filippz
February 4, 2024, 11:14am
351
When I try setting it to 36 and applied it the Luci reported 36 (6.130 GHz).
I'm running 2 SSIDs on 2,4 GHz, and 2 SSIDs on 5GHz (one of those being mesh). I was lazy and adapted the config from C2600 so I haven't observed any issues by adding SSIDs from Luci - I tried it just now and it went OK.
Since you are using mesh it might be the same issue as mine. Maybe your nodes become "isolated" and your clients connected to them stop working the same as mine? In any case iw scan could help reproduce the behavior (you can just try the "Luci" way with the same result). If I'm reading the log correctly, SAE errors appear after the the DFS scan has already been done.
This is what I got out of logread -f when I am having channel issues @160 . hostapd: could not get valid channel
20:38:28 2024 daemon.notice hostapd: phy1-ap0: interface state UNINITIALIZED->COUNTRY_UPDATE
20:38:29 2024 daemon.notice hostapd: phy1-ap0: interface state COUNTRY_UPDATE->HT_SCAN
20:38:29 2024 daemon.err hostapd: could not get valid channel
20:38:29 2024 daemon.notice hostapd: phy1-ap0: interface state HT_SCAN->DFS
With the mesh off, changing to 160mhz ch 36:
20:46:04 2024 daemon.notice hostapd: phy1-ap0: interface state UNINITIALIZED->COUNTRY_UPDATE
20:46:04 2024 daemon.notice hostapd: phy1-ap0: interface state COUNTRY_UPDATE->HT_SCAN
20:46:05 2024 daemon.notice netifd: Wireless device 'radio1' is now up
20:46:05 2024 daemon.notice hostapd: Switch own primary and secondary channel to get secondary channel with no Beacons from other BSSes
20:46:05 2024 daemon.notice hostapd: phy1-ap0: interface state HT_SCAN->DFS
20:46:05 2024 daemon.notice hostapd: phy1-ap0: DFS-CAC-START freq=5200 chan=40 sec_chan=-1, width=2, seg0=50, seg1=0, cac_time=60s
Something is off in the tangled mess of 160mhz, DFS, country codes, and channel selection.
For note, HR has a different reg setting in 5g (extra power and no outdoor restriction) to the rest of EU so have jumped between that a few times to see if there are changes.
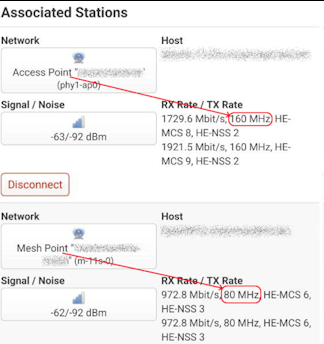
I didn't get to try to kick anything off with iw scan but feel lucky to have 80mhz back on ch100. 160mhz seems to work on ch36 without a mesh ap.
filippz
February 6, 2024, 6:16am
353
Yes - something is definitely off when combining mesh, channels and friends. I'm by no means expert but I can't imagine that this would specific to AX4200. For me using ch 100 is not an issue, but still I'd like to know whats going on...
My main concern is the intermittent stopping of the traffic over mesh which (assuming it's the same issue) can also be triggered by doing an ip scan and I'm out of ideas how to debug this further as tcpdump is showing ARP packets from one side of the mesh coming to the other and the reply from other side not being received by the originating side.
I just want to find out, if I roll back from OpenWRT to AsusWRT with the firmware restore tool does that also delete/remove any partitions that OpenWRT created? Or is there still things left behind.
I think I briefly had the 160mhz ap + 80mhz mesh on ch 36 earlier.
Since there appears to be a max 2 APs, order probably matters for a scan. Disable your 5ghz AP and try the scan, if the mesh stays connected you're hitting that limit by trying to scan for other APs.
When my setup goes sideways, the mesh jumps to channel 149 and my power is limited to 13db
opened 07:04AM - 10 May 22 UTC
target/ipq806x
release/21.02
After DFS radar detection my 5Ghz wifi does not come back online. In the logs it… looks like this. I have to restart wifi to get it working again. Will work around this with a short script but it would be much better if wifi comes back by its own.
Device: Netgear R7800
Firmware: OpenWrt 21.02.2 r16495-bf0c965af0
Wifi Driver: ath10k-firmware-qca9984-ct-full-htt
hostapd-common | 2020-06-08-5a8b3662-40


[openwrt.log](https://github.com/openwrt/openwrt/files/8658999/openwrt.log)
Hi,
I have an issue with VHT160 and DFS as if there is an radar event 5Ghz breaks complete and forever. It seems that it is not implemented (or faulty) in hostapd to revive the connection of the radar is gone. I also do not like to use 36 as fallback Openwrt will stay on that channel forever and it has less power.
Does anybody know if this is known and perhaps somebody working on it? The Issue and discussion is from last year and I am sure somebody else should run into this. Should be fixed wi…
I haven't seen DFS detected in the logs yet but haven't been looking. This comes up looking for the valid channel with some interesting ways to test the fallback channels for later. The only valid 160mhz non DFS range is in the 6ghz space, which might explain how it gets to 149. Half of ch36@160 needs DFS so it might get skiped.
option channel 'auto'
option channels '100 36'
I don't see a way to drop to 80mhz on DFS detection. It also shouldn't kill the whole range, just that freq.
I did not test this rollback option, since this utility refused to work on my system.facinstall, since in this case I can say for sure that all volumes created for OpenWRT will be deleted.
I did follow this facinstall method. When the router rebooted I could ping it, but the login page did not want to open. There was only a Luci weblink but nothing else like the prompt to enter username / password. So I did a Emergency restore with the Asus tool and that worked 100%. But now I am not sure what garbage is left behind on the device.
Command for checking: ubinfo /dev/ubi0 -a
Thank you, will paste the output here. Can I run this command on normal Asus WRT firmware? SSH
Hi there. Herewith the output
Volumes count: 6
Volume ID: 5 (on ubi0)
filippz
February 7, 2024, 5:55am
364
I already have only mesh active on 5GHz for my secondary - scan still breaks it.
I haven't noticed that (at least after after a scan) - I'll keep my eye on it but we might actually experiencing different issues after all.
I think we have different problems too, 160mhz width detects a radar and all it changes immediately. The phy1-mesh0 doesn't seem to wait for another dfs, jumps to 149 while the phy-ap0 tries to scan on ch36 (160mhz requirement. I'm pretty sure there's a race or problem in the channel switch logic. The 6ghz channels would be a natural fit for 160mhz but this router can't use them so there's a bug there.
daemon.notice hostapd: phy1-ap0: interface state COUNTRY_UPDATE->DFS
daemon.notice hostapd: phy1-ap0: DFS-CAC-START freq=5500 chan=100 sec_chan=1, width=2, seg0=114, seg1=0, cac_time=60s
daemon.notice hostapd: phy1-ap0: DFS-CAC-COMPLETED success=0 freq=5500 ht_enabled=0 chan_offset=0 chan_width=5 cf1=5570 cf2=0
daemon.notice hostapd: phy1-ap0: DFS-RADAR-DETECTED freq=5500 ht_enabled=0 chan_offset=0 chan_width=5 cf1=5570 cf2=0
daemon.notice wpa_supplicant[1628]: phy1-mesh0: DFS-RADAR-DETECTED freq=5500 ht_enabled=0 chan_offset=0 chan_width=5 cf1=5570 cf2=0
daemon.notice wpa_supplicant[1628]: phy1-mesh0: DFS-NEW-CHANNEL freq=5745 chan=149 sec_chan=1
daemon.notice hostapd: phy1-ap0: DFS-NEW-CHANNEL freq=5180 chan=36 sec_chan=1
daemon.notice hostapd: phy1-ap0: interface state DFS->DFS
daemon.notice hostapd: phy1-ap0: DFS-CAC-START freq=5180 chan=36 sec_chan=1, width=2, seg0=50, seg1=0, cac_time=60s
daemon.err hostapd: DFS start_dfs_cac() failed, -1
daemon.notice hostapd: phy1-ap0: interface state DFS->DISABLED
ch149 is expected to be 13db and 80MHz (5725 - 5875 @ 80), (N/A, 13), (N/A)
I think some of my mania is related to the DFS channels being blocked for 30 minutes after I hit something on freq 5570 width 5. I'll try to scan with another AP on the 100 and 116 channel range to see if I really have a radar hit.
Ok, my 160mhz problem is definitely radar. I tested this with another AP on the 116 channel and it dropped out as quick as the ax4200. It also exhibited the same attempt to jump to a 6ghz channel so I think that's a bug in hostapd.
daemon.notice hostapd: phy1-ap0: DFS-RADAR-DETECTED freq=5580 ht_enabled=0 chan_offset=0 chan_width=3 cf1=5610 cf2=0
I haven't had the general wifi failure for while now but am a bit better equipped to track it in logs now.
I have used your method @remittor and that workerd.
However i flashed the upgrade that is on the openwrt page for the AX4200, and my lan internet was gone, router still had connection as i could install packages and ping.
Is there something obvious that i missed?
Flashed your file again and it works.
Thanks in advance!
Just in time for the wifi crash!
kern.alert kernel: [345509.078843] Unable to handle kernel write to read-only memory at virtual address 0000000000000000
kern.alert kernel: [345509.087807] Mem abort info:
kern.alert kernel: [345509.090673] ESR = 0x0000000096000045
kern.alert kernel: [345509.094497] EC = 0x25: DABT (current EL), IL = 32 bits
kern.alert kernel: [345509.099895] SET = 0, FnV = 0
kern.alert kernel: [345509.103025] EA = 0, S1PTW = 0
kern.alert kernel: [345509.106239] FSC = 0x05: level 1 translation fault
kern.alert kernel: [345509.111196] Data abort info:
kern.alert kernel: [345509.114154] ISV = 0, ISS = 0x00000045
kern.alert kernel: [345509.118072] CM = 0, WnR = 1
kern.alert kernel: [345509.121117] user pgtable: 4k pages, 39-bit VAs, pgdp=000000004672e000
kern.alert kernel: [345509.127637] [0000000000000000] pgd=0000000000000000, p4d=0000000000000000, pud=0000000000000000
1 Like
r24688-8b706d9297 Busybox was 23.12 so roughly then.
opened 07:25PM - 24 Nov 23 UTC
closed 02:07PM - 16 Jan 24 UTC
I've encountered consistent kernel crashes on both Linksys E8450 and Xiaomi Redm… i Router AX6S, both mt7622, running OpenWrt Master ae500e62e2. It happens on 23.05 as well, although I have not saved any logs for them, or even know if it crashed in the same place. I haven't been able to establish any means to promptly cause the crash, or any action that I can correlate with crashes, but idle routers don't appear to crash.
```
Unable to handle kernel write to read-only memory at virtual address 0000000000000000
CPU: 1 PID: 396 Comm: napi/mtk_eth-4 Tainted: G S 5.15.137 #0
pc : mt76_tx+0xb8/0x634 [mt76]
```
<details><summary>Xiaomi Redmi AX6S Crashlog</summary>
<p>
```
<1>[385471.808583] Unable to handle kernel write to read-only memory at virtual address 0000000000000000
<1>[385471.817576] Mem abort info:
<1>[385471.820455] ESR = 0x0000000096000045
<1>[385471.824282] EC = 0x25: DABT (current EL), IL = 32 bits
<1>[385471.829685] SET = 0, FnV = 0
<1>[385471.832818] EA = 0, S1PTW = 0
<1>[385471.836037] FSC = 0x05: level 1 translation fault
<1>[385471.841001] Data abort info:
<1>[385471.843960] ISV = 0, ISS = 0x00000045
<1>[385471.847879] CM = 0, WnR = 1
<1>[385471.850925] user pgtable: 4k pages, 39-bit VAs, pgdp=00000000454d8000
<1>[385471.857450] [0000000000000000] pgd=0000000000000000, p4d=0000000000000000, pud=0000000000000000
<0>[385471.866235] Internal error: Oops: 0000000096000045 [#1] SMP
<7>[385471.871885] Modules linked in: pppoe ppp_async wireguard pppox ppp_generic nft_fib_inet nf_flow_table_ipv6 nf_flow_table_ipv4 nf_flow_table_inet mt7915e mt7615e mt7615_common mt76_connac_lib mt76 mac80211 libchacha20poly1305 ipt_REJECT chacha_neon cfg80211 xt_time xt_tcpudp xt_tcpmss xt_statistic xt_state xt_recent xt_nat xt_multiport xt_mark xt_mac xt_limit xt_length xt_hl xt_helper xt_ecn xt_dscp xt_conntrack xt_connmark xt_connlimit xt_connbytes xt_comment xt_TCPMSS xt_REDIRECT xt_MASQUERADE xt_LOG xt_HL xt_DSCP xt_CT xt_CLASSIFY slhc sch_cake poly1305_neon nft_reject_ipv6 nft_reject_ipv4 nft_reject_inet nft_reject_bridge nft_reject nft_redir nft_quota nft_objref nft_numgen nft_nat nft_meta_bridge nft_masq nft_log nft_limit nft_hash nft_fwd_netdev nft_flow_offload nft_fib_ipv6 nft_fib_ipv4 nft_fib nft_dup_netdev nft_ct nft_counter nft_compat nft_chain_nat nf_tables nf_reject_ipv4 nf_log_syslog nf_flow_table nf_dup_netdev nf_conntrack_netlink nf_conntrack_bridge nf_conncount
<7>[385471.872072] libcurve25519_generic libcrc32c libchacha iptable_raw iptable_nat iptable_mangle iptable_filter ipt_ECN ip_tables hwmon crc_ccitt compat act_connmark sch_tbf sch_ingress sch_htb sch_hfsc em_u32 cls_u32 cls_route cls_matchall cls_fw cls_flow cls_basic act_skbedit act_mirred act_gact ledtrig_usbport ledtrig_oneshot xt_set ip_set_list_set ip_set_hash_netportnet ip_set_hash_netport ip_set_hash_netnet ip_set_hash_netiface ip_set_hash_net ip_set_hash_mac ip_set_hash_ipportnet ip_set_hash_ipportip ip_set_hash_ipport ip_set_hash_ipmark ip_set_hash_ipmac ip_set_hash_ip ip_set_bitmap_port ip_set_bitmap_ipmac ip_set_bitmap_ip ip_set nfnetlink ip6table_nat nf_nat nf_conntrack nf_defrag_ipv6 nf_defrag_ipv4 ip6t_NPT ip6table_mangle ip6table_filter ip6_tables ip6t_REJECT x_tables nf_reject_ipv6 ifb ip6_udp_tunnel udp_tunnel nls_utf8 nls_iso8859_1 nls_cp437 seqiv uas usb_storage leds_gpio xhci_plat_hcd xhci_pci xhci_mtk_hcd xhci_hcd ohci_platform ohci_hcd ledtrig_transient
<7>[385471.958789] gpio_button_hotplug vfat fat exfat usbcore usb_common
<7>[385472.050996] CPU: 1 PID: 394 Comm: napi/mtk_eth-4 Not tainted 5.15.137 #0
<7>[385472.057777] Hardware name: Xiaomi Redmi Router AX6S (DT)
<7>[385472.063166] pstate: 80400005 (Nzcv daif +PAN -UAO -TCO -DIT -SSBS BTYPE=--)
<7>[385472.070206] pc : mt76_tx+0xb8/0x634 [mt76]
<7>[385472.074395] lr : mt7915_eeprom_get_power_delta+0x1a08/0x23f0 [mt7915e]
<7>[385472.081008] sp : ffffffc009253400
<7>[385472.084400] x29: ffffffc009253400 x28: ffffff80034c08a0 x27: ffffffc0092535c0
<7>[385472.091618] x26: ffffffc0092535c0 x25: ffffff8003cab328 x24: ffffff80034c0db0
<7>[385472.098835] x23: ffffff8003cab328 x22: ffffffc000f10018 x21: ffffff8003cab300
<7>[385472.106052] x20: ffffff80034c2040 x19: ffffff80034fcce8 x18: 0000000000000000
<7>[385472.113270] x17: 0000000000001e40 x16: ffffff8002962000 x15: 0000000006c00000
<7>[385472.120487] x14: 0000000000000008 x13: 00000003aaaa0000 x12: 0000000000000000
<7>[385472.127705] x11: ffffff80002822b8 x10: 0000000000000014 x9 : 0000000000001f37
<7>[385472.134922] x8 : ffffff80034fcc3a x7 : 0000000055b90d00 x6 : ffffff80093484bc
<7>[385472.142140] x5 : ffffff80034c2040 x4 : 0000000000000000 x3 : 0000000000000001
<7>[385472.149356] x2 : 0000000000000000 x1 : 0000000000000000 x0 : ffffff80034fce28
<7>[385472.156574] Call trace:
<7>[385472.159099] mt76_tx+0xb8/0x634 [mt76]
<7>[385472.162931] mt7915_eeprom_get_power_delta+0x1a08/0x23f0 [mt7915e]
<7>[385472.169195] __ieee80211_schedule_txq+0xf50/0x1830 [mac80211]
<7>[385472.175058] __ieee80211_xmit_fast+0x7b8/0xa90 [mac80211]
<7>[385472.180558] __ieee80211_subif_start_xmit+0x1e8/0x354 [mac80211]
<7>[385472.186666] ieee80211_subif_start_xmit+0x3c/0x3bc [mac80211]
<7>[385472.192514] ieee80211_subif_start_xmit_8023+0x310/0x420 [mac80211]
<7>[385472.198884] dev_hard_start_xmit+0xe4/0x180
<7>[385472.203149] __dev_queue_xmit+0x990/0xc50
<7>[385472.207238] dev_queue_xmit+0x10/0x20
<7>[385472.210978] br_dev_queue_push_xmit+0x9c/0x1b4
<7>[385472.215504] br_forward_finish+0x98/0xb0
<7>[385472.219508] __br_forward+0x138/0x1a0
<7>[385472.223250] br_forward+0x124/0x150
<7>[385472.226819] br_handle_frame_finish+0x310/0x4d4
<7>[385472.231430] br_handle_frame+0x398/0x41c
<7>[385472.235434] __netif_receive_skb_core.constprop.0+0x254/0xca4
<7>[385472.241259] __netif_receive_skb_list_core+0xd4/0x1ec
<7>[385472.246390] netif_receive_skb_list_internal+0x1b4/0x280
<7>[385472.251781] napi_complete_done+0x64/0x1a0
<7>[385472.255955] gro_cell_poll+0x80/0xa0
<7>[385472.259615] __napi_poll+0x54/0x1b0
<7>[385472.263183] net_rx_action+0x2a8/0x330
<7>[385472.267010] _stext+0x10c/0x28c
<7>[385472.270232] do_softirq+0x8c/0xa0
<7>[385472.273631] __local_bh_enable_ip+0xa0/0xa4
<7>[385472.277894] napi_threaded_poll+0x120/0x1a0
<7>[385472.282156] kthread+0x11c/0x130
<7>[385472.285469] ret_from_fork+0x10/0x20
<0>[385472.289128] Code: f90002a0 52800002 f90006a1 f900a675 (f9000035)
<4>[385472.295300] ---[ end trace b13da71c4f07389d ]---
```
</p>
</details>
<details><summary>Linksys E8450 Crashlog</summary>
<p>
```
<1>[66246.289787] Unable to handle kernel write to read-only memory at virtual address 0000000000000000
<1>[66246.298695] Mem abort info:
<1>[66246.301488] ESR = 0x0000000096000045
<1>[66246.305228] EC = 0x25: DABT (current EL), IL = 32 bits
<1>[66246.310556] SET = 0, FnV = 0
<1>[66246.313609] EA = 0, S1PTW = 0
<1>[66246.316742] FSC = 0x05: level 1 translation fault
<1>[66246.321624] Data abort info:
<1>[66246.324499] ISV = 0, ISS = 0x00000045
<1>[66246.328341] CM = 0, WnR = 1
<1>[66246.331305] user pgtable: 4k pages, 39-bit VAs, pgdp=0000000043bae000
<1>[66246.337752] [0000000000000000] pgd=0800000042a59003, p4d=0800000042a59003, pud=0800000042a59003, pmd=0000000000000000
<0>[66246.348377] Internal error: Oops: 0000000096000045 [#1] SMP
<7>[66246.353946] Modules linked in: pppoe ppp_async wireguard pppox ppp_generic nft_fib_inet nf_flow_table_ipv6 nf_flow_table_ipv4 nf_flow_table_inet mt7915e mt7615e mt7615_common mt76_connac_lib mt76 mac80211 libchacha20poly1305 ipt_REJECT chacha_neon cfg80211 xt_time xt_tcpudp xt_tcpmss xt_statistic xt_state xt_recent xt_nat xt_multiport xt_mark xt_mac xt_limit xt_length xt_hl xt_helper xt_ecn xt_dscp xt_conntrack xt_connmark xt_connlimit xt_connbytes xt_comment xt_TCPMSS xt_REDIRECT xt_MASQUERADE xt_LOG xt_HL xt_DSCP xt_CT xt_CLASSIFY slhc sch_cake poly1305_neon nft_reject_ipv6 nft_reject_ipv4 nft_reject_inet nft_reject_bridge nft_reject nft_redir nft_quota nft_objref nft_numgen nft_nat nft_meta_bridge nft_masq nft_log nft_limit nft_hash nft_fwd_netdev nft_flow_offload nft_fib_ipv6 nft_fib_ipv4 nft_fib nft_dup_netdev nft_ct nft_counter nft_compat nft_chain_nat nf_tables nf_reject_ipv4 nf_log_syslog nf_flow_table nf_dup_netdev nf_conntrack_netlink nf_conntrack_bridge nf_conncount
<7>[66246.354139] libcurve25519_generic libcrc32c libchacha iptable_raw iptable_nat iptable_mangle iptable_filter ipt_ECN ip_tables hwmon crc_ccitt compat act_connmark sch_tbf sch_ingress sch_htb sch_hfsc em_u32 cls_u32 cls_route cls_matchall cls_fw cls_flow cls_basic act_skbedit act_mirred act_gact ledtrig_usbport ledtrig_oneshot xt_set ip_set_list_set ip_set_hash_netportnet ip_set_hash_netport ip_set_hash_netnet ip_set_hash_netiface ip_set_hash_net ip_set_hash_mac ip_set_hash_ipportnet ip_set_hash_ipportip ip_set_hash_ipport ip_set_hash_ipmark ip_set_hash_ipmac ip_set_hash_ip ip_set_bitmap_port ip_set_bitmap_ipmac ip_set_bitmap_ip ip_set nfnetlink ip6table_nat nf_nat nf_conntrack nf_defrag_ipv6 nf_defrag_ipv4 ip6t_NPT ip6table_mangle ip6table_filter ip6_tables ip6t_REJECT x_tables nf_reject_ipv6 ifb ip6_udp_tunnel udp_tunnel nls_utf8 nls_iso8859_1 nls_cp437 seqiv uas usb_storage leds_gpio xhci_plat_hcd xhci_pci xhci_mtk_hcd xhci_hcd ohci_platform ohci_hcd ledtrig_transient
<7>[66246.440775] gpio_button_hotplug vfat fat exfat usbcore usb_common
<7>[66246.532817] CPU: 1 PID: 396 Comm: napi/mtk_eth-4 Tainted: G S 5.15.137 #0
<7>[66246.540901] Hardware name: Linksys E8450 (UBI) (DT)
<7>[66246.545769] pstate: 80400005 (Nzcv daif +PAN -UAO -TCO -DIT -SSBS BTYPE=--)
<7>[66246.552724] pc : mt76_tx+0xb8/0x634 [mt76]
<7>[66246.556830] lr : mt7915_eeprom_get_power_delta+0x1a08/0x23f0 [mt7915e]
<7>[66246.563357] sp : ffffffc0093ab400
<7>[66246.566662] x29: ffffffc0093ab400 x28: ffffff80036608a0 x27: ffffffc0093ab5c0
<7>[66246.573795] x26: ffffffc0093ab5c0 x25: ffffff800356df28 x24: ffffff8003660db0
<7>[66246.580926] x23: ffffff800356df28 x22: ffffffc000f2f018 x21: ffffff800356df00
<7>[66246.588057] x20: ffffff8003662040 x19: ffffff8003bf0ce8 x18: 0000000000000001
<7>[66246.595188] x17: 000000000000c360 x16: ffffff8003670000 x15: 0000000006c00000
<7>[66246.602318] x14: ffffffffffffd978 x13: 00000003aaaa0000 x12: 0000000000000000
<7>[66246.609449] x11: ffffff80002f9eb8 x10: 0000000000000014 x9 : 0000000000001f37
<7>[66246.616580] x8 : ffffff8003bf0c3a x7 : 0000000055b90d00 x6 : ffffff80080d76bc
<7>[66246.623710] x5 : ffffff8003662040 x4 : 0000000000000000 x3 : 0000000000000001
<7>[66246.630839] x2 : 0000000000000000 x1 : 0000000000000000 x0 : ffffff8003bf0e28
<7>[66246.637970] Call trace:
<7>[66246.640409] mt76_tx+0xb8/0x634 [mt76]
<7>[66246.644160] mt7915_eeprom_get_power_delta+0x1a08/0x23f0 [mt7915e]
<7>[66246.650338] __ieee80211_schedule_txq+0xf50/0x1830 [mac80211]
<7>[66246.656112] __ieee80211_xmit_fast+0x7b8/0xa90 [mac80211]
<7>[66246.661526] __ieee80211_subif_start_xmit+0x1e8/0x354 [mac80211]
<7>[66246.667548] ieee80211_subif_start_xmit+0x3c/0x3bc [mac80211]
<7>[66246.673309] ieee80211_subif_start_xmit_8023+0x310/0x420 [mac80211]
<7>[66246.679592] dev_hard_start_xmit+0xe4/0x180
<7>[66246.683772] __dev_queue_xmit+0x990/0xc50
<7>[66246.687775] dev_queue_xmit+0x10/0x20
<7>[66246.691429] br_dev_queue_push_xmit+0x9c/0x1b4
<7>[66246.695869] br_forward_finish+0x98/0xb0
<7>[66246.699785] __br_forward+0x138/0x1a0
<7>[66246.703443] br_forward+0x124/0x150
<7>[66246.706926] br_handle_frame_finish+0x310/0x4d4
<7>[66246.711451] br_handle_frame+0x398/0x41c
<7>[66246.715368] __netif_receive_skb_core.constprop.0+0x254/0xca4
<7>[66246.721107] __netif_receive_skb_list_core+0xd4/0x1ec
<7>[66246.726151] netif_receive_skb_list_internal+0x1b4/0x280
<7>[66246.731455] napi_complete_done+0x64/0x1a0
<7>[66246.735544] gro_cell_poll+0x80/0xa0
<7>[66246.739117] __napi_poll+0x54/0x1b0
<7>[66246.742598] net_rx_action+0x2a8/0x330
<7>[66246.746339] _stext+0x10c/0x28c
<7>[66246.749475] do_softirq+0x8c/0xa0
<7>[66246.752787] __local_bh_enable_ip+0xa0/0xa4
<7>[66246.756965] napi_threaded_poll+0x120/0x1a0
<7>[66246.761140] kthread+0x11c/0x130
<7>[66246.764367] ret_from_fork+0x10/0x20
<0>[66246.767940] Code: f90002a0 52800002 f90006a1 f900a675 (f9000035)
<4>[66246.774025] ---[ end trace 10627a923a3b6fdf ]---
```
</p>
</details>
gdb points the address of the crash to ./include/linux/skbuff.h:2021
```
(gdb) l *(mt76_tx+0xb8)
0x7ec8 is in mt76_tx (./include/linux/skbuff.h:2021).
```
``` C
static inline void __skb_insert(struct sk_buff *newsk,
struct sk_buff *prev, struct sk_buff *next,
struct sk_buff_head *list)
{
2019 WRITE_ONCE(newsk->next, next);
2020 WRITE_ONCE(newsk->prev, prev);
2021 WRITE_ONCE(next->prev, newsk);
2022 WRITE_ONCE(prev->next, newsk);
2023 WRITE_ONCE(list->qlen, list->qlen + 1);
}
```
The line that starts a long chain of inlined functions that ends with `__skb_insert` is in tx.c:349
https://github.com/openwrt/mt76/blob/2afc7285f75dca5a0583fd917285bf33f1429cc6/tx.c#L348-L350
The occurrence during FT roaming matches last night and the dates line up. I'll try a new snapshot.