This is how I prepared my Home Hub 5a for an OpenSSL benchmark with hardware crypto acceleration:
# download the SDK matching the OpenWrt version installed on your router:
wget https://downloads.openwrt.org/releases/18.06.0-rc1/targets/lantiq/xrx200/openwrt-sdk-18.06.0-rc1-lantiq-xrx200_gcc-7.3.0_musl.Linux-x86_64.tar.xz
tar xf openwrt-sdk-18.06.0-rc1-lantiq-xrx200_gcc-7.3.0_musl.Linux-x86_64.tar.xz
cd openwrt-sdk-18.06.0-rc1-lantiq-xrx200_gcc-7.3.0_musl.Linux-x86_64
scripts/feeds update base packages
scripts/feeds install openssl cryptodev-linux
sed -i -e 's/^PKG_RELEASE:=1$/PKG_RELEASE:=1.1/' feeds/base/package/libs/openssl/Makefile
make menuconfig
Global build settings -> # disable all 4 options
Kernel modules -> Cryptographic API modules -> <M> kmod-cryptodev
# return to top level menu: "Linux Kernel Configuration"
Libraries -> SSL -> <M> libopenssl ->
[*] Crypto acceleration support
[*] Digests acceleration support
Utilities -> <M> openssl-util
make download
make -j5
# find build results under bin/
bin/targets/lantiq/xrx200/packages/kmod-cryptodev_4.9.109+1.9.git-2017-10-04-lantiq-1_mips_24kc.ipk
bin/packages/mips_24kc/base/libopenssl_1.0.2o-1.1_mips_24kc.ipk
bin/packages/mips_24kc/base/openssl-util_1.0.2o-1.1_mips_24kc.ipk
# copy packages to router, install with opkg
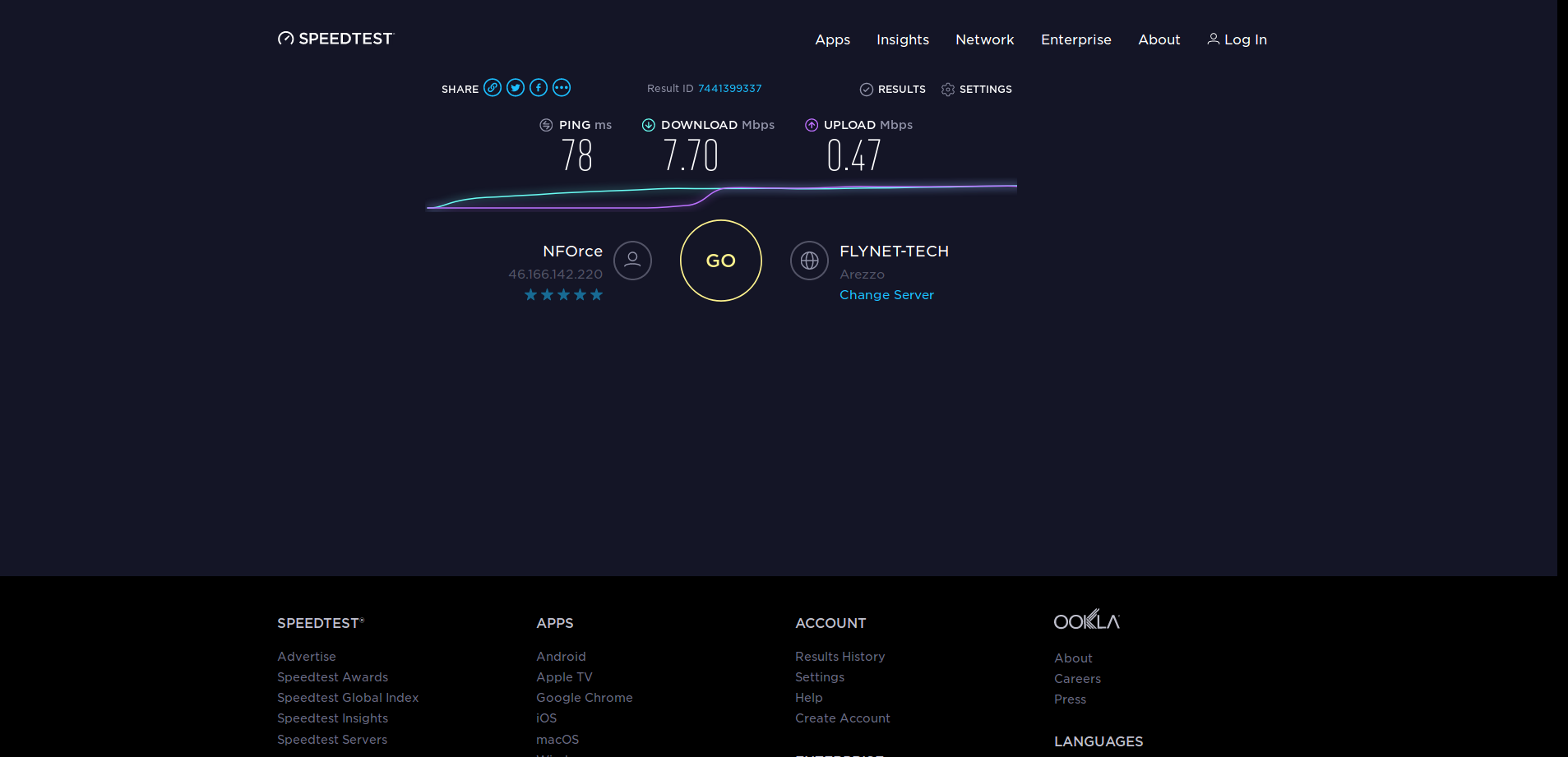
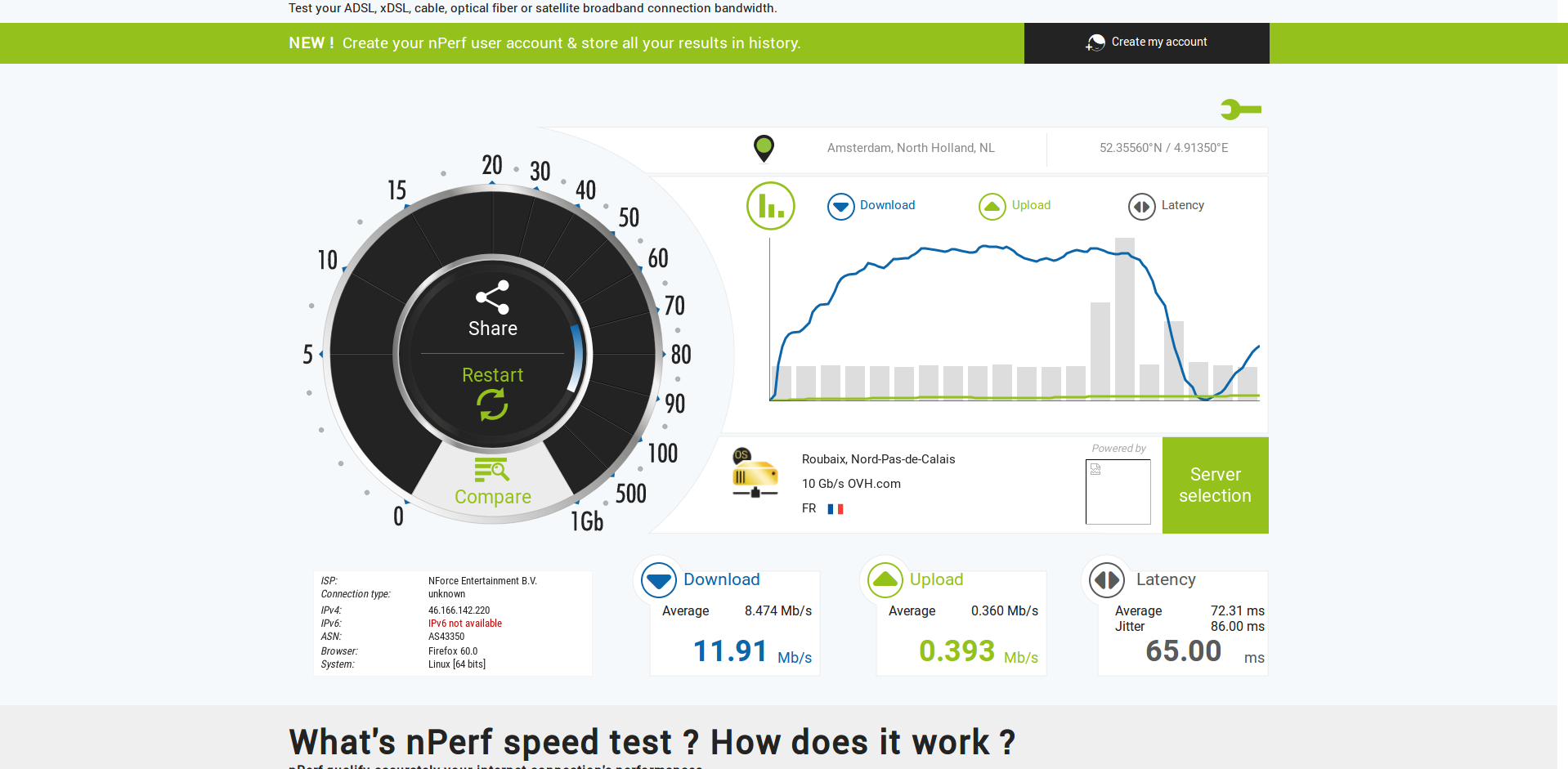
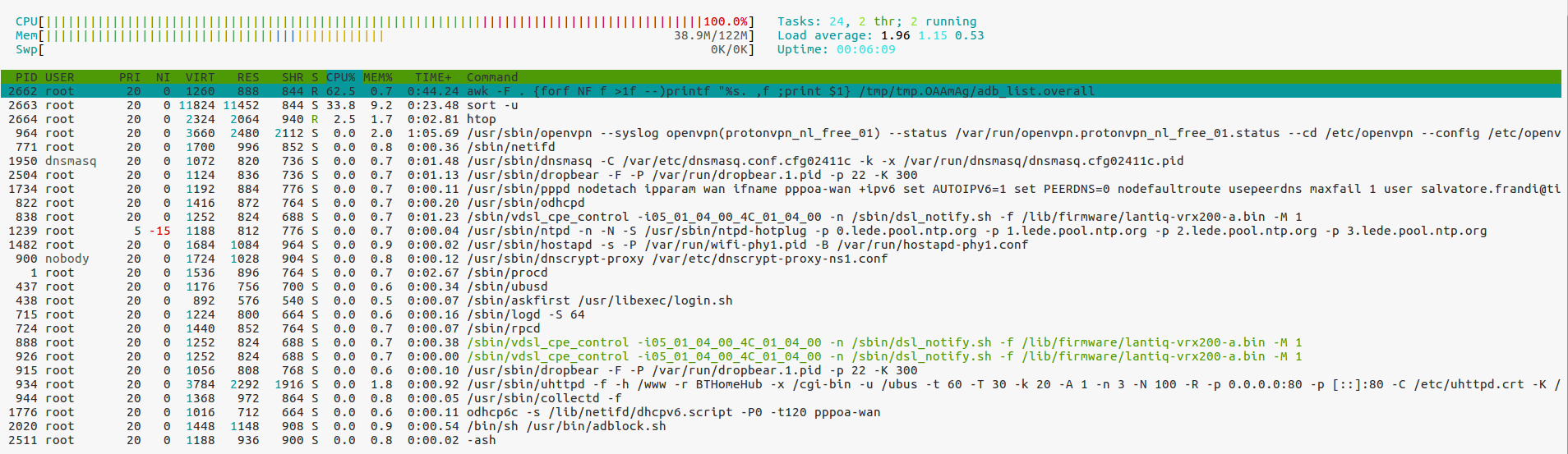
Now to the benchmark results. First with OpenSSL built-in crypto (no acceleration):
# rmmod cryptodev
# openssl engine -c -t
(dynamic) Dynamic engine loading support
[ unavailable ]
# openssl speed md5 sha1 sha256 aes-128-cbc aes-256-cbc
[...]
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes
md5 1004.44k 3689.23k 11875.46k 26415.79k 40771.58k
sha1 1221.11k 4219.29k 11907.67k 21875.71k 28983.30k
aes-128 cbc 5853.58k 6478.76k 6663.00k 6718.12k 6725.63k
aes-256 cbc 4589.95k 4977.60k 5083.90k 5106.35k 5114.54k
sha256 2342.86k 5436.57k 9545.22k 11838.67k 12626.60k
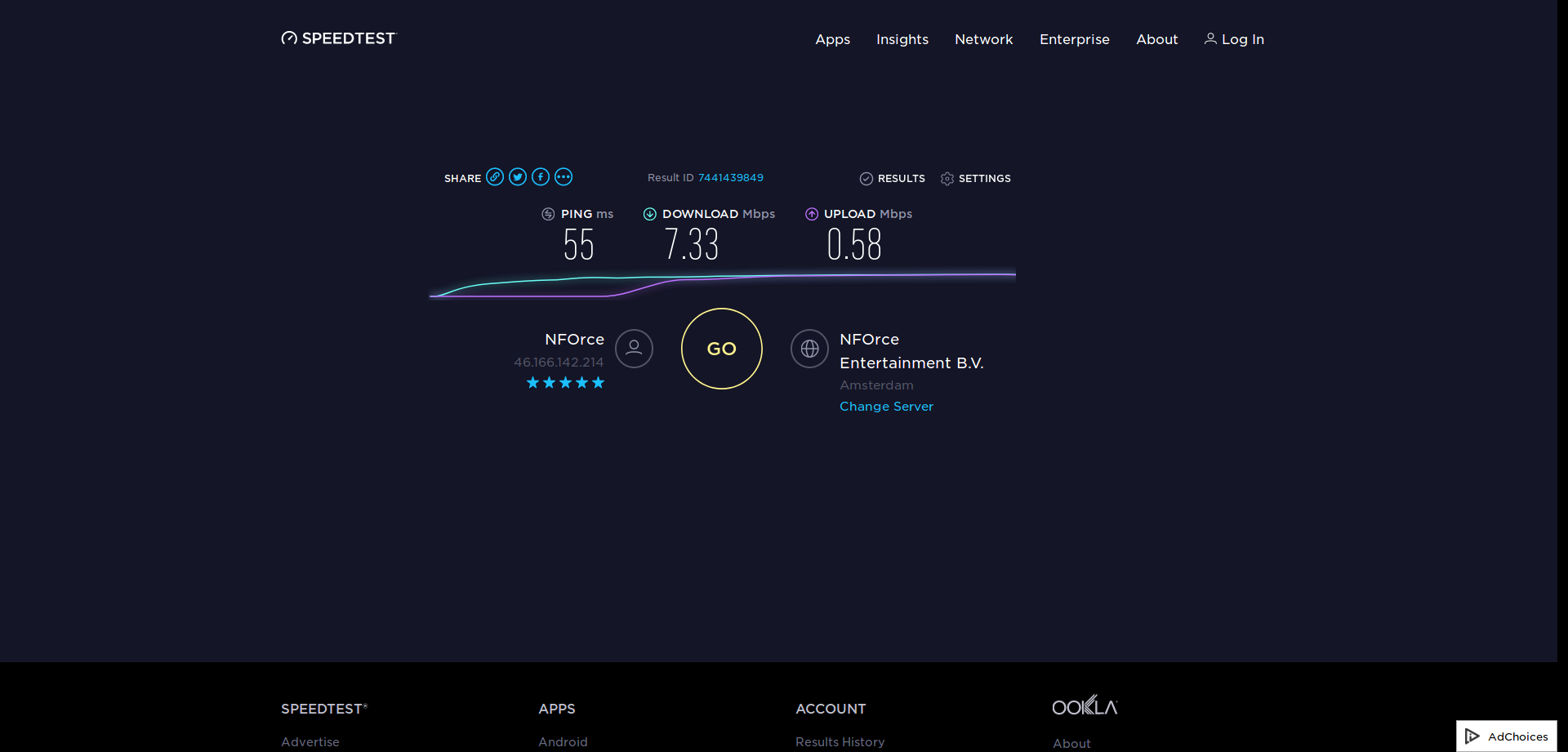
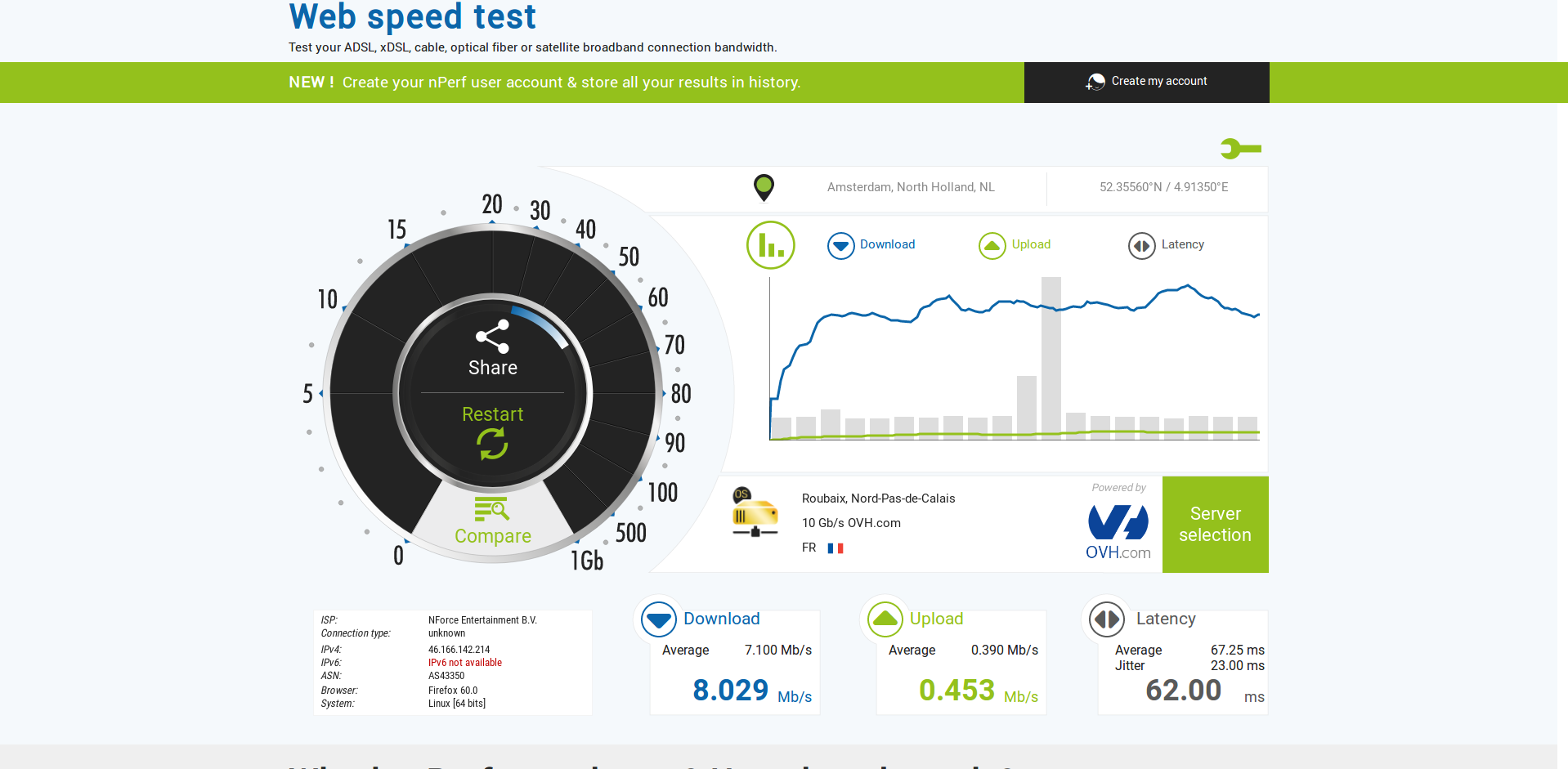
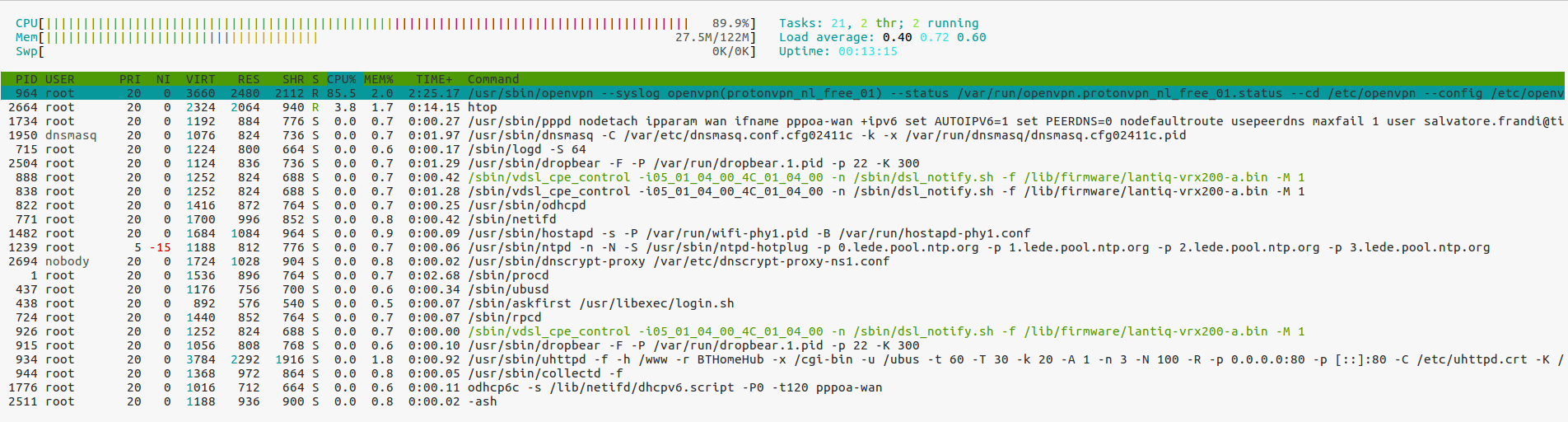
Second, with hardware acceleration through cryptodev:
# modprobe cryptodev
# openssl engine -c -t
(cryptodev) BSD cryptodev engine
[RSA, DSA, DH, DES-CBC, AES-128-CBC, AES-192-CBC, AES-256-CBC, hmacWithMD5, hmacWithSHA1, MD5, SHA1]
[ available ]
(dynamic) Dynamic engine loading support
[ unavailable ]
# openssl speed -engine cryptodev md5 sha1 sha256 aes-128-cbc aes-256-cbc
engine "cryptodev" set.
[...]
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes
md5 358.83k 1438.15k 5096.50k 19664.49k 163187.98k
sha1 385.79k 1484.09k 6103.97k 23343.18k 211105.93k
aes-128 cbc 5834.75k 6467.58k 6670.76k 6727.68k 6745.39k
aes-256 cbc 4592.57k 4973.93k 5084.07k 5131.64k 5134.38k
sha256 2344.61k 5447.53k 9553.07k 11782.83k 12679.79k
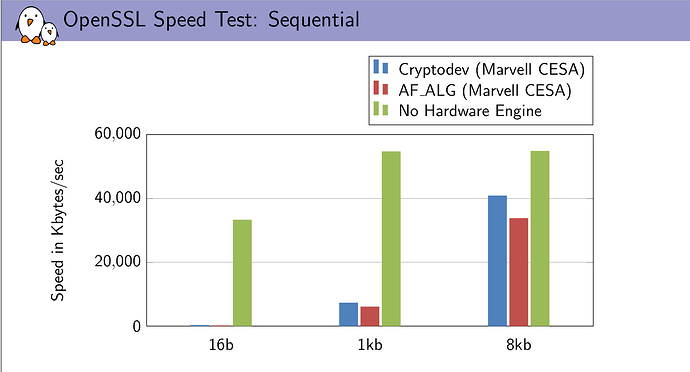
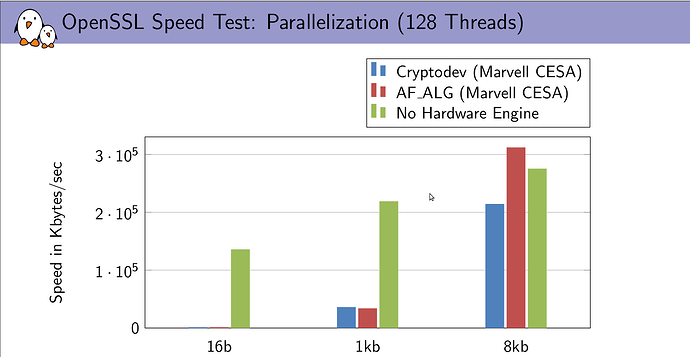
Bulk data transfers over VPN have a payload near 1500 bytes, so the most relevant column for this usecase should be 1024 bytes. For md5, cryptodev even brings a slowdown, and for sha1, a small speedup.
[EDIT: Please don't rely on these numbers. openssl speed should be invoked with option -elapsed as suggested by @drbrains below.]
However, aes-cbc and sha256 seem to be completely unaffected by the acceleration, perhaps it was not used at all. Maybe something about my setup is wrong, or maybe cryptodev is not fully supported by OpenSSL, I don't know.
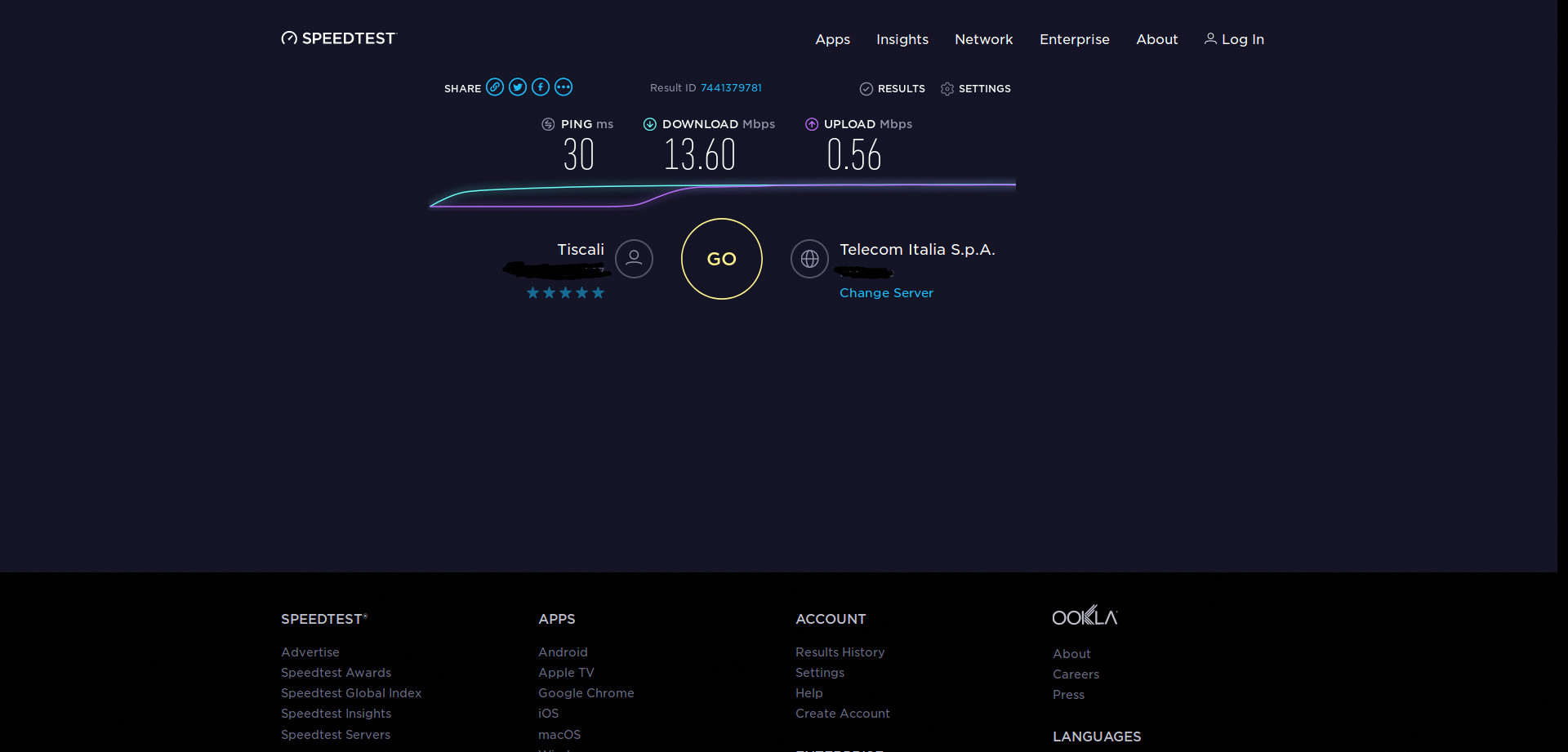
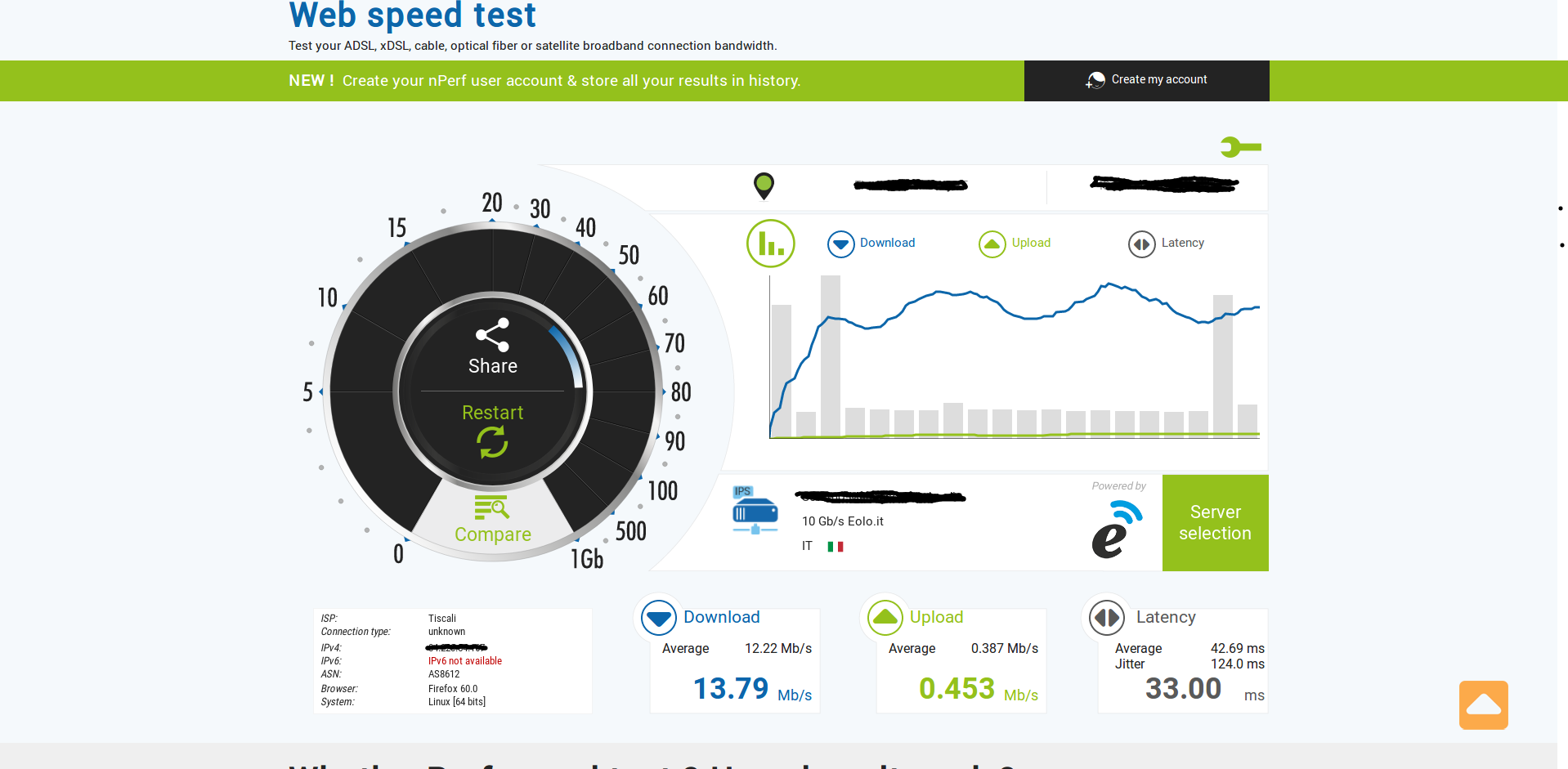
You can also see that encryption is multiple times faster than 9 Mbit/s. The low performance of OpenVPN is likely also caused by other processing, for example by copying data from and to userspace.
Use faster hardware, or use a VPN software which encrypts/decrypts in kernel space. With IPsec on the TP-Link TD-W8980, I get a throughput of 12..15 Mbits/s without acceleration, and 27 Mbits/s with crypto acceleration enabled (all measurements with conntrack disabled). Wireguard might also have good performance, I have not tried it.
 !
! !ù
!ù