Hi all,
I've OpenWRT 23.05.5 on Netgear GS108T v3
I will use the switch as a lan switch, without wan interface and/or Internet connection.
My goal is to bridge all
but drop udp packets destinated to a particular port (eg. 3000) for the host plugged to a physical port (eg. lan6)
and drop all UDP packets for a host plugged to a physical port (eg. lan7) except for packets destinated to a particular port (eg. 4000).
Particular performance on speed is not required.
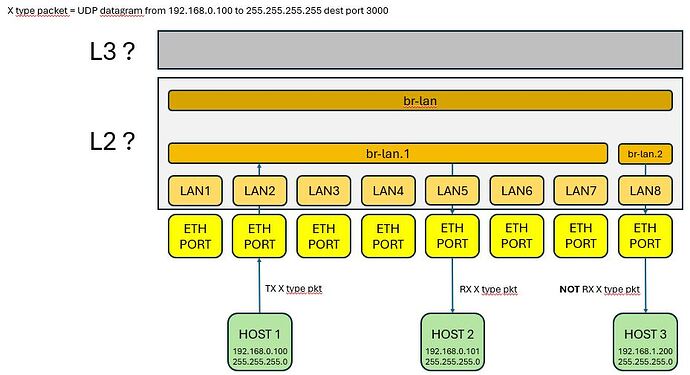
What I've manged up to now (thanks to PSherman and Pavel for help and understanding) is to bridge all ports in a 'br-lan' Bridge device with 'Bridge VLAN filtering', create 3 VLANs devices whose base device is 'br-lan', and create 3 firewall zones to forward packets between zones.
That is working: I can transmit udp packets destinated to port 3000 and all VLANs receive them.
Now it's time to DROP these packets for the VLAN where I dont want to forward them.
And here comes the difficult (and my incompetence...).
What I've understood is that the configuration up to now works at L2, so if I will set a firewall rule between zones (L3) it will be NOT handled. As for PSherman suggestion I have to deal with 'Bridge Firewall': https://openwrt.org/docs/guide-user/firewall/fw3_configurations/bridge?s[]=firewall
I followed the instructions but no success: I've set a nft bridge table, chain and rule to drop packets destinated to port 3000 but them yet comes.
Are there someone who can tell:
- if fw4 can handle Bridge Firewall settings
- And how to gain my goal
Following there are my settings:
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd93:4551:c672::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
list ports 'lan5'
list ports 'lan6'
list ports 'lan7'
list ports 'lan8'
config bridge-vlan
option device 'br-lan'
option vlan '1'
list ports 'lan1:u*'
list ports 'lan2:u*'
list ports 'lan3:u*'
list ports 'lan4:u*'
list ports 'lan5:u*'
list ports 'lan6:u*'
list ports 'lan7:u*'
list ports 'lan8:u*'
config bridge-vlan
option device 'br-lan'
option vlan '2'
config bridge-vlan
option device 'br-lan'
option vlan '3'
config interface 'rhib'
option device 'br-lan.1'
option proto 'static'
option ipaddr '192.168.0.1'
option netmask '255.255.255.0'
config interface 'simpulse'
option device 'br-lan.2'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.0.2'
config interface 'radio'
option device 'br-lan.3'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.0.3'
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'ACCEPT'
config zone
option name 'rhibzone'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'rhib'
option log '1'
config zone
option name 'simpulsezone'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'simpulse'
config zone
option name 'radiozone'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'radio'
config forwarding
option src 'rhibzone'
option dest 'simpulsezone'
config forwarding
option src 'simpulsezone'
option dest 'rhibzone'
config forwarding
option src 'rhibzone'
option dest 'radiozone'
config forwarding
option src 'radiozone'
option dest 'rhibzone'
config include 'bridge'
option path '/etc/nftables.d/bridge.sh'
/etc/nftables.d/bridge.sh
nft add table bridge filter
nft flush table bridge filter
nft add chain bridge filter forward '{type filter hook forward priority -200; }'
nft add rule bridge filter forward iifname "br-lan.1" oifname "br-lan.2" ip daddr 255.255.255.255 udp dport 3000 counter drop
Any help is appreciated!