I'm trying to set up a WLAN network without access to the internet which my IOT devices/ IP cameras will connect to, and is reachable from the LAN, however am running into some weird issues.
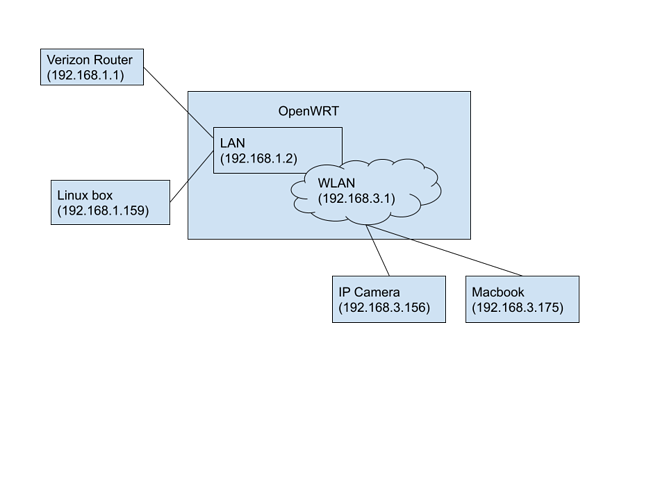
To start, describing my network layout, I have a Verizon router (IP Address 192.168.1.1) acting as my primary network/running DHCP (the wifi capabilities are superior to my openwrt router). I have my openWRT router connected to that configured with the DHCP disabled for the LAN interface (IP Address 192.168.1.2) (so essentially an unmanaged switch).
I have a linux box also connected on the LAN to host home assistant.
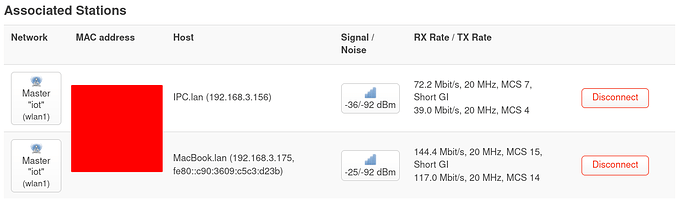
The OpenWRT router has a wlan configured with IP Address 192.168.3.1, and connected to that wlan I have an IP Camera (192.168.3.156) and my macbook to test with (192.168.3.175).
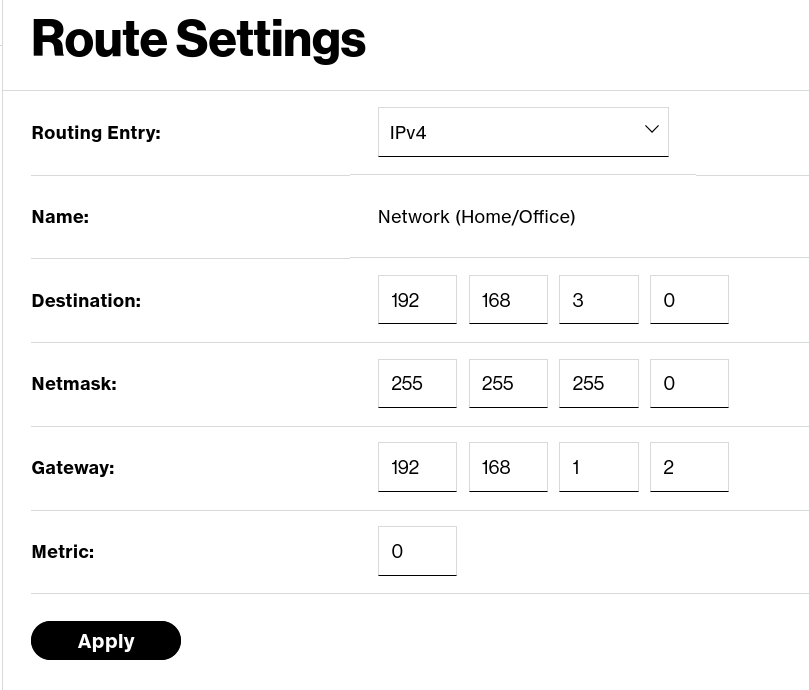
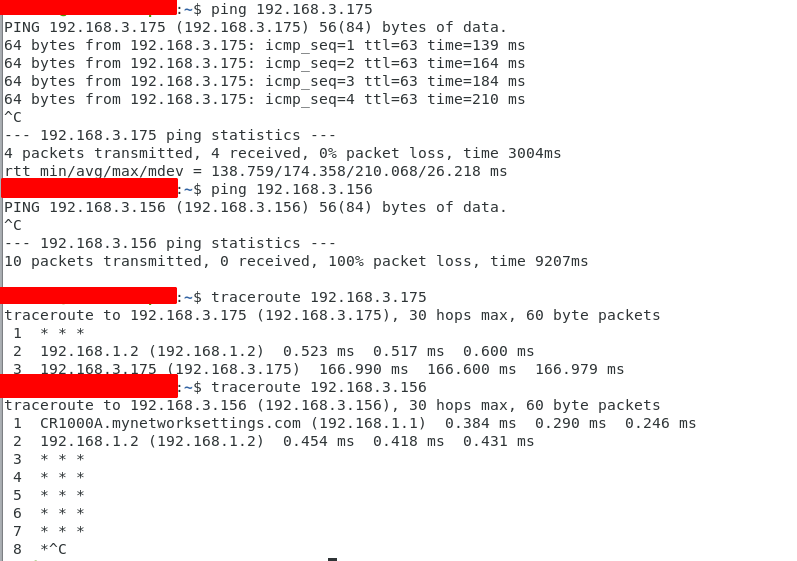
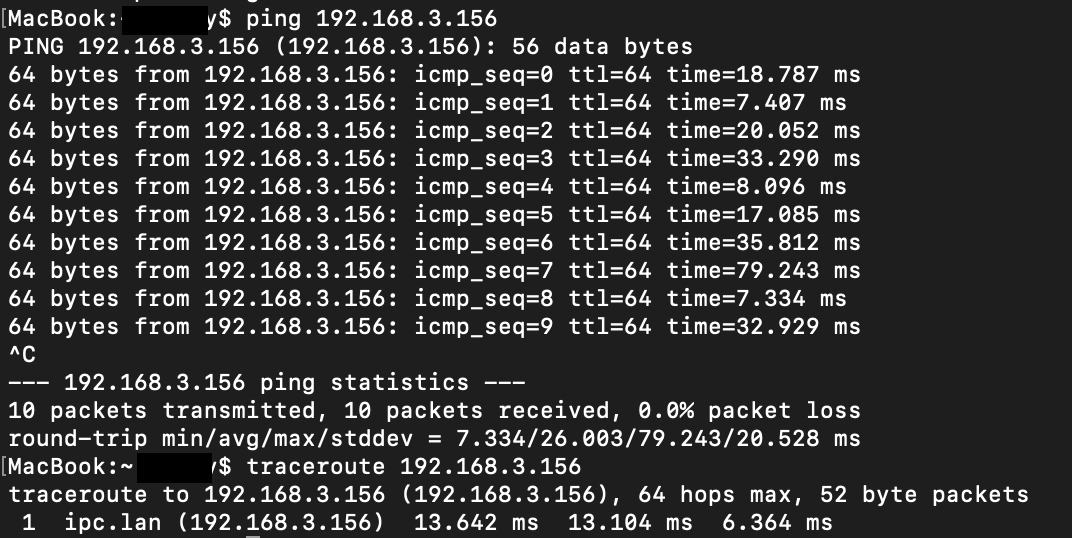
I had to set up static routes on my verizon router, however I'm now able to ping and traceroute my macbook from the linux server. Further, I'm able to ping the IP camera from my macbook, which makes sense since it's on the same network.
What's strange though, is that I can't ping the IP camera from my linux server. the traceroute suggests to me that it's at least getting to the openwrt, but then failing to route to the camera, or else blocking the response for some reason.
And below is pinging/tracerouting the IP camera from the Macbook, so I know the device does respond:
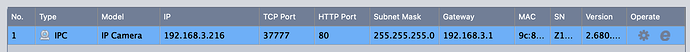
I've added another IP camera (192.168.3.216), same issue, can stream it to my macbook while also connected to the IOT wlan, but can't ping it from my linux box.
I also checked, and I can SSH onto the openwrt router and can ping the cameras from there.
When I connect the macbook to the LAN I again can't ping the camera.
I've been beating my head on this for a while, would love to hear if anyone has suggestions on what is going wrong connecting to the IP Camera.