camus
December 1, 2022, 11:26pm
1
it used to be, before there was an opkg package for AGH that it was possible to manually install AGH and then do this:
iptables -t nat -A PREROUTING -i br-lan -p udp --dport 53 -j DNAT --to 10.x.x.x:5353
iptables -t nat -A PREROUTING -i br-lan -p tcp --dport 53 -j DNAT --to 10.x.x.x:5353
but with the latest openwrt, even with a build on iptables, the option to add that through Luci Network > Firewall > Custom rule is no longer there.
Where can one add the above lines in the current version of openwrt and the default AGH opkg version in Softwares, please?
thanks a lot.
You can follow the wiki but add an “Internal port” of 5353 in the rule.
camus
December 2, 2022, 12:27pm
3
@dave14305 thanks a lot. i will give it and try and report.
camus
December 4, 2022, 12:11pm
4
@dave14305 thanks a lot! And for those wandering and wondering about AGH not auto starting, which is another issue, a solution is below, NOT the commands in the wiki. The solution is taken from the link below:
https://forum.openwrt.org/t/adguardhome-ipk-autostart-not-working-after-reboot/119274/18
service adguardhome disable
camus
December 4, 2022, 12:49pm
5
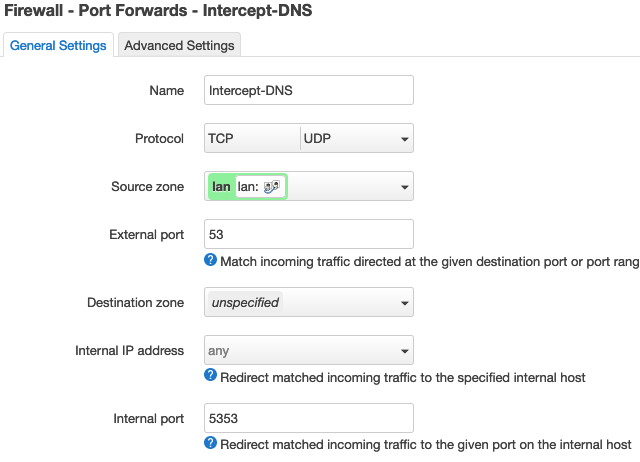
I spoke too soon. DNS hijacking from the wiki is not working. Still looking for help. Here's a screenshot of my settings:
Is Adguardhome listening on port 5353?
netstat -nltup | grep 53
nft list ruleset | grep Intercept
camus
December 4, 2022, 1:08pm
7
It would not allow me to proceed with "53" at configuration, and so I did 5353. Is this my error? How do I now correct it, please?
I don’t use AGH. I just want to understand the current setup on your router.
camus
December 4, 2022, 1:18pm
9
dave14305:
netstat -nltup | grep 53
^Croot@OpenWrt:~# netstat -nltup | grep 53
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 2577/dnsmasq
tcp 0 0 192.168.1.1:53 0.0.0.0:* LISTEN 2577/dnsmasq
tcp 0 0 192.168.0.54:53 0.0.0.0:* LISTEN 2577/dnsmasq
tcp 0 0 192.168.1.1:5353 0.0.0.0:* LISTEN 3092/AdGuardHome
tcp 0 0 ::1:53 :::* LISTEN 2577/dnsmasq
tcp 0 0 fe80::a2f3:c1ff:fea5:f79c:53 :::* LISTEN 2577/dnsmasq
tcp 0 0 fdec:688a:7325::1:53 :::* LISTEN 2577/dnsmasq
tcp 0 0 fe80::a2f3:c1ff:fea5:f79c:53 :::* LISTEN 2577/dnsmasq
tcp 0 0 2a02:8109:b640:43f:a2f3:c1ff:fea5:f79d:53 :::* LISTEN 2577/dnsmasq
tcp 0 0 fe80::a2f3:c1ff:fea5:f79d:53 :::* LISTEN 2577/dnsmasq
udp 0 0 192.168.1.1:5353 0.0.0.0:* 3092/AdGuardHome
udp 0 0 127.0.0.1:53 0.0.0.0:* 2577/dnsmasq
udp 0 0 192.168.1.1:53 0.0.0.0:* 2577/dnsmasq
udp 0 0 192.168.0.54:53 0.0.0.0:* 2577/dnsmasq
udp 0 0 ::1:53 :::* 2577/dnsmasq
udp 0 0 fe80::a2f3:c1ff:fea5:f79c:53 :::* 2577/dnsmasq
udp 0 0 fdec:688a:7325::1:53 :::* 2577/dnsmasq
udp 0 0 fe80::a2f3:c1ff:fea5:f79c:53 :::* 2577/dnsmasq
udp 0 0 2a02:8109:b640:43f:a2f3:c1ff:fea5:f79d:53 :::* 2577/dnsmasq
udp 0 0 fe80::a2f3:c1ff:fea5:f79d:53 :::* 2577/dnsmasq
camus
December 4, 2022, 1:18pm
10
this does not output anything at all
Is there any warning/error output if you run fw4 reload
Which OpenWrt version are you running?
camus
December 4, 2022, 1:41pm
12
yes:
How about:
iptables-save -c | grep Intercept
Just want to see if the rule is present and catching anything at all.
camus
December 4, 2022, 2:19pm
14
that seems to be the case.
[0:0] -A zone_lan_prerouting -p tcp -m tcp --dport 53 -m comment --comment "!fw3: Intercept-DNS" -j REDIRECT --to-ports 5353
[35:2448] -A zone_lan_prerouting -p udp -m udp --dport 53 -m comment --comment "!fw3: Intercept-DNS" -j REDIRECT --to-ports 5353
camus
December 4, 2022, 2:20pm
15
but as you can see the results are different from the example I gave at the start of this thread. Is it a zoning issue now?
camus
December 4, 2022, 3:48pm
16
this was my error; a stupid one. i had my wifi connection on my laptop taking over the lan. the wifi was not connected to the router with AGH, so obviously, I was able to go to websites AGH should block. stupid, silly mistake!
1 Like
system
December 14, 2022, 3:48pm
17
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.