If like do did something wrong, like me. Putting back it online can be interresting (but warranty will be lost)
My mistake was pushing back the backup.con file, wich is not a valid image (yes it's a non sense to make un unrestorable backup but that's a classical job protect ![]() )
)
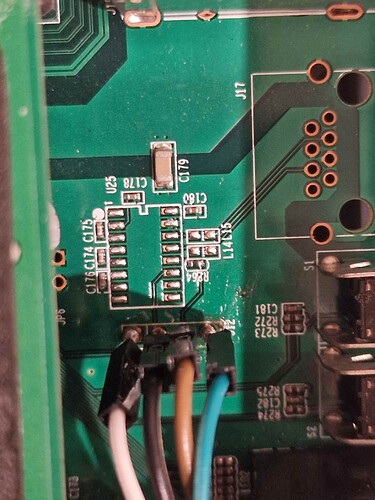
UART Connexion / place
Do not forget, to unplug power and wait a moment... It could be your last mistake (370W POE+ is far over what you can resist ![]() )
)
Serial connexion is near LED and button. You have 4 PIN named J12 (possibly something else).
---I am Not allowed to put images Yet---
Why did I solder the four wire? Just in case the first one is one of the supposed RX TX GND on my version, ingeneers makes jokes.
Putty parameter
COM Port: COM 7 (may vary)
Speed (Bauds): 115200
Type: Serial
Data/parity/Stop : 8N1(default ones)
Flow Control XON/XOFF (default ones)
OpenWRT ROM
Take the kernel version
OpenWrt Firmware Selector
Firmware push
Push Stock Firmware / Backup (ineffective)
In the OpenWRT doc you have a "default" command line, DON'T DO THAT... I did it and it does nots end up nicely ![]() ...
...
It works on most case, but ours is different.
tftpboot 0x80000000 openwrt-xxx-generic-xxx-squashfs-factory.bin
erase 0x9f020000 +0x332004
cp.b 0x80000000 0x9f020000 0x332004
the cp.b line need some precisions:
- the third param is the image length (you get it in the tftpboot return)
- it takes a while (for me 6 hours
 )
)
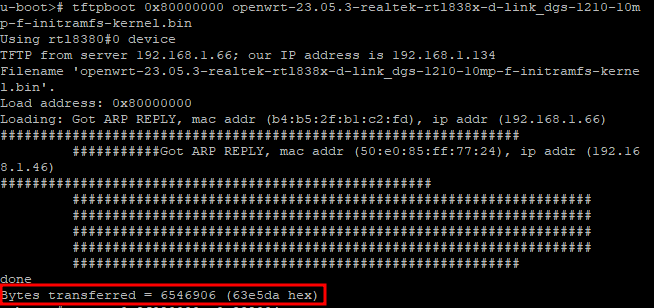
You can push a file and boot on it like this:
dhcp
setenv serverip 192.168.1.25
tftpboot 0x8f000000 DGS-1210-FX-SERIES-FX-6-20-B020.hex
bootm 0x8f000000
Details:
- dhcp: to obtain an Ip from ypur DHCP (or use setenv ipaddr 192.168.1.1)
- setenv serverip 192.168.1.25: Means where is your TFTP server (here a simple one: tftpd64)
- tftpboot 0x8f000000 DGS-1210-FX-SERIES-FX-6-20-B020.hex: this push the file (in your tftpd) to your switch RAM at the specified adress
- bootm 0x8f000000: boot on the specified adress
And.... it crashed.
I have tried all .hex file (old firmware file), all .con file (new firmware file and backup made with Dlink interface) that you can found on the link in ressources at the end.
Any idea would be higly appreciate ![]()
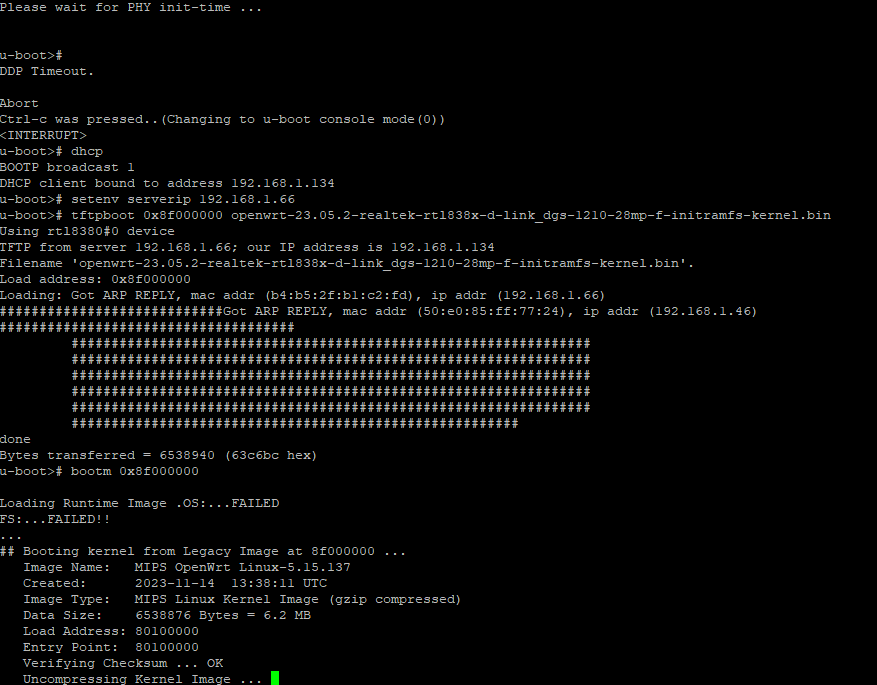
Pushing a OpenWRT (effective)
As before, but with the correct OpenWRT kernel image version (take the one before the last one... we will perform a sysupgrade after)
dhcp
setenv serverip 192.168.1.66
tftpboot 0x8f000000 openwrt-23.05.2-realtek-rtl838x-d-link_dgs-1210-28mp-f-initramfs-kernel.bin
bootm 0x8f000000
After this, your OpenWRT does not fill really good and ask you a sysupgrade, but it boot.
You have to push last sys upgrade version.
And there it boot alone correctly (or near) on openWRT.
Questions
Arrived there, you probably wonder, but where is the question...
- Does anyone knows how to flash a stock Firmware on this DGS-1210-28MP (or DGS-1210 * Fx rev)?
Why: This unit has 2 kernel slot, I would like have the hability to boot back on stock firmware because some function does not work: standart POE for example, I will made a topics on this, but I don't have finish testing some solution.
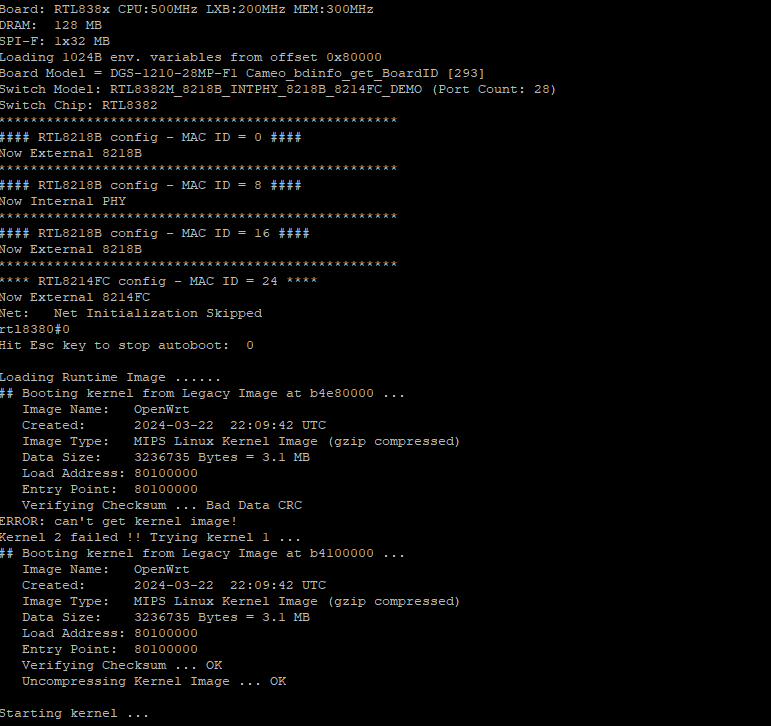
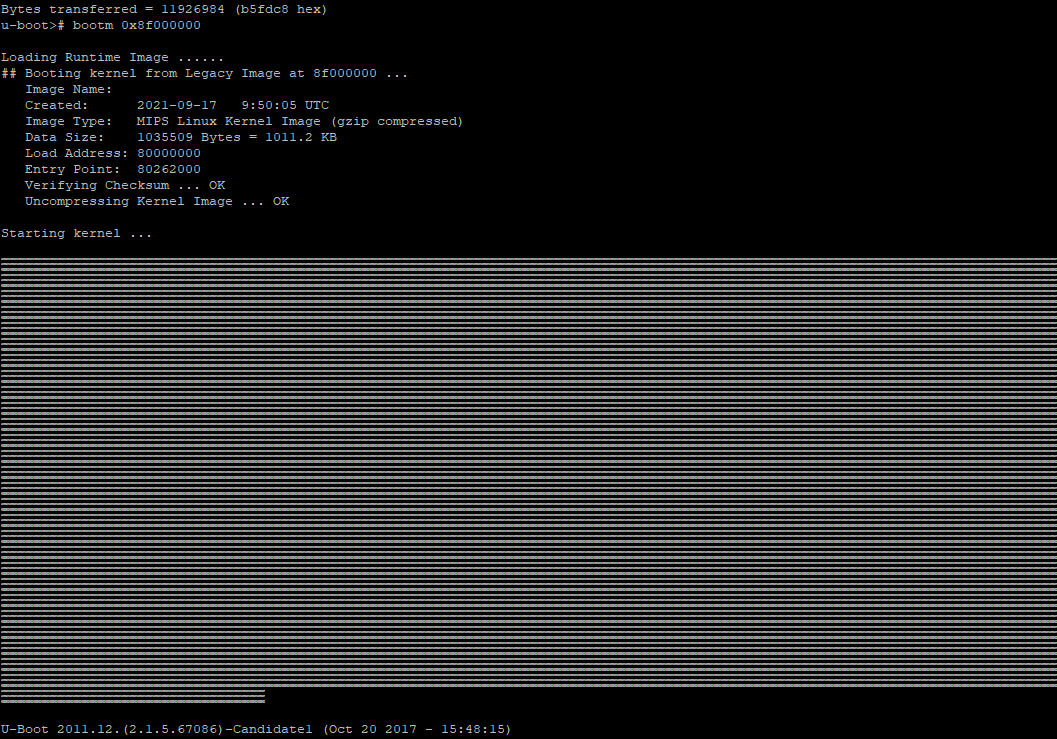
- Does anyone has a the normal boot text (like the one below, but without any trouble (on stock or OpenWRT Rom)?
The idea is to get normal load adress' / Entry Point, and perhaps a flashable backup ![]() I supposed they are 0xb4100000 and 0xb4e80000. But flashing Firmware on guessed addresses is not a good idea, I prefer to verify them before.
I supposed they are 0xb4100000 and 0xb4e80000. But flashing Firmware on guessed addresses is not a good idea, I prefer to verify them before.
Ressources
Hex Firmware here:https://ftp.dlink.ru/pub/Switch/DGS-1210-28MP/Firmware/
Con Firmware here: https://support.dlink.com/resource/products/DGS-1210-SERIES/REVF/FIRMWARE/v6.30.016/
SRC Code sources: https://tsd.dlink.com.tw/
PS: excuse my english, I speak python usualy ![]()