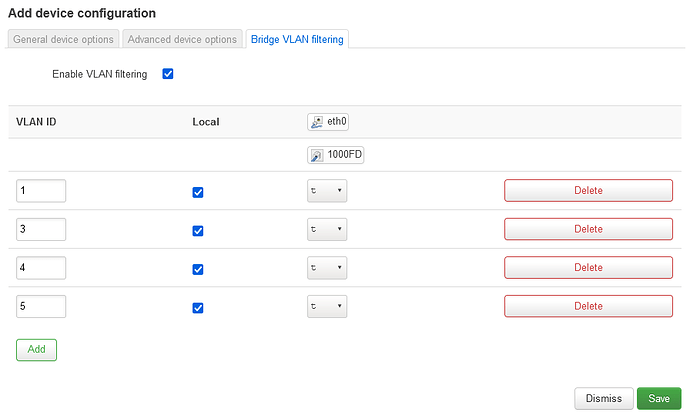
What is the difference (if any) between using Bridge VLAN filter/DSA to setup VLAN tagging and creating a driver-level VLAN in the context of a device without a switch like a RPi4?
My setup is using the RPi4 as the router/firewall with VLAN tagging with a separate dumb AP. Goal is isolation between the VLANs.
For more context, here is the network config on the RPi4 router/firewall:
/etc/config/network
# vim:set ts=2 sw=2 et:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd1a:184b:b879::/48'
option packet_steering '1'
config bridge-vlan
option device 'br-main'
option vlan '1'
list ports 'eth0:t*'
config bridge-vlan
option device 'br-main'
option vlan '3'
list ports 'eth0:t'
config bridge-vlan
option device 'br-main'
option vlan '4'
list ports 'eth0:t'
config bridge-vlan
option device 'br-main'
option vlan '5'
list ports 'eth0:t'
config device
option name 'eth0'
option ipv6 '0'
config device
option name 'eth1'
option ipv6 '0'
config device
option name 'br-main'
option type 'bridge'
list ports 'eth0'
option ipv6 '0'
config device
option name 'br-wan'
option type 'bridge'
list ports 'eth1'
option ipv6 '0'
config device
option name 'br-lxc'
option type 'bridge'
list ports 'br-main.4'
option ipv6 '0'
config device
option name 'br-main.1'
option type '8021q'
option ifname 'br-main'
option vid '1'
option ipv6 '0'
config device
option name 'br-main.3'
option type '8021q'
option ifname 'br-main'
option vid '3'
option ipv6 '0'
config device
option name 'br-main.4'
option type '8021q'
option ifname 'br-main'
option vid '4'
option ipv6 '0'
config device
option name 'br-main.5'
option type '8021q'
option ifname 'br-main'
option vid '5'
option ipv6 '0'
config device
option name 'wg0'
option ipv6 '0'
config interface 'wan'
option proto 'dhcp'
option peerdns '0'
option delegate '0'
list dns '1.1.1.1'
list dns '1.0.0.1'
option device 'br-wan'
config interface 'lan'
option proto 'static'
option ipaddr '10.9.8.1'
option netmask '255.255.255.0'
option device 'br-main.1'
config interface 'guest'
option proto 'static'
option ipaddr '10.9.7.1'
option netmask '255.255.255.0'
option device 'br-main.3'
config interface 'lxc'
option proto 'static'
option ipaddr '10.0.4.1'
option netmask '255.255.255.0'
option device 'br-lxc'
config interface 'iot'
option proto 'static'
option ipaddr '10.9.5.1'
option netmask '255.255.255.0'
option device 'br-main.5'
config interface 'wg0'
option proto 'wireguard'
...
# omitted wireguard section
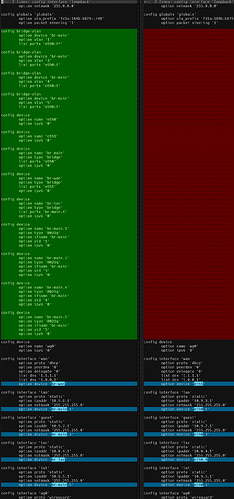
 Nothing worked upon rebooting both devices... I simply replaced
Nothing worked upon rebooting both devices... I simply replaced