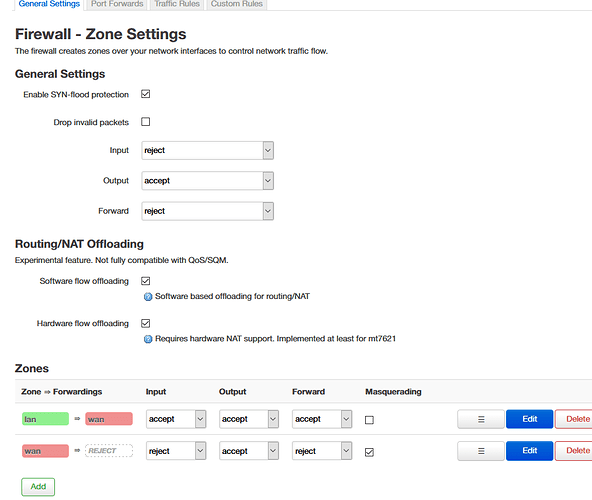
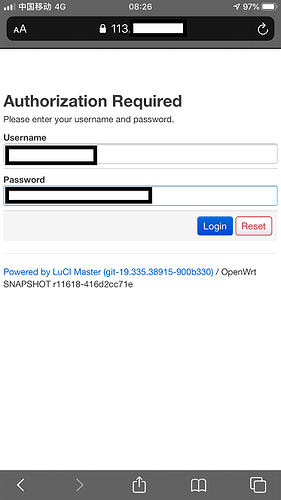
I'm going crazy, i have a public ip address that can be used to access my router LUCI and SSH. In the general firewall settings i've already set Input: reject but still seems like that i can access to my router from my external IP address.
Is there anything i can do to block access from WAN and allow only from LAN?
trendy
December 4, 2019, 2:23pm
2
You'd better not expose the Luci on the WAN.
General firewall settings apply to interfaces not part of a zone.
Please, post your "network" and "firewall" config files here.
Did you test the network access to LuCI and SSH from a machine on LAN (that has an ACCEPT rule); or from another location on the Internet (which should be REJECT)?
Firewall
config defaults
option syn_flood '1'
option output 'ACCEPT'
option flow_offloading '1'
option flow_offloading_hw '1'
option forward 'REJECT'
option input 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config redirect
option dest_port 'x'
option src 'wan'
option name 'Deluge'
option src_dport 'x'
option target 'DNAT'
option dest_ip '192.168.1.x'
option dest 'lan'
option proto 'tcp udp'
config include
option path '/etc/firewall.user'
config redirect
option target 'DNAT'
option name 'Deluged-Web'
option proto 'tcp udp'
option src 'wan'
option src_dport 'x'
option dest 'lan'
option dest_ip '192.168.1.x'
option dest_port 'x
config rule
option name 'Port'
option proto 'tcp udp'
option src 'wan'
option src_port '80'
option dest_port '80'
option target 'REJECT'
config rule
option name 'Port2'
option proto 'tcp udp'
option src 'wan'
option src_port '443'
option dest_port '433'
option target 'REJECT'
Network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix '#'
config interface 'lan'
option type 'bridge'
option ifname 'eth1.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option delegate '0'
list dns '192.168.1.1'
config interface 'wan'
option ifname 'eth0.2'
option proto 'pppoe'
option username 'x'
option ipv6 '0'
list dns '192.168.1.1'
option peerdns '0'
option password 'x'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '5 0t'
config route
option target '8.8.8.8'
option metric '2'
option gateway '192.168.1.1'
option interface 'lan'
config route
option target '8.8.4.4'
option metric '2'
option gateway '192.168.1.1'
option interface 'lan'
I test from an internet device, open firefox insert my external IP and i can access to my router.
1 Like
That's my point, i dont want to expose Luci to my WAN.
should be better...
You may also have to uncheck in ADMIN section the listen to WAN for SSH
trendy
December 4, 2019, 4:18pm
9
m4niacjp:
config rule
config rule
These are useless anyway, as no server (src_port 80 & 443) will contact your Luci directly.
However there doesn't seem to be any port open. Are you sure the firewall is running?iptables-save -c
Option to listen to WAN for SSH not enabled.
trendy:
m4niacjp:
config rule
config rule
These are useless anyway, as no server (src_port 80 & 443) will contact your Luci directly.
However there doesn't seem to be any port open. Are you sure the firewall is running?iptables-save -c
I've typed your command and a huge WOT appeared. If you need it i can post it.
root@OpenWrt:~# iptables-save -c
# Generated by iptables-save v1.8.3 on Wed Dec 4 16:19:06 2019
*nat
:PREROUTING ACCEPT [1800:201878]
:INPUT ACCEPT [1137:78972]
...
...
[212:14282] -A zone_wan_src_REJECT -i pppoe-wan -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_src_REJECT -i eth0.2 -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Wed Dec 4 16:19:06 2019
What else i can do ? I really really don't want my LUCI to be exposed to WAN.
trendy
December 4, 2019, 4:26pm
12
Yes, post it in preformatted text </>
root@OpenWrt:~# iptables-save -c
# Generated by iptables-save v1.8.3 on Wed Dec 4 16:33:06 2019
*nat
:PREROUTING ACCEPT [2205:209529]
:INPUT ACCEPT [1060:74819]
:OUTPUT ACCEPT [5695:345211]
:POSTROUTING ACCEPT [3153:214581]
:clash_tcp - [0:0]
:clash_udp - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[317:20476] -A PREROUTING -p udp -m udp --dport 53 -j clash_udp
[3216:307266] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[2555:230614] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[661:76652] -A PREROUTING -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_prerouting
[0:0] -A PREROUTING -i eth0.2 -m comment --comment "!fw3" -j zone_wan_prerouting
[1812:122821] -A PREROUTING -p tcp -j clash_tcp
[0:0] -A OUTPUT -d 198.18.0.0/16 -p tcp -j REDIRECT --to-ports 7892
[7785:533235] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[1027:88865] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[4631:318550] -A POSTROUTING -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_postrouting
[0:0] -A POSTROUTING -o eth0.2 -m comment --comment "!fw3" -j zone_wan_postrouting
[0:0] -A clash_tcp -d 0.0.0.0/8 -j RETURN
[2:120] -A clash_tcp -d 10.0.0.0/8 -j RETURN
[0:0] -A clash_tcp -d 127.0.0.0/8 -j RETURN
[0:0] -A clash_tcp -d 169.254.0.0/16 -j RETURN
[0:0] -A clash_tcp -d 172.16.0.0/12 -j RETURN
[78:4056] -A clash_tcp -d 192.168.0.0/16 -j RETURN
[0:0] -A clash_tcp -d 224.0.0.0/4 -j RETURN
[56:3360] -A clash_tcp -d 240.0.0.0/4 -j RETURN
[0:0] -A clash_tcp -d 192.168.1.1/32 -j RETURN
[0:0] -A clash_tcp -p tcp -m tcp --dport 22 -j ACCEPT
[1077:70181] -A clash_tcp -p tcp -m set --match-set clash_lan src -j RETURN
[599:45104] -A clash_tcp -p tcp -j REDIRECT --to-ports 7892
[317:20476] -A clash_udp -p udp -j REDIRECT --to-ports 5300
[1027:88865] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[0:0] -A zone_lan_postrouting -s 192.168.1.0/24 -d 192.168.1.166/32 -p tcp -m tcp --dport 6881 -m comment --comment "!fw3: Deluge (reflection)" -j SNAT --to-source 192.168.1.1
[0:0] -A zone_lan_postrouting -s 192.168.1.0/24 -d 192.168.1.166/32 -p udp -m udp --dport 6881 -m comment --comment "!fw3: Deluge (reflection)" -j SNAT --to-source 192.168.1.1
[0:0] -A zone_lan_postrouting -s 192.168.1.0/24 -d 192.168.1.166/32 -p tcp -m tcp --dport 8112 -m comment --comment "!fw3: Deluged-Web (reflection)" -j SNAT --to-source 192.168.1.1
[0:0] -A zone_lan_postrouting -s 192.168.1.0/24 -d 192.168.1.166/32 -p udp -m udp --dport 8112 -m comment --comment "!fw3: Deluged-Web (reflection)" -j SNAT --to-source 192.168.1.1
[2555:230614] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[0:0] -A zone_lan_prerouting -s 192.168.1.0/24 -d 113.80.87.158/32 -p tcp -m tcp --dport 6881 -m comment --comment "!fw3: Deluge (reflection)" -j DNAT --to-destination 192.168.1.166:6881
[0:0] -A zone_lan_prerouting -s 192.168.1.0/24 -d 113.80.87.158/32 -p udp -m udp --dport 6881 -m comment --comment "!fw3: Deluge (reflection)" -j DNAT --to-destination 192.168.1.166:6881
[0:0] -A zone_lan_prerouting -s 192.168.1.0/24 -d 113.80.87.158/32 -p tcp -m tcp --dport 8112 -m comment --comment "!fw3: Deluged-Web (reflection)" -j DNAT --to-destination 192.168.1.166:8112
[0:0] -A zone_lan_prerouting -s 192.168.1.0/24 -d 113.80.87.158/32 -p udp -m udp --dport 8112 -m comment --comment "!fw3: Deluged-Web (reflection)" -j DNAT --to-destination 192.168.1.166:8112
[4631:318550] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[4631:318550] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[661:76652] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
[162:27301] -A zone_wan_prerouting -p tcp -m tcp --dport 6881 -m comment --comment "!fw3: Deluge" -j DNAT --to-destination 192.168.1.166:6881
[219:22624] -A zone_wan_prerouting -p udp -m udp --dport 6881 -m comment --comment "!fw3: Deluge" -j DNAT --to-destination 192.168.1.166:6881
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 8112 -m comment --comment "!fw3: Deluged-Web" -j DNAT --to-destination 192.168.1.166:8112
[0:0] -A zone_wan_prerouting -p udp -m udp --dport 8112 -m comment --comment "!fw3: Deluged-Web" -j DNAT --to-destination 192.168.1.166:8112
COMMIT
# Completed on Wed Dec 4 16:33:06 2019
# Generated by iptables-save v1.8.3 on Wed Dec 4 16:33:06 2019
*mangle
:PREROUTING ACCEPT [60037:41141447]
:INPUT ACCEPT [49542:38068829]
:FORWARD ACCEPT [10200:3011229]
:OUTPUT ACCEPT [51214:36728350]
:POSTROUTING ACCEPT [61024:39710695]
[4792:286488] -A FORWARD -o pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[0:0] -A FORWARD -o eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Wed Dec 4 16:33:06 2019
# Generated by iptables-save v1.8.3 on Wed Dec 4 16:33:06 2019
*filter
:INPUT DROP [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[5362:400213] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[44181:37668656] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[42193:37459390] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[551:29640] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[1434:164924] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
[554:44342] -A INPUT -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_input
[0:0] -A INPUT -i eth0.2 -m comment --comment "!fw3" -j zone_wan_input
[37:1480] -A INPUT -m comment --comment "!fw3" -j reject
[10200:3011229] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[4169:2568393] -A FORWARD -m comment --comment "!fw3: Traffic offloading" -m conntrack --ctstate RELATED,ESTABLISHED -j FLOWOFFLOAD --hw
[4169:2568393] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[5587:385331] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
[444:57505] -A FORWARD -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -i eth0.2 -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[5362:400213] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[45850:36328945] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[41656:36069360] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[691:41120] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
[3503:218465] -A OUTPUT -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_output
[0:0] -A OUTPUT -o eth0.2 -m comment --comment "!fw3" -j zone_wan_output
[308:18923] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[89:4930] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[551:29640] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[710:42716] -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[5587:385331] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[5587:385331] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[19:1596] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[1434:164924] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[748:45333] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[686:119591] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[691:41120] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[691:41120] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[649:118111] -A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[385:28324] -A zone_wan_dest_ACCEPT -o pppoe-wan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[8686:573876] -A zone_wan_dest_ACCEPT -o pppoe-wan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_ACCEPT -o eth0.2 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[0:0] -A zone_wan_dest_ACCEPT -o eth0.2 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o pppoe-wan -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_dest_REJECT -o eth0.2 -m comment --comment "!fw3" -j reject
[444:57505] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[444:57505] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[554:44342] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[0:0] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -p tcp -m tcp --sport 80 --dport 80 -m comment --comment "!fw3: Port" -j reject
[0:0] -A zone_wan_input -p udp -m udp --sport 80 --dport 80 -m comment --comment "!fw3: Port" -j reject
[0:0] -A zone_wan_input -p tcp -m tcp --sport 443 --dport 433 -m comment --comment "!fw3: Port2" -j reject
[0:0] -A zone_wan_input -p udp -m udp --sport 443 --dport 433 -m comment --comment "!fw3: Port2" -j reject
[194:21969] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[360:22373] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[3503:218465] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[3503:218465] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[360:22373] -A zone_wan_src_REJECT -i pppoe-wan -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_src_REJECT -i eth0.2 -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Wed Dec 4 16:33:06 2019
root@OpenWrt:~#
Mushoz
December 4, 2019, 4:47pm
16
Are you absolutely sure that this internet device is NOT connected to your router's LAN? Typing in the public IP is NOT sufficient to see the connection blocked, since the connection will still originate from within the LAN, and hence will be accepted. Use a phone with 4G for example to make sure your device is actually trying to reach the public IP from the WAN side.
3 Likes
trendy
December 4, 2019, 4:56pm
17
Your firewall is not allowing anything.Verify that you are indeed coming from the WAN interface when you test.
2 Likes
What happens if you disable Software and Hardware NAT offloading?
Mushoz:
Are you absolutely sure that this internet device is NOT connected to your router's LAN? Typing in the public IP is NOT sufficient to see the connection blocked, since the connection will still originate from within the LAN, and hence will be accepted. Use a phone with 4G for example to make sure your device is actually trying to reach the public IP from the WAN side.
Yes, i'm using a phone with 4g network (disabled wifi) and i open chrome, type my external ip and like magic i can access my router luci login screen.
I had just try and same thing, i can still access to my router LUCI via WAN. I have no idea what to do, basically i'm open to WAN and can get pwned any time and firewall seems useless.
For the moment i made my router password extremely long and SSH only available via privatekey (no password), is there any way to lockout after few wrong attempts?
Broken firewall is pretty bad man. Might want to try resetting to factory and checking if it works after that. or perhaps reinstall a different openwrt image.
worst case you can't find a functioning firewall you could just edit "/etc/config/uhttpd" and set the Luci GUI server to your routers LAN ip like "192.168.1.1:80" instead of the default "0.0.0.0:80"
GG
I've just did what you mentioned....STILL can access my router from WAN.
# Server configuration
config uhttpd main
# HTTP listen addresses, multiple allowed
list listen_http 192.168.1.1:80
#list listen_http [::]:80
# HTTPS listen addresses, multiple allowed
list listen_https 192.168.1.1:443
#list listen_https [::]:443
root@OpenWrt:~# service uhttpd restart
root@OpenWrt:~#