Good day,
There I was, another normal night for me, when bam, WiFi goes down. My TP LInk-Archer c6v2 seemed fine at first, the lights were blinking, status indicators indicated that there was WAN, LAN and WIFI. But I did not hesitate and pulled out my USB-C to RJ-45 (because ASUS sucks and doesn't have an ethernet port on my laptop model) and went to work!
The first thing I tried was obviously resetting the router. Odd, after resetting the router I still don't get DHCP leases. Hmm, well let's enable the WiFi radio0 802.11nac and check it out...
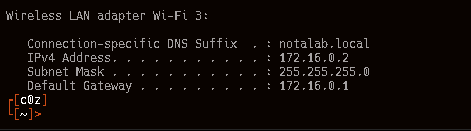
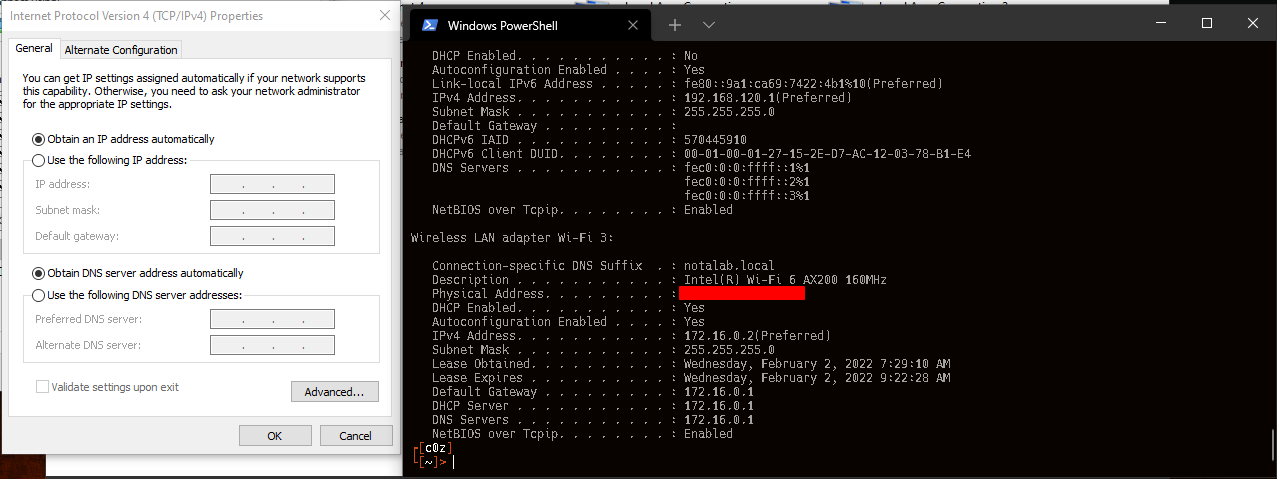
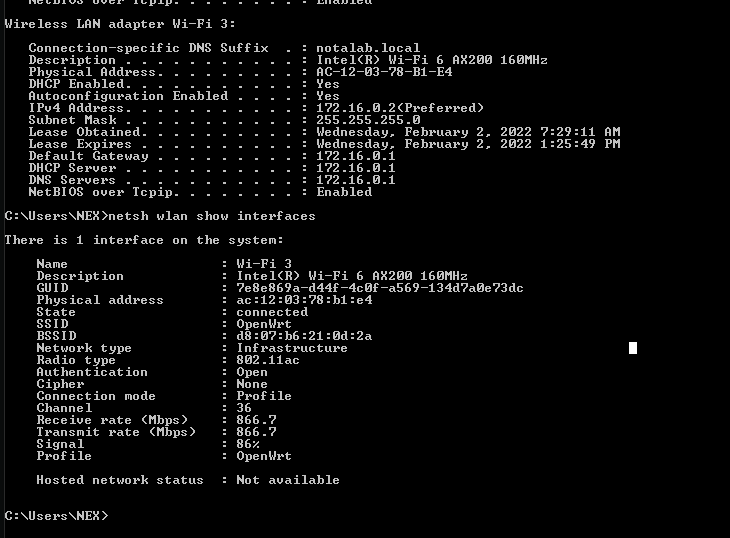
That's... odd, why is my WiFi interface address in the 172.16.0.0/16 range? Why can't I get any other DHCP leases via wired interfaces? Why does my breath smell? So I started digging more.
A fresh upgrade to:
OpenWrt 21.02.1 r16325-88151b8303 / LuCI openwrt-21.02 branch ... kernel version: 5.4.154
I didn't save any of the configurations I had, but nothing works? Taking a look at the most common configuration files:
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdb7:f9b5:cd82::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '2 3 4 5 0t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 0t'
/etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
/etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option channel '36'
option hwmode '11a'
option path 'pci0000:00/0000:00:00.0'
option htmode 'VHT80'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
config wifi-device 'radio1'
option type 'mac80211'
option channel '11'
option hwmode '11g'
option path 'platform/ahb/18100000.wmac'
option htmode 'HT20'
option disabled '1'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
/etc/config/firewall
configdefaults
optionsyn_flood 1
optioninput ACCEPT
optionoutput ACCEPT
optionforward REJECT
configzone
optionname lan
listnetwork 'lan'
optioninput ACCEPT
optionoutput ACCEPT
optionforward ACCEPT
configzone
optionname wan
listnetwork 'wan'
listnetwork 'wan6'
optioninput REJECT
optionoutput ACCEPT
optionforward REJECT
optionmasq 1
optionmtu_fix 1
configforwarding
optionsrc lan
optiondest wan
configrule
optionname Allow-DHCP-Renew
optionsrc wan
optionproto udp
optiondest_port 68
optiontarget ACCEPT
optionfamily ipv4
configrule
optionname Allow-Ping
optionsrc wan
optionproto icmp
optionicmp_type echo-request
optionfamily ipv4
optiontarget ACCEPT
configrule
optionname Allow-IGMP
optionsrc wan
optionproto igmp
optionfamily ipv4
optiontarget ACCEPT
configrule
optionname Allow-DHCPv6
optionsrc wan
optionproto udp
optionsrc_ip fc00::/6
optiondest_ip fc00::/6
optiondest_port 546
optionfamily ipv6
optiontarget ACCEPT
configrule
optionname Allow-MLD
optionsrc wan
optionproto icmp
optionsrc_ip fe80::/10
listicmp_type '130/0'
listicmp_type '131/0'
listicmp_type '132/0'
listicmp_type '143/0'
optionfamily ipv6
optiontarget ACCEPT
configrule
optionname Allow-ICMPv6-Input
optionsrc wan
optionproto icmp
listicmp_type echo-request
listicmp_type echo-reply
listicmp_type destination-unreachable
listicmp_type packet-too-big
listicmp_type time-exceeded
listicmp_type bad-header
listicmp_type unknown-header-type
listicmp_type router-solicitation
listicmp_type neighbour-solicitation
listicmp_type router-advertisement
listicmp_type neighbour-advertisement
optionlimit 1000/sec
optionfamily ipv6
optiontarget ACCEPT
configrule
optionname Allow-ICMPv6-Forward
optionsrc wan
optiondest *
optionproto icmp
listicmp_type echo-request
listicmp_type echo-reply
listicmp_type destination-unreachable
listicmp_type packet-too-big
listicmp_type time-exceeded
listicmp_type bad-header
listicmp_type unknown-header-type
optionlimit 1000/sec
optionfamily ipv6
optiontarget ACCEPT
configrule
optionname Allow-IPSec-ESP
optionsrc wan
optiondest lan
optionproto esp
optiontarget ACCEPT
configrule
optionname Allow-ISAKMP
optionsrc wan
optiondest lan
optiondest_port 500
optionproto udp
optiontarget ACCEPT
configrule
optionname Support-UDP-Traceroute
optionsrc wan
optiondest_port 33434:33689
optionproto udp
optionfamily ipv4
optiontarget REJECT
optionenabled false
configinclude
optionpath/etc/firewall.user
And the logs:
# Obtained with:
# logread | grep -v 'kern\.info' | grep -v 'kern\.debug'
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 0.000000] Linux version 5.4.154 (builder@buildhost) (gcc version 8.4.0 (OpenWrt GCC 8.4.0 r16325-88151b8303)) #0 Sun Oct 24 09:01:35 2021
Tue Feb 1 14:40:34 2022 kern.warn kernel: [ 0.000000] Primary instruction cache 64kB, VIPT, 4-way, linesize 32 bytes.
Tue Feb 1 14:40:34 2022 kern.warn kernel: [ 0.000000] Primary data cache 32kB, 4-way, VIPT, cache aliases, linesize 32 bytes
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 0.000000] Kernel command line: console=ttyS0,115200n8 rootfstype=squashfs,jffs2
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 0.000000] random: get_random_bytes called from 0x8065fa28 with crng_init=0
Tue Feb 1 14:40:34 2022 kern.warn kernel: [ 0.124605] workqueue: max_active 576 requested for napi_workq is out of range, clamping between 1 and 512
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 0.349973] 6 fixed-partitions partitions found on MTD device spi0.0
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 0.356545] Creating 6 MTD partitions on "spi0.0":
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 0.361519] 0x000000000000-0x000000020000 : "factory-boot"
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 0.368076] 0x000000020000-0x000000030000 : "info"
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 0.373901] 0x000000030000-0x000000050000 : "u-boot"
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 0.379920] 0x000000050000-0x000000fd0000 : "firmware"
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 0.389431] 2 uimage-fw partitions found on MTD device firmware
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 0.395598] Creating 2 MTD partitions on "firmware":
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 0.400743] 0x000000000000-0x0000001f3e9d : "kernel"
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 0.406760] 0x0000001f3e9d-0x000000f80000 : "rootfs"
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 0.412721] mtd: device 5 (rootfs) set to be root filesystem
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 0.420341] 1 squashfs-split partitions found on MTD device rootfs
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 0.426793] 0x000000590000-0x000000f80000 : "rootfs_data"
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 0.433238] 0x000000fd0000-0x000000ff0000 : "tplink"
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 0.439271] 0x000000ff0000-0x000001000000 : "art"
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 1.158237] random: fast init done
Tue Feb 1 14:40:34 2022 kern.warn kernel: [ 1.870125] This architecture does not have kernel memory protection.
Tue Feb 1 14:40:34 2022 user.info kernel: [ 2.487686] init: Console is alive
Tue Feb 1 14:40:34 2022 user.info kernel: [ 2.491478] init: - watchdog -
Tue Feb 1 14:40:34 2022 user.info kernel: [ 3.590555] kmodloader: loading kernel modules from /etc/modules-boot.d/*
Tue Feb 1 14:40:34 2022 user.info kernel: [ 3.626607] kmodloader: done loading kernel modules from /etc/modules-boot.d/*
Tue Feb 1 14:40:34 2022 user.info kernel: [ 3.644697] init: - preinit -
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 4.692005] random: jshn: uninitialized urandom read (4 bytes read)
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 4.806384] random: jshn: uninitialized urandom read (4 bytes read)
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 4.961333] random: jshn: uninitialized urandom read (4 bytes read)
Tue Feb 1 14:40:34 2022 kern.warn kernel: [ 6.270695] urandom_read: 4 callbacks suppressed
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 6.270703] random: procd: uninitialized urandom read (4 bytes read)
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 10.500549] jffs2: notice: (551) jffs2_build_xattr_subsystem: complete building xattr subsystem, 13 of xdatum (0 unchecked, 1 orphan) and 18 of xref (1 dead, 0 orphan) found.
Tue Feb 1 14:40:34 2022 user.info kernel: [ 10.518641] mount_root: switching to jffs2 overlay
Tue Feb 1 14:40:34 2022 kern.warn kernel: [ 10.527826] overlayfs: upper fs does not support tmpfile.
Tue Feb 1 14:40:34 2022 user.warn kernel: [ 10.538372] urandom-seed: Seeding with /etc/urandom.seed
Tue Feb 1 14:40:34 2022 user.info kernel: [ 10.648129] procd: - early -
Tue Feb 1 14:40:34 2022 user.info kernel: [ 10.651326] procd: - watchdog -
Tue Feb 1 14:40:34 2022 user.info kernel: [ 11.274306] procd: - watchdog -
Tue Feb 1 14:40:34 2022 user.info kernel: [ 11.278913] procd: - ubus -
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 11.334402] random: ubusd: uninitialized urandom read (4 bytes read)
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 11.343133] random: ubusd: uninitialized urandom read (4 bytes read)
Tue Feb 1 14:40:34 2022 user.info kernel: [ 11.355826] procd: - init -
Tue Feb 1 14:40:34 2022 user.info kernel: [ 12.118597] kmodloader: loading kernel modules from /etc/modules.d/*
Tue Feb 1 14:40:34 2022 user.info kernel: [ 12.446141] urngd: v1.0.2 started.
Tue Feb 1 14:40:34 2022 kern.notice kernel: [ 12.627705] random: crng init done
Tue Feb 1 14:40:34 2022 kern.warn kernel: [ 17.348216] ath10k_pci 0000:00:00.0: 10.4 wmi init: vdevs: 16 peers: 48 tid: 96
Tue Feb 1 14:40:34 2022 kern.warn kernel: [ 17.355987] ath10k_pci 0000:00:00.0: msdu-desc: 2500 skid: 32
Tue Feb 1 14:40:34 2022 user.info kernel: [ 17.865746] kmodloader: done loading kernel modules from /etc/modules.d/*
Tue Feb 1 14:40:35 2022 user.notice dnsmasq: DNS rebinding protection is active, will discard upstream RFC1918 responses!
Tue Feb 1 14:40:35 2022 user.notice dnsmasq: Allowing 127.0.0.0/8 responses
Tue Feb 1 14:40:36 2022 daemon.info dnsmasq[1246]: Connected to system UBus
Tue Feb 1 14:40:36 2022 daemon.info dnsmasq[1246]: started, version 2.85 cachesize 150
Tue Feb 1 14:40:36 2022 daemon.info dnsmasq[1246]: DNS service limited to local subnets
Tue Feb 1 14:40:36 2022 daemon.info dnsmasq[1246]: compile time options: IPv6 GNU-getopt no-DBus UBus no-i18n no-IDN DHCP no-DHCPv6 no-Lua TFTP no-conntrack no-ipset no-auth no-cryptohash no-DNSSEC no-ID loop-detect inotify dumpfile
Tue Feb 1 14:40:36 2022 daemon.info dnsmasq[1246]: UBus support enabled: connected to system bus
Tue Feb 1 14:40:36 2022 daemon.info dnsmasq[1246]: using only locally-known addresses for domain test
Tue Feb 1 14:40:36 2022 daemon.info dnsmasq[1246]: using only locally-known addresses for domain onion
Tue Feb 1 14:40:36 2022 daemon.info dnsmasq[1246]: using only locally-known addresses for domain localhost
Tue Feb 1 14:40:36 2022 daemon.info dnsmasq[1246]: using only locally-known addresses for domain local
Tue Feb 1 14:40:36 2022 daemon.info dnsmasq[1246]: using only locally-known addresses for domain invalid
Tue Feb 1 14:40:36 2022 daemon.info dnsmasq[1246]: using only locally-known addresses for domain bind
Tue Feb 1 14:40:36 2022 daemon.info dnsmasq[1246]: using only locally-known addresses for domain lan
Tue Feb 1 14:40:36 2022 daemon.warn dnsmasq[1246]: no servers found in /tmp/resolv.conf.d/resolv.conf.auto, will retry
Tue Feb 1 14:40:36 2022 daemon.info dnsmasq[1246]: read /etc/hosts - 4 addresses
Tue Feb 1 14:40:36 2022 daemon.info dnsmasq[1246]: read /tmp/hosts/dhcp.cfg01411c - 0 addresses
Tue Feb 1 14:40:36 2022 authpriv.info dropbear[1308]: Not backgrounding
Tue Feb 1 14:40:38 2022 daemon.notice wpa_supplicant[1407]: Successfully initialized wpa_supplicant
Tue Feb 1 14:40:39 2022 user.notice : Added device handler type: 8021ad
Tue Feb 1 14:40:39 2022 user.notice : Added device handler type: 8021q
Tue Feb 1 14:40:39 2022 user.notice : Added device handler type: macvlan
Tue Feb 1 14:40:39 2022 user.notice : Added device handler type: veth
Tue Feb 1 14:40:39 2022 user.notice : Added device handler type: bridge
Tue Feb 1 14:40:39 2022 user.notice : Added device handler type: Network device
Tue Feb 1 14:40:39 2022 user.notice : Added device handler type: tunnel
Tue Feb 1 14:40:42 2022 user.notice ucitrack: Setting up /etc/config/network reload dependency on /etc/config/dhcp
Tue Feb 1 14:40:42 2022 user.notice ucitrack: Setting up /etc/config/wireless reload dependency on /etc/config/network
Tue Feb 1 14:40:42 2022 user.notice ucitrack: Setting up /etc/config/firewall reload dependency on /etc/config/luci-splash
Tue Feb 1 14:40:42 2022 user.notice ucitrack: Setting up /etc/config/firewall reload dependency on /etc/config/qos
Tue Feb 1 14:40:42 2022 user.notice ucitrack: Setting up /etc/config/firewall reload dependency on /etc/config/miniupnpd
Tue Feb 1 14:40:43 2022 user.notice ucitrack: Setting up /etc/config/dhcp reload dependency on /etc/config/odhcpd
Tue Feb 1 14:40:43 2022 user.notice ucitrack: Setting up non-init /etc/config/fstab reload handler: /sbin/block mount
Tue Feb 1 14:40:43 2022 user.notice ucitrack: Setting up /etc/config/system reload trigger for non-procd /etc/init.d/led
Tue Feb 1 14:40:43 2022 user.notice ucitrack: Setting up /etc/config/system reload dependency on /etc/config/luci_statistics
Tue Feb 1 14:40:44 2022 user.notice ucitrack: Setting up /etc/config/system reload dependency on /etc/config/dhcp
Tue Feb 1 14:40:45 2022 daemon.notice procd: /etc/rc.d/S96led: setting up led LAN
Tue Feb 1 14:40:45 2022 daemon.notice procd: /etc/rc.d/S96led: setting up led WAN
Tue Feb 1 14:40:45 2022 daemon.notice netifd: Interface 'lan' is enabled
Tue Feb 1 14:40:45 2022 daemon.notice netifd: Interface 'lan' is setting up now
Tue Feb 1 14:40:45 2022 daemon.notice netifd: Interface 'lan' is now up
Tue Feb 1 14:40:45 2022 daemon.notice netifd: bridge 'br-lan' link is up
Tue Feb 1 14:40:45 2022 daemon.notice netifd: Interface 'lan' has link connectivity
Tue Feb 1 14:40:45 2022 daemon.notice netifd: VLAN 'eth0.1' link is up
Tue Feb 1 14:40:45 2022 daemon.notice netifd: Interface 'loopback' is enabled
Tue Feb 1 14:40:45 2022 daemon.notice netifd: Interface 'loopback' is setting up now
Tue Feb 1 14:40:45 2022 daemon.notice netifd: Interface 'loopback' is now up
Tue Feb 1 14:40:45 2022 daemon.notice netifd: Interface 'wan' is enabled
Tue Feb 1 14:40:45 2022 daemon.notice netifd: Interface 'wan6' is enabled
Tue Feb 1 14:40:45 2022 daemon.notice netifd: Network device 'eth0' link is up
Tue Feb 1 14:40:45 2022 daemon.notice netifd: Network device 'lo' link is up
Tue Feb 1 14:40:45 2022 daemon.notice netifd: Interface 'loopback' has link connectivity
Tue Feb 1 14:40:45 2022 daemon.notice netifd: VLAN 'eth0.2' link is up
Tue Feb 1 14:40:45 2022 daemon.notice netifd: Interface 'wan' has link connectivity
Tue Feb 1 14:40:45 2022 daemon.notice netifd: Interface 'wan' is setting up now
Tue Feb 1 14:40:45 2022 daemon.notice netifd: Interface 'wan6' has link connectivity
Tue Feb 1 14:40:45 2022 daemon.notice netifd: Interface 'wan6' is setting up now
Tue Feb 1 14:40:46 2022 daemon.notice netifd: wan (2039): udhcpc: started, v1.33.1
Tue Feb 1 14:40:46 2022 daemon.err odhcp6c[2040]: Failed to send RS (Address not available)
Tue Feb 1 14:40:46 2022 daemon.err odhcpd[1523]: Failed to send to ff02::1%lan@br-lan (Address not available)
Tue Feb 1 14:40:46 2022 user.notice firewall: Reloading firewall due to ifup of lan (br-lan)
Tue Feb 1 14:40:46 2022 daemon.err odhcp6c[2040]: Failed to send SOLICIT message to ff02::1:2 (Address not available)
Tue Feb 1 14:40:47 2022 daemon.notice netifd: wan (2039): udhcpc: sending discover
Tue Feb 1 14:40:47 2022 daemon.notice netifd: wan (2039): udhcpc: sending select for 192.168.0.10
Tue Feb 1 14:40:47 2022 daemon.notice netifd: wan (2039): udhcpc: lease of 192.168.0.10 obtained, lease time 86400
Tue Feb 1 14:40:47 2022 daemon.info procd: - init complete -
Tue Feb 1 14:40:48 2022 daemon.notice netifd: Interface 'wan' is now up
Tue Feb 1 14:40:48 2022 daemon.info dnsmasq[1246]: reading /tmp/resolv.conf.d/resolv.conf.auto
Tue Feb 1 14:40:48 2022 daemon.info dnsmasq[1246]: using only locally-known addresses for domain test
Tue Feb 1 14:40:48 2022 daemon.info dnsmasq[1246]: using only locally-known addresses for domain onion
Tue Feb 1 14:40:48 2022 daemon.info dnsmasq[1246]: using only locally-known addresses for domain localhost
Tue Feb 1 14:40:48 2022 daemon.info dnsmasq[1246]: using only locally-known addresses for domain local
Tue Feb 1 14:40:48 2022 daemon.info dnsmasq[1246]: using only locally-known addresses for domain invalid
Tue Feb 1 14:40:48 2022 daemon.info dnsmasq[1246]: using only locally-known addresses for domain bind
Tue Feb 1 14:40:48 2022 daemon.info dnsmasq[1246]: using only locally-known addresses for domain lan
Tue Feb 1 14:40:48 2022 daemon.info dnsmasq[1246]: using nameserver 1.1.1.1#53
Tue Feb 1 14:40:48 2022 daemon.info dnsmasq[1246]: using nameserver 1.0.0.1#53
Tue Feb 1 14:40:48 2022 user.notice firewall: Reloading firewall due to ifup of wan (eth0.2)
Tue Feb 1 14:40:48 2022 user.notice dnsmasq: found already running DHCP-server on interface 'br-lan' refusing to start, use 'option force 1' to override
Tue Feb 1 14:40:48 2022 daemon.info dnsmasq[1246]: exiting on receipt of SIGTERM
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: Connected to system UBus
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: started, version 2.85 cachesize 150
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: DNS service limited to local subnets
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: compile time options: IPv6 GNU-getopt no-DBus UBus no-i18n no-IDN DHCP no-DHCPv6 no-Lua TFTP no-conntrack no-ipset no-auth no-cryptohash no-DNSSEC no-ID loop-detect inotify dumpfile
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: UBus support enabled: connected to system bus
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: using only locally-known addresses for domain test
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: using only locally-known addresses for domain onion
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: using only locally-known addresses for domain localhost
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: using only locally-known addresses for domain local
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: using only locally-known addresses for domain invalid
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: using only locally-known addresses for domain bind
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: using only locally-known addresses for domain lan
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: reading /tmp/resolv.conf.d/resolv.conf.auto
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: using only locally-known addresses for domain test
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: using only locally-known addresses for domain onion
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: using only locally-known addresses for domain localhost
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: using only locally-known addresses for domain local
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: using only locally-known addresses for domain invalid
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: using only locally-known addresses for domain bind
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: using only locally-known addresses for domain lan
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: using nameserver 1.1.1.1#53
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: using nameserver 1.0.0.1#53
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: read /etc/hosts - 4 addresses
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: read /tmp/hosts/dhcp.cfg01411c - 0 addresses
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: read /etc/hosts - 4 addresses
Tue Feb 1 14:40:49 2022 daemon.info dnsmasq[2353]: read /tmp/hosts/dhcp.cfg01411c - 0 addresses
Tue Feb 1 14:45:25 2022 daemon.info dnsmasq[2353]: read /etc/hosts - 4 addresses
Tue Feb 1 14:45:25 2022 daemon.info dnsmasq[2353]: read /tmp/hosts/odhcpd - 1 addresses
Tue Feb 1 14:45:25 2022 daemon.info dnsmasq[2353]: read /tmp/hosts/dhcp.cfg01411c - 0 addresses
Tue Feb 1 14:45:27 2022 daemon.info dnsmasq[2353]: read /etc/hosts - 4 addresses
Tue Feb 1 14:45:27 2022 daemon.info dnsmasq[2353]: read /tmp/hosts/odhcpd - 2 addresses
Tue Feb 1 14:45:27 2022 daemon.info dnsmasq[2353]: read /tmp/hosts/dhcp.cfg01411c - 0 addresses
Tue Feb 1 14:45:33 2022 daemon.err uhttpd[1642]: luci: accepted login on / for root from 192.168.1.2
Tue Feb 1 14:46:20 2022 daemon.err uhttpd[1642]: luci: accepted login on /admin for root from 192.168.1.2
Tue Feb 1 14:47:28 2022 daemon.err uhttpd[1642]: luci: accepted login on /admin for root from 192.168.1.2
Tue Feb 1 14:48:36 2022 daemon.notice hostapd: Configuration file: /var/run/hostapd-phy0.conf (phy wlan0) --> new PHY
Tue Feb 1 14:48:38 2022 kern.warn kernel: [ 237.992392] ath10k_pci 0000:00:00.0: 10.4 wmi init: vdevs: 16 peers: 48 tid: 96
Tue Feb 1 14:48:38 2022 kern.warn kernel: [ 238.000176] ath10k_pci 0000:00:00.0: msdu-desc: 2500 skid: 32
Tue Feb 1 14:48:38 2022 kern.warn kernel: [ 238.381317] ath10k_pci 0000:00:00.0: Firmware lacks feature flag indicating a retry limit of > 2 is OK, requested limit: 4
Tue Feb 1 14:48:38 2022 daemon.notice hostapd: wlan0: interface state UNINITIALIZED->HT_SCAN
Tue Feb 1 14:48:39 2022 daemon.notice hostapd: wlan0: interface state HT_SCAN->ENABLED
Tue Feb 1 14:48:39 2022 daemon.notice hostapd: wlan0: AP-ENABLED
Tue Feb 1 14:48:40 2022 daemon.notice netifd: Network device 'wlan0' link is up
Tue Feb 1 14:48:47 2022 daemon.info hostapd: wlan0: STA ac:12:03:78:b1:e4 IEEE 802.11: authenticated
Tue Feb 1 14:48:47 2022 daemon.info hostapd: wlan0: STA ac:12:03:78:b1:e4 IEEE 802.11: associated (aid 1)
Tue Feb 1 14:48:47 2022 daemon.notice hostapd: wlan0: AP-STA-CONNECTED ac:12:03:78:b1:e4
Tue Feb 1 14:48:47 2022 daemon.notice hostapd: wlan0: STA-OPMODE-SMPS-MODE-CHANGED ac:12:03:78:b1:e4 off
Tue Feb 1 14:51:06 2022 daemon.notice hostapd: wlan0: AP-STA-DISCONNECTED ac:12:03:78:b1:e4
Tue Feb 1 14:51:06 2022 daemon.info hostapd: wlan0: STA ac:12:03:78:b1:e4 IEEE 802.11: authenticated
Tue Feb 1 14:51:06 2022 daemon.info hostapd: wlan0: STA ac:12:03:78:b1:e4 IEEE 802.11: associated (aid 1)
Tue Feb 1 14:51:06 2022 daemon.notice hostapd: wlan0: AP-STA-CONNECTED ac:12:03:78:b1:e4
Tue Feb 1 14:51:06 2022 daemon.notice hostapd: wlan0: STA-OPMODE-SMPS-MODE-CHANGED ac:12:03:78:b1:e4 off
Tue Feb 1 14:51:25 2022 daemon.notice hostapd: wlan0: AP-STA-DISCONNECTED ac:12:03:78:b1:e4
Tue Feb 1 14:55:57 2022 authpriv.info dropbear[6466]: Child connection from 192.168.1.2:1374
Tue Feb 1 14:56:12 2022 authpriv.notice dropbear[6466]: Password auth succeeded for 'root' from 192.168.1.2:1374
Tue Feb 1 14:57:50 2022 daemon.info hostapd: wlan0: STA ac:12:03:78:b1:e4 IEEE 802.11: authenticated
Tue Feb 1 14:57:50 2022 daemon.info hostapd: wlan0: STA ac:12:03:78:b1:e4 IEEE 802.11: associated (aid 1)
Tue Feb 1 14:57:50 2022 daemon.notice hostapd: wlan0: AP-STA-CONNECTED ac:12:03:78:b1:e4
Tue Feb 1 14:57:50 2022 daemon.notice hostapd: wlan0: STA-OPMODE-SMPS-MODE-CHANGED ac:12:03:78:b1:e4 off
Tue Feb 1 14:58:06 2022 daemon.notice hostapd: wlan0: AP-STA-DISCONNECTED ac:12:03:78:b1:e4
Tue Feb 1 14:58:06 2022 daemon.info hostapd: wlan0: STA ac:12:03:78:b1:e4 IEEE 802.11: authenticated
Tue Feb 1 14:58:06 2022 daemon.info hostapd: wlan0: STA ac:12:03:78:b1:e4 IEEE 802.11: associated (aid 1)
Tue Feb 1 14:58:06 2022 daemon.notice hostapd: wlan0: AP-STA-CONNECTED ac:12:03:78:b1:e4
Tue Feb 1 14:58:06 2022 daemon.notice hostapd: wlan0: STA-OPMODE-SMPS-MODE-CHANGED ac:12:03:78:b1:e4 off
Tue Feb 1 14:58:25 2022 daemon.notice hostapd: wlan0: AP-STA-DISCONNECTED ac:12:03:78:b1:e4
Oh the vanity!
If you need anything else let me know!
- I would have put more pictures but your discourse server's policies only allow me to post one picture.