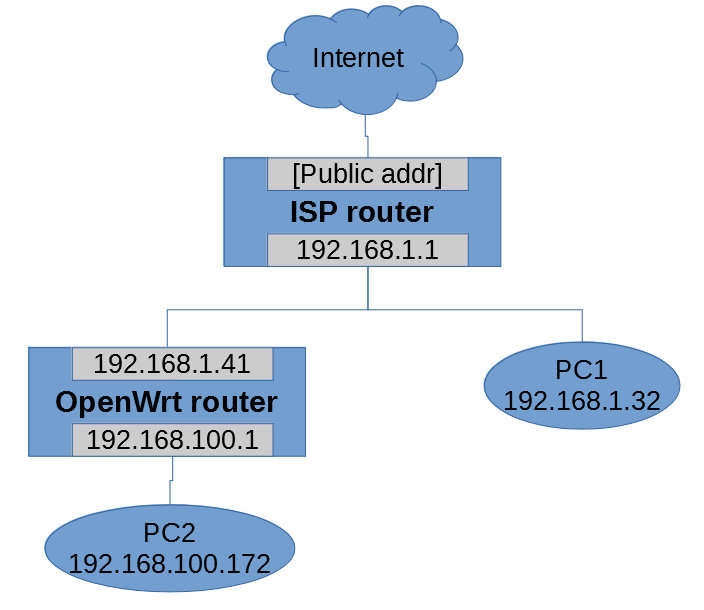
I need some help configuring the firewall and static routes. I am trying what is described here. My topology:
/etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd73:c662:4d27::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.100.1'
config device 'lan_dev'
option name 'eth0.1'
option macaddr '20:76:93:46:64:4f'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
config device 'wan_dev'
option name 'eth0.2'
option macaddr '20:76:93:46:64:50'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 3 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6t'
# This is what I added:
config route
option interface 'wan'
option target '192.168.1.0'
option netmask '255.255.255.0'
config route
option interface 'wan'
option target '0.0.0.0'
option netmask '0.0.0.0'
option gateway '192.168.1.1'
/etc/config/firewall
config defaults
option syn_flood 1
option input ACCEPT
option output ACCEPT
option forward REJECT
config zone
option name lan
list network 'lan'
option input ACCEPT
option output ACCEPT
option forward ACCEPT
# input changed from REJECT to ACCEPT, masq changed from 1 to 0
config zone
option name wan
list network 'wan'
list network 'wan6'
option input ACCEPT
option output ACCEPT
option forward REJECT
option masq 0
option mtu_fix 1
config forwarding
option src lan
option dest wan
# This is what I added:
config forwarding
option src wan
option dest lan
config rule
option name Allow-DHCP-Renew
option src wan
option proto udp
option dest_port 68
option target ACCEPT
option family ipv4
config rule
option name Allow-Ping
option src wan
option proto icmp
option icmp_type echo-request
option family ipv4
option target ACCEPT
config rule
option name Allow-IGMP
option src wan
option proto igmp
option family ipv4
option target ACCEPT
config rule
option name Allow-DHCPv6
option src wan
option proto udp
option src_ip fc00::/6
option dest_ip fc00::/6
option dest_port 546
option family ipv6
option target ACCEPT
config rule
option name Allow-MLD
option src wan
option proto icmp
option src_ip fe80::/10
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family ipv6
option target ACCEPT
config rule
option name Allow-ICMPv6-Input
option src wan
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
list icmp_type router-solicitation
list icmp_type neighbour-solicitation
list icmp_type router-advertisement
list icmp_type neighbour-advertisement
option limit 1000/sec
option family ipv6
option target ACCEPT
config rule
option name Allow-ICMPv6-Forward
option src wan
option dest *
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
option limit 1000/sec
option family ipv6
option target ACCEPT
config rule
option name Allow-IPSec-ESP
option src wan
option dest lan
option proto esp
option target ACCEPT
config rule
option name Allow-ISAKMP
option src wan
option dest lan
option dest_port 500
option proto udp
option target ACCEPT
config include
option path /etc/firewall.user
First question: the strange thing I encountered is that, if I change wan option masq to 0 to disable SNAT, I can no longer access the Internet. A simple tracert shows that the traffic reaches the ISP router and stops there.
PS C:\Users\livyi> tracert facebook.com
Tracing route to facebook.com [31.13.95.36] over a maximum of 30 hops:
1 <1 ms <1 ms <1 ms OpenWrt.lan [192.168.100.1]
2 <1 ms <1 ms <1 ms 192.168.1.1
3 * * * Request timed out.
Maybe the ISP router denies doing NAT for client IPs which is out of its subnet range 192.168.1.0/24?
Second question: what did I do wrong in the config above? I can ping PC1 from PC2, but not to PC2 from PC1 -- I want to make both PCs access each other. The static route was added to the ISP router to forward 192.168.100.0/24 traffic to gateway 192.168.1.41. And I can ping 192.168.100.1 from PC1.