Im running the latest version of openwrt which is 23.5.3, after fresh install and changing the ip to 192.168.1.10 and configuring vlan devices and adding brvlan interface then rebooting. I cannot access luci and ssh on the new assigned ip address the web browser show cannot reach the device. Ive already done many reset and I can access with the default ip 192.168.1.1 after reset, but when changing as stated above the same problem persist. Thanks for the help
Please connect to your OpenWrt device using ssh and copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
ubus call system board
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
Without seeing what you are changing, it is not possible to diagnose and solve the problem.
Can you tell us specifically what you are trying to achieve and post your current configs? We can help you get where you are going.
content://com.facebook.orca.securefileprovider/temp/2.txt
My configuration
root@OpenWrt:~# ubus call system board
{
"kernel": "5.15.150",
"hostname": "OpenWrt",
"system": "MediaTek MT7621 ver:1 eco:4",
"model": "MikroTik RouterBOARD 750Gr3",
"board_name": "mikrotik,routerboard-750gr3",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.3",
"revision": "r23809-234f1a2efa",
"target": "ramips/mt7621",
"description": "OpenWrt 23.05.3 r23809-234f1a2efa"
}
}
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd05:d652:aa7a::/48'
option packet_steering '1'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
list ports 'lan5'
config device
option name 'lan2'
option macaddr '78:9a:18:d3:b7:de'
config device
option name 'lan3'
option macaddr '78:9a:18:d3:b7:de'
config device
option name 'lan4'
option macaddr '78:9a:18:d3:b7:de'
config device
option name 'lan5'
option macaddr '78:9a:18:d3:b7:de'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.10'
option netmask '255.255.255.0'
option ip6assign '60'
option gateway '192.168.1.1'
list dns '8.8.8.8'
list dns '8.8.4.4'
config device
option name 'wan'
option macaddr '78:9a:18:d3:b7:dd'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
config device
option type 'bridge'
option name 'BRVLAN'
list ports 'eth0'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
list ports 'lan5'
list ports 'wan'
option bridge_empty '1'
option igmp_snooping '1'
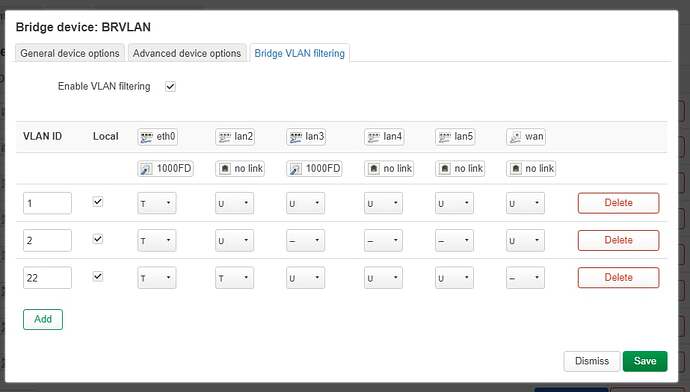
config bridge-vlan
option device 'BRVLAN'
option vlan '1'
list ports 'eth0:t'
list ports 'lan2'
config bridge-vlan
option device 'BRVLAN'
option vlan '2'
list ports 'eth0:t'
list ports 'wan'
config bridge-vlan
option device 'BRVLAN'
option vlan '22'
list ports 'eth0:t'
list ports 'lan2:t'
list ports 'lan3'
list ports 'lan4'
list ports 'lan5'
config device
option name 'BRVLAN.1'
option type '8021q'
option ifname 'BRVLAN'
option vid '1'
config device
option name 'BRVLAN.2'
option type '8021q'
option ifname 'BRVLAN'
option vid '2'
config device
option name 'BRVLAN.22'
option type '8021q'
option ifname 'BRVLAN'
option vid '22'
config interface 'VLAN22'
option proto 'static'
option device 'BRVLAN'
option ipaddr '20.0.0.5'
option netmask '255.255.255.0'
option gateway '20.0.0.1'
list dns '8.8.8.8'
list dns '8.8.4.4'
root@OpenWrt:~# cat /etc/config/wireless
cat: can't open '/etc/config/wireless': No such file or directory
root@OpenWrt:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option filter_aaaa '0'
option filter_a '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'VLAN22'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'VLAN22'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config forwarding
option src 'VLAN22'
option dest 'wan'
root@OpenWrt:~#
Ports may only exist in one bridge, but you’ve used them in multiple bridges.
This is one of multiple major issues.
Please describe the desired goals and we can help describe the edits you need to make to achieve them.
If I will delete the default lan interface and unconfigure the default br-lan do you think it will work to access luci and ssh to the ip address of the Vlan22 interface?
I would like to have a setup like this wan would be may internet source port 2 is for may vlan22 device and the remaining port would be the attachment port for my access points connected to vlan22 device in port2 which will give the internet connection and ip address to connected users connected to the ap's attached to the port 3,4,5
Is there an upstream router? What VLANs are setup on the upstream device?