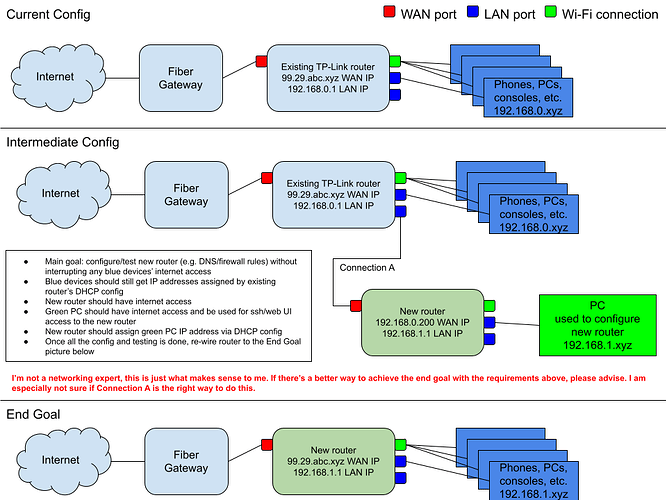
Hi all, new user, requisite apology at the end*
I want to do all the DCHP and DNS (filtering for ads and parental controls) configuration of my new router behind my existing router so I can test it without interrupting current internet access in our home.
The existing router is 192.168.0.1 to its clients. I have the new router's WAN port connected to a LAN port on the existing router, and the new router is 192.168.0.200 on the existing router's network. I can access it from computers on the existing network via the web interface @ http://192.168.0.200 just fine, and ssh@192.168.0.200.
Meanwhile, the new router's IP address for its LAN is 192.168.8.1. It also has DHCP enabled and some settings related to DNS filtering I am now trying to test.
So I connect a laptop to a LAN port on the new router (and turn off wifi on the laptop) but I never get a 192.168.8.x address assigned. It just spins forever "connecting". I can't even ping 192.168.8.1. I can, however, ping 8.8.8.8 from the ssh session into the new router, so it seems the new router can access the internet.
But ultimately what I want is for the existing router to continue to provide DHCP/internet access for its clients, including the new router, and for the new router to provide DHCP/internet access for its clients. Clients connected to the existing router would continue to get a 192.168.0.x IP address, and clients connected to the new router would get a 192.168.8.x IP address.
Without getting into all the details, what am I missing here? Basically all other config is untouched. I don't know much about NAT, I suspect it might be that. I can provide the details if that helps but I want to narrow it down a bit first.
*I did search this forum and google for existing answers but couldn't find anything quite the same as my scenario, or the posts included so many details it made it unclear if it was the same or not. Most people seem to want one DHCP server for the whole network, but I intend to totally replace the existing router with the new one when I'm done testing, so that's why I want both for now.
Thanks!