Dear Community,
As many of you well know - we have been on a long and arduous journey all with the intent of arriving at Yazdan's goal to Create Surfshark wireguard connection on OpenWrt easily. Well - IMHO - we have arrived at that destination. With that being said, I am throwing this entry up here to aid others. Please - no comments about me trying to hijack this thread. My purpose is to KISS for those who come here looking for THE ANSWER. So here we go with SurfShark WireGurard ~ SSWG the latest and greatest will save you hours of potential agita - of this I am certain.
Installation Prerequisites -- Overview of nano's shortcuts
# opkg update ; opkg install kmod-wireguard luci-app-wireguard luci-proto-wireguard wireguard-tools diffutils curl jq ntpdate qrencode
Step 1 - download zip file from SSWG Homepage
https://github.com/reIyst/SSWG
direct link to SSWG Script zip file =
https://codeload.github.com/reIyst/SSWG/zip/refs/heads/main
Extract SSWG-main zip file to directory of
your choosing on your desktop ( windows )
Linux - you are own your own
You will have SSWG-main folder when done
Step 2 - Create /wg/ Default Folder for SSWG Script
on your device
# mkdir -p /wg/
Step 3 - WINSCP these two files below from location of
extracted SSWG-main folder directory
into the default /wg/ install directory
on your device
The two files to transfer = sswg.json and sswg.sh
Step 3 - make script executable
# chmod 755 /wg/sswg.sh
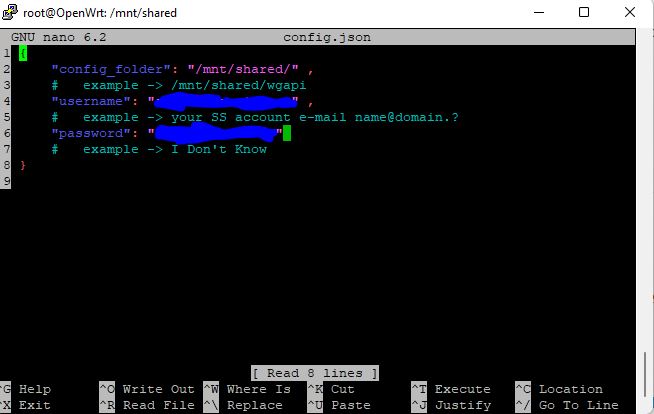
Step 4 - Go into the default install /wg/ directory on your router
and edit sswg.json with your SurFShark E-mail and Password
# cd /wg/
# nano sswg.json
Step 5 - Run SSWG Script ( you will get server configuration files
and your public key is automatically registered
run command below while still in the
default /wg/ install directory :
# ./sswg.sh -g
go back into root directory # cd /root
Step 6 - Set Up Cron Job - you will have fully automated public key
renewal from hence forth - read SSWG HOMEPAGE for details
A -
cat << "EOF" >> /etc/crontabs/root
# Thursday Key Reinstate ## Sunday conf files download and Key Reinstate
#######################################################
15 00 * * 4 /wg/sswg.sh >>/wg/wg.log 2 >&1 # standard registration and Redirect standard output to file '>' to log midnight+15min Thurs
15 00 * * 0 /wg/sswg.sh -g >>/wg/wg.log 2 >&1 # servers conf files dwl and Append standard output to file '>>' to log midnight+15min Sunday
#######################################################
EOF
B -
# uci set system.@system[0].cronloglevel="5"
C -
# uci commit system
D -
# /etc/init.d/cron restart
Done With That Phase - It's That Simple
No More Public Key Expiration Every 6 Days
Bonus Information
In order to read sswg log files on Sunday and Thursday
or anytime thereafter just enter :
# cat /wg/wg.log
If you want to clear log files weekly ( on Sunday ) -
amend your cron job as shown below :
cat << "EOF" >> /etc/crontabs/root
# Thursday Key Reinstate ## Sunday conf files download and Key Reinstate
#######################################################
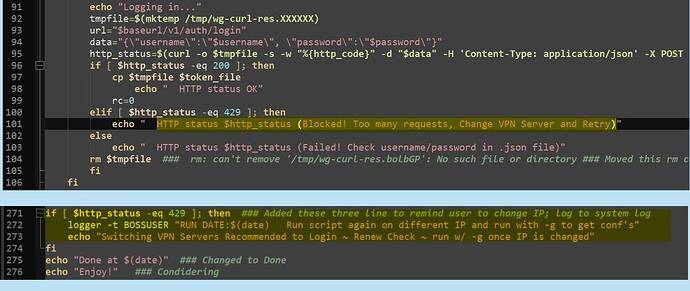
15 00 * * 4 /wg/sswg.sh >/wg/wg.log 2 >&1 # standard registration and overwrite '>>' to log midnight+15min Thurs
01 00 * * 0 now=$(date) ; echo "Overwriting Log - wg.log" >/wg/wg.log 2>&1 ## clear wg.log midnight +1 Sunday
15 00 * * 0 /wg/sswg.sh -g >>/wg/wg.log 2 >&1 # servers conf files dwl and amend '>>' to log midnight+15min Sunday
#######################################################
EOF
Remember to enter the other three commands
B C and D for cron - as shown in Step 6 above.
Lastly, to set up your device with
SurfShark WireGuard Configuration Files
refer to post # 97 of this thread - click on link below`
WireGuard Interface and Simple FireWall Setup
As Ron Popeil made famous You Just Set It And Forget It
You Just Set it and Forget It
Don't thank me - this has been a team effort
Peace Be Unto All