Hi,
I just bougth a BT Homehub 5A router and I found it a great router together with latest openWRT.
I would like to configure it as VPN client in order to protect all my LAN. I'm using protonVPN as service both free and paid versions. I followed this guide in order to setup it into my openWRT.
If I use standard openVPN client from my GNU/linux OS, I can connect to protonVPN and it works well.
I used different protonVPN accounts with different servers and via UDP.
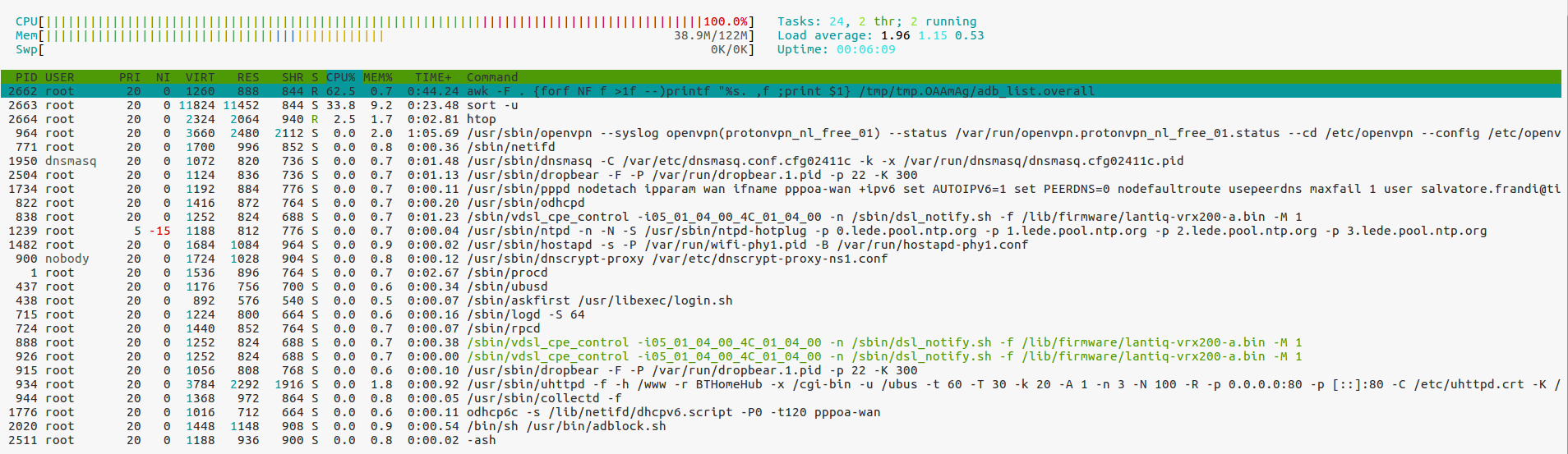
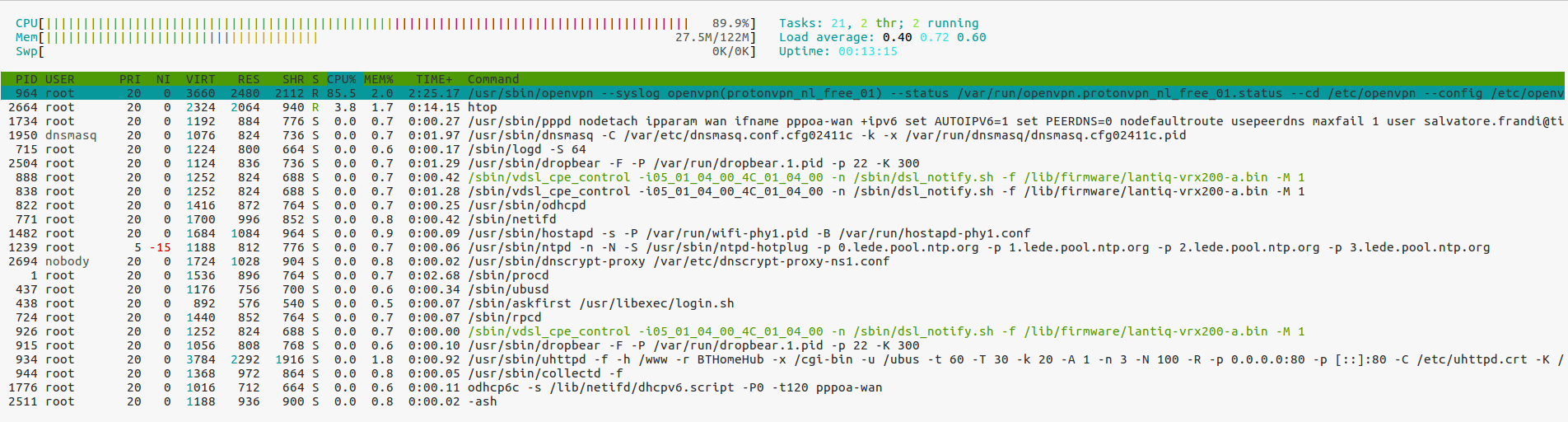
Then, I tried to use the same accounts and the same servers via openVPN on my openWRT router and in this case, I can connect to protonVPN, but I cannot navigate. When the router finishes the boot I can navigate on Internet for less than one minute.
I think that sources of the problem could be two:
- Insufficient processing power
- Wrong configuration
For the first point. The router has SoC: Lantiq XWAY VRX268 (PSB 80910 EL V1.2) MIPS 34Kc and 128 MB RAM with openWRT 17.01.4 and kernel 4.4.92.
I also ran benchmark in order to test encryption performance following this guide:
| r3560 | xRX200 rev 1.2 | BTHOMEHUBV5A - BT Home Hub 5A | MIPS 34Kc V5.6 | 332.54 | 1.0.2o | 25504330 | 22153860 | 12252030 | 3649200 | 3882310 | 1475740 | 6657450 | 5786680 | 5134420 | 5.5 | 206.2 15.8 | 16.7 |
This is my laptop (i7- i7-3537U) in which openVPN works well:
| | 1.0.2o | 424338410 | 344252780 | 199024370 | 228348100 | 57664760 | 18779730 | 96382760 | 91406340 | 57513530 | 455.4 | 18359.5 1639.3 | 1371.7 |
Both are using the same version of openSSL 1.0.2o. i7 is 10-15 times faster than SoC.
Do you think that the bottleneck is into CPU?
In other thread, an user suggested that the SoC has a crypto CPU embedded compatible with openWRT via package kmod-crypto-user even if it requires openSSL 1.1.0 instead of 1.0.2 currently used by openWRT.
Do you think it could be a CPU bottleneck problem?
Regarding the second point. The configuration seems correct, however the behaviour it is strange since the connection is dropped quite instantly.
Do you have any advice?
Thank you
P.S.
output of cat /proc/crypto here
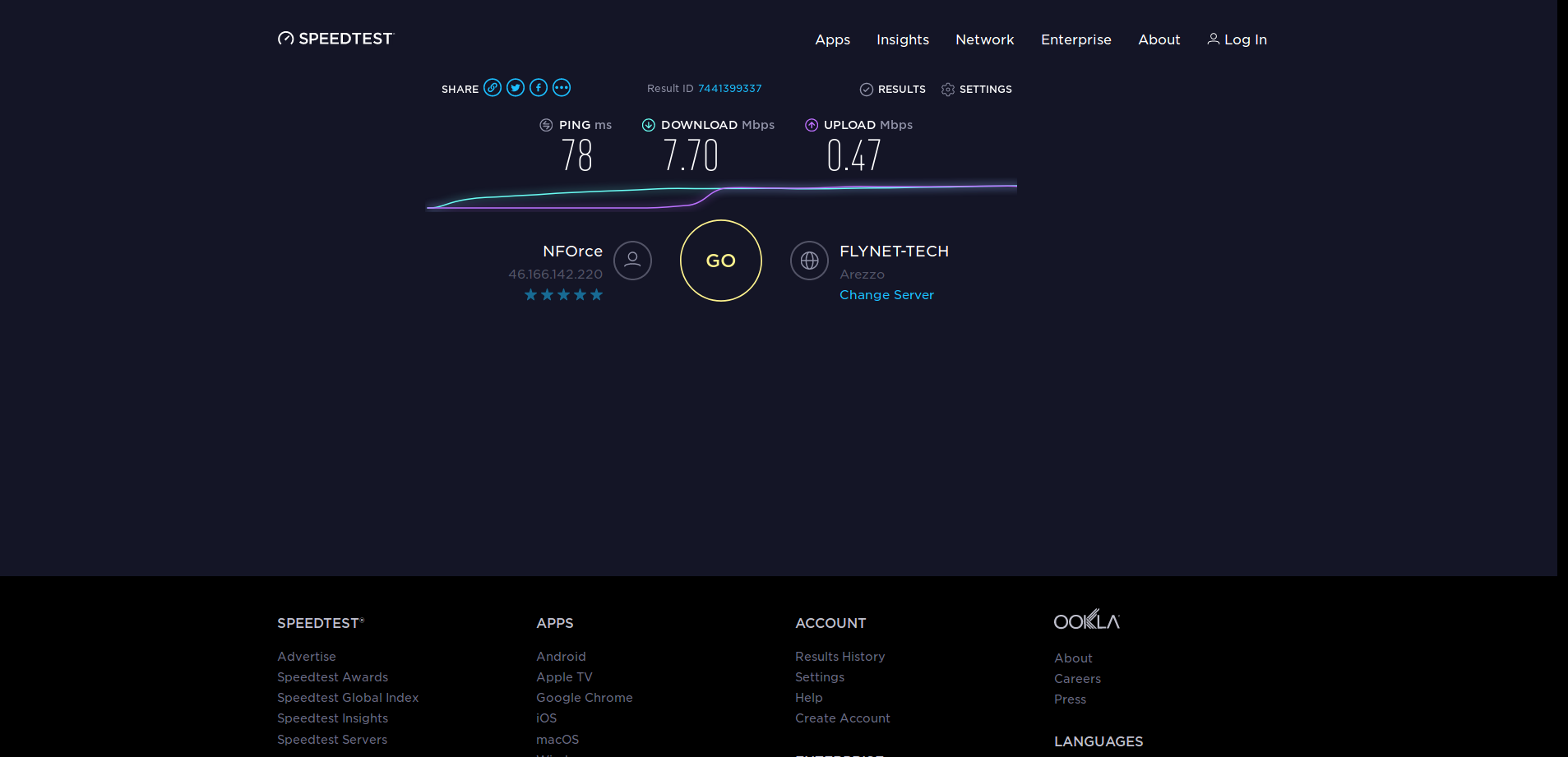
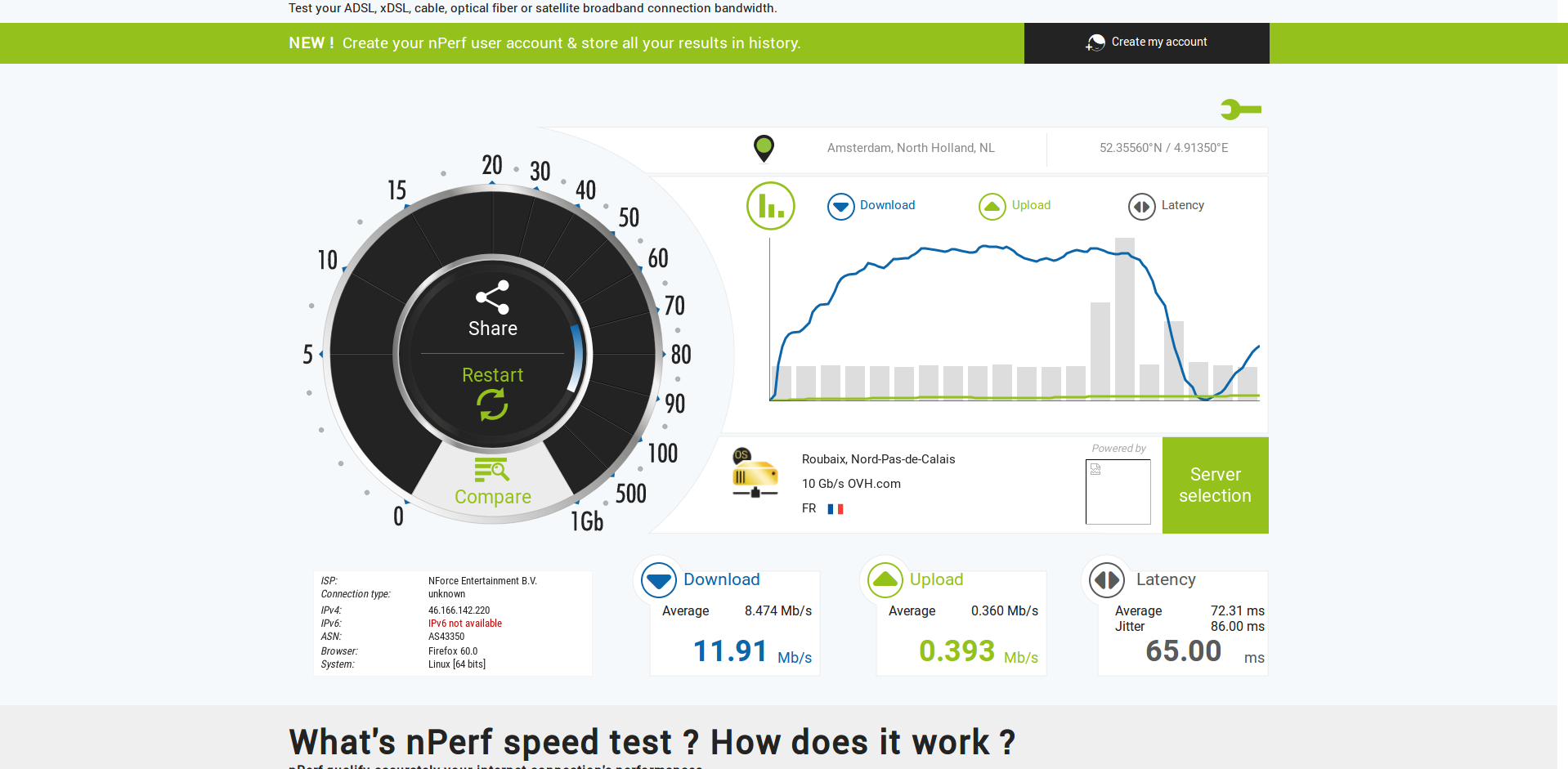
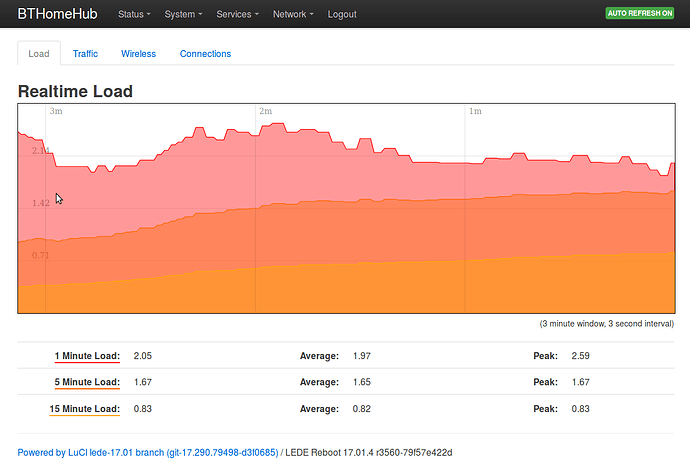
Real time load after boot no openVPN
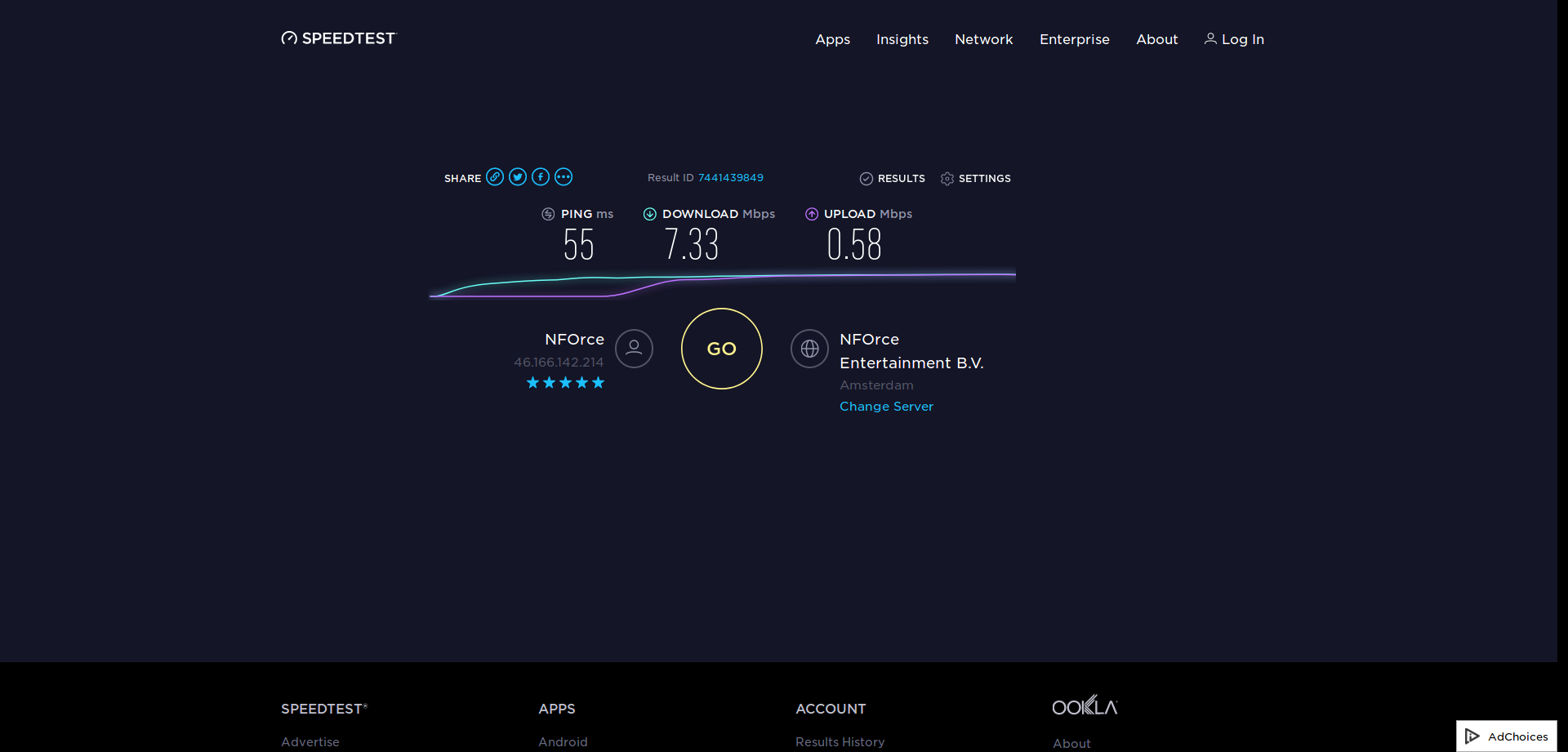
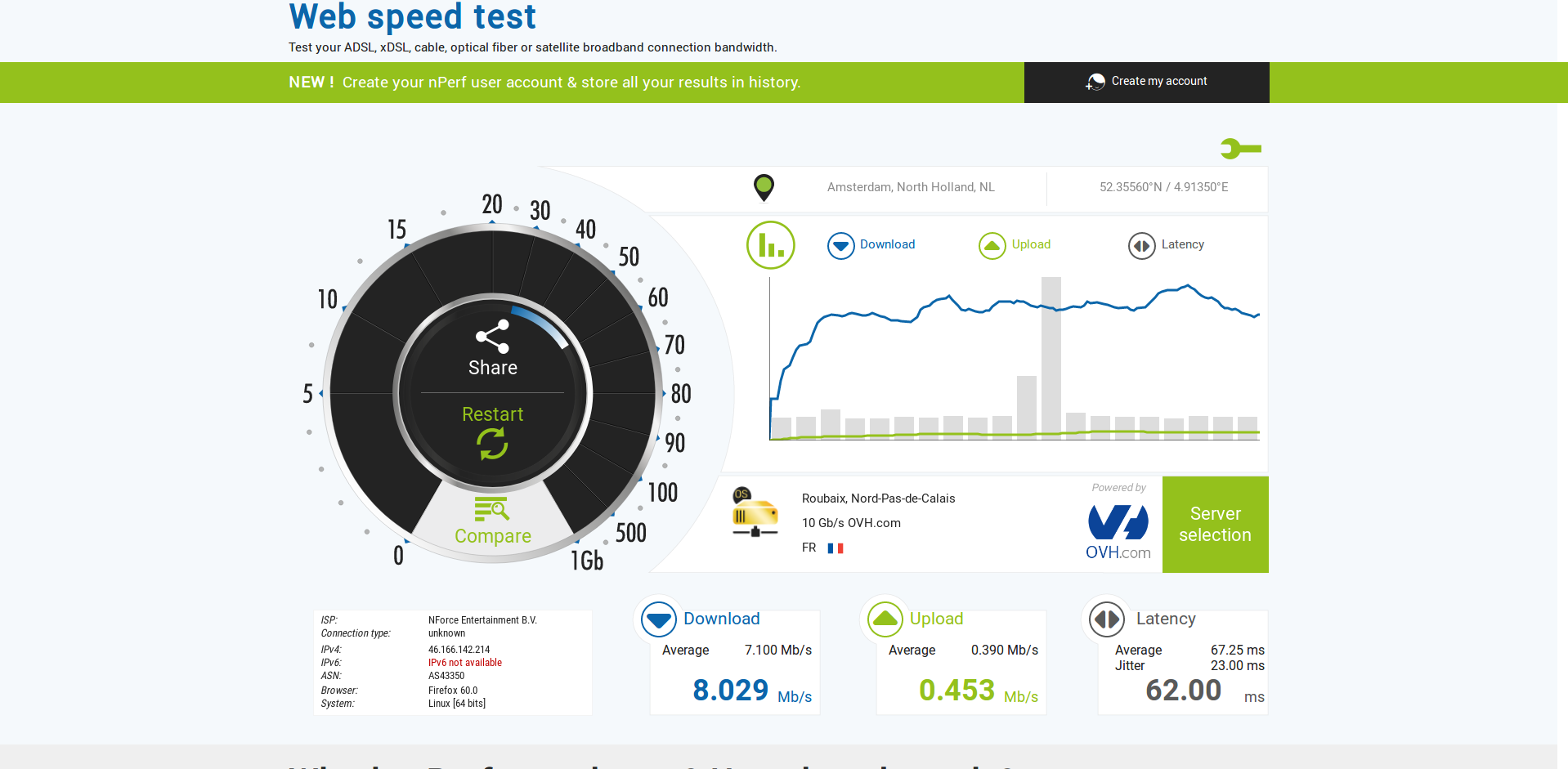
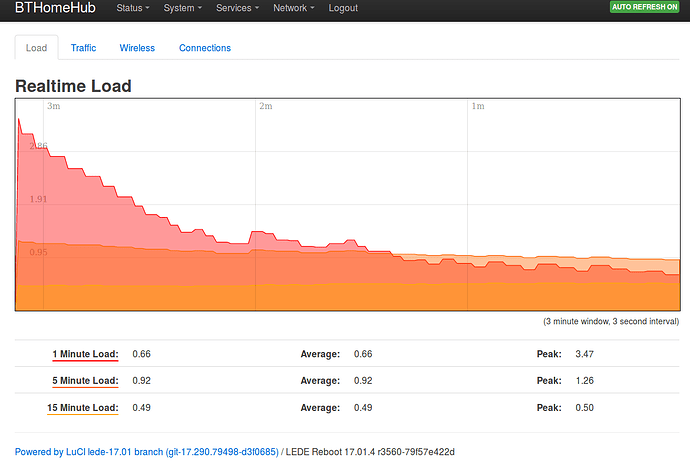
Real time load after boot with openVPN
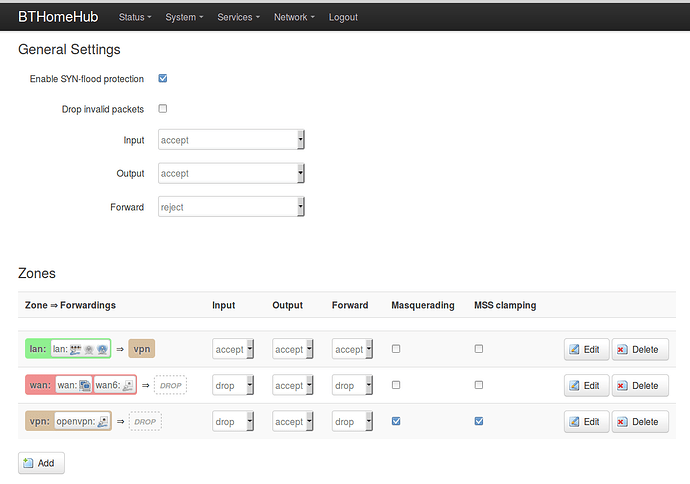
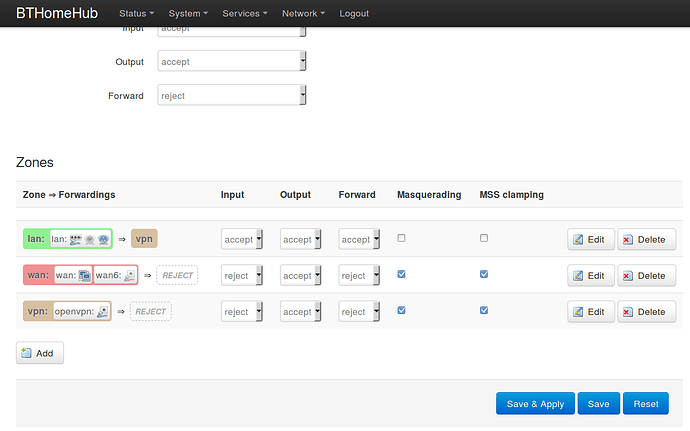
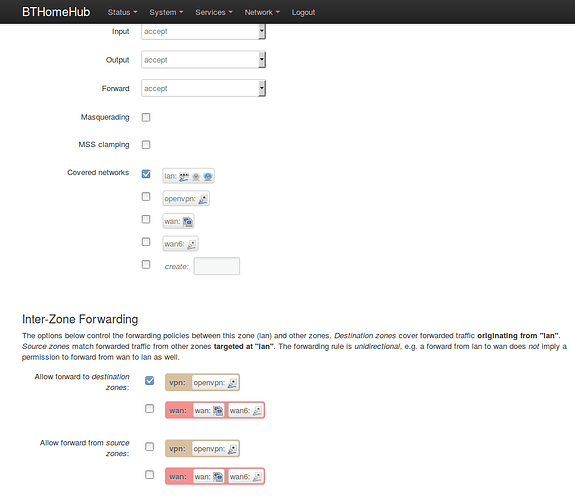
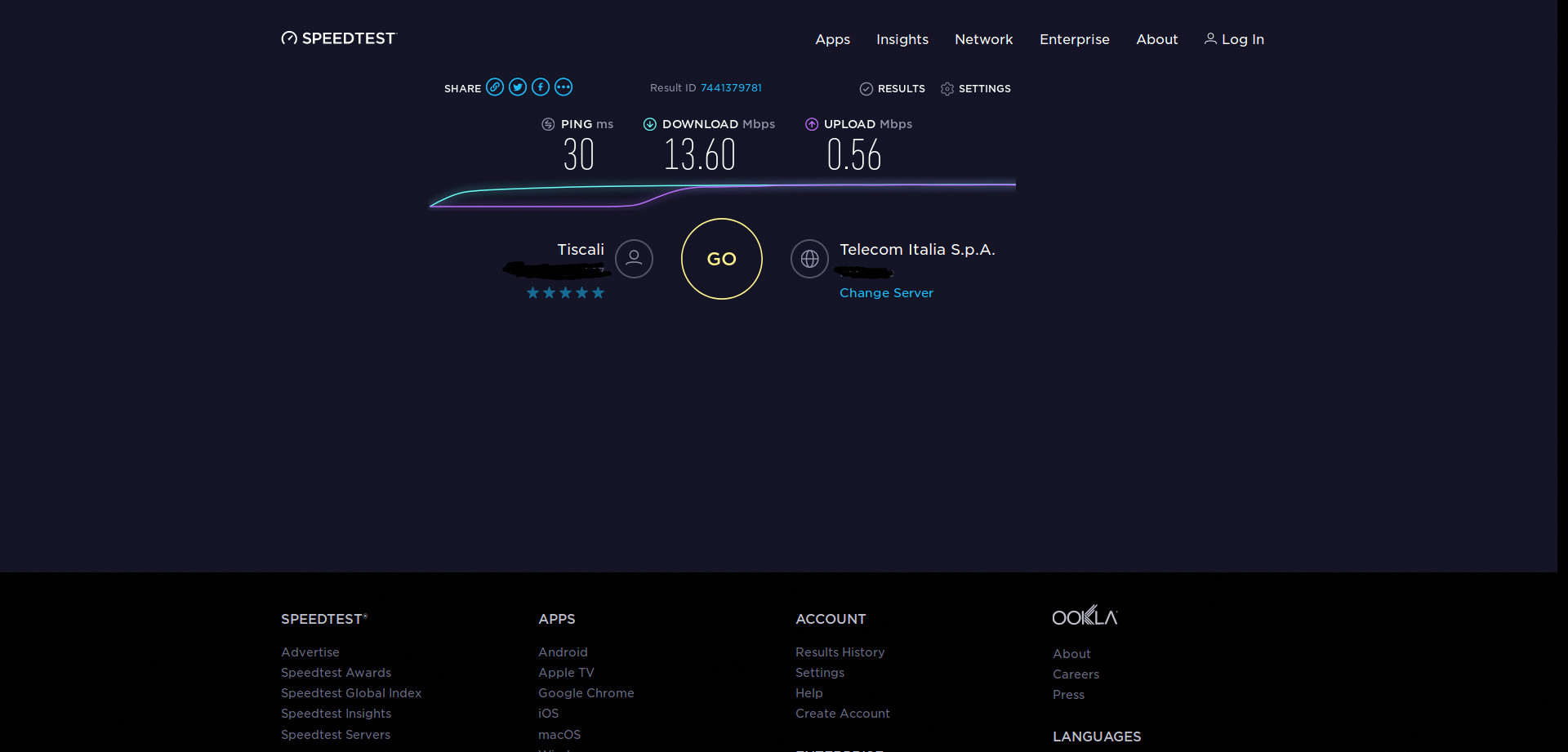 !
! !ù
!ù