Good evening.
I've been using openwrt on a single router for a couple months now and I'm loving it, but I recently upgraded to a bigger house and am having wireless range issues, so I purchased another router to extend my networks. I'm looking for some help in how I could go about configuring everything correctly, this is what I want to eventually end up with:
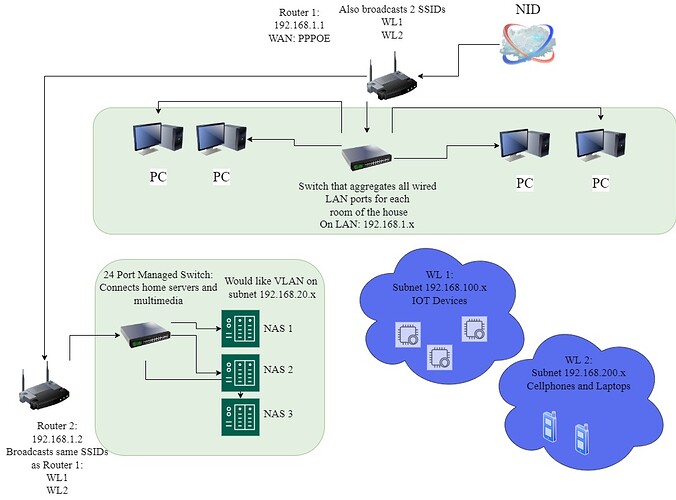
Router 1 is a Netgear R7800 running openwrt.
Router 2 is a Linksys EA8500 running openwrt.
Router 1 takes in the ethernet cable to the WAN port configured as PPPOE. The 1st port goes to a smaller unmanaged 8 port switch that just connects to the houses wired LAN ports, these stay on the base subnet of 192.168.1.x
It also broadcasts the 2 wireless networks, one for home IOT devices on subnet 192.168.100.x, and the other is for laptops and phones on subnet 192.168.200.x
The second port runs to the other side of the house and connects to the LAN 1 port of router 2. Router 2 is configured with the address 192.168.1.2, and was configured utilizing the "Dumb Access Point" tutorial located at: https://openwrt.org/docs/guide-user/network/wifi/dumbap .
The second port of router2 goes to a 24 port managed switch that connects the home multimedia servers and NAS. These should be on their own VLAN with the subnet 192.168.20.x
I'm just looking for some tips on how to correctly configure this. I'm currently having problems/questions about:
1: I can't connect to router 2 without directly plugging into it with a laptop and assigning a static IP of 192.168.1.x
2. Router 2 doesn't show any wired devices connected to it (this might be normal since DHCP is disabled?)
3. How do I correctly configure the 192.168.20.x VLAN so both routers recognize it? Can it all be handled from router 1, even though router 2 and the devices connected to it are on the same port with router 2 being assigned 192.168.1.2?
4. Do the ports on switch 2 also need to be tagged with the VID?
5. I'm assuming the VLANs need to be configured and matching on both routers?
Thank you for your help.