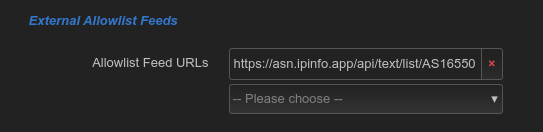
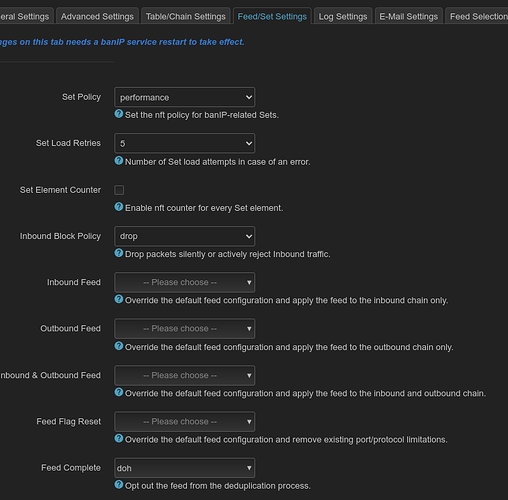
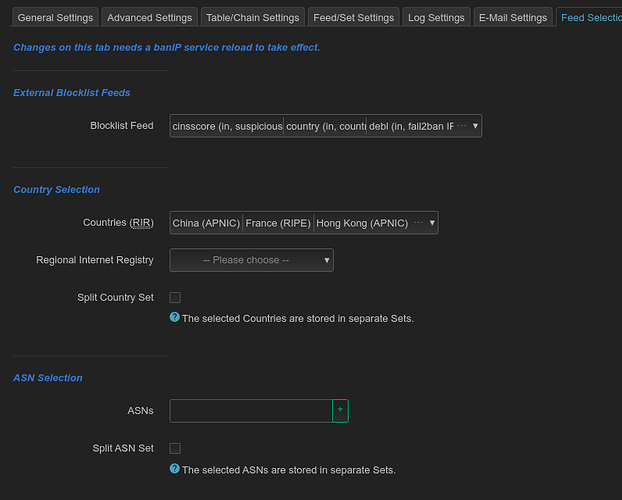
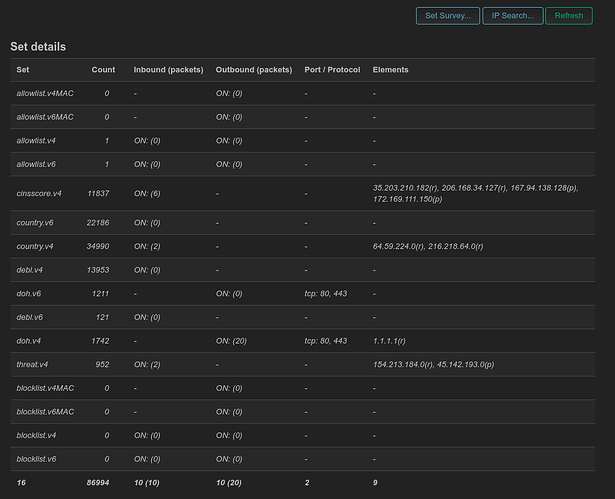
Hello everyone and Happy New Year!
I just installed BanIP, and I get "download utility with SSL support not found, please set 'ban_fetchcmd' manually" error.
May someone help me? Someone here got similar issue but not same error message.
Sorry for my ultra noob skills, I started to play with OpenWRT very recently.
This is detailed clearly in the 'Readme' under the "Prerequisites" section, second line. You need to install support such as curl / wget package. Then reboot.
https://github.com/openwrt/packages/blob/master/net/banip/files/README.md
Thank you very much! Ok I read it, I have no idea what that means ![]() but will find out!
but will find out!
Hi, does anyone have any ideas why this behavior happens? It seems strange to me ![]()
Ref: banIP support thread - #2269 by kmau
@didbot, any way to whitelist a particular AS number in allowlist along with CIDR/FQDN exceptions?
Basically this would allow blacklisting entire country except networks belonging to a specific AS number.
Tue Jan 14 12:14:34 2025 kern.warn kernel: [7848364.900007] banIP/pre-ct/drop: IN=eth1 OUT= MAC=64:62:66:22:01:b0:00:21:59:04:57:c9:08:00 SRC=17.248.199.68 DST=111.222.333.444 LEN=115 TOS=0x00 PREC=0x00 TTL=56 ID=57496 DF PROTO=TCP SPT=443 DPT=59694 WINDOW=63 RES=0x00 ACK PSH FIN URGP=0
Tue Jan 14 12:14:36 2025 kern.warn kernel: [7848366.628196] banIP/pre-ct/drop: IN=eth1 OUT= MAC=64:62:66:22:01:b0:00:21:59:04:57:c9:08:00 SRC=17.248.199.68 DST=111.222.333.444 LEN=115 TOS=0x00 PREC=0x00 TTL=56 ID=57497 DF PROTO=TCP SPT=443 DPT=59694 WINDOW=63 RES=0x00 ACK PSH FIN URGP=0
Am I doing something wrong?
are the packets being forged?
17/8 is Apple..
I've enabled logging and have tons of these lines from IPs owned by Amazon, Google, Microsoft..
::: banIP runtime information
+ status : active (nft: ✔, monitor: ✔)
+ version : 1.0.1-2
+ element_count : 45566
+ active_feeds : allowlistv4MAC, allowlistv6MAC, allowlistv4, allowlistv6, cinsscorev4, deblv4, countryv4, dshieldv4, dropv4, etcompromisedv4, threatv4, torv4, turrisv4, blocklistv4MAC, blocklistv6MAC, blocklistv4, blocklistv6
+ active_devices : wan: eth1 / wan-if: wan, - / vlan-allow: - / vlan-block: -
+ active_uplink : 111.222.333.444/29
+ nft_info : priority: -100, policy: memory, loglevel: warn, expiry: -, limit (icmp/syn/udp): 250/250/250
+ run_info : base: /tmp, backup: /tmp/banIP-backup, report: /tmp/banIP-report
+ run_flags : auto: ✔, proto (4/6): ✔/✘, log (pre/inp/fwd/lan): ✔/✘/✔/✘, dedup: ✔, split: ✘, custom feed: ✔, allowed only: ✘
+ last_run : mode: reload, period: 1m 37s, memory: 15519 MB available, 1736 KB max. used, cores: 4, log: logread, fetch: uclient-fetch
+ system_info : 2025-01-14 12:14:05, Protectli VP2420, x86/64, OpenWrt 23.05.5 r24106-10cc5fcd00
Thank you in advance..
Tue Jan 14 12:24:39 2025 kern.warn kernel: [7848969.680907] banIP/pre-ct/drop: IN=eth1 OUT= MAC=64:62:66:22:01:b0:00:21:59:04:57:c9:08:00 SRC=17.137.162.3 DST=111.222.333.444 LEN=83 TOS=0x00 PREC=0x00 TTL=46 ID=7561 DF PROTO=TCP SPT=443 DPT=60196 WINDOW=18 RES=0x00 ACK PSH FIN URGP=0
Why is apple sending ack psh fin and urgp
Tue Jan 14 12:29:45 2025 kern.warn kernel: [7849276.234252] banIP/pre-ct/drop: IN=eth1 OUT= MAC=64:62:66:22:01:b0:00:21:59:04:57:c9:08:00 SRC=34.159.123.222 DST=111.222.333.444 LEN=40 TOS=0x00 PREC=0x60 TTL=250 ID=2653 PROTO=TCP SPT=45432 DPT=445 WINDOW=1200 RES=0x00 RST URGP=0
Also don't think Google is trying to use smb..
I just didn't see these things in banip thread..
Thank you in advance..
eth1 is my wan link..
sysctl -a | grep rp_filter shows everything is 0..
sysctl -w net.ipv4.conf.eth1.rp_filter=1
seems to have drastically calmed the logs down..
What did you do when the logging started?
Is the MAC new to the network?
Where do the values come from:
There are different IP's:
...
The src ips are Apple, Apple, and Google (34.128/10)
The logs have been going for several weeks now.. (and shouldn't have been) when I noticed them I started looking up the IPs as if something were happening.. (then noticed the 17.x) and couldn't possibly think that Apple was interested in this device..
then looking at the flags.. ack psh fin and urg (want to very quickly close the session?)
just confused as to why..
then thought they were forged.. and the rp_filter
These are also google (safe search)
Tue Jan 14 13:10:03 2025 kern.warn kernel: [7851694.527852] banIP/pre-ct/drop: IN=eth1 OUT= MAC=64:62:66:22:01:b0:00:21:59:04:57:c9:08:00 SRC=216.239.38.120 DST=111.222.333.444 LEN=125 TOS=0x00 PREC=0x80 TTL=122 ID=32835 PROTO=TCP SPT=443 DPT=23274 WINDOW=1033 RES=0x00 ACK PSH URGP=0
Tue Jan 14 13:10:10 2025 kern.warn kernel: [7851701.376374] banIP/pre-ct/drop: IN=eth1 OUT= MAC=64:62:66:22:01:b0:00:21:59:04:57:c9:08:00 SRC=216.239.38.120 DST=111.222.333.444 LEN=125 TOS=0x00 PREC=0x80 TTL=122 ID=32836 PROTO=TCP SPT=443 DPT=23274 WINDOW=1033 RES=0x00 ACK PSH URGP=0
(really want to get that ack through?)
If the last of the data was sent, combining flags in the last packet is an efficient way to ack and terminate the connection.
A brief note on a major banIP update in master branch:
Before testing it may be a good idea to start with a fresh config (cause many options has been changed), although an existing config should not hurt.
Screenshots with new options/features:
New Set settings:
New feed settings:
New Set reporting:
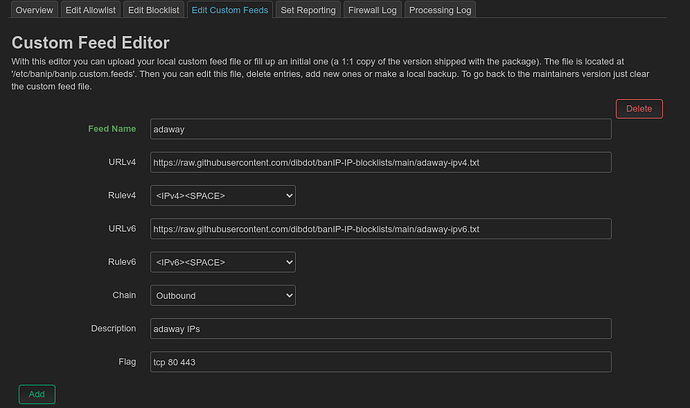
New custom feed editor:
If you have any questions feel free to ask! ![]()
Do we need to update Luci?
yep, absolutely.
@dibdot
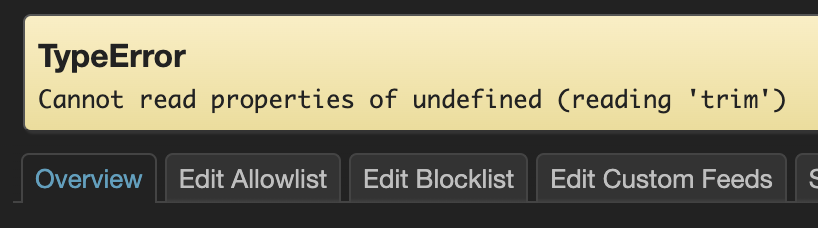
Just upgraded to your newest test version 1.5.0-1 and now I get this error in luci on the "overview" tab only; other tabs seem ok:
I've double checked my config file and I don't see any problems there. Any ideas?
Did you use a custom feeds file from a former release? If so, clear this custom feeds file.
Somehow I did have an old placeholder file in /etc/banip that was 0 bytes in size:
-rw------- 1 root root 0 Jun 22 2024 banip.custom.feeds
However, removing this empty file did not fix the (reading 'trim') TypeError displayed in luci. ![]()
Edit: I will also add that banip itself is running fine, I can execute service commands for status, report, etc and they all seem OK. So this appears to be some kind of luci rendering error only.
No, please don't delete this file! Please re-create this 0-byte file, e.g. : > /etc/banip/banip.custom.feeds
Please post the content of /etc/banip/banip.feeds.
Ok, I've recreated the /etc/banip/banip.custom.feeds file w/ 0600 perms. Here's the current content of my /etc/banip/banip.feeds file:
{
"adaway":{
"url_4": "https://raw.githubusercontent.com/dibdot/banIP-IP-blocklists/main/adaway-ipv4.txt",
"url_6": "https://raw.githubusercontent.com/dibdot/banIP-IP-blocklists/main/adaway-ipv6.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"rule_6": "/^(([0-9A-f]{0,4}:){1,7}[0-9A-f]{0,4}:?(\\/(1?[0-2][0-8]|[0-9][0-9]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"descr": "adaway IPs",
"flag": "tcp 80 443"
},
"adguard":{
"url_4": "https://raw.githubusercontent.com/dibdot/banIP-IP-blocklists/main/adguard-ipv4.txt",
"url_6": "https://raw.githubusercontent.com/dibdot/banIP-IP-blocklists/main/adguard-ipv6.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"rule_6": "/^(([0-9A-f]{0,4}:){1,7}[0-9A-f]{0,4}:?(\\/(1?[0-2][0-8]|[0-9][0-9]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"descr": "adguard IPs",
"flag": "tcp 80 443"
},
"adguardtrackers":{
"url_4": "https://raw.githubusercontent.com/dibdot/banIP-IP-blocklists/main/adguardtrackers-ipv4.txt",
"url_6": "https://raw.githubusercontent.com/dibdot/banIP-IP-blocklists/main/adguardtrackers-ipv6.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"rule_6": "/^(([0-9A-f]{0,4}:){1,7}[0-9A-f]{0,4}:?(\\/(1?[0-2][0-8]|[0-9][0-9]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"descr": "adguardtracker IPs",
"flag": "tcp 80 443"
},
"antipopads":{
"url_4": "https://raw.githubusercontent.com/dibdot/banIP-IP-blocklists/main/antipopads-ipv4.txt",
"url_6": "https://raw.githubusercontent.com/dibdot/banIP-IP-blocklists/main/antipopads-ipv6.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"rule_6": "/^(([0-9A-f]{0,4}:){1,7}[0-9A-f]{0,4}:?(\\/(1?[0-2][0-8]|[0-9][0-9]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"descr": "antipopads IPs",
"flag": "tcp 80 443"
},
"asn":{
"url_4": "https://asn.ipinfo.app/api/text/list/",
"url_6": "https://asn.ipinfo.app/api/text/list/",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"rule_6": "/^(([0-9A-f]{0,4}:){1,7}[0-9A-f]{0,4}:?(\\/(1?[0-2][0-8]|[0-9][0-9]))?)$/{printf \"%s,\\n\",$1}",
"descr": "ASN IP segments"
},
"backscatterer":{
"url_4": "http://wget-mirrors.uceprotect.net/rbldnsd-all/ips.backscatterer.org.gz",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "backscatterer IPs",
"flag": "gz"
},
"becyber":{
"url_4": "https://raw.githubusercontent.com/duggytuxy/malicious_ip_addresses/main/botnets_zombies_scanner_spam_ips.txt",
"url_6": "https://raw.githubusercontent.com/duggytuxy/malicious_ip_addresses/main/botnets_zombies_scanner_spam_ips_ipv6.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"rule_6": "/^(([0-9A-f]{0,4}:){1,7}[0-9A-f]{0,4}:?(\\/(1?[0-2][0-8]|[0-9][0-9]))?)$/{printf \"%s,\\n\",$1}",
"descr": "malicious attacker IPs"
},
"binarydefense":{
"url_4": "https://iplists.firehol.org/files/bds_atif.ipset",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "binary defense banlist"
},
"bogon":{
"url_4": "https://www.team-cymru.org/Services/Bogons/fullbogons-ipv4.txt",
"url_6": "https://www.team-cymru.org/Services/Bogons/fullbogons-ipv6.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"rule_6": "/^(([0-9A-f]{0,4}:){1,7}[0-9A-f]{0,4}:?(\\/(1?[0-2][0-8]|[0-9][0-9]))?)$/{printf \"%s,\\n\",$1}",
"descr": "bogon prefixes"
},
"bruteforceblock":{
"url_4": "https://danger.rulez.sk/projects/bruteforceblocker/blist.php",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"descr": "bruteforceblocker IPs"
},
"cinsscore":{
"url_4": "https://cinsscore.com/list/ci-badguys.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "suspicious attacker IPs"
},
"country":{
"url_4": "https://www.ipdeny.com/ipblocks/data/aggregated/",
"url_6": "https://www.ipdeny.com/ipv6/ipaddresses/aggregated/",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"rule_6": "/^(([0-9A-f]{0,4}:){1,7}[0-9A-f]{0,4}:?(\\/(1?[0-2][0-8]|[0-9][0-9]))?)$/{printf \"%s,\\n\",$1}",
"descr": "country blocks"
},
"debl":{
"url_4": "https://lists.blocklist.de/lists/all.txt",
"url_6": "https://lists.blocklist.de/lists/all.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"rule_6": "/^(([0-9A-f]{0,4}:){1,7}[0-9A-f]{0,4}:?(\\/(1?[0-2][0-8]|[0-9][0-9]))?)$/{printf \"%s,\\n\",$1}",
"descr": "fail2ban IP blocklist"
},
"doh":{
"url_4": "https://raw.githubusercontent.com/dibdot/DoH-IP-blocklists/master/doh-ipv4.txt",
"url_6": "https://raw.githubusercontent.com/dibdot/DoH-IP-blocklists/master/doh-ipv6.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"rule_6": "/^(([0-9A-f]{0,4}:){1,7}[0-9A-f]{0,4}:?(\\/(1?[0-2][0-8]|[0-9][0-9]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"descr": "public DoH-Provider",
"flag": "tcp 80 443"
},
"drop":{
"url_4": "https://www.spamhaus.org/drop/drop.txt",
"url_6": "https://www.spamhaus.org/drop/dropv6.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"rule_6": "/^(([0-9A-f]{0,4}:){1,7}[0-9A-f]{0,4}:?(\\/(1?[0-2][0-8]|[0-9][0-9]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"descr": "spamhaus drop compilation"
},
"dshield":{
"url_4": "https://feeds.dshield.org/block.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)[[:space:]]/{printf \"%s/%s,\\n\",$1,$3}",
"descr": "dshield IP blocklist"
},
"etcompromised":{
"url_4": "https://iplists.firehol.org/files/et_compromised.ipset",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "ET compromised hosts"
},
"feodo":{
"url_4": "https://feodotracker.abuse.ch/downloads/ipblocklist.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "feodo tracker"
},
"firehol1":{
"url_4": "https://iplists.firehol.org/files/firehol_level1.netset",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "firehol level 1 compilation"
},
"firehol2":{
"url_4": "https://iplists.firehol.org/files/firehol_level2.netset",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "firehol level 2 compilation"
},
"firehol3":{
"url_4": "https://iplists.firehol.org/files/firehol_level3.netset",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "firehol level 3 compilation"
},
"firehol4":{
"url_4": "https://iplists.firehol.org/files/firehol_level4.netset",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{if(!seen[$1]++)printf \"%s,\\n\",$1}",
"descr": "firehol level 4 compilation"
},
"greensnow":{
"url_4": "https://blocklist.greensnow.co/greensnow.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "suspicious server IPs"
},
"iblockads":{
"url_4": "https://list.iblocklist.com/?list=dgxtneitpuvgqqcpfulq&fileformat=cidr&archiveformat=gz",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "advertising IPs",
"flag": "gz tcp 80 443"
},
"iblockspy":{
"url_4": "https://list.iblocklist.com/?list=llvtlsjyoyiczbkjsxpf&fileformat=cidr&archiveformat=gz",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "malicious spyware IPs",
"flag": "gz tcp 80 443"
},
"ipblackhole":{
"url_4": "https://blackhole.s-e-r-v-e-r.pw/blackhole-today",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "blackhole IP blocklist"
},
"ipsum":{
"url_4": "https://raw.githubusercontent.com/stamparm/ipsum/master/levels/3.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)[-[:space:]]?/{printf \"%s,\\n\",$1}",
"descr": "malicious IPs"
},
"ipthreat":{
"url_4": "https://lists.ipthreat.net/file/ipthreat-lists/threat/threat-30.txt.gz",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)[-[:space:]]?/{printf \"%s,\\n\",$1}",
"descr": "hacker and botnet IPs",
"flag": "gz"
},
"myip":{
"url_4": "https://myip.ms/files/blacklist/general/latest_blacklist.txt",
"url_6": "https://myip.ms/files/blacklist/general/latest_blacklist.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"rule_6": "/^(([0-9A-f]{0,4}:){1,7}[0-9A-f]{0,4}:?(\\/(1?[0-2][0-8]|[0-9][0-9]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"descr": "real-time IP blocklist"
},
"nixspam":{
"url_4": "https://www.nixspam.net/download/nixspam-ip.dump.gz",
"rule_4": "/127\\./{next}/(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)[[:space:]]/{printf \"%s,\\n\",$2}",
"descr": "iX spam protection",
"flag": "gz"
},
"oisdbig":{
"url_4": "https://raw.githubusercontent.com/dibdot/banIP-IP-blocklists/main/oisdbig-ipv4.txt",
"url_6": "https://raw.githubusercontent.com/dibdot/banIP-IP-blocklists/main/oisdbig-ipv6.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"rule_6": "/^(([0-9A-f]{0,4}:){1,7}[0-9A-f]{0,4}:?(\\/(1?[0-2][0-8]|[0-9][0-9]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"descr": "OISD-big IPs",
"flag": "tcp 80 443"
},
"oisdnsfw":{
"url_4": "https://raw.githubusercontent.com/dibdot/banIP-IP-blocklists/main/oisdnsfw-ipv4.txt",
"url_6": "https://raw.githubusercontent.com/dibdot/banIP-IP-blocklists/main/oisdnsfw-ipv6.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"rule_6": "/^(([0-9A-f]{0,4}:){1,7}[0-9A-f]{0,4}:?(\\/(1?[0-2][0-8]|[0-9][0-9]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"descr": "OISD-nsfw IPs",
"flag": "tcp 80 443"
},
"oisdsmall":{
"url_4": "https://raw.githubusercontent.com/dibdot/banIP-IP-blocklists/main/oisdsmall-ipv4.txt",
"url_6": "https://raw.githubusercontent.com/dibdot/banIP-IP-blocklists/main/oisdsmall-ipv6.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"rule_6": "/^(([0-9A-f]{0,4}:){1,7}[0-9A-f]{0,4}:?(\\/(1?[0-2][0-8]|[0-9][0-9]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"descr": "OISD-small IPs",
"flag": "tcp 80 443"
},
"pallebone":{
"url_4": "https://raw.githubusercontent.com/pallebone/StrictBlockPAllebone/master/BlockIP.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "curated IP blocklist"
},
"proxy":{
"url_4": "https://iplists.firehol.org/files/proxylists.ipset",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "open proxies"
},
"sslbl":{
"url_4": "https://sslbl.abuse.ch/blacklist/sslipblacklist.csv",
"rule_4": "BEGIN{FS=\",\"}/127\\./{next}/(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)/{printf \"%s,\\n\",$2}",
"descr": "SSL botnet IPs"
},
"stevenblack":{
"url_4": "https://raw.githubusercontent.com/dibdot/banIP-IP-blocklists/main/stevenblack-ipv4.txt",
"url_6": "https://raw.githubusercontent.com/dibdot/banIP-IP-blocklists/main/stevenblack-ipv6.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"rule_6": "/^(([0-9A-f]{0,4}:){1,7}[0-9A-f]{0,4}:?(\\/(1?[0-2][0-8]|[0-9][0-9]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"descr": "stevenblack IPs",
"flag": "tcp 80 443"
},
"talos":{
"url_4": "https://www.talosintelligence.com/documents/ip-blacklist",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "talos IPs"
},
"threat":{
"url_4": "https://rules.emergingthreats.net/fwrules/emerging-Block-IPs.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "emerging threats"
},
"threatview":{
"url_4": "https://threatview.io/Downloads/IP-High-Confidence-Feed.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "malicious IPs"
},
"tor":{
"url_4": "https://www.dan.me.uk/torlist/?exit",
"url_6": "https://www.dan.me.uk/torlist/?exit",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"rule_6": "/^(([0-9A-f]{0,4}:){1,7}[0-9A-f]{0,4}:?(\\/(1?[0-2][0-8]|[0-9][0-9]))?)$/{printf \"%s,\\n\",$1}",
"descr": "tor exit nodes"
},
"turris":{
"url_4":"https://view.sentinel.turris.cz/greylist-data/greylist-latest.csv",
"rule_4":"BEGIN{FS=\",\"}/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)/{printf \"%s,\\n\",$1}",
"descr":"turris sentinel blocklist"
},
"uceprotect1":{
"url_4": "http://wget-mirrors.uceprotect.net/rbldnsd-all/dnsbl-1.uceprotect.net.gz",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "spam protection level 1",
"flag": "gz"
},
"uceprotect2":{
"url_4": "http://wget-mirrors.uceprotect.net/rbldnsd-all/dnsbl-2.uceprotect.net.gz",
"rule_4": "BEGIN{IGNORECASE=1}/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)([[:space:]]NET)/{printf \"%s,\\n\",$1}",
"descr": "spam protection level 2",
"flag": "gz"
},
"uceprotect3":{
"url_4": "http://wget-mirrors.uceprotect.net/rbldnsd-all/dnsbl-3.uceprotect.net.gz",
"rule_4": "BEGIN{IGNORECASE=1}/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)([[:space:]]YOUR)/{printf \"%s,\\n\",$1}",
"descr": "spam protection level 3",
"flag": "gz"
},
"urlhaus":{
"url_4": "https://urlhaus.abuse.ch/downloads/ids/",
"rule_4": "BEGIN{FS=\";\"}/content:\"127\\./{next}/(content:\"([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5]))/{printf \"%s,\\n\",substr($10,11,length($10)-11)}",
"descr": "urlhaus IDS IPs"
},
"urlvir":{
"url_4": "https://iplists.firehol.org/files/urlvir.ipset",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "malware related IPs"
},
"voip":{
"url_4": "https://voipbl.org/update/",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "VoIP fraud blocklist"
},
"webclient":{
"url_4": "https://iplists.firehol.org/files/firehol_webclient.netset",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr": "malware related IPs"
},
"yoyo":{
"url_4": "https://raw.githubusercontent.com/dibdot/banIP-IP-blocklists/main/yoyo-ipv4.txt",
"url_6": "https://raw.githubusercontent.com/dibdot/banIP-IP-blocklists/main/yoyo-ipv6.txt",
"rule_4": "/^127\\./{next}/^(([1-9][0-9]{0,2}\\.){1}([0-9]{1,3}\\.){2}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"rule_6": "/^(([0-9A-f]{0,4}:){1,7}[0-9A-f]{0,4}:?(\\/(1?[0-2][0-8]|[0-9][0-9]))?)[[:space:]]/{printf \"%s,\\n\",$1}",
"descr": "yoyo IPs",
"flag": "tcp 80 443"
}
}