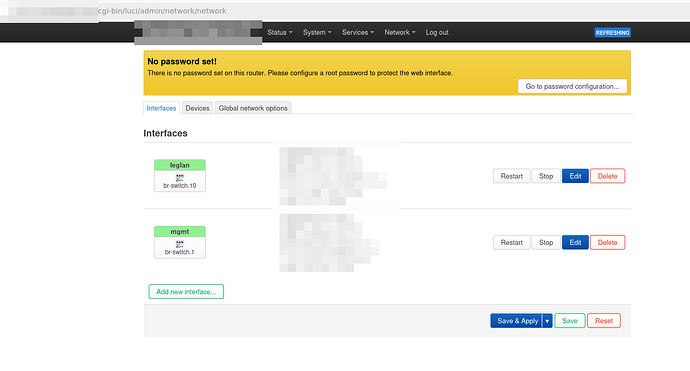
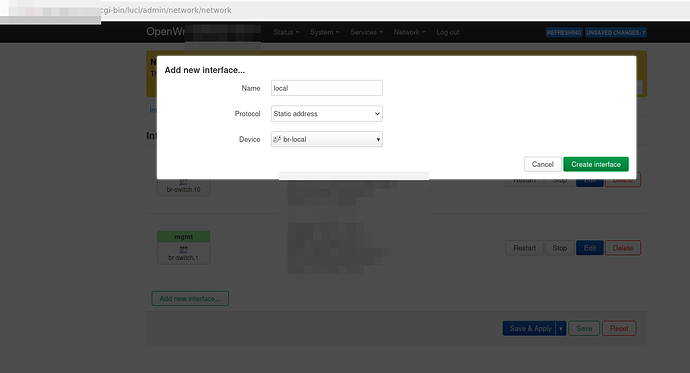
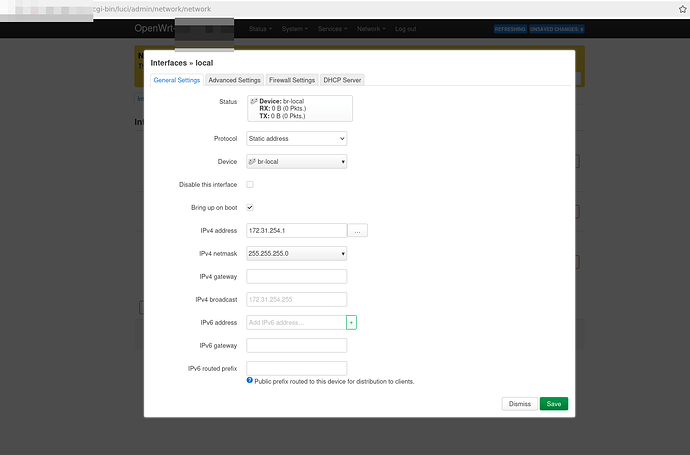
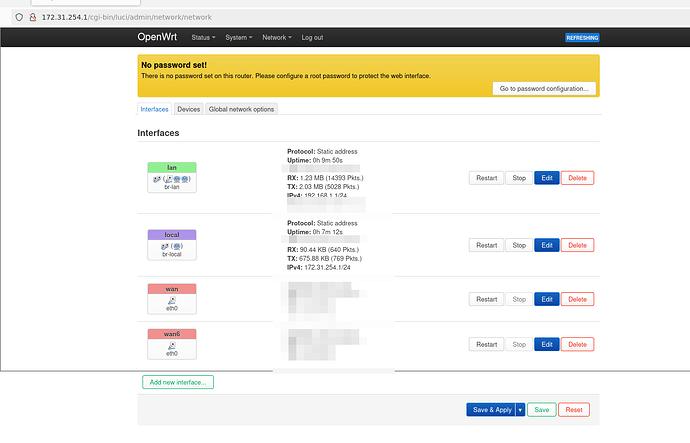
Okay so firstly apologies I had to do an edit as I missed that the default on my example was input reject now for a new firewall group. It's always good to test your own instructions hahahaha.
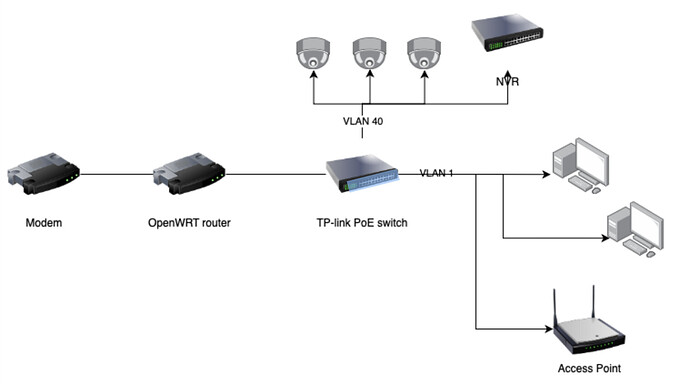
Anyway. Witih the following instructions I've switched devices to something that's the closest I have to your target. Which is an aerohive ap330. (i.e. two network devices).
in this example it's eth0 for wan and eth1 for lan. But it shouldn't matter for the "switch to vlans" example.
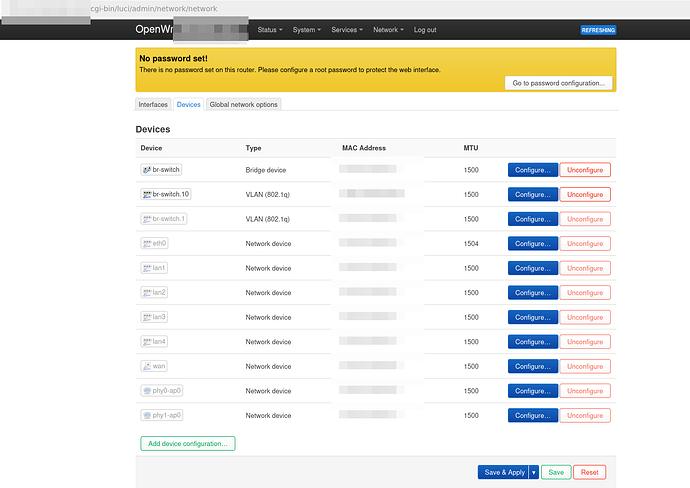
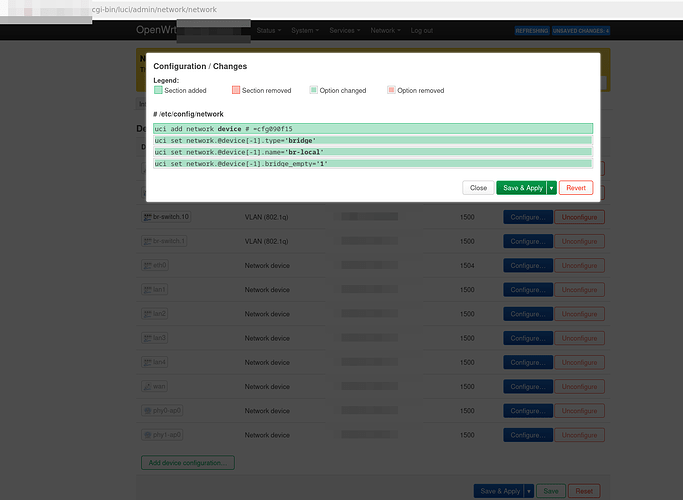
Basically in UCI it'd be the following: (i.e. this is what I copied out of luci unsaved changes)
# /etc/config/network
uci add network bridge-vlan # =cfg09a1b0
uci set network.@bridge-vlan[-1].device='br-lan'
uci set network.@bridge-vlan[-1].vlan='1'
uci add_list network.@bridge-vlan[-1].ports='eth1:u*'
uci add network bridge-vlan # =cfg0aa1b0
uci set network.@bridge-vlan[-1].device='br-lan'
uci set network.@bridge-vlan[-1].vlan='40'
uci add_list network.@bridge-vlan[-1].ports='eth1:t'
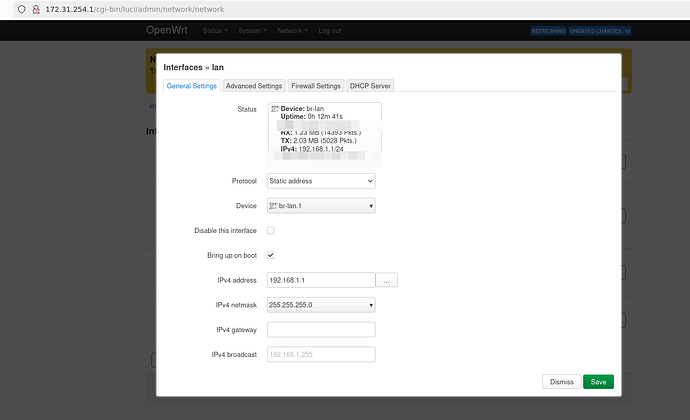
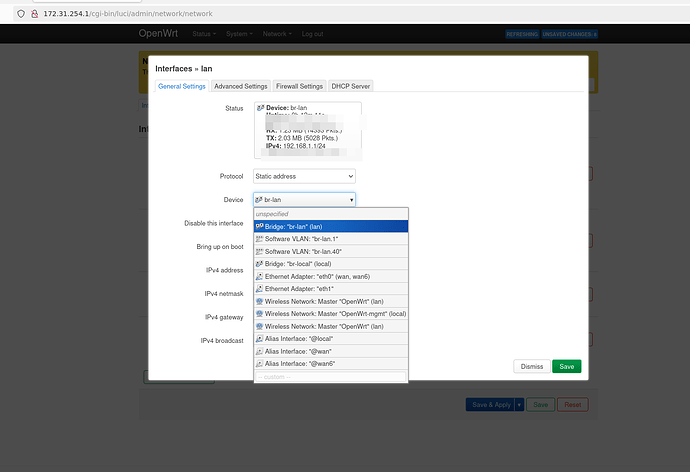
uci set network.lan.device='br-lan.1'
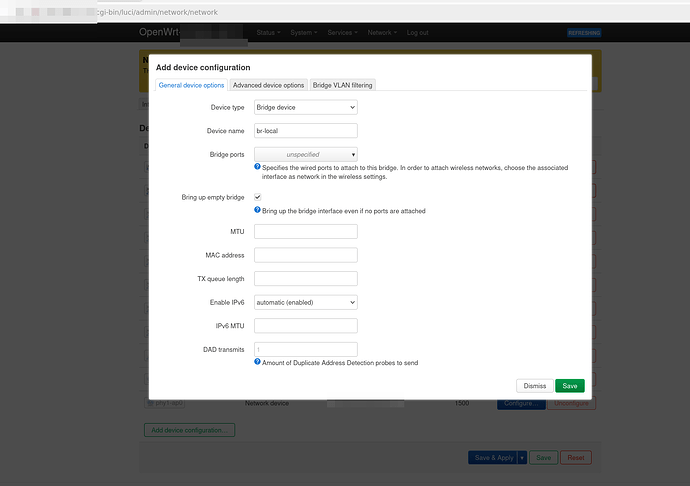
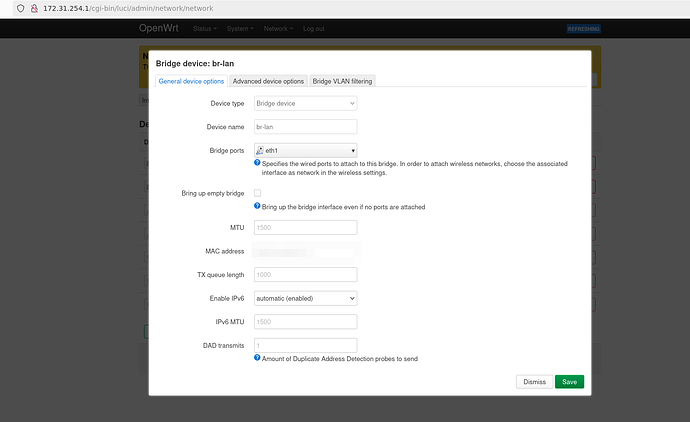
Your steps are to go to your bridge device, hit configure, turn on bridge vlan filtering.
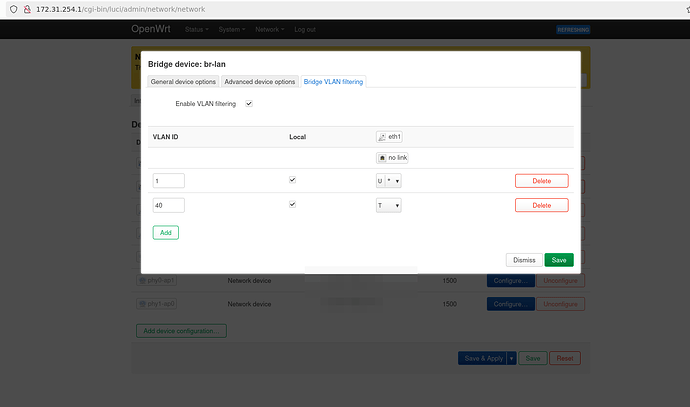
The easiest will be then add vlan1, make it untagged and primary VID.
Then add vlan 40 as tagged.
Then before saving you need to also go to the network section and change your "lan" network from br-lan to br-lan.1.
Pictures:
An important item to note is you will need to restart your wireless or brute force all of networking after you save your changes as you need your wireless to reconnect to the bridge. (i.e. othherwise devices may not connect to your AP correctly). After restarting wireless you should then check that your existting wifi and wired clients work correctly.
Now that we're at this stage, we should make another effort to back up the configuration. (i.e. before we change IP address ranges, then configure vlan40, do switch config. Also backing up your switch config is probably a good idea at this time).
When we get to this point, we are now at the stage for configuring VLAN40 and the network that will be for your CCTV. However up to here We shouldn't have actually impacted the wired network / cctv yet as we set PVID1 / untagged vlan 1 on the same IP address.
Once we get to here it's more complicated =(
I believe to start, your IP range for br-lan will conflict with your CCTV desired static IP's? So one would need to switch your br-lan IP range....
Then we have switch configuration.... I don't have your switch on hand. I think tp-link has emulators for some stuff but It will be challenging and switch dependent....
I think the next steps would be configure your switch for vlans and a static IP address. With all ports untagged PVID vlan 1.
We then need to configure the switch to accept tagged vlan40 on the port connected to your router.
Then configure vlan 40 to untagged vlan 40 and PVID 40 without vlan1 on the CCTV connected ports.
It's then a case of add a network of the appropriate IP range for your router on br-lan.40.