Hello to all,
I'm still quite a newbie within the OpenWrt usage, but thanks to you I have succeeded in in setting up my global configuration:
So I have
1 Pi 4 & a USB3 to 1Gb adapter & 1Gb internet link (ISP box configured in bridge mode & fixed IP)
1 Pi 3b & a USB2 to 10/100Mb adapter & 20Mb internet link (ISP box configured in bridge mode & Non fixed IP --> NoIP defined)
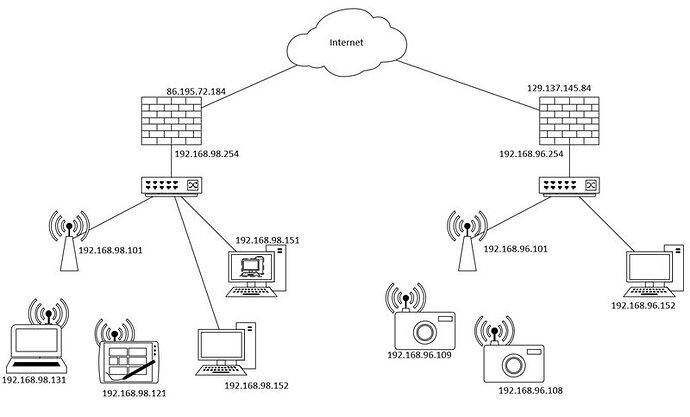
Everything is working quite well when I access the internet from any of the locations. Now I would like to access any of the locations from the other one. Below is an example of my network, the idea would be to access the security cameras 192.168.96.108 & 109 from a laptop 192.168.98.131 and to be able to control the workload running in 192.168.98.151 from PC 192.168.96.152
Could anyone help me on this?
Thx
what you want is a wireguard tunnel. Since one end has a fixed IP this should be easy to set up.
wireguard is a peer-to-peer (symmetric) tunnel system. You create public/private keys on each end, and then configure each end to accept the other end's traffic... it's pretty easy-peasy compared to for example OpenVPN
1 Like
Cool... interesting, I'm going to have a look to it tomorrow (yes in France already evening
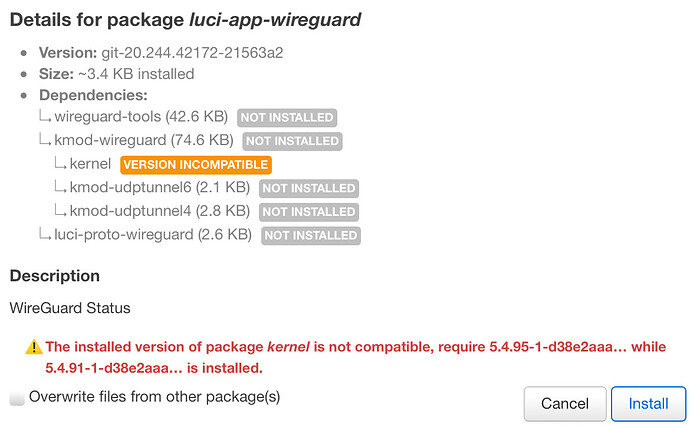
Realty looks interesting. However I have an issue with the kernel version. As I am using a Pi4 I don’t know if i can update the snapshot or if I have to reinstall from scratch.
I’ll continue digging!
Wow!... What a quick help. Thx @vgaetera I'm going to try this...
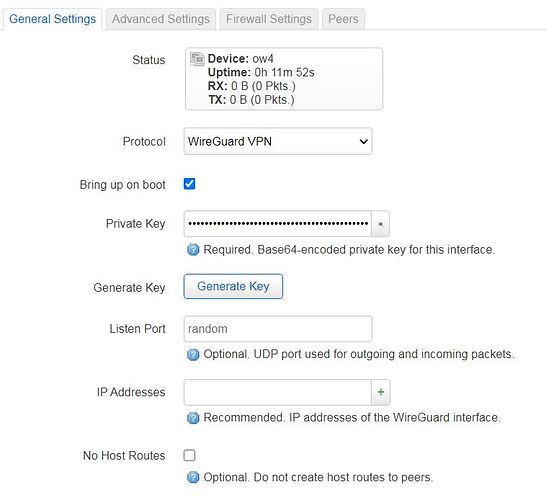
Setting up networkLuCI → Network → Interfaces → Add new interface… and select WireGuard VPN from the Protocol dropdown menu.
But there is a lot of information to fill!!!
IP Address: Do I need to setup a specific IP for the WireGuard link such as 192.168.95.1 & .2 with a netmask 255.255.255.253
For this one I suppose that I should select wan
& at last what is this IP supposed to be? My local network? the remote network? The remote peer IP?
Finally sorry to bother everyone here, but usually I do RTFM, & I will try to upgrade the one available when I understand how this works...
1 Like
krazeh
February 23, 2021, 5:29pm
7
No. You can add one if you like, but it's not necessary.
Add it to the LAN zone.
The subnet that you want to access at the other end. So 192.168.96.0/32 and 192.168.98.0/32 respectively. And tick the Route Allowed IPs box.
krazeh:
Add it to the LAN zone.
or to a new zone if you want to limit communication between the two LANs. Adding it to LAN zone will generally give 100% communication between the two remote LANs.
allowed IPs is the set of IP addresses the remote wireguard peer is allowed to pass over the tunnel... so on each end, it's the IP range in use at the remote site. Don't forget ipv6 ULA
OK I tried to implement all your recommendations on a local lab. below is the global design.
I did create a specific zone for the wg0. Now here is my problem:
I am connected on the PC 98.152 I can ping interface 95.1 but not 95.2
unreachable destination from 98.254
I am on the FW 98.254 same behavior
root@OpenWrt:~# ping 192.168.95.2
don't put any IP addresses on the wg0 interfaces, that's just confusing and useless.
The point, as I understand it... is that 192.168.98.0/24 devices can talk to 192.168.96.0/24 devices and vice versa...
so on the left hand router, put allowed ips 192.168.96.0/24, and on the right hand put 192.168.98.0/24 as allowed.
Then from the machine with 192.168.98.152 do ping to say 192.168.96.152 and vice-versa
2 Likes
My MacBook is 192.168.96.152
MacBook:~ air$ ping 192.168.98.152
However if from the same MacBook I ssh to the 192.168.96.254 & from there I ping 192.168.99.98 it works!
krazeh
February 23, 2021, 7:02pm
13
What are your configs on the openwrt routers? Please run the following commands (copy-paste the whole block) and paste the output here, using the "Preformatted text </> " button:
uci export network; \
uci export dhcp; uci export firewall; \
head -n -0 /etc/firewall.user; \
iptables-save -c; \
ip -4 addr ; ip -4 ro li tab all ; ip -4 ru
Here it goes...
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd99:0306:2fe1::/48'
config interface 'lan'
option ifname 'eth0'
option proto 'static'
option ipaddr '192.168.98.254'
option netmask '255.255.255.0'
option ip6assign '60'
option gateway '192.168.99.254'
list dns '8.8.8.8'
list dns '9.9.9.9'
list dns '1.1.1.1'
config interface 'wan'
option ifname 'eth1'
option proto 'dhcp'
config interface 'wg0'
option proto 'wireguard'
option private_key 'XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX'
option listen_port '51888'
config wireguard_wg0
option description 'ow3'
option public_key 'AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA'
option route_allowed_ips '1'
list allowed_ips '192.168.96.0/24'
package dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
option ra_management '1'
option start '10'
option limit '40'
list dhcp_option '42,192.168.98.254'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option dns '1'
option mac '2C:9E:FC:09:D9:42'
option ip '192.168.98.100'
option name 'mg5250'
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
config zone
option name 'Intercom'
option network 'wg0'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
# Generated by iptables-save v1.8.7 on Tue Feb 23 20:16:00 2021
*nat
:PREROUTING ACCEPT [399:105333]
:INPUT ACCEPT [138:10415]
:OUTPUT ACCEPT [288:19010]
:POSTROUTING ACCEPT [7:494]
:postrouting_Intercom_rule - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_Intercom_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_Intercom_postrouting - [0:0]
:zone_Intercom_prerouting - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[399:105333] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[331:89213] -A PREROUTING -i eth0 -m comment --comment "!fw3" -j zone_lan_prerouting
[68:16120] -A PREROUTING -i eth1 -m comment --comment "!fw3" -j zone_wan_prerouting
[0:0] -A PREROUTING -i wg0 -m comment --comment "!fw3" -j zone_Intercom_prerouting
[424:86314] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[0:0] -A POSTROUTING -o eth0 -m comment --comment "!fw3" -j zone_lan_postrouting
[417:85820] -A POSTROUTING -o eth1 -m comment --comment "!fw3" -j zone_wan_postrouting
[0:0] -A POSTROUTING -o wg0 -m comment --comment "!fw3" -j zone_Intercom_postrouting
[0:0] -A zone_Intercom_postrouting -m comment --comment "!fw3: Custom Intercom postrouting rule chain" -j postrouting_Intercom_rule
[0:0] -A zone_Intercom_prerouting -m comment --comment "!fw3: Custom Intercom prerouting rule chain" -j prerouting_Intercom_rule
[0:0] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[331:89213] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[417:85820] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[417:85820] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[68:16120] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Tue Feb 23 20:16:00 2021
# Generated by iptables-save v1.8.7 on Tue Feb 23 20:16:00 2021
*mangle
:PREROUTING ACCEPT [10550:2585131]
:INPUT ACCEPT [2418:244846]
:FORWARD ACCEPT [8061:2327459]
:OUTPUT ACCEPT [3963:508639]
:POSTROUTING ACCEPT [12001:2835178]
[81:4424] -A FORWARD -o eth1 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[81:4288] -A FORWARD -i eth1 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Tue Feb 23 20:16:00 2021
# Generated by iptables-save v1.8.7 on Tue Feb 23 20:16:00 2021
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_Intercom_rule - [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_Intercom_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_Intercom_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_Intercom_dest_ACCEPT - [0:0]
:zone_Intercom_dest_REJECT - [0:0]
:zone_Intercom_forward - [0:0]
:zone_Intercom_input - [0:0]
:zone_Intercom_output - [0:0]
:zone_Intercom_src_ACCEPT - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[50:4118] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[2370:240808] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[1927:164605] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[3:156] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[385:59603] -A INPUT -i eth0 -m comment --comment "!fw3" -j zone_lan_input
[58:16600] -A INPUT -i eth1 -m comment --comment "!fw3" -j zone_wan_input
[0:0] -A INPUT -i wg0 -m comment --comment "!fw3" -j zone_Intercom_input
[8062:2327512] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[7903:2259288] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[159:68224] -A FORWARD -i eth0 -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i eth1 -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -i wg0 -m comment --comment "!fw3" -j zone_Intercom_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[50:4118] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[3919:505929] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[3631:486977] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A OUTPUT -o eth0 -m comment --comment "!fw3" -j zone_lan_output
[288:18952] -A OUTPUT -o eth1 -m comment --comment "!fw3" -j zone_wan_output
[0:0] -A OUTPUT -o wg0 -m comment --comment "!fw3" -j zone_Intercom_output
[0:0] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[54:14788] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[3:156] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[0:0] -A zone_Intercom_dest_ACCEPT -o wg0 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_Intercom_dest_REJECT -o wg0 -m comment --comment "!fw3" -j reject
[0:0] -A zone_Intercom_forward -m comment --comment "!fw3: Custom Intercom forwarding rule chain" -j forwarding_Intercom_rule
[0:0] -A zone_Intercom_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_Intercom_forward -m comment --comment "!fw3" -j zone_Intercom_dest_REJECT
[0:0] -A zone_Intercom_input -m comment --comment "!fw3: Custom Intercom input rule chain" -j input_Intercom_rule
[0:0] -A zone_Intercom_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[0:0] -A zone_Intercom_input -m comment --comment "!fw3" -j zone_Intercom_src_ACCEPT
[0:0] -A zone_Intercom_output -m comment --comment "!fw3: Custom Intercom output rule chain" -j output_Intercom_rule
[0:0] -A zone_Intercom_output -m comment --comment "!fw3" -j zone_Intercom_dest_ACCEPT
[0:0] -A zone_Intercom_src_ACCEPT -i wg0 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_lan_dest_ACCEPT -o eth0 -m comment --comment "!fw3" -j ACCEPT
[159:68224] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[159:68224] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[385:59603] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[385:59603] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[0:0] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[0:0] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[385:59603] -A zone_lan_src_ACCEPT -i eth0 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[23:920] -A zone_wan_dest_ACCEPT -o eth1 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[424:86256] -A zone_wan_dest_ACCEPT -o eth1 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o eth1 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[58:16600] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[3:1728] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[1:84] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[54:14788] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[288:18952] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[288:18952] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[54:14788] -A zone_wan_src_REJECT -i eth1 -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Tue Feb 23 20:16:00 2021
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
inet 192.168.98.254/24 brd 192.168.98.255 scope global eth0
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP qlen 1000
inet 192.168.99.98/24 brd 192.168.99.255 scope global eth1
valid_lft forever preferred_lft forever
default via 192.168.99.254 dev eth1 src 192.168.99.98
192.168.96.0/24 dev wg0 scope link
192.168.98.0/24 dev eth0 scope link src 192.168.98.254
192.168.99.0/24 dev eth1 scope link src 192.168.99.98
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
broadcast 192.168.98.0 dev eth0 table local scope link src 192.168.98.254
local 192.168.98.254 dev eth0 table local scope host src 192.168.98.254
broadcast 192.168.98.255 dev eth0 table local scope link src 192.168.98.254
broadcast 192.168.99.0 dev eth1 table local scope link src 192.168.99.98
local 192.168.99.98 dev eth1 table local scope host src 192.168.99.98
broadcast 192.168.99.255 dev eth1 table local scope link src 192.168.99.98
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
hope this helps!!! Edit Sorry I hadn't seen the Preformatted text option
mk24
February 23, 2021, 7:58pm
15
The wg0 interface has not come up. I don't see any firewall rule opening port 51888 on the wan, which would be necessary to accept a Wireguard connection.
The other peer needs to be configured to connect to this peer's IP (on the "Internet", your .99 network) and port 51888.
2 Likes
Thx Mike,
I have created the new zone as defined earlier
Then to test I tried to authorize nearly everything (I'll fix later)
And still nothing works...
In order to establish a wireguard connection, at least one side of the two devices needs to listen for incoming UDP packets on the wireguard port. This means it needs an input rule allowing packets from WAN on that port.
2 Likes
Thanks Daniel & Mark,
Unfortunately I'm still stuck... Here is the detail of what I have done:
Install the last version of OpenWrt on both Pis (snapshot for Pi4)
Configure eth0 as fixed IP & setup dnsmasq
Disable wireless
Configure USB2Eth as eth1 DHCP IP from my ISP box so both FW get an eth1 IP in the same network & are able to see each other.
Installed WireGuard on both FW, generated keys, created interfaces wg0 in a new FWzone named Intercom
I created the FW rule below
firewall.@rule[0]=rule
firewall.@rule[0].family='ipv4'
firewall.@rule[0].proto='udp'
firewall.@rule[0].src='wan'
firewall.@rule[0].dest='lan'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].name='Allow WireGuard'
firewall.@rule[0].dest_port='51888'
At this point if I correctly understood, I should have the the wireguard connection up... and it is not
Any idea would help. I must admit that I tried everything I thought about, looked at several youtube (from Van Tech Corner) but nothing fixes this...
krazeh
February 26, 2021, 11:39am
19
Your firewall rule is wrong. The destination is the router, not the lan zone. Try running:
uci delete firewall.@rule[0].dest
uci commit firewall
/etc/init.d/firewall reload
Thx Krazeh...
Dis the change in both FW. Rebooted both FW

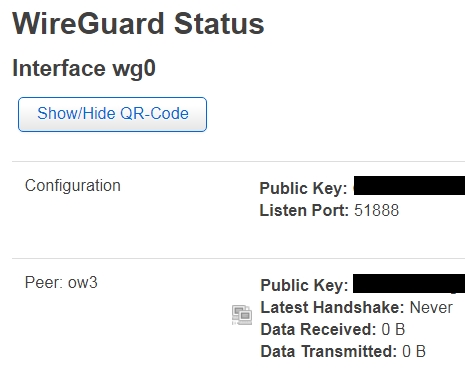
 )
)

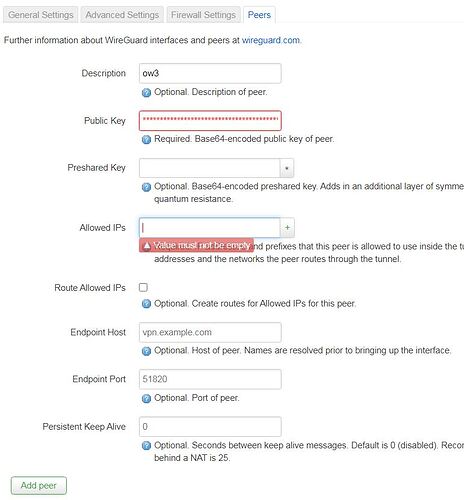
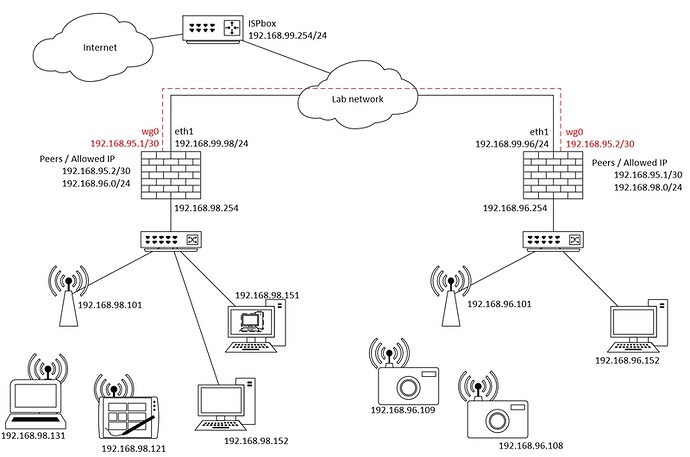
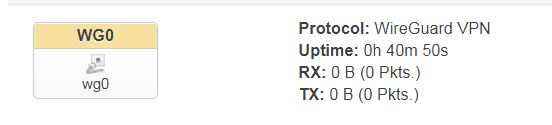
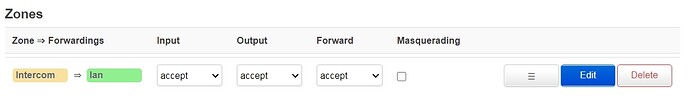
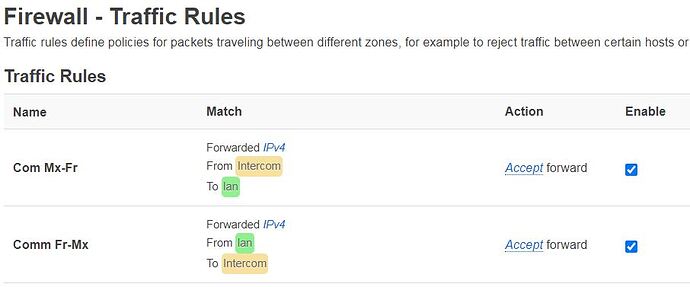
 I must be missing something but as I am discovering this tool, I can't figure what!
I must be missing something but as I am discovering this tool, I can't figure what!