Hi folks,
I'm struggling with my configuration for cascaded routing:
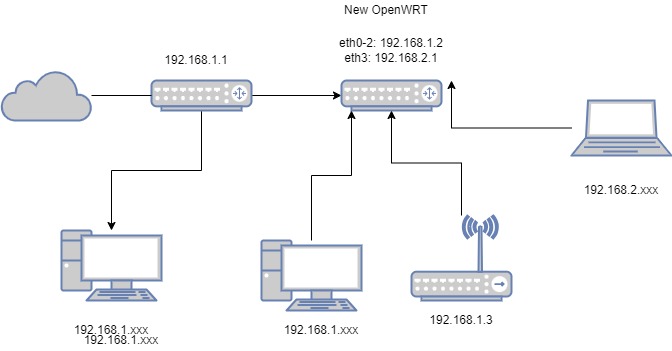
Network 192.168.1.0/24 is my "old" and working network. 192.168.1.1 acting as my normal gateway for all my devices, DHCP, DNS and so on. The typical ISP router.
Now I've added the OpenWRT device. Bridging eth0-2 as LAN Ports and static IP 192.168.1.2. This bridge is connected to various devices such as APs, PCs and so on. Up to here everything is fine and works as expected.
But now I want to create a cabled guest network on eth3. Again static IP on eth3, connecting a device and nothing works from 192.168.2.0/24. No DHCP, no WAN, no LAN. I'm just able to ping eth3 from anywhere. Any suggestions on my configuration?
My current configuration (if anything is missing, please let me know):
# uci show network
network.loopback=interface
network.loopback.device='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fdef:ab1b:f2d9::/48'
network.globals.packet_steering='1'
network.@device[0]=device
network.@device[0].name='br-lan'
network.@device[0].type='bridge'
network.@device[0].ports='eth0' 'eth1' 'eth2'
network.lan=interface
network.lan.device='br-lan'
network.lan.proto='static'
network.lan.ipaddr='192.168.1.2'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.lan.dns='192.168.1.25'
network.lan.gateway='192.168.1.1'
network.@device[1]=device
network.@device[1].type='bridge'
network.@device[1].name='br-guest'
network.@device[1].ports='eth3'
network.guest=interface
network.guest.proto='static'
network.guest.device='br-guest'
network.guest.ipaddr='192.168.2.1'
network.guest.netmask='255.255.255.0'
# uci show firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].input='REJECT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@defaults[0].synflood_protect='1'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[0].network='lan'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-Ping'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='icmp'
firewall.@rule[0].icmp_type='echo-request'
firewall.@rule[0].family='ipv4'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-IGMP'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='igmp'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-DHCPv6'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='udp'
firewall.@rule[2].dest_port='546'
firewall.@rule[2].family='ipv6'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-MLD'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='icmp'
firewall.@rule[3].src_ip='fe80::/10'
firewall.@rule[3].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-ICMPv6-Input'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advert
isement'
firewall.@rule[4].limit='1000/sec'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Forward'
firewall.@rule[5].src='wan'
firewall.@rule[5].dest='*'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-IPSec-ESP'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='lan'
firewall.@rule[6].proto='esp'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-ISAKMP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].dest_port='500'
firewall.@rule[7].proto='udp'
firewall.@rule[7].target='ACCEPT'
firewall.@zone[2]=zone
firewall.@zone[2].name='Guest'
firewall.@zone[2].input='ACCEPT'
firewall.@zone[2].output='ACCEPT'
firewall.@zone[2].forward='ACCEPT'
firewall.@zone[2].network='guest'
firewall.@zone[2].masq='1'
firewall.@forwarding[1]=forwarding
firewall.@forwarding[1].src='Guest'
firewall.@forwarding[1].dest='wan'
firewall.@forwarding[2]=forwarding
firewall.@forwarding[2].src='lan'
firewall.@forwarding[2].dest='Guest'
firewall.@nat[0]=nat
firewall.@nat[0].name='Allow-Guest-Internet'
firewall.@nat[0].proto='all'
firewall.@nat[0].src='Guest'
firewall.@nat[0].target='SNAT'
firewall.@nat[0].snat_ip='192.168.178.2'
firewall.@nat[0].enabled='0'
firewall.@forwarding[3]=forwarding
firewall.@forwarding[3].src='Guest'
firewall.@forwarding[3].dest='lan'