256
ff00::/8 dev eth1 table local metric 256
ff00::/8 dev br-lan table local metric 256
ff00::/8 dev wlan0 table local metric 256
0: from all lookup local
32766: from all lookup main
4200000000: from 2a01:e34:ecb2:a156::1/64 iif br-lan lookup unspec unreachable
4200000000: from 2a01:e34:ecb2:a157::1/64 iif br-lan lookup unspec unreachable
4200000001: from all iif lo lookup unspec 12
4200000008: from all iif br-lan lookup unspec 12
4200000010: from all iif eth1.2 lookup unspec 12
4200000010: from all iif eth1.2 lookup unspec 12
it seems also that all the device on the LAN have now 2 IPv6 address
nslookup lumbar
Server: 127.0.0.1
Address: 127.0.0.1#53
Name: lumbar
Address 1: 192.168.12.4
Address 2: 2a00:xxx:yyy:zzz7::1204
Address 3: 2a00:xxx:yyy:zzz6::1204