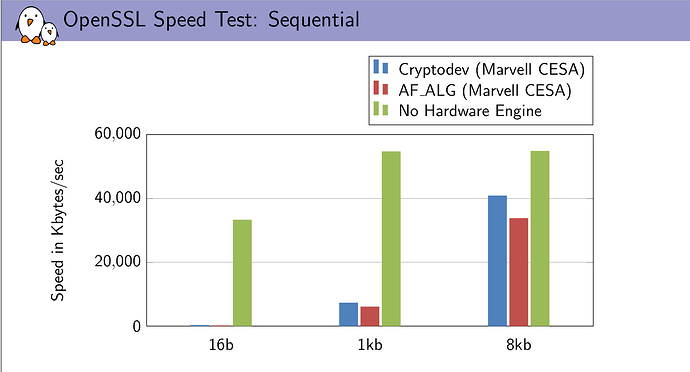
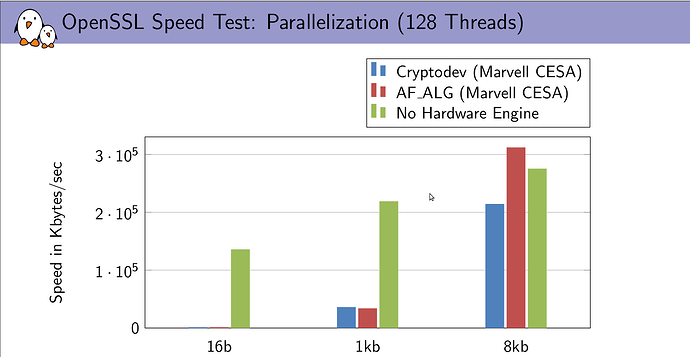
I made some searches on the Web. According to this, cryptodev has better performance than AF_ALG API. However, according to more recent sources here 2014, here 2017 and here, software implementation outperforms both cryptodev and AF_ALG especially for small data size (TCP/UDP/IP about 64kBytes, ethernet between 1.5kBytes for standard frame and 9kBytes for jumbo frame). Moreover, according to latest benchmark here the difference between cryptodev and AF_ALG is not so high as showed here.
In my opinion using the cryptodev approach + the 3rd party module is the wrong way. I can only suggest perhaps someone picks this up as a task to have a look at Crypto API based acceleration.
Since AF_ALG is into the kernel and since OpenSSL 1.1 supports it, I agree that is the right way to go.
As soon as OpenSSL 1.1 is officially in OpenWRT both approaches should work and switching between the two options is just a matter of changing engine. The AF_ALG engine in OpenSSL is a little more flexible in terms of selecting which encryption method or hash is using the engine.
I hope that OpenSSL 1.1 package will come soon after openWRT 18.06 release. I read your [thread](Status of OpenSSL 1.1 Lede/OpenWrt? kmod-crypto-test).
Finally, the performance of various OpenSSL on my PC (i7- i7-3537U) are reported below.
openssl speed -elapsed md5 sha256 sha512 des-ede3 aes-192-cbc aes-256-cbc
OpenSSL 1.0.2g 1 Mar 2016
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes
md5 53154.38k 153379.90k 340930.30k 496694.95k 586377.90k
des ede3 23009.45k 23092.95k 23529.30k 23612.07k 23811.41k
aes-192 cbc 93006.03k 98322.52k 98695.85k 102235.14k 100177.24k
aes-256 cbc 80941.49k 83786.88k 83017.22k 77857.45k 82927.62k
sha256 55436.81k 124654.14k 219929.43k 266457.43k 277113.51k
sha512 38305.91k 155056.85k 249469.61k 344811.52k 395487.91
OpenSSL 1.0.2o 27 Mar 2018
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes
md5 36815.35k 115230.29k 304914.77k 481625.43k 585973.76k
des ede3 22890.91k 23685.12k 23256.23k 23674.88k 23568.38k
aes-192 cbc 88807.08k 95228.42k 99297.11k 95685.97k 98899.29k
aes-256 cbc 79682.97k 85615.96k 85707.69k 86874.79k 86876.16k
sha256 59590.05k 132226.45k 227302.66k 277670.23k 293915.31k
sha512 41993.43k 165328.75k 238422.27k 356699.48k 410555.73k
OpenSSL 1.1.0h 27 Mar 2018
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes 16384 bytes
md5 106596.49k 246759.36k 441293.65k 554538.33k 596413.10k 592942.42k
des ede3 22817.63k 23257.19k 22951.51k 23186.09k 23358.12k 23358.12k
aes-192 cbc 89113.88k 91224.68k 99162.88k 100212.05k 93547.18k 90030.08k
aes-256 cbc 77074.08k 80776.85k 84904.96k 82820.44k 87135.57k 87610.71k
sha256 57051.51k 130352.60k 226432.43k 276851.71k 291703.47k 297451.52k
sha512 39645.48k 160842.07k 248906.67k 362397.35k 416626.01k 414302.21k
Excluding md5 cipher, there is not great difference between latest OpenSSL 1.0.2o and OpenSSL 1.1.0h. So I do not expect any performance improvement on 18.06 and OpenSSL 1.1.0h. However, only benchmark can tell the truth.
Single thread
Multi thread