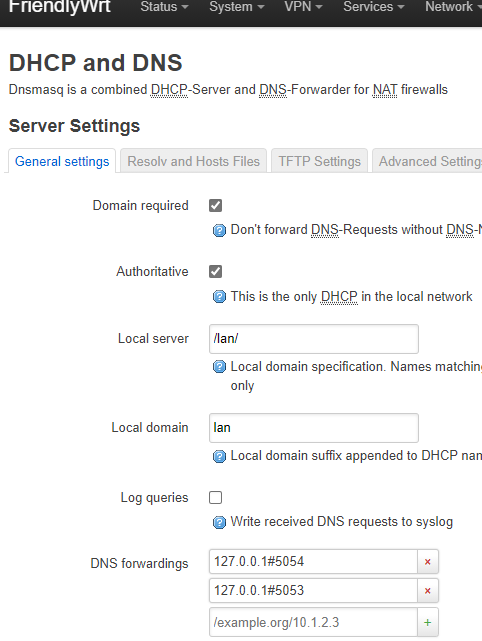
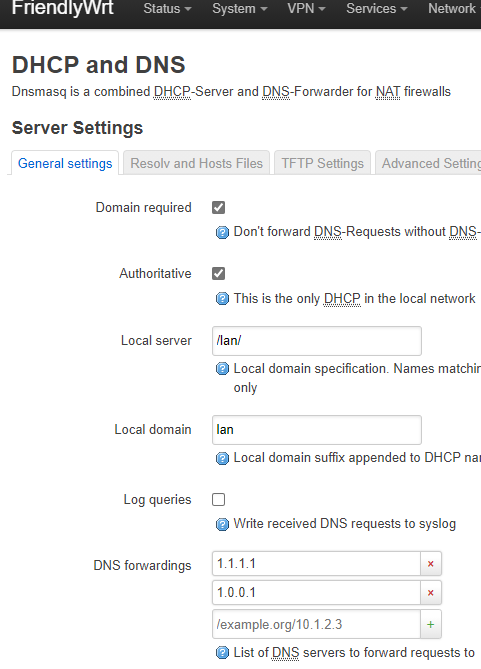
TCPDUMP shows DNS traffic exiting the WAN
root@FriendlyWrt:~#
root@FriendlyWrt:~# tcpdump -i eth0 | grep -i "one"
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
20:57:58.532170 STP 802.1d, Config, Flags [none], bridge-id 0000.40:2b:50:5b:24:d2.8001, length 43
20:57:59.532155 STP 802.1d, Config, Flags [none], bridge-id 0000.40:2b:50:5b:24:d2.8001, length 43
20:58:00.532061 STP 802.1d, Config, Flags [none], bridge-id 0000.40:2b:50:5b:24:d2.8001, length 43
20:58:01.532137 STP 802.1d, Config, Flags [none], bridge-id 0000.40:2b:50:5b:24:d2.8001, length 43
20:58:02.532056 STP 802.1d, Config, Flags [none], bridge-id 0000.40:2b:50:5b:24:d2.8001, length 43
20:58:03.532128 STP 802.1d, Config, Flags [none], bridge-id 0000.40:2b:50:5b:24:d2.8001, length 43
**20:58:04.021018 IP 192.168.1.108.56388 > one.one.one.one.53: 46886+ A? one.one.one.one. (33)**
**20:58:04.021302 IP 192.168.1.108.50099 > one.one.one.one.53: 62257+ AAAA? one.one.one.one. (33)**
**20:58:04.027212 IP one.one.one.one.53 > 192.168.1.108.56388: 46886 2/0/0 A 1.0.0.1, A 1.1.1.1 (65)**
**20:58:04.029045 IP one.one.one.one.53 > 192.168.1.108.50099: 62257 2/0/0 AAAA 2606:4700:4700::1001, AAAA 2606:4700:4700::1111 (89)**
20:58:04.532236 STP 802.1d, Config, Flags [none], bridge-id 0000.40:2b:50:5b:24:d2.8001, length 43
20:58:05.041327 IP 192.168.1.108.30143 > one.one.one.one.53: 5989+ PTR? 1.1.1.1.in-addr.arpa. (38)
20:58:05.049098 IP one.one.one.one.53 > 192.168.1.108.30143: 5989 1/0/0 PTR one.one.one.one. (67)
20:58:05.532174 STP 802.1d, Config, Flags [none], bridge-id 0000.40:2b:50:5b:24:d2.8001, length 43
20:58:06.532362 STP 802.1d, Config, Flags [none], bridge-id 0000.40:2b:50:5b:24:d2.8001, length 43
20:58:07.532319 STP 802.1d, Config, Flags [none], bridge-id 0000.40:2b:50:5b:24:d2.8001, length 43
20:58:08.532228 STP 802.1d, Config, Flags [none], bridge-id 0000.40:2b:50:5b:24:d2.8001, length 43
20:58:09.532352 STP 802.1d, Config, Flags [none], bridge-id 0000.40:2b:50:5b:24:d2.8001, length 43
20:58:10.532185 STP 802.1d, Config, Flags [none], bridge-id 0000.40:2b:50:5b:24:d2.8001, length 43
20:58:10.927227 IP 192.168.1.108.16608 > one.one.one.one.53: 46961+ PTR? 1.0.0.1.in-addr.arpa. (38)
20:58:10.927374 IP 192.168.1.108.16608 > one.one.one.one.53: 46961+ PTR? 1.0.0.1.in-addr.arpa. (38)
20:58:10.933125 IP one.one.one.one.53 > 192.168.1.108.16608: 46961 1/0/0 PTR one.one.one.one. (67)
20:58:10.933125 IP one.one.one.one.53 > 192.168.1.108.16608: 46961 1/0/0 PTR one.one.one.one. (67)
20:58:10.934585 IP 192.168.1.108.38078 > one.one.one.one.53: 54008+ PTR? 1.1.1.1.in-addr.arpa. (38)
20:58:10.940615 IP one.one.one.one.53 > 192.168.1.108.38078: 54008 1/0/0 PTR one.one.one.one. (67)
20:58:10.945552 IP 192.168.1.254.53 > 192.168.1.108.16608: 46961 1/0/0 PTR one.one.one.one. (67)
20:58:11.532343 STP 802.1d, Config, Flags [none], bridge-id 0000.40:2b:50:5b:24:d2.8001, length 43
^C186 packets captured
186 packets received by filter
0 packets dropped by kernel