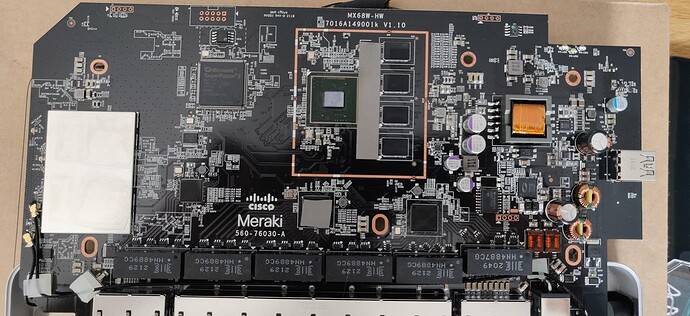
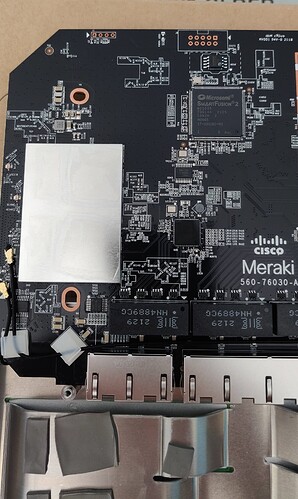
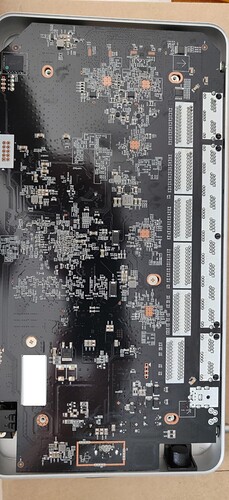
Post was too big - the rest of the boot log:
[ 0.350193] Qman: FQID allocator includes range 32768:32768
[ 0.355847] Qman: CGRID allocator includes range 0:256
[ 0.361151] Qman: pool channel allocator includes range 1025:15
[ 0.367196] No USDPAA memory, no 'fsl,usdpaa-mem' in device-tree
[ 0.373256] fsl-ifc 1530000.ifc: Freescale Integrated Flash Controller
[ 0.379821] fsl-ifc 1530000.ifc: IFC version 1.4, 8 banks
[ 0.385856] clocksource: Switched to clocksource arch_sys_counter
[ 0.392043] VFS: Disk quotas dquot_6.6.0
[ 0.396010] VFS: Dquot-cache hash table entries: 512 (order 0, 4096 bytes)
[ 0.406751] NET: Registered protocol family 2
[ 0.411388] TCP established hash table entries: 32768 (order: 6, 262144 bytes)
[ 0.418797] TCP bind hash table entries: 32768 (order: 7, 524288 bytes)
[ 0.425880] TCP: Hash tables configured (established 32768 bind 32768)
[ 0.432485] UDP hash table entries: 2048 (order: 4, 65536 bytes)
[ 0.438571] UDP-Lite hash table entries: 2048 (order: 4, 65536 bytes)
[ 0.445154] NET: Registered protocol family 1
[ 0.449657] Unpacking initramfs...
[ 2.668251] Freeing initrd memory: 80144K
[ 2.672520] hw perfevents: enabled with armv8_pmuv3 PMU driver, 7 counters available
[ 2.681556] Initialise system trusted keyrings
[ 2.686189] workingset: timestamp_bits=46 max_order=20 bucket_order=0
[ 2.719697] Key type asymmetric registered
[ 2.723822] Asymmetric key parser 'x509' registered
[ 2.728957] Block layer SCSI generic (bsg) driver version 0.4 loaded (major 248)
[ 2.736392] io scheduler noop registered
[ 2.740330] io scheduler deadline registered
[ 2.744707] io scheduler cfq registered (default)
[ 2.750268] OF: PCI: host bridge /soc/pcie@3500000 ranges:
[ 2.755791] OF: PCI: IO 0x4800010000..0x480001ffff -> 0x00000000
[ 2.762091] OF: PCI: MEM 0x4840000000..0x487fffffff -> 0x40000000
[ 2.768520] layerscape-pcie 3500000.pcie: PCI host bridge to bus 0000:00
[ 2.775258] pci_bus 0000:00: root bus resource [bus 00-ff]
[ 2.780769] pci_bus 0000:00: root bus resource [io 0x0000-0xffff]
[ 2.786979] pci_bus 0000:00: root bus resource [mem 0x4840000000-0x487fffffff] (bus address [0x40000000-0x7fffffff])
[ 2.797792] pci 0000:00:00.0: BAR 6: assigned [mem 0x4840000000-0x48400007ff pref]
[ 2.805402] pci 0000:00:00.0: PCI bridge to [bus 01-ff]
[ 2.810705] OF: PCI: host bridge /soc/pcie@3600000 ranges:
[ 2.816221] OF: PCI: IO 0x5000010000..0x500001ffff -> 0x00000000
[ 2.822520] OF: PCI: MEM 0x5040000000..0x507fffffff -> 0x40000000
[ 2.828917] layerscape-pcie 3600000.pcie: PCI host bridge to bus 0001:00
[ 2.835653] pci_bus 0001:00: root bus resource [bus 00-ff]
[ 2.841165] pci_bus 0001:00: root bus resource [io 0x10000-0x1ffff] (bus address [0x0000-0xffff])
[ 2.850170] pci_bus 0001:00: root bus resource [mem 0x5040000000-0x507fffffff] (bus address [0x40000000-0x7fffffff])
[ 2.860959] pci 0001:00:00.0: BAR 6: assigned [mem 0x5040000000-0x50400007ff pref]
[ 2.868569] pci 0001:00:00.0: PCI bridge to [bus 01-ff]
[ 2.874825] Freescale LS2 console driver
[ 2.878879] fsl-ls2-console: device fsl_mc_console registered
[ 2.884767] fsl-ls2-console: device fsl_aiop_console registered
[ 3.036892] Serial: 8250/16550 driver, 4 ports, IRQ sharing disabled
[ 3.054257] console [ttyS0] disabled
[ 3.057888] 21c0500.serial: ttyS0 at MMIO 0x21c0500 (irq = 38, base_baud = 25000000) is a 16550A
[ 3.066731] console [ttyS0] enabled
[ 3.066731] console [ttyS0] enabled
[ 3.073716] bootconsole [uart8250] disabled
[ 3.073716] bootconsole [uart8250] disabled
[ 3.082668] 21c0600.serial: ttyS1 at MMIO 0x21c0600 (irq = 38, base_baud = 25000000) is a 16550A
[ 3.091865] 21d0500.serial: ttyS2 at MMIO 0x21d0500 (irq = 39, base_baud = 25000000) is a 16550A
[ 3.101063] 21d0600.serial: ttyS3 at MMIO 0x21d0600 (irq = 39, base_baud = 25000000) is a 16550A
[ 3.110265] Trying to register dev faulty etc
[ 3.120457] loop: module loaded
[ 3.124409] at24 0-0050: 8192 byte 24c64 EEPROM, writable, 1 bytes/write
[ 3.131275] hisi_sas: driver version v1.6
[ 3.136868] nand: device found, Manufacturer ID: 0x2c, Chip ID: 0xa3
[ 3.143239] nand: Micron MT29F8G08ABBCAH4
[ 3.147243] nand: 1024 MiB, SLC, erase size: 256 KiB, page size: 4096, OOB size: 224
[ 3.155473] Bad block table found at page 262080, version 0x01
[ 3.162210] Bad block table found at page 262016, version 0x01
[ 3.168641] 3 ofpart partitions found on MTD device 7e800000.flash
[ 3.174816] Creating 3 MTD partitions on "7e800000.flash":
[ 3.180297] 0x000000000000-0x000001800000 : "mtdraw-uboot"
[ 3.187337] 0x000001800000-0x000002000000 : "oops"
[ 3.304517] random: fast init done
[ 3.433424] mtdoops: Attached to MTD device 1
[ 3.438207] 0x000002000000-0x000040000000 : "mtdraw-ubi"
[ 3.444771] fsl,ifc-nand 7e800000.nand: IFC NAND device at 0x7e800000, bank 0
[ 3.453498] libphy: Fixed MDIO Bus: probed
[ 3.457602] tun: Universal TUN/TAP device driver, 1.6
[ 3.462647] tun: (C) 1999-2004 Max Krasnyansky <maxk@qualcomm.com>
[ 3.469135] libphy: Freescale XGMAC MDIO Bus: probed
[ 3.474163] libphy: Freescale XGMAC MDIO Bus: probed
[ 3.479187] libphy: Freescale XGMAC MDIO Bus: probed
[ 3.484353] libphy: Freescale XGMAC MDIO Bus: probed
[ 3.489507] libphy: Freescale XGMAC MDIO Bus: probed
[ 3.494658] libphy: Freescale XGMAC MDIO Bus: probed
[ 3.499812] libphy: Freescale XGMAC MDIO Bus: probed
[ 3.504965] libphy: Freescale XGMAC MDIO Bus: probed
[ 3.510115] libphy: Freescale XGMAC MDIO Bus: probed
[ 3.527296] Freescale FM module, FMD API version 21.1.0
[ 3.535218] Freescale FM Ports module
[ 3.538891] fsl_mac: fsl_mac: FSL FMan MAC API based driver sdk_dpaa mac-api.c
[ 3.546626] drivers/net/ethernet/freescale/sdk_fman/Peripherals/FM/MAC/memac.c:93 SetupSgmiiInternalPhy(macId=1, enetMode=000803e8, phyAddr=0)
[ 3.559472] fsl_mac 1ae2000.ethernet: FMan MEMAC
[ 3.564088] fsl_mac 1ae2000.ethernet: FMan MAC address: 00:11:22:33:44:11
[ 3.571100] fsl_mac 1ae4000.ethernet: FMan MEMAC
[ 3.575719] fsl_mac 1ae4000.ethernet: FMan MAC address: 00:11:22:33:44:22
[ 3.582737] drivers/net/ethernet/freescale/sdk_fman/Peripherals/FM/MAC/memac.c:93 SetupSgmiiInternalPhy(macId=0, enetMode=000803e8, phyAddr=0)
[ 3.595572] fsl_mac 1af0000.ethernet: FMan MEMAC
[ 3.600186] fsl_mac 1af0000.ethernet: FMan MAC address: 00:11:22:33:44:66
[ 3.607012] fsl_dpa: FSL DPAA Ethernet driver
[ 3.612298] fsl_dpa soc:fsl,dpaa:ethernet@2: Skip RX PCD High Priority FQs initialization
[ 3.624108] fsl_dpa: fsl_dpa: Probed interface eth0
[ 3.629683] fsl_dpa soc:fsl,dpaa:ethernet@1: Skip RX PCD High Priority FQs initialization
[ 3.641809] fsl_dpa: fsl_dpa: Probed interface eth1
[ 3.647496] fsl_dpa soc:fsl,dpaa:ethernet@8: Skip RX PCD High Priority FQs initialization
[ 3.659820] fsl_dpa: fsl_dpa: Probed interface eth2
[ 3.664756] fsl_advanced: FSL DPAA Advanced drivers:
[ 3.669721] fsl_proxy: FSL DPAA Proxy initialization driver
[ 3.675557] fsl_oh: FSL FMan Offline Parsing port driver
[ 3.681109] PPP generic driver version 2.4.2
[ 3.755192] PPP BSD Compression module registered
[ 3.759909] PPP Deflate Compression module registered
[ 3.764958] NET: Registered protocol family 24
[ 3.769460] usbcore: registered new interface driver cdc_ether
[ 3.775319] usbcore: registered new interface driver cdc_eem
[ 3.780989] usbcore: registered new interface driver net1080
[ 3.786657] usbcore: registered new interface driver zaurus
[ 3.792246] usbcore: registered new interface driver sierra_net
[ 3.798180] usbcore: registered new interface driver cdc_ncm
[ 3.804844] ehci_hcd: USB 2.0 'Enhanced' Host Controller (EHCI) Driver
[ 3.811379] ehci-pci: EHCI PCI platform driver
[ 3.815845] ohci_hcd: USB 1.1 'Open' Host Controller (OHCI) Driver
[ 3.822022] ohci-pci: OHCI PCI platform driver
[ 3.826894] xhci-hcd xhci-hcd.0.auto: xHCI Host Controller
[ 3.832388] xhci-hcd xhci-hcd.0.auto: new USB bus registered, assigned bus number 1
[ 3.840131] xhci-hcd xhci-hcd.0.auto: hcc params 0x0220f66d hci version 0x100 quirks 0x100010810
[ 3.848934] xhci-hcd xhci-hcd.0.auto: irq 48, io mem 0x02f00000
[ 3.855197] hub 1-0:1.0: USB hub found
[ 3.859120] hub 1-0:1.0: 1 port detected
[ 3.863211] xhci-hcd xhci-hcd.0.auto: xHCI Host Controller
[ 3.868751] xhci-hcd xhci-hcd.0.auto: new USB bus registered, assigned bus number 2
[ 3.876749] hub 2-0:1.0: USB hub found
[ 3.880513] hub 2-0:1.0: 1 port detected
[ 3.884666] xhci-hcd xhci-hcd.1.auto: xHCI Host Controller
[ 3.890157] xhci-hcd xhci-hcd.1.auto: new USB bus registered, assigned bus number 3
[ 3.897921] xhci-hcd xhci-hcd.1.auto: hcc params 0x0220f66d hci version 0x100 quirks 0x100010810
[ 3.906724] xhci-hcd xhci-hcd.1.auto: irq 49, io mem 0x03000000
[ 3.912983] hub 3-0:1.0: USB hub found
[ 3.916747] hub 3-0:1.0: 1 port detected
[ 3.920825] xhci-hcd xhci-hcd.1.auto: xHCI Host Controller
[ 3.926311] xhci-hcd xhci-hcd.1.auto: new USB bus registered, assigned bus number 4
[ 3.934284] hub 4-0:1.0: USB hub found
[ 3.938050] hub 4-0:1.0: 1 port detected
[ 3.942179] xhci-hcd xhci-hcd.2.auto: xHCI Host Controller
[ 3.947668] xhci-hcd xhci-hcd.2.auto: new USB bus registered, assigned bus number 5
[ 3.955416] xhci-hcd xhci-hcd.2.auto: hcc params 0x0220f66d hci version 0x100 quirks 0x100010810
[ 3.964221] xhci-hcd xhci-hcd.2.auto: irq 50, io mem 0x03100000
[ 3.970484] hub 5-0:1.0: USB hub found
[ 3.974249] hub 5-0:1.0: 1 port detected
[ 3.978319] xhci-hcd xhci-hcd.2.auto: xHCI Host Controller
[ 3.983804] xhci-hcd xhci-hcd.2.auto: new USB bus registered, assigned bus number 6
[ 3.991826] hub 6-0:1.0: USB hub found
[ 3.995590] hub 6-0:1.0: 1 port detected
[ 3.999753] usbcore: registered new interface driver cdc_acm
[ 4.005410] cdc_acm: USB Abstract Control Model driver for USB modems and ISDN adapters
[ 4.013478] usbcore: registered new interface driver usb-storage
[ 4.019528] usbcore: registered new interface driver usbserial
[ 4.025377] usbcore: registered new interface driver option
[ 4.030958] usbserial: USB Serial support registered for GSM modem (1-port)
[ 4.038076] usbcore: registered new interface driver qcserial
[ 4.043828] usbserial: USB Serial support registered for Qualcomm USB modem
[ 4.050817] usbcore: registered new interface driver sierra
[ 4.056394] usbserial: USB Serial support registered for Sierra USB modem
[ 4.063509] input: soc:gpio_keys as /devices/platform/soc/soc:gpio_keys/input/input0
[ 4.071523] i2c /dev entries driver
[ 4.075400] ptp_qoriq: device tree node missing required elements, try automatic configuration
[ 4.084149] pps pps0: new PPS source ptp0
[ 4.089066] lm90 0-004c: Failed to initialize device
[ 4.094453] imx2-wdt 2ad0000.wdog: timeout 60 sec (nowayout=1)
[ 4.100766] sdhci: Secure Digital Host Controller Interface driver
[ 4.106952] sdhci: Copyright(c) Pierre Ossman
[ 4.111303] Synopsys Designware Multimedia Card Interface Driver
[ 4.117777] sdhci-pltfm: SDHCI platform and OF driver helper
[ 4.169868] mmc0: SDHCI controller on 1560000.esdhc [1560000.esdhc] using ADMA 64-bit
[ 4.205693] lp5562 0-0030: internal clock used
[ 4.216247] platform caam_qi: Linux CAAM Queue I/F driver initialised
[ 4.222704] caam 1700000.crypto: Entropy delay = 3200
[ 4.227774] caam 1700000.crypto: Instantiated RNG4 SH0
[ 4.247826] caam 1700000.crypto: Instantiated RNG4 SH1
[ 4.252958] caam 1700000.crypto: device ID = 0x0a12060000000000 (Era 8)
[ 4.259565] caam 1700000.crypto: job rings = 4, qi = 1
[ 4.267895] caam algorithms registered in /proc/crypto
[ 4.274728] platform caam_qi: algorithms registered in /proc/crypto
[ 4.281868] caam_jr 1710000.jr: registering rng-caam
[ 4.286880] caam 1700000.crypto: caam pkc algorithms registered in /proc/crypto
[ 4.294327] usbcore: registered new interface driver usbhid
[ 4.299896] usbhid: USB HID core driver
[ 4.304495] Freescale USDPAA process driver
[ 4.308678] fsl-usdpaa: no region found
[ 4.312506] Freescale USDPAA process IRQ driver
[ 4.317387] nf_conntrack version 0.5.0 (16384 buckets, 65536 max)
[ 4.323671] ip_tables: (C) 2000-2006 Netfilter Core Team
[ 4.329010] Initializing XFRM netlink socket
[ 4.333586] NET: Registered protocol family 10
[ 4.338608] ip6_tables: (C) 2000-2006 Netfilter Core Team
[ 4.344065] sit: IPv6, IPv4 and MPLS over IPv4 tunneling driver
[ 4.350298] NET: Registered protocol family 17
[ 4.354763] NET: Registered protocol family 15
[ 4.359230] bridge: filtering via arp/ip/ip6tables is no longer available by default. Update your scripts to load br_netfilter if you need this.
[ 4.372184] l2tp_core: L2TP core driver, V2.0
[ 4.376539] l2tp_ppp: PPPoL2TP kernel driver, V2.0
[ 4.381324] 8021q: 802.1Q VLAN Support v1.8
[ 4.385860] Loading compiled-in X.509 certificates
[ 4.392622] Loaded X.509 cert 'Cisco Meraki: Auto-generated kernel signing key: d08ae62b90f897058a35e3b5f8b20e04c616ec74'
[ 4.404190] Key type encrypted registered
[ 4.408797] libphy: mdio_mux: probed
[ 4.412405] libphy: mdio_mux: probed
[ 4.415977] mdio-mux-gpio 1a00000.fman:mdio-mux: Version 1.0
[ 4.421779] ubi0: attaching mtd2
[ 8.099541] ubi0: scanning is finished
[ 8.111168] ubi0: attached mtd2 (name "mtdraw-ubi", size 992 MiB)
[ 8.117292] ubi0: PEB size: 262144 bytes (256 KiB), LEB size: 253952 bytes
[ 8.124167] ubi0: min./max. I/O unit sizes: 4096/4096, sub-page size 4096
[ 8.130951] ubi0: VID header offset: 4096 (aligned 4096), data offset: 8192
[ 8.137907] ubi0: good PEBs: 3964, bad PEBs: 4, corrupted PEBs: 0
[ 8.143993] ubi0: user volume: 4, internal volumes: 1, max. volumes count: 128
[ 8.151207] ubi0: max/mean erase counter: 75/44, WL threshold: 4096, image sequence number: 945605211
[ 8.160417] ubi0: available PEBs: 841, total reserved PEBs: 3123, PEBs reserved for bad PEB handling: 76
[ 8.169898] hctosys: unable to open rtc device (rtc0)
[ 8.173865] ubi0: background thread "ubi_bgt0d" started, PID 2019
[ 8.182426] Freeing unused kernel memory: 1856K
[ 8.200053] early_init: linked /dev/meraki-board-config to /sys/bus/i2c/devices/0-0050/eeprom for wired-arm64
[ 8.225026] random: board_data_conf: uninitialized urandom read (4 bytes read)
[ 8.284353] random: board_data_conf: uninitialized urandom read (4 bytes read)
[ 8.348012] random: board_data_conf: uninitialized urandom read (4 bytes read)
[ 8.475109] early_init: meraki_MX68 600-76020, (52) MX68, 1, [Serial / MAC Removed], arch:arm64, board:wired-arm64, hw:MX68, pid:2039, ppid:2037, fd1:/early_init.log, fd2:/early_init.log
[ 8.576540] UBIFS (ubi0:0): background thread "ubifs_bgt0_0" started, PID 2169
[ 8.634422] UBIFS (ubi0:0): recovery needed
[ 8.792493] UBIFS (ubi0:0): recovery completed
[ 8.796977] UBIFS (ubi0:0): UBIFS: mounted UBI device 0, volume 0, name "storage"
[ 8.804454] UBIFS (ubi0:0): LEB size: 253952 bytes (248 KiB), min./max. I/O unit sizes: 4096 bytes/4096 bytes
[ 8.814360] UBIFS (ubi0:0): FS size: 533807104 bytes (509 MiB, 2102 LEBs), journal size 26664960 bytes (25 MiB, 105 LEBs)
[ 8.825306] UBIFS (ubi0:0): reserved for root: 4952683 bytes (4836 KiB)
[ 8.831914] UBIFS (ubi0:0): media format: w4/r0 (latest is w4/r0), UUID 02A05816-0314-426D-8260-2D303ADF4207, small LPT model
[ 8.846940] early_init done
WARNING! THIS CONSOLE IS LOGGED! UNAUTHORIZED ACCESS FORBIDDEN!
<Meraki> [ 9.122398] S05diagnostic: meraki_MX68 600-76020, (52) MX68, 1, XXXX-XXXX-XXXX, XX:XX:XX:XX:XX:XX, arch:arm64, board:wired-arm64, hw:MX68, pid:2179, ppid:2176, fd1:/dev/kmsg, fd2:/dev/kmsg
[ 9.141887] S05diagnostic done
[ 9.278516] random: crng init done
[ 9.281916] random: 7 urandom warning(s) missed due to ratelimiting
[ 9.379954] S07platform: meraki_MX68 600-76020, (52) MX68, 1, XXXX-XXXX-XXXX, XX:XX:XX:XX:XX:XX, arch:arm64, board:wired-arm64, hw:MX68, pid:2250, ppid:2176, fd1:/S07platform.log, fd2:/S07platform.log
[ 9.573590] S07platform done (rc = 0)
[ 9.802618] S10boot: meraki_MX68 600-76020, (52) MX68, 1, XXXX-XXXX-XXXX, XX:XX:XX:XX:XX:XX, arch:arm64, board:wired-arm64, hw:MX68, pid:2343, ppid:2176, fd1:/dev/kmsg, fd2:/dev/kmsg
[ 9.871001] gpio_meraki_fpga: loading out-of-tree module taints kernel.
[ 9.894663] /etc/init.d/S10boot: [ 9.897802] line 242:
[ 9.900178] board_is_legacy_wireless: not found[ 9.904592]
[ 9.952876] cp: can't stat '/run/*': No such file or directory
[ 10.025520] Quick boot reason lookup:
[ 10.032469] No valid safe config available or fallback disabled, remove unsafe config
[ 10.056365] ip_local_port_range: prefer different parity for start/end values.
[ 10.072938] ICMPv6: process `sysctl' is using deprecated sysctl (syscall) net.ipv6.neigh.default.base_reachable_time - use net.ipv6.neigh.default.base_reachable_time_ms instead
[ 10.222156] setup_ar83xx_switches: initial setup of sw0, sw1 and sw2
[ 10.231100] sw0: Bringing down PHYs (linkneg off) 1-2
[ 10.353331] sw1: Bringing down PHYs (linkneg off) 0-4
[ 10.557343] sw2: Bringing down PHYs (linkneg off) 0-4
[ 10.923881] IPv6: ADDRCONF(NETDEV_UP): eth0: link is not ready
[ 10.930659] Cannot change rx-checksumming
[ 10.935991] Actual changes:
[ 10.938835] scatter-gather: off
[ 10.938835] tx-scatter-gather: off
[ 10.938835] generic-segmentation-offload: off [requested on]
[ 10.951711] Cannot change tcp-segmentation-offload
[ 10.957803] Cannot change rx-vlan-offload
[ 11.398391] IPv6: ADDRCONF(NETDEV_UP): eth1: link is not ready
[ 11.565771] IPv6: ADDRCONF(NETDEV_UP): eth2: link is not ready
[ 11.748378] !!!!! {meraki_watchdog} meraki_watchdog set hardware watchdog timeout to 160
[ 11.798337] ntdp: module license 'Copyright (c) 2014-2020 by cisco Systems, Inc.' taints kernel.
[ 11.807147] Disabling lock debugging due to kernel taint
[ 11.859203] NTKM - ntkm_pid_init - nitro_pid created
[ 11.865651] NTKM - nitro_nbar_mpe_init - nitro_nbar_mpe created
[ 11.872521] NTKM - ntkm_init - Nitro KM loaded
[ 11.886343] proclikefs: unknown parameter 'threads' ignored
[ 11.891923] proclikefs: unknown parameter 'thread_affinity_list' ignored
[ 12.014208] IPv6: ADDRCONF(NETDEV_CHANGE): eth0: link becomes ready
[ 12.125833] click: starting router thread pid 0 (ffff800866eb4200)
[ 12.132036] click: starting router thread pid 0 (ffff800866eb4400)
[ 12.132061] click: starting router thread pid 0 (ffff800866eb4600)
[ 12.405932] IPv6: ADDRCONF(NETDEV_CHANGE): eth1: link becomes ready
[ 12.593183] elts_meraki: no symbol version for _ZNK6String10hard_c_strEv
[ 12.601956] IPv6: ADDRCONF(NETDEV_CHANGE): eth2: link becomes ready
[ 12.657996] elts_meraki: unknown parameter 'threads' ignored
[ 12.663660] elts_meraki: unknown parameter 'thread_affinity_list' ignored
[ 12.761467] Bridge firewalling registered
[ 12.890558] S10boot done
[ 13.121079] S80meraki: meraki_MX68 600-76020, (52) MX68, 1, XXXX-XXXX-XXXX, XX:XX:XX:XX:XX:XX, arch:arm64, board:wired-arm64, hw:MX68, pid:3061, ppid:2176, fd1:/dev/kmsg, fd2:/dev/kmsg
[ 14.111952] RUNIT: installed, starting runsvdir...
[ 14.159448] udevd[3146]: starting version 3.2.9
[ 14.206082] udevd[3146]: specified group 'tty' unknown
[ 14.218376] udevd[3146]: specified group 'dialout' unknown
[ 14.225517] ok: run: strongswan_log_trailer: (pid 3412) 0s, normally down
[ 14.232955] !!!!! {/usr/bin/list_updater} reading /tmp/brain_state failed, error 2 (No such file or directory)
[ 14.235929] tail: can't open '/var/log/strongswan_meraki/current': No such file or directory
[ 14.236285] udevd[3146]: specified group 'kmem' unknown
[ 14.236336] udevd[3146]: specified group 'input' unknown
[ 14.236388] udevd[3146]: specified group 'video' unknown
[ 14.236471] udevd[3146]: specified group 'audio' unknown
[ 14.236582] udevd[3146]: specified group 'lp' unknown
[ 14.236655] udevd[3146]: specified group 'disk' unknown
[ 14.236704] udevd[3146]: specified group 'cdrom' unknown
[ 14.262887] udevd[3146]: starting eudev-3.2.9
[ 14.604816] ok: run: strongswan_meraki_log_trailer: (pid 3371) 0s, normally down
[ 15.118502] down: /service/baykok: 1s; run: log: (pid 3220) 1s
[ 15.125981] 1s; run: log: (pid 3274) 1s
[ 15.125981] run: /service/udev: (pid 3146) 1s; run: log: (pid 3143) 1s
[ 15.125981] down: /service/xl2tpd: 1s; run: log: (pid 3141) 1s
[ 15.125981] down: /service/xl2tpd_log_trailer: 1s
[ 15.149499] RUNIT: runsvdir has launched all supervisors
[ 15.226340] not unlocked
[ 15.236041] tail: /var/log/strongswan_meraki/current has appeared; following end of new file
[ 15.704023] OK
[ 15.707043] Starting ciscotamservices
[ 17.210281] ln: /usr/bin/slowfcgi: File exists
[ 20.285105] !!!!! {/usr/bin/wired_brain} HandlerManager not available: writing directly to "/click/thm/write" ""
[ 20.295402] !!!!! {/usr/bin/wired_brain} open failed for "/click/thm/write", error: No such file or directory
[ 20.374269] !!!!! {/usr/bin/wired_brain} HandlerManager not available: writing directly to "/click/thm/write" ""
[ 20.384511] !!!!! {/usr/bin/wired_brain} open failed for "/click/thm/write", error: No such file or directory
[ 20.510166] !!!!! {/usr/bin/wired_brain} HandlerManager not available: writing directly to "/click/thm/write" ""
[ 20.520408] !!!!! {/usr/bin/wired_brain} open failed for "/click/thm/write", error: No such file or directory
[ 20.589253] !!!!! {/usr/bin/wired_brain} HandlerManager not ready: Writing "/click/config"
[ 20.598020] [3552]: <info> [base-manager] couldn't check support for device '/sys/devices/platform/soc/soc:fsl,dpaa/soc:fsl,dpaa:ethernet@1': not supported by any plugin
[ 20.613774] [3552]: <info> [base-manager] couldn't check support for device '/sys/devices/platform/soc/soc:fsl,dpaa/soc:fsl,dpaa:ethernet@2': not supported by any plugin
[ 20.629289] [3552]: <info> [base-manager] couldn't check support for device '/sys/devices/platform/soc/soc:fsl,dpaa/soc:fsl,dpaa:ethernet@8': not supported by any plugin
[ 27.947136] chatter: rb0/CheckIPHeader@2653: IP header check failed: bad IP version
[ 27.954951] chatter: rb0/CheckIPHeader@2627: IP header check failed: bad IP version
[ 27.965939] chatter: rb0/to_snort/CheckIPHeader@4: IP header check failed: bad IP version
[ 28.167584] In write handler 'write(thm.write / sw0_atheros_hw_intf.cpu_port 0)' for 'hm :: HandlerManager':
[ 28.177418] no element named 'sw0_atheros_hw_intf'
[ 28.182454] In write handler 'write(thm.write / sw0_atheros_hw_intf.set_port_map )' for 'hm :: HandlerManager':
[ 28.192536] no element named 'sw0_atheros_hw_intf'
[ 28.197566] In write handler 'write(thm.write / sw0_atheros_hw_intf.dev_name sw0)' for 'hm :: HandlerManager':
[ 28.207563] no element named 'sw0_atheros_hw_intf'
[ 28.255547] chatter: from_bird :: FromHost: device 'bird' went down
[ 28.261844] chatter: to_bird :: ToHost: device 'bird' went down
[ 28.307083] chatter: from_bird :: FromHost: device 'bird' came up
[ 28.313238] chatter: to_bird :: ToHost: device 'bird' came up
[ 28.403488] chatter: from_bird_autovpn0 :: FromHost: device 'bird_autovpn0' went down
[ 28.411377] chatter: to_bird_autovpn0 :: ToHost: device 'bird_autovpn0' went down
[ 28.471176] chatter: from_bird_autovpn0 :: FromHost: device 'bird_autovpn0' came up
[ 28.478899] chatter: to_bird_autovpn0 :: ToHost: device 'bird_autovpn0' came up
[ 28.611510] chatter: from_bird_autovpn1 :: FromHost: device 'bird_autovpn1' went down
[ 28.619365] chatter: to_bird_autovpn1 :: ToHost: device 'bird_autovpn1' went down
[ 28.679113] chatter: from_bird_autovpn1 :: FromHost: device 'bird_autovpn1' came up
[ 28.686830] chatter: to_bird_autovpn1 :: ToHost: device 'bird_autovpn1' came up
[ 28.819488] chatter: from_bird_misc :: FromHost: device 'bird_misc' went down
[ 28.826674] chatter: to_bird_misc :: ToHost: device 'bird_misc' went down
[ 28.883082] chatter: from_bird_misc :: FromHost: device 'bird_misc' came up
[ 28.890104] chatter: to_bird_misc :: ToHost: device 'bird_misc' came up
[ 29.119498] chatter: from_pimd_lan :: FromHost: device 'pimd-lan' went down
[ 29.126488] chatter: to_pimd_lan :: ToHost: device 'pimd-lan' went down
[ 29.175081] chatter: from_pimd_lan :: FromHost: device 'pimd-lan' came up
[ 29.181930] chatter: to_pimd_lan :: ToHost: device 'pimd-lan' came up
[ 29.339491] chatter: from_pimd_vpn :: FromHost: device 'pimd-vpn' went down
[ 29.346477] chatter: to_pimd_vpn :: ToHost: device 'pimd-vpn' went down
[ 29.383091] chatter: from_pimd_vpn :: FromHost: device 'pimd-vpn' came up
[ 29.389946] chatter: to_pimd_vpn :: ToHost: device 'pimd-vpn' came up
[ 29.654740] chatter: rb0/from_squid_check_ip: IP header check failed: bad IP version
[ 29.702004] !!!!! {/usr/bin/wired_brain} Resetting ClickController!
[ 30.878070] chatter: rb0/cli_h/nbar :: NBAR2 (init) INFO: NBAR2::run_timer nitro_api_dp_create returned dp = 0xffff8008652f9800 rb_instance_id = 0
[ 33.167319] IPv6: ADDRCONF(NETDEV_UP): nextun: link is not ready
[ 33.219186] IPv6: ADDRCONF(NETDEV_CHANGE): nextun: link becomes ready
[ 33.966050] NTKM - ntkm_activate - Activating DP [id 0]
[ 33.976826] NTKM - ntkm_check_for_state_change - DP active [id 0]
[ 38.420548] chatter: rb0/nat/from_host_nat_routing :: IP4RouteTableSetReferencePaint: no route for 208.67.220.220
[ 38.421041] chatter: from_linux_test_client :: FromHost: device 'test_client' went down
[ 38.421057] chatter: _to_linux_test_client :: ToHost: device 'test_client' went down
[ 40.452093] S80meraki done
[ 41.134727] !!!!! {/usr/bin/config_updater} failsafe_mode "value='0' state='0' bootloop='0' ver='1' " ""
[ 62.185605] chatter: rb0/big_acl :: BigACL: skipping undersized restore buffer (buf size: 0)
[ 71.921801] meraki_watchdog: [ 71.924605] reading file /tmp/connection_state
[ 71.929084] : [ 71.930578] No such file or directory
[ 71.934239]
[ 132.081369] meraki_watchdog: [ 132.084172] reading file /tmp/connection_state
[ 132.088616] : [ 132.090105] No such file or directory
[ 132.093757]
[ 192.229666] meraki_watchdog: [ 192.232468] reading file /tmp/connection_state
[ 192.236908] : [ 192.238398] No such file or directory
[ 192.242053]
^@