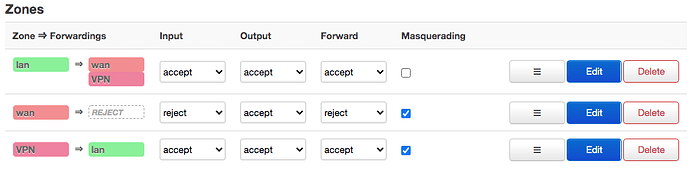
Hello, not it cannot. Here is tunnelblick log:
2020-05-28 14:04:14.470797 *Tunnelblick: macOS 10.13.6 (17G12034); Tunnelblick 3.8.2a (build 5481); prior version 3.8.2 (build 5480)
2020-05-28 14:04:14.763268 *Tunnelblick: Attempting connection with vilkas-pc using shadow copy; Set nameserver = 769; monitoring connection
2020-05-28 14:04:14.763712 *Tunnelblick: openvpnstart start vilkas-pc.tblk 61102 769 0 1 0 1098032 -ptADGNWradsgnw 2.4.9-openssl-1.1.1e
2020-05-28 14:04:14.797430 *Tunnelblick: openvpnstart starting OpenVPN
2020-05-28 14:04:15.151386 OpenVPN 2.4.9 x86_64-apple-darwin [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on May 22 2020
2020-05-28 14:04:15.151493 library versions: OpenSSL 1.1.1e 17 Mar 2020, LZO 2.10
2020-05-28 14:04:15.152713 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:61102
2020-05-28 14:04:15.152755 Need hold release from management interface, waiting...
2020-05-28 14:04:15.387036 *Tunnelblick: openvpnstart log:
OpenVPN started successfully.
Command used to start OpenVPN (one argument per displayed line):
/Applications/Tunnelblick.app/Contents/Resources/openvpn/openvpn-2.4.9-openssl-1.1.1e/openvpn
--daemon
--log /Library/Application Support/Tunnelblick/Logs/-SUsers-SVilkas-SLibrary-SApplication Support-STunnelblick-SConfigurations-Svilkas--pc.tblk-SContents-SResources-Sconfig.ovpn.769_0_1_0_1098032.61102.openvpn.log
--cd /Library/Application Support/Tunnelblick/Users/Vilkas/vilkas-pc.tblk/Contents/Resources
--machine-readable-output
--setenv IV_GUI_VER "net.tunnelblick.tunnelblick 5481 3.8.2a (build 5481)"
--verb 3
--config /Library/Application Support/Tunnelblick/Users/Vilkas/vilkas-pc.tblk/Contents/Resources/config.ovpn
--setenv TUNNELBLICK_CONFIG_FOLDER /Library/Application Support/Tunnelblick/Users/Vilkas/vilkas-pc.tblk/Contents/Resources
--verb 3
--cd /Library/Application Support/Tunnelblick/Users/Vilkas/vilkas-pc.tblk/Contents/Resources
--management 127.0.0.1 61102 /Library/Application Support/Tunnelblick/dlegbjocihhgmagfabcblmhcckfoibedpfchhhll.mip
--management-query-passwords
--management-hold
--script-security 2
--route-up /Applications/Tunnelblick.app/Contents/Resources/client.up.tunnelblick.sh -9 -d -f -m -w -ptADGNWradsgnw
--down /Applications/Tunnelblick.app/Contents/Resources/client.down.tunnelblick.sh -9 -d -f -m -w -ptADGNWradsgnw
2020-05-28 14:04:15.388110 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:61102
2020-05-28 14:04:15.393610 MANAGEMENT: CMD 'pid'
2020-05-28 14:04:15.393709 MANAGEMENT: CMD 'auth-retry interact'
2020-05-28 14:04:15.393759 MANAGEMENT: CMD 'state on'
2020-05-28 14:04:15.393787 MANAGEMENT: CMD 'state'
2020-05-28 14:04:15.393840 MANAGEMENT: CMD 'bytecount 1'
2020-05-28 14:04:15.393930 *Tunnelblick: Established communication with OpenVPN
2020-05-28 14:04:15.394740 *Tunnelblick: >INFO:OpenVPN Management Interface Version 1 -- type 'help' for more info
2020-05-28 14:04:15.395846 MANAGEMENT: CMD 'hold release'
2020-05-28 14:04:15.396044 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
2020-05-28 14:04:15.399198 Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
2020-05-28 14:04:15.399249 Outgoing Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
2020-05-28 14:04:15.399269 Incoming Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
2020-05-28 14:04:15.399288 Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
2020-05-28 14:04:15.399528 TCP/UDP: Preserving recently used remote address: [AF_INET]78.56.57.142:1194
2020-05-28 14:04:15.399583 Socket Buffers: R=[196724->196724] S=[9216->9216]
2020-05-28 14:04:15.399602 UDP link local: (not bound)
2020-05-28 14:04:15.399619 UDP link remote: [AF_INET]xxxxxxxx:1194
2020-05-28 14:04:15.399653 MANAGEMENT: >STATE:1590663855,WAIT,,,,,,
2020-05-28 14:04:15.427445 MANAGEMENT: >STATE:1590663855,AUTH,,,,,,
2020-05-28 14:04:15.427502 TLS: Initial packet from [AF_INET]xxxxxxxx:1194, sid=a1345435 07e4c969
2020-05-28 14:04:15.562499 VERIFY OK: depth=1, CN=xxxxxx
2020-05-28 14:04:15.562896 VERIFY KU OK
2020-05-28 14:04:15.562920 Validating certificate extended key usage
2020-05-28 14:04:15.562936 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
2020-05-28 14:04:15.562950 VERIFY EKU OK
2020-05-28 14:04:15.562963 VERIFY OK: depth=0, CN=xxxxx
2020-05-28 14:04:15.623527 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1541', remote='link-mtu 1542'
2020-05-28 14:04:15.623744 WARNING: 'comp-lzo' is present in remote config but missing in local config, remote='comp-lzo'
2020-05-28 14:04:15.623969 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_CHACHA20_POLY1305_SHA256, 2048 bit RSA
2020-05-28 14:04:15.624057 [xxxxxx] Peer Connection Initiated with [AF_INET]78.56.57.142:1194
2020-05-28 14:04:16.634638 MANAGEMENT: >STATE:1590663856,GET_CONFIG,,,,,,
2020-05-28 14:04:16.634777 SENT CONTROL [xxxxxx]: 'PUSH_REQUEST' (status=1)
2020-05-28 14:04:16.728624 PUSH: Received control message: 'PUSH_REPLY,route 192.168.2.0 255.255.255.0,route 192.168.7.0 255.255.255.0,topology net30,ping 10,ping-restart 120,ifconfig 192.168.7.14 192.168.7.13,peer-id 0,cipher AES-256-GCM'
2020-05-28 14:04:16.728731 OPTIONS IMPORT: timers and/or timeouts modified
2020-05-28 14:04:16.728750 OPTIONS IMPORT: --ifconfig/up options modified
2020-05-28 14:04:16.728764 OPTIONS IMPORT: route options modified
2020-05-28 14:04:16.728777 OPTIONS IMPORT: peer-id set
2020-05-28 14:04:16.728791 OPTIONS IMPORT: adjusting link_mtu to 1624
2020-05-28 14:04:16.728803 OPTIONS IMPORT: data channel crypto options modified
2020-05-28 14:04:16.728817 Data Channel: using negotiated cipher 'AES-256-GCM'
2020-05-28 14:04:16.728937 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
2020-05-28 14:04:16.728958 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
2020-05-28 14:04:16.729290 Opening utun (connect(AF_SYS_CONTROL)): Resource busy (errno=16)
2020-05-28 14:04:16.729433 Opened utun device utun1
2020-05-28 14:04:16.729475 MANAGEMENT: >STATE:1590663856,ASSIGN_IP,,192.168.7.14,,,,
2020-05-28 14:04:16.729500 /sbin/ifconfig utun1 delete
ifconfig: ioctl (SIOCDIFADDR): Can't assign requested address
2020-05-28 14:04:16.735216 NOTE: Tried to delete pre-existing tun/tap instance -- No Problem if failure
2020-05-28 14:04:16.735326 /sbin/ifconfig utun1 192.168.7.14 192.168.7.13 mtu 1500 netmask 255.255.255.255 up
2020-05-28 14:04:16.739497 MANAGEMENT: >STATE:1590663856,ADD_ROUTES,,,,,,
2020-05-28 14:04:16.739555 /sbin/route add -net 192.168.2.0 192.168.7.13 255.255.255.0
add net 192.168.2.0: gateway 192.168.7.13
2020-05-28 14:04:16.744828 /sbin/route add -net 192.168.7.0 192.168.7.13 255.255.255.0
add net 192.168.7.0: gateway 192.168.7.13
14:04:16 *Tunnelblick: **********************************************
14:04:16 *Tunnelblick: Start of output from client.up.tunnelblick.sh
14:04:18 *Tunnelblick: NOTE: No network configuration changes need to be made.
14:04:18 *Tunnelblick: WARNING: Will NOT monitor for other network configuration changes.
14:04:18 *Tunnelblick: WARNING: Will NOT disable IPv6 settings.
14:04:18 *Tunnelblick: DNS servers '8.8.8.8 8.8.4.4' were set manually
14:04:18 *Tunnelblick: DNS servers '8.8.8.8 8.8.4.4' will be used for DNS queries when the VPN is active
14:04:19 *Tunnelblick: The DNS servers include only free public DNS servers known to Tunnelblick.
14:04:19 *Tunnelblick: Flushed the DNS cache via dscacheutil
14:04:19 *Tunnelblick: /usr/sbin/discoveryutil not present. Not flushing the DNS cache via discoveryutil
14:04:19 *Tunnelblick: Notified mDNSResponder that the DNS cache was flushed
14:04:19 *Tunnelblick: Not notifying mDNSResponderHelper that the DNS cache was flushed because it is not running
14:04:19 *Tunnelblick: End of output from client.up.tunnelblick.sh
14:04:19 *Tunnelblick: **********************************************
2020-05-28 14:04:19.120971 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
2020-05-28 14:04:19.121041 Initialization Sequence Completed
2020-05-28 14:04:19.121107 MANAGEMENT: >STATE:1590663859,CONNECTED,SUCCESS,192.168.7.14,xxxxxxx,1194,,
2020-05-28 14:04:19.332907 *Tunnelblick: Warning: DNS server Address 8.8.4.4 is a known public DNS server but is not being routed through the VPN
2020-05-28 14:04:19.438815 *Tunnelblick: Warning: DNS server Address 8.8.8.8 is a known public DNS server but is not being routed through the VPN
2020-05-28 14:04:25.806495 *Tunnelblick: This computer's apparent public IP address (xxxxxxxx) was unchanged after the connection was made