Sorry if I ask so many questions, but I'm quite inexperienced.
With a lot of effort I managed to create a network and associate a VPN with wireguard protocol.
I am very satisfied.
But now I need to create a network without VPN to connect all my devices.
I want to use the VPN network only for TV.
Can you give me some advice?
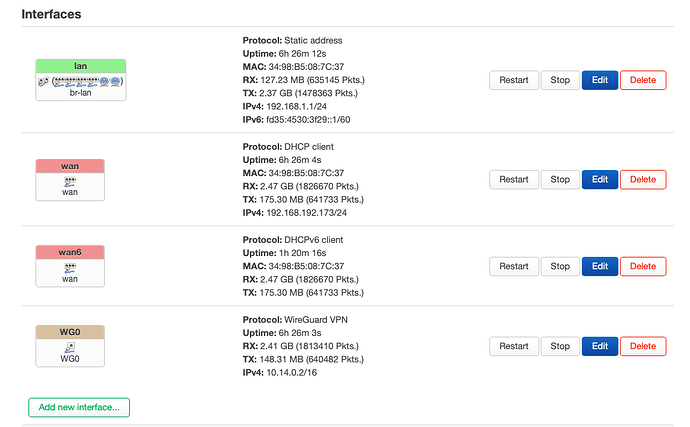
I attach 2 pictures of my system.
Thank you.
I made some test, but I wasn't lucky.
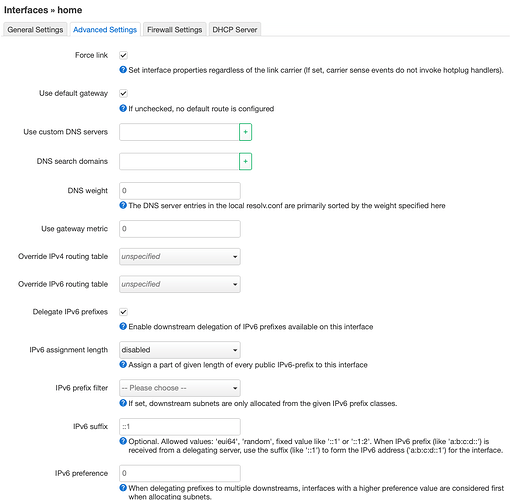
I create a wireless connection connected to lan2
I create a new Interface (lan2).
I set it to my new wireless network.
I set IPv4 Address: 192.168.22.2
IPv4 netmask: 255.255.255.0
IPv4 gateway: 192.168.12.28
I invent the numbers.
I don't know what to write.
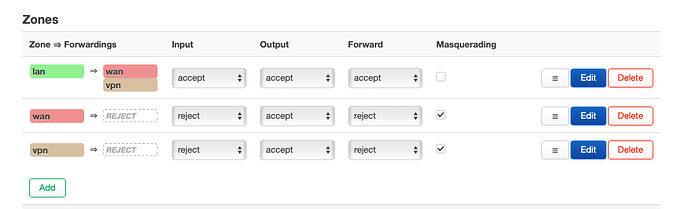
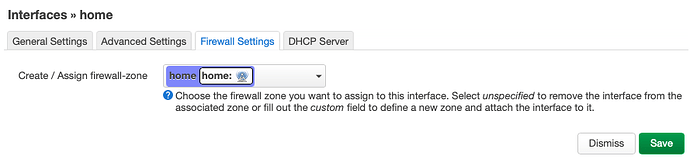
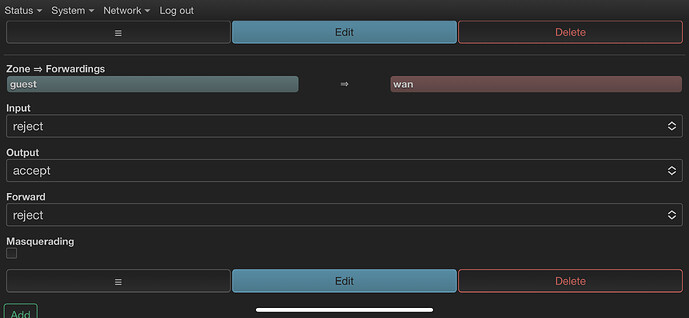
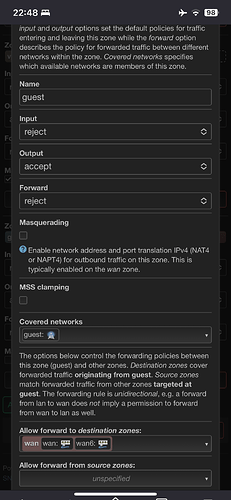
I create a firewall zone called lan2 identical to lan.
Covered networks: lan2
Allow forward to destination zone: "wan wan6"
This doesn't work.
And all the network didn't work.
When I delete this configuration all was restored.
I think that the solution must be similar to this.
Can someone help me?
Don't specify a gateway. In the usual configuration, there is only one gateway (default route-- path to the Internet) and it is will be through wan. Usually the gateway is assigned automatically by DHCP or pppoe from the ISP.
There are wiki pages about a guest network. That is what you are trying to do. The guest network IP address is usually .1 in a separate /24 from the lan and the wan. It's conventional for X.Y.Z.1 to be the router in a /24 network, though that is not required.
Since you've edited your question to also ask how to make only some devices or networks to go through a VPN, that is done with policy based routing-- search the wiki for that.
Thank you.
Now I’ll search how to create a guest network.
And I think that later I’ll make some question for the rules.
Because I can set many server profiles in one wireguard interface, so I think that could be possible to assign a profile to a specific app.
P.s. I find this guide:
It’s very clear.
Tomorrow I’ll try to create a line like this.
I find a very good video on youtube that explain how to make guest network.
It's identical to the guide I link.
I tried again, but my connection doesn't work.
Can someone help me?
Thanks
I've tried again to try to fix the problem but I can't.
I masked the LAN, but nothing changed.
The problem is probably in the firewall configuration, but I can't find where, because the configurations I find in the guides don't work with me.
But isn't it possible that the firmware that maybe isn't stable and has a bug creates problems?
I made test for more than 6 hours.
I reinstall many times openwrt.
If I configure it from a fresh install I can create a guess network.
But in this case the vpn doesn't work.
If I configure before the vpn with wireguard the guest network doesn't work.
I don't know how to do.
hi,
let's confirm couple of things:
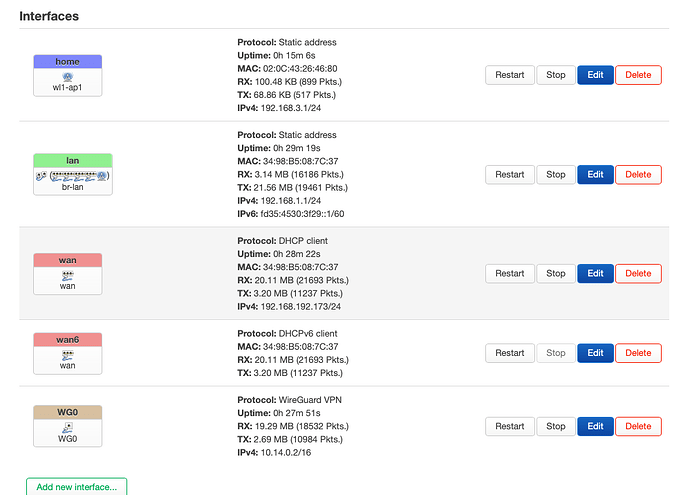
- in screenshots your guest network called home using *.3.1 address but in config it is *.2.1. which one is the latest used?
- you have not showed your latest firewall setup. please make sure there is zone forwarding rule allowing from home to forward to wan. this is crucial to let home users to access wan zone, i.e the internet by allowing making outgoing traffic from home to wan. (the reply from wan to originator in home is automatically taken care of.)
can you somehow (*) copy the content of following files pls? screenshots are hard to read and not always show all details.
files usually asked for troubleshooting are:
- /etc/config/network
- /etc/config/dhcp
- /etc/config/firewall
please obscure sensitive data (e.g. password, public/private key) if you share here and use forum engine's preformatted text/CTRL+e to format your input.
(*) to access these files, either SSH into your router and use basic linux knowledge (e.g. cat command); or from Windows pc use WinSCP to connect to router and browse through files/directories.
when you say not work what exactly does not work? your guest clients receive a DHCP lease, get a valid IP address? can they use dns, e.g. nslookup <put whatever internet hostname you fancy>? or totally nothing: you have a valid ip address assigned to client but from it cannot even ping any public ip address?
Thank you very much for your help.
I can connect to the network with a valid ip and I can ping connection.
All works correctly, only internet access doesn't work.
Network:
oot@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd86:0fdc:14d5::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
config interface 'wg0'
option proto 'wireguard'
option private_key ‘x’xxxxxxxxxxx
list addresses '10.14.0.2/16'
list dns '162.252.172.57'
list dns '149.154.159.92'
config wireguard_wg0
option description 'it-mil.conf'
option public_key ‘xxxxxxxxxxx’xx
list allowed_ips '0.0.0.0/0'
option endpoint_host 'it-mxxxxxxxfsxxxxrk.com'
option endpoint_port '51820'
option route_allowed_ips '1'
config interface 'guest'
option proto 'static'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
DHCP:
root@OpenWrt:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option filter_aaaa '0'
option filter_a '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'guest'
option interface 'guest'
option start '100'
option limit '150'
option leasetime '12h'
Firewall:
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option mtu_fix '1'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
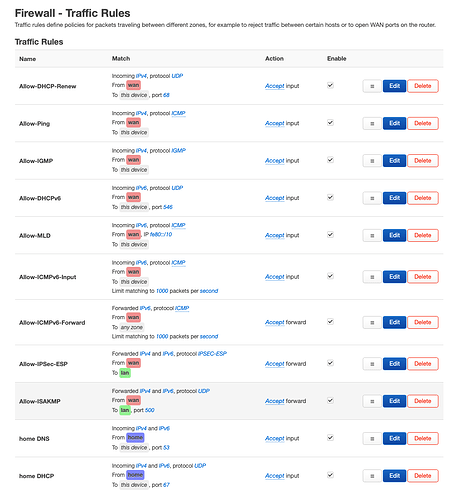
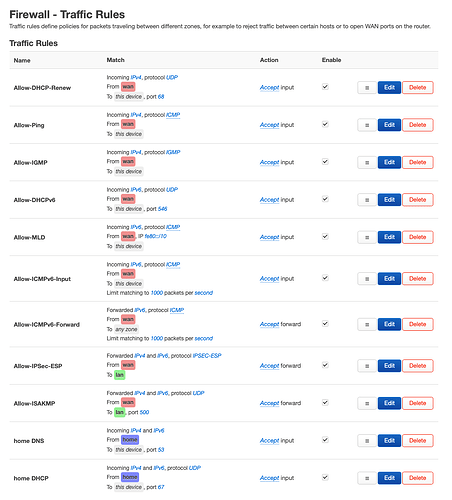
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'vpn'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
list network 'wg0'
config forwarding
option src 'lan'
option dest 'vpn'
config zone
option name 'guest'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'guest'
config forwarding
option src 'guest'
option dest 'wan'
config rule
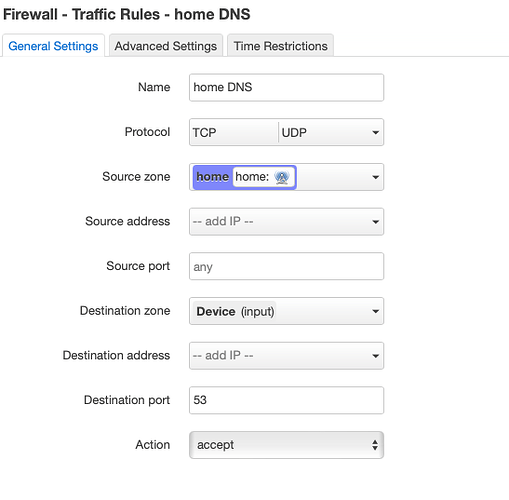
option name 'Guest-DNS'
option src 'guest'
option dest_port '53'
option target 'ACCEPT'
config rule
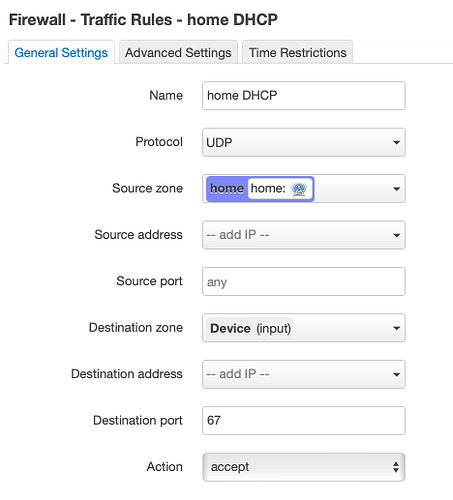
option name 'Guest-DHCP'
list proto 'udp'
option src 'guest'
option dest_port '67'
option target 'ACCEPT'
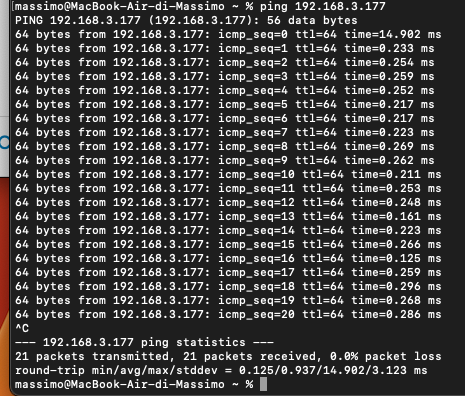
so, your client receives a DHCP lease -that's ok. your client receives 192.168.3.177, right?
but from the client (192.168.3.177) you ping itself, that is not what we want. pls from the client ping the guest interface's address, i.e. on client ping 192.168.3.1.
also, according to firewall config:
config forwarding
option src 'guest'
option dest 'wan'
this allows guest to reach wan, so in theory this should be enough.
so please also ping 1.1.1.1 from client. and check on the router nft list chain inet fw4 forward_guest. you should see something similar:
table inet fw4 {
chain forward_guest {
jump accept_to_wan comment "!fw4: Accept guest to wan forwarding"
jump reject_to_guest
}
verify if jump accept_to_wan exists.
if still does not work you may disable ipv6 on your client - that may interfere.
but from first look, your config looks ok. to me at least, someone else may find the problem if any though.
Maybe if everything is routed via the VPN, the guest wifi will not have internet (maybe that is the desired outcome but otherwise perhaps add ?:
config forwarding
option src 'guest'
option dest 'vpn'
Now I'll try, but I don't want all with VPN.
I'm doing a second network for this thing.
At the end I would like to have a normal line and a guest line with VPN.
Then you have to use Policy Based Routing.
If you do not use PBR and have a default WG client installed everything is going via the VPN, except your guest wifi that is blocked because it is not allowed to go out via the VPN.
If that is what you want, excellent, just leave it as it is ![]()
I try both solution
config forwarding
option src 'guest'
option dest 'vpn'
And
config forwarding
option src 'guest'
option dest 'vpn'
I add this at the end of firewall file.
but they don't work.
I don't know how to check on the router this:
nft list chain inet fw4 forward_guest
I want the VPN only on guest network, not in all the network.
But this is the next problem to solve.
let's fix internet access first.
can you SSH into your router? you already did cat /etc/config/network so i assume it was via SSH, do the same: login and run command nft ... .
if you want selective outgoing routing it was already mentioned you need Policy Based Routing (PBR). check wiki how it works.
but take the next step first, i.e. verify if from client you can ping the router guest's ip address.
then run the nft ... command to verify if guest to wan rule exists.