Ok, I’ve spent some time testing out the BGW’s firewall and confirmed the following:
- Disabling the packet filter does not disable the advanced firewall rules. However, all the rules shown on the packet filter tab are already disabled by default, although the UI makes this unclear at first glance.
- The packet filter remains on for IP Passthrough devices unless it’s turned off altogether, contrary to what some posts have stated online.
Instructions to confirm (1)
- Find the modem’s IPv6 address under Home Network > Status > IPv6 > Global Unicast IPv6 Address.
- Run
ping6 <ipv6address> from your home network. This should go through.
$ ping6 e23e:a854:e5b5:67fc::1 -c1
16 bytes from e23e:a854:e5b5:67fc::1, icmp_seq=0 hlim=63 time=4.504 ms
--- e23e:a854:e5b5:67fc::1 ping6 statistics ---
1 packets transmitted, 1 packets received, 0.0% packet loss
round-trip min/avg/max/std-dev = 4.504/4.504/4.504/0.000 ms
- Connect to a VPN or external network and run
ping6 <ipv6address> again. The packets should be dropped.
$ ping6 e23e:a854:e5b5:67fc::1
^C
--- e23e:a854:e5b5:67fc::1 ping6 statistics ---
3 packets transmitted, 0 packets received, 100.0% packet loss
- Go to Firewall > Packet Filter and click Disable Packet Filters, then run the above command again. The packets should still be dropped.
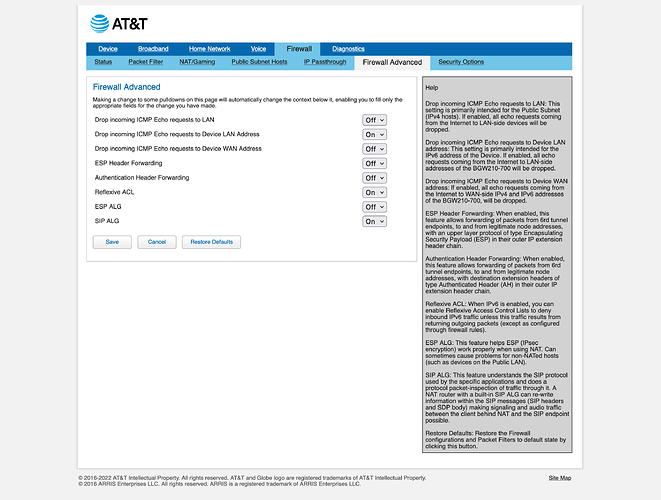
- Go to Firewall > Firewall Advanced, set “Drop incoming ICMP Echo requests to Device LAN Address” to Off, and click save. Run the ping command again, and it should go through.
- Turn the packet filter back on.
Instructions to confirm (2)
Note: I chose port 22 to test, with SSH password authentication disabled.
Temporarily update the SSH interface to be unspecified:
uci delete dropbear.@dropbear[0].Interface
uci commit dropbear
service dropbear restart
Add the following rule to /etc/config/firewall:
config redirect
option dest 'lan'
option target 'DNAT'
option name 'testing firewall ipv4’
option src 'wan'
option src_dport '22'
option dest_ip <router_lan_ip>
option dest_port '22'
config rule
option name 'testing firewall ipv6’
option target 'ACCEPT'
option src 'wan'
option dest_port '22'
option proto 'tcp'
option family 'ipv6'
Connect to a VPN or external network and run the following:
# nmap -p 22 <router_wan_ip>
# nmap -p 22 <router_wan6_ip> -6
These should show port 22 as open. Now add the following firewall rule to the BGW under Firewall > Packet Filter:
Drop packets that match:
IP Version of "Both IPv4AndIPv4"
Protocol of "TCP"
Source Port of "22"
Click the empty checkbox to enable the rule, then run the nmap command again. It should now show as closed. Make sure to remove the firewall rules when done and set the SSH interface to LAN.
Bridge settings
Everything is now set back to the defaults on my BGW210-700, except:
- The access code is changed.
- Wi-Fi is turned off under Home Network > Wi-Fi > Advanced Options.
- IP Passthrough is setup with the OpenWrt router and Passthrough DHCP Lease time is set to 1 day. No other devices are connected to the modem.
- Under Firewall > Firewall Advanced, Reflexive ACL and SIP ALG is turned off. I’ve left the default setting specific to the BGW210 (“Drop incoming ICMP Echo requests to Device LAN Address”) turned on.
Public Subnet Mode is off (default), Cascaded Router is disabled (default), and the Packet Filter had no rules set (default) but is set to disabled.
I am able to connect to the modem web portal on devices behind my openwrt router using the default IP of 192.168.1.254 without any special setup.
Alternatively, if you're a fiber customer, you may be interested in this guide on setting up an EAP Proxy which allows connecting your own router directly to the ONT without rooting.
DSL (AT&T U-Verse) customers may be interested in this guide to use an alternative modem with a proper bridge mode, but it relies on a rooting method which no longer works on the latest firmware.