zawier
June 17, 2023, 8:32pm
1
Hello,
I am attempting to set up access to my local webpage. I thought it would be a tedious task, but in my case, it doesn't seem to be.
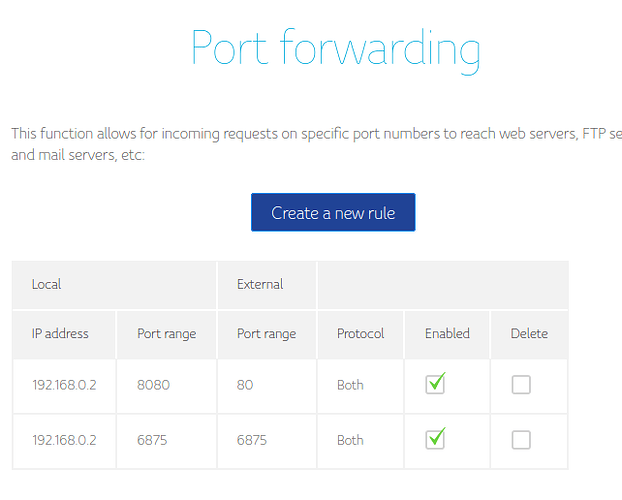
Let's start with my network specifications. My main router (from the internet provider with the IP address 192.168.0.1) already has a port forwarding set up from the WAN on port 6875 to the LAN on port 6875. The second router (NanoPi) is connected to the first one via the WAN port and is recognized by the first router as 192.168.0.2. On the NanoPi, I have installed OpenWrt + Docker. One of the Docker images is Book Stack, which is functioning properly on my LAN under the IP address 192.168.2.1:6875. I would like to expose it to the internet, which is why I also added another port forwarding rule (on the NanoPi) from any WAN IP address to the local LAN IP address 192.168.2.1 on port 6875. However, it does not work. Whenever I try to access my_public_ip:6875, I end up with a timeout on 192.168.2.1:6875.
I have tried making changes to the firewall zones and adding NAT rules, but honestly, in that area, I am navigating blindly. I am unsure about what else I can modify or check.
I would greatly appreciate any assistance with this issue. I am confident that my ISP does not block port forwarding since I am able to share a test page using Kod Explorer out of the box without any special settings.
Best regards.
Let's see your configuration:
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
cat /etc/config/network
cat /etc/config/firewall
and we also need to see your ISP router's port forwarding (screenshots are fine).
zawier
June 17, 2023, 9:20pm
3
Sure. Here you get:
cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd00:ab:cd::/48'
config interface 'wan'
option device 'eth0'
option proto 'static'
option ipaddr '192.168.0.2'
option netmask '255.255.255.0'
option gateway '192.168.0.1'
option broadcast '192.168.0.255'
option dns '8.8.8.8'
option delegate '0'
option force_link '0'
config interface 'wan6'
option device 'eth0'
option proto 'dhcpv6'
option auto '0'
option reqaddress 'try'
option reqprefix 'auto'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
option mtu '1500'
option txqueuelen '1000'
option ipv6 '0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
option ip6assign '60'
option broadcast '192.168.2.255'
option delegate '0'
option force_link '0'
option gateway '192.168.0.2'
option dns '8.8.8.8'
config device 'eth0'
option name 'eth0'
option macaddr '9a:e9:5f:49:d9:a3'
option mtu '1500'
option txqueuelen '1000'
option ipv6 '0'
config device 'eth1'
option name 'eth1'
option macaddr '9a:e9:5f:49:d9:a4'
option mtu '1500'
option txqueuelen '1000'
option ipv6 '0'
option acceptlocal '1'
config device 'dummy0'
option name 'dummy0'
option ipv6 '0'
config device 'erspan0'
option name 'erspan0'
option ipv6 '0'
config interface 'Docker'
option proto 'none'
option delegate '0'
option device 'docker0'
cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option fullcone '1'
option forward 'ACCEPT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option output 'ACCEPT'
option fullcone4 '1'
option fullcone6 '1'
option mtu_fix '1'
option input 'ACCEPT'
option forward 'ACCEPT'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
config rule
option name 'Reject-IPv6'
option family 'ipv6'
option src 'wan'
option dest '*'
option target 'REJECT'
option enabled '0'
config zone
option name 'docker'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list device 'docker0'
option family 'ipv4'
list network 'Docker'
list network 'lan'
list network 'wan'
config nat
option name 'BookStackNat'
option src_ip '192.168.2.1'
option dest_ip '192.168.0.2'
option target 'SNAT'
option snat_ip '192.168.2.1'
list proto 'all'
option src 'wan'
option enabled '0'
config redirect
option target 'DNAT'
option src 'wan'
option dest_port '6875'
option dest_ip '192.168.2.1'
option reflection_src 'external'
option src_dport '6875'
option dest 'lan'
option name 'BookStack6875'
From ISP router:
remove the lan and wan networks from the docker firewall zone. You must never have a network assigned to more than one firewall zone.
Remove the fullcone statements here and enable masquerading.
Delete this rule.
Then test again. If it doesn't work from a truly external connection (i.e. coming in from the ISP wan), try connecting to the ISP router (so you get an address on the 192.168.0.0/24 network) and see if it connects when you try 192.168.0.2:6875
zawier
June 17, 2023, 10:43pm
5
Firewall adjusted according to your proposal:
cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option output 'ACCEPT'
option mtu_fix '1'
option input 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
config rule
option name 'Reject-IPv6'
option family 'ipv6'
option src 'wan'
option dest '*'
option target 'REJECT'
option enabled '0'
config zone
option name 'docker'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list device 'docker0'
option family 'ipv4'
list network 'Docker'
config redirect
option target 'DNAT'
option src 'wan'
option dest_port '6875'
option dest_ip '192.168.2.1'
option reflection_src 'external'
option src_dport '6875'
option dest 'lan'
option name 'BookStack6875'
BookStackNat removed.
From docker zone removed:
list network 'lan'
list network 'wan'
For 100% sure I have restarted system.
Tested on my mobile phone with WiFi down.
Effect - again timeout.
remove the docker device from this (keep the docker network):
How did you test this -- from inside your network or from outside?
Did you try connecting to 192.168.0.2:6875 while connected to the 192.168.0.0/24 network (i.e. the LAN of the ISP router)?
zawier
June 17, 2023, 10:58pm
7
Of course outside. Once I'm connected directly to my ISP router and try get 192.168.0.2:6875 it works, but it worked even before.
Docker device removed from:
config zone
option name 'docker'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option family 'ipv4'
list network 'Docker'
Going to test it. Be right back soon.
This means that OpenWrt (and your docker container) are working properly.
The problem is either your ISP or your ISP router.
zawier
June 17, 2023, 11:06pm
9
My bad - it worked before we have changed settings. Now I'm not able to get 192.168.0.2:6875 from my ISP router any more.
To test outside I use mobile phone. To test locally from first or second router I switch WiFi easly.
before what changes? At what point was it working?
zawier
June 17, 2023, 11:08pm
11
I trully belive today before we attempt with modification.
So you can undo the changes we made today... do it one thing at a time and test from the ISP lan and see when it starts working again.
zawier
June 17, 2023, 11:13pm
13
You mean undo all and step by step apply your's suggestions and then test lan/wan?But there are some mistakes (which I wasn't aware) like 2 networks in the same zone etc. Should I also go back to that point before we started?
Yes... if you believe that it was working before we started making changes, you can undo those to get back to that previous state.
zawier
June 17, 2023, 11:21pm
15
Ok. Yeap, I really belive so, because I'm still in the midle of tinkering around another problem with my router and I was mostly connected to my ISP router and checked BookStack (192.168.0.2:6875) from primary (ISP) WiFi.
Thank you very much for yours todays support! I really appriciate it!
zawier
June 19, 2023, 10:25am
16
OK , did additional tests. Eventually it's not a true that on ISP router I'm able to connect 192.168.0.2. My appoloize for mess that information up. I restored network and firewall configuration to the point where we were lastly.
zawier
June 20, 2023, 11:57am
17
Any idea what else could be changed?