techmol
December 11, 2023, 10:02am
1
I tried configuring Wireguard client using the instructions provided here: [Instruction] Config NordVPN wireguard (Nordlynx) on OpenWrt
However, when creating an Interface I run into difficulties.
At first it would not accept the public key I put in? I used the one from runnint this command:curl -s "https://api.nordvpn.com/v1/servers/recommendations?&filters\[servers_technologies\]\[identifier\]=wireguard_udp&limit=1"|jq -r '.[]|.hostname, .station, (.locations|.[]|.country|.city.name), (.locations|.[]|.country|.name), (.technologies|.[].metadata|.[].value), .load'
However, now I can't even open the interface anymore (see screenshot).
When I click the link, it shows me 21 packages starting with 'luci-proto'. Which one do I need?
frollic
December 11, 2023, 10:05am
2
try installing luci-proto-wireguard, it should pull all the dependencies you need.
1 Like
techmol
December 11, 2023, 11:03am
3
Ok, that helped. Thank you.
techmol
December 11, 2023, 11:49am
4
I continued with the instructions provided here. .
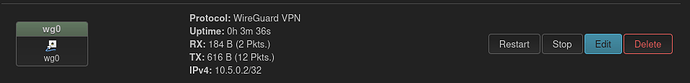
I was able to get the Interface (wg0) running:
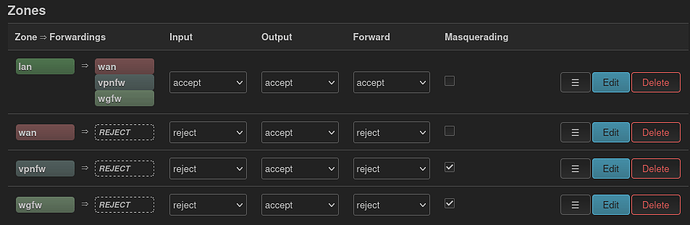
I also set up the firewall rules:
This is the firewall config:
cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone 'lan'
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone 'wan'
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option mtu_fix '1'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'wan-local-wireguard'
list proto 'udp'
option src 'wan'
option dest_port '51820'
option target 'ACCEPT'
config zone
option name 'vpnfw'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'novpn'
config forwarding
option src 'lan'
option dest 'vpnfw'
config zone
option name 'wgfw'
option output 'ACCEPT'
option forward 'REJECT'
list network 'wg0'
option input 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wgfw'
But the traffic is not routed through the vpn interface (wg0). What is wrong?
techmol
December 12, 2023, 12:39pm
5
The Wireguard status is positve:
For some reason it's still not working. No traffic is routed through Wireguard.
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone 'lan'
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone 'wan'
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option mtu_fix '1'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'wan-local-wireguard'
list proto 'udp'
option src 'wan'
option dest_port '51820'
option target 'ACCEPT'
config zone
option name 'vpnfw'
option input 'REJECT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option output 'ACCEPT'
list network 'novpn'
config forwarding
option src 'lan'
option dest 'vpnfw'
config zone
option name 'wgfirewall'
option output 'ACCEPT'
option forward 'REJECT'
option input 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wireg'
config forwarding
option src 'lan'
option dest 'wgfirewall'
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'ffa0:ff3f:ff34::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.201.1'
config interface 'wan'
option device 'eth1'
option proto 'static'
option ipaddr '192.168.100.35'
option netmask '255.255.255.0'
option gateway '192.168.100.1'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 0'
config interface 'novpn'
option proto 'none'
option device 'tun0'
config interface 'wireg'
option proto 'wireguard'
option private_key '8gfd09g8fsdß09g8fdß0g8dfß0g8ffsdfsd'
list addresses '10.5.0.2'
option mtu '1420'
config wireguard_wireg
option description 'ca10.nordvpn.com'
option public_key '8gfd09g8fsdß09g8fdß0g8dfß0g8ffsdfsd='
list allowed_ips '0.0.0.0/0'
option endpoint_host 'ca10.nordvpn.com'
option endpoint_port '51820'
option persistent_keepalive '25'
frollic
December 12, 2023, 12:41pm
6
1 Like
techmol
December 12, 2023, 12:50pm
7
For some reason, it's working with OVPN, but not with wg. I have the same firewall settings for ovpn (vpnfw) as for wireguard (wgfirewall).
krazeh
December 12, 2023, 1:07pm
8
Add option route_allowed_ips '1' to the above bit of config. Then restart the WG interface.
2 Likes
mk24
December 12, 2023, 1:13pm
9
Yes, route_allowed_ips needs to be set. Also do not run OpenVPN and Wireguard at the same time.
Forwarding between networks is a two-step process.
The routing table(s) must direct it to occur (default route via wireguard in this case).
The firewall must allow it to occur.
In other words, setting lan->wireguard forward in the firewall is only half of the process.
2 Likes
system
December 22, 2023, 1:13pm
10
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.