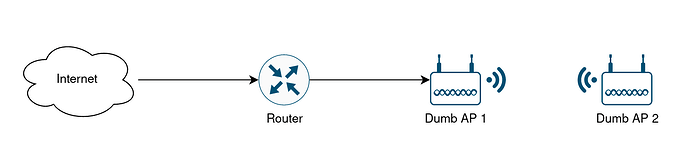
router ubus call system board
{
"kernel": "5.15.137",
"hostname": "router",
"system": "Intel(R) Core(TM) i7-4790K CPU @ 4.00GHz",
"model": "QEMU Standard PC (Q35 + ICH9, 2009)",
"board_name": "qemu-standard-pc-q35-ich9-2009",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.2",
"revision": "r23630-842932a63d",
"target": "x86/64",
"description": "OpenWrt 23.05.2 r23630-842932a63d"
}
}
(I know I said it was another TP-Link Archer C7, but I don't think that's relevant since I have the same problem with two C7 as well)
dumb ap ubus call system board
{
"kernel": "5.15.137",
"hostname": "dumbap",
"system": "Qualcomm Atheros QCA956X ver 1 rev 0",
"model": "TP-Link Archer C7 v5",
"board_name": "tplink,archer-c7-v5",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.2",
"revision": "r23630-842932a63d",
"target": "ath79/generic",
"description": "OpenWrt 23.05.2 r23630-842932a63d"
}
}
router network config
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config bridge-vlan
option device 'br-lan'
option vlan '10'
list ports 'eth0:t'
config bridge-vlan
option device 'br-lan'
option vlan '20'
list ports 'eth0:t'
config interface 'lan'
option device 'br-lan.10'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '64'
config interface 'management'
option proto 'static'
option device 'br-lan.20'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
option ip6assign '64'
router firewall config
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config zone
option name 'management'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'management'
config forwarding
option src 'lan'
option dest 'management'
config forwarding
option src 'lan'
option dest 'wan'
config forwarding
option src 'management'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
list proto 'udp'
option src '*'
option src_port '5353'
list dest_ip '224.0.0.251'
list dest_ip 'ff02::fb'
option dest_port '5353'
option target 'ACCEPT'
option name 'Allow-mDNS'
config rule
option name 'Allow-DHCP'
list proto 'udp'
option src '*'
option dest_port '67 68'
option target 'ACCEPT'
config rule
option name 'Allow-DNS'
option src '*'
option dest_port '53'
option target 'ACCEPT'
dumb ap network config
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.10'
option ipv6 '1'
config device
option type 'bridge'
option name 'br-management'
list ports 'eth0.20'
option ipv6 '1'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0t 1t 2 3 4'
option vid '10'
option description 'lan'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1t 5t'
option vid '20'
option description 'management'
config interface 'lan'
option device 'br-lan'
option proto 'static' # this is the want I want to change to unmanaged
option ipaddr '192.168.1.2'
option netmask '255.255.255.0'
option ip6assign '64'
config interface 'management'
option proto 'static'
option device 'br-management'
option ipaddr '192.168.2.2'
option netmask '255.255.255.0'
option ip6assign '64'
option gateway '192.168.2.1'
list dns '192.168.2.1'
dumb ap firewall is disabled
when I switch the dumb ap lan interface to unmanaged I loose acces to the portal and can't ping the router anymore (using the management IP address)