@richb-hanover-priv Thanks Rich.
@darksky Let's start by explaining a bit of how things work.
DSA only sets up the switch ports. E.g. interfaces called wan, lan1, lan2, etc.
To configure VLANs on a switch using DSA framework, you'd have to put all of the interfaces (wan, lan1, lan2, etc.) into one bridge (e.g. br0). Then, create a subinterface of the bridge interface (e.g. br0.5 which is based off of br0 and set to use VLAN ID 5) to send & receive frames with the specified VLAN. Check the Converting to DSA page I wrote for more details.
These interfaces (br0.5 in this example) are also called subinterfaces. This just means that they're based off of another interface. E.g. if the br0.5 is based off of br0, it's a subinterface of br0.
The name of your interface actually doesn't matter. You could name your interface whatever you want and still make it based off of, for example, br0 and set it to use VLAN 5.
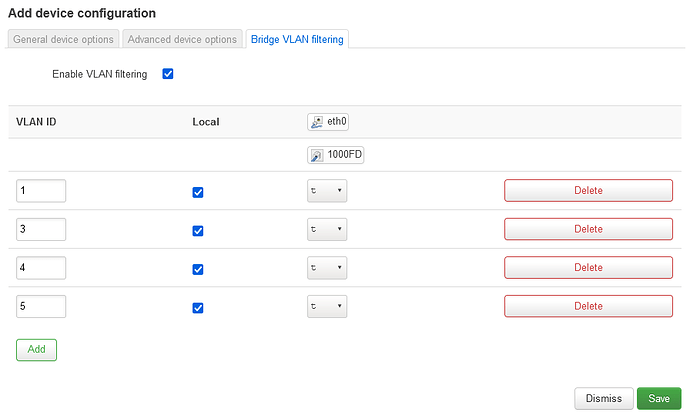
Here's a screenshot where I call my interface name "whatever", it's still based off of br0 and set to use VLAN 5:
To do the same thing on the command line is this command:
ip link add link br0 name whatever type vlan id 5
You can see VLAN and other information of the interfaces on the command line with this command: ip -d link (you need ip-full package on OpenWrt to use the "-d" option). E.g. the output of the "whatever" interface I created:
6: whatever@br0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN mode DEFAULT group default qlen 1000
link/ether a0:b0:c0:d0:e0:f0 brd ff:ff:ff:ff:ff:ff promiscuity 0 minmtu 0 maxmtu 65535
vlan protocol 802.1Q id 5 <REORDER_HDR> addrgenmode eui64 numtxqueues 1 numrxqueues 1 gso_max_size 62780 gso_max_segs 65535
It's more convenient to name your subinterface e.g. br0.5 so you can easily figure out which interface it's based off of and what VLAN ID it uses by just looking at the name of the subinterface.
OpenWrt makes things more easier. If you just add an interface (it's incorrectly called "device" on LuCI) called br0.5 on one of the networks on the "Interfaces" page, OpenWrt will automatically create a subinterface of br0 and set the interface to use VLAN 5.
When you have a subinterface called br0.5 based off of br0 with VLAN 5, this is how frames are forwarded:
Any untagged frames going to br0.5 are forwarded out of br0 as tagged frames with VLAN 5.
Any tagged frames with VLAN 5 going to br0 will be forwarded to br0.5 as untagged frames.
VLAN filtering needs to be enabled on the bridge. The Linux kernel will then forward frames per the VLAN configuration.
Back to your case
On devices without a switch, the ethernet port(s) - mostly singular - is directly connected to the CPU. Therefore the interface of the ethernet port is usually called something like eth0, eth1, etc. You don't use DSA to initialise these ports in this case.
You only have one port so you don't need to put it under a bridge (if you don't want to include wireless interfaces on the VLANs. If you intend to, the wiki page I linked above should keep you covered).
Let's say you have 3 networks. On "Interfaces" page, for the first network, specify the interface as eth0.10.
For the second, specify eth0.20. For the third eth0.30.
And then you can set up the router to route between these networks.
I hope this was inclusive enough. Let me know if you have any questions.