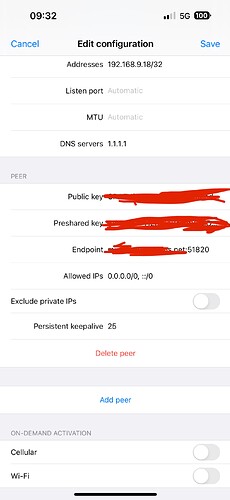
Hello,
i've been struggling to setup wireguard as a server on this router. This router sits behind a speedport (ISP) router and i've connected it to the "Internet" port. No matter what i do, i cannot get a handshake to work with my iphone. i've checked if i am sitting behind a CG-NAT but that doesn't seem the case.
I suspect something is off with the firewall. Really appreciating your support
Below is my config file:
{
"kernel": "5.10.146",
"hostname": "OpenWrt",
"system": "ARMv7 Processor rev 1 (v7l)",
"model": "Linksys WRT3200ACM",
"board_name": "linksys,wrt3200acm",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "22.03.2",
"revision": "r19803-9a599fee93",
"target": "mvebu/cortexa9",
"description": "OpenWrt 22.03.2 r19803-9a599fee93"
}
}
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fc00::/7'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.8.1'
config device
option name 'wan'
option macaddr '62:38:e0:c1:ea:c0'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
config interface 'VPNGR'
option proto 'wireguard'
option private_key XXXX
option listen_port '51820'
list addresses '192.168.9.1/24'
config wireguard_VPNGR
option preshared_key XXXX
option public_key XXXX
option private_key XXXX
option persistent_keepalive '25'
option description 'iphone'
list allowed_ips '192.168.9.18/32'
option route_allowed_ips '1'
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'VPNGR'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
head: /etc/firewall.user: No such file or directory
# Generated by iptables-save v1.8.7 on Mon Nov 21 09:01:24 2022
*mangle
:PREROUTING ACCEPT [173683:109393859]
:INPUT ACCEPT [6297:898094]
:FORWARD ACCEPT [166436:108218445]
:OUTPUT ACCEPT [8448:2474559]
:POSTROUTING ACCEPT [172622:110233145]
COMMIT
# Completed on Mon Nov 21 09:01:24 2022
# Generated by iptables-save v1.8.7 on Mon Nov 21 09:01:24 2022
*filter
:INPUT ACCEPT [6066:881278]
:FORWARD ACCEPT [164174:107758586]
:OUTPUT ACCEPT [8448:2474559]
COMMIT
# Completed on Mon Nov 21 09:01:24 2022
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
7: wan@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.1.3/24 brd 192.168.1.255 scope global wan
valid_lft forever preferred_lft forever
11: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.8.1/24 brd 192.168.8.255 scope global br-lan
valid_lft forever preferred_lft forever
12: VPNGR: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN group default qlen 1000
inet 192.168.9.1/24 brd 192.168.9.255 scope global VPNGR
valid_lft forever preferred_lft forever
default via 192.168.1.1 dev wan proto static src 192.168.1.3
192.168.1.0/24 dev wan proto kernel scope link src 192.168.1.3
192.168.8.0/24 dev br-lan proto kernel scope link src 192.168.8.1
192.168.9.0/24 dev VPNGR proto kernel scope link src 192.168.9.1
192.168.9.18 dev VPNGR proto static scope link
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
broadcast 192.168.1.0 dev wan table local proto kernel scope link src 192.168.1.3
local 192.168.1.3 dev wan table local proto kernel scope host src 192.168.1.3
broadcast 192.168.1.255 dev wan table local proto kernel scope link src 192.168.1.3
broadcast 192.168.8.0 dev br-lan table local proto kernel scope link src 192.168.8.1
local 192.168.8.1 dev br-lan table local proto kernel scope host src 192.168.8.1
broadcast 192.168.8.255 dev br-lan table local proto kernel scope link src 192.168.8.1
broadcast 192.168.9.0 dev VPNGR table local proto kernel scope link src 192.168.9.1
local 192.168.9.1 dev VPNGR table local proto kernel scope host src 192.168.9.1
broadcast 192.168.9.255 dev VPNGR table local proto kernel scope link src 192.168.9.1
0: from all lookup local
32766: from all lookup main
32767: from all lookup default