Hi all,
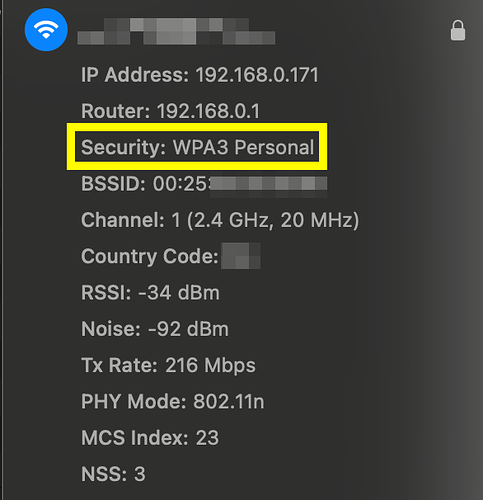
I have my Linksys WRT1900ACS set to mixed WPA2/WPA3 (option encryption 'sae-mixed') for one SSID. When I connect from my Macbook Pro 2019, it shows "WPA3 Personal" as expected.
Interestingly, an active scan using the third-party macOS tool WiFi Explorer Pro 3 from Intuitibits shows the same BSSID as "WPA2 (PSK)". A passive scan however shows it correctly as "WPA2/WPA3 (PSK/SAE).
I reported it to the developer of WiFi Explorer Pro 3 as I first thought it's a bug on their side, and the main developer helped to look through my data captures.
His answer:
It appears there’s an issue in OpenWrt where the RSN information element in the probe response doesn’t match the element in beacons. In fact, the RSN information element in the probe response seems to contain bogus information. This causes WiFi Explorer to show the wrong security configuration when you’re not connected to the AP. Once connected, macOS may provide WiFi Explorer with cached beacons instead of probe responses (this is an internal optimization that macOS performs, not WiFi Explorer).
Fortunately, the capture you sent us contained both beacons and probe responses from the AP in question, and that helped in finding the problem.
Below is the RSN information element from a beacon. Note that the Auth Key Management Suite List correctly enumerates PSK (WPA2) and SAE (WPA3) as supported AKMs. This is expected when using mixed mode.
RSNE - Group Cipher: CCMP-128; Pairwise Cipher(s): CCMP-128; AKM Suite(s): PSK, FT using PSK, PSK (SHA-256), SAE (SHA-256), FT using SAE (SHA-256); MFP Capable
Element ID: 48
Length: 36 bytes
RSN Version: 1
Group Cipher Suite OUI: 00-0F-AC (IEEE 802.11)
Group Cipher Suite Type: CCMP-128 (4)
Pairwise Cipher Suite Count: 1
Pairwise Cipher Suite List
Pairwise Cipher Suite OUI: 00-0F-AC (IEEE 802.11)
Pairwise Cipher Suite Type: CCMP-128 (4)
Auth Key Management Suite Count: 5
Auth Key Management Suite List
Auth Key Management Suite OUI: 00-0F-AC (IEEE 802.11)
Auth Key Management Suite Type: PSK (2)
Auth Key Management Suite OUI: 00-0F-AC (IEEE 802.11)
Auth Key Management Suite Type: FT using PSK (4)
Auth Key Management Suite OUI: 00-0F-AC (IEEE 802.11)
Auth Key Management Suite Type: PSK (SHA-256) (6)
Auth Key Management Suite OUI: 00-0F-AC (IEEE 802.11)
Auth Key Management Suite Type: SAE (SHA-256) (8)
Auth Key Management Suite OUI: 00-0F-AC (IEEE 802.11)
Auth Key Management Suite Type: FT using SAE (SHA-256) (9)
RSN Capabilities: 0x008c
.... .... .... ...0 RSN Pre-Authentication Capabilities: Not supported
.... .... .... ..0. RSN No Pairwise Capabilities: STA can support WEP default key simultaneously with Pairwise key
.... .... .... 11.. RSN PTKSA Replay Counter Capabilities: 16 replay counters (0x0003)
.... .... ..00 .... RSN GTKSA Replay Counter Capabilities: 1 replay counter (0x0000)
.... .... .0.. .... Management Frame Protection Required: No
.... .... 1... .... Management Frame Protection Capable: Yes
.... ...0 .... .... Joint Multi-band RSNA: Not supported
.... ..0. .... .... PeerKey Enabled: No
And here’s the RSN information element from a probe response. Note that the AKM List only enumerates PSK. Instead, three bogus AKMs are listed, and it doesn’t include SAE. In my opinion, this is a bug in OpenWrt.
RSNE - Group Cipher: CCMP-128; Pairwise Cipher(s): CCMP-128; AKM Suite(s): PSK, FT using PSK, None, None, None
Element ID: 48
Length: 36 bytes
RSN Version: 1
Group Cipher Suite OUI: 00-0F-AC (IEEE 802.11)
Group Cipher Suite Type: CCMP-128 (4)
Pairwise Cipher Suite Count: 1
Pairwise Cipher Suite List
Pairwise Cipher Suite OUI: 00-0F-AC (IEEE 802.11)
Pairwise Cipher Suite Type: CCMP-128 (4)
Auth Key Management Suite Count: 5
Auth Key Management Suite List
Auth Key Management Suite OUI: 00-0F-AC (IEEE 802.11)
Auth Key Management Suite Type: PSK (2)
Auth Key Management Suite OUI: 00-0F-AC (IEEE 802.11)
Auth Key Management Suite Type: FT using PSK (4)
Auth Key Management Suite OUI: 00-0F-00 (Legra Systems Inc.)
Auth Key Management Suite Type: None (0)
Auth Key Management Suite OUI: 00-00-00 (Xerox Corp.)
Auth Key Management Suite Type: None (0)
Auth Key Management Suite OUI: 00-00-00 (Xerox Corp.)
Auth Key Management Suite Type: None (0)
RSN Capabilities: 0x0000
.... .... .... ...0 RSN Pre-Authentication Capabilities: Not supported
.... .... .... ..0. RSN No Pairwise Capabilities: STA can support WEP default key simultaneously with Pairwise key
.... .... .... 00.. RSN PTKSA Replay Counter Capabilities: 1 replay counter (0x0000)
.... .... ..00 .... RSN GTKSA Replay Counter Capabilities: 1 replay counter (0x0000)
.... .... .0.. .... Management Frame Protection Required: No
.... .... 0... .... Management Frame Protection Capable: No
.... ...0 .... .... Joint Multi-band RSNA: Not supported
.... ..0. .... .... PeerKey Enabled: No
I am using OpenWrt 23.05.2 r23630.
Can someone reproduce this behaviour? Is this a bug?
Thanks,
softice