Hello,
By using the OpenWRT VLAN and VPN functionality, I’m trying to associate a VLAN to a VPN network, but I’m missing something. I suspect it should be somewhere in the firewall configuration. I’ve tried so many things that I’m not sure anymore.
Basically I'm trying to configure OpenWRT so that devices from a specific VLAN could access Internet through the VPN tunnel while the devices from the other VLANs could access the internet from the current (normal) access.
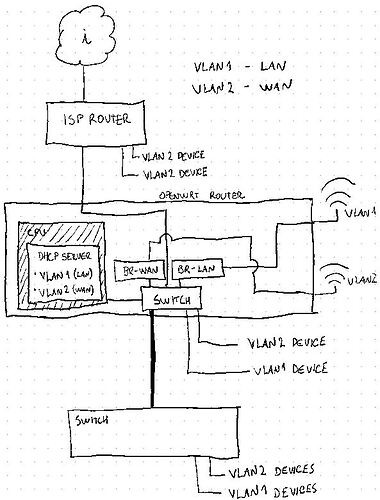
Firstly, my current OpenWRT setup:
I have an ISP router connected to my OpenWRT router. The LAN behind the ISP router is connected to OpenWRT’s WAN port, so I’m calling it “WAN”.
I’m calling “LAN” to the LAN behind the OpenWRT router. VLAN1 is the VLAN for “LAN” and VLAN2 is the VLAN for “WAN”.
Each VLAN is associated to its own WIFI SSID and both receive IPs from OpenWRT DHCP server, depending on the pool configured for each.
Some ports of the OpenWRT router are dedicated to VLAN1 and others are dedicated to VLAN2. Other port is a trunk port (link where VLANs traffic goes tagged), which is connected to a managed switch.
In the switch I have configured some ports to be VLAN1 ports and other ports to be VLAN2 ports.
In other words: If I connect a device to any VLAN1 port (or VLAN1 SSID), it will get an IP from VLAN1 pool and if I connect to any VLAN2 port (of VLAN2 SSID) it will get an IP from the VLAN2 pool.
VLAN1 can access VLAN2 but the opposite isn’t allowed.
This is working happily for some time now. I got it working with the help of @vgaetera in this thread.
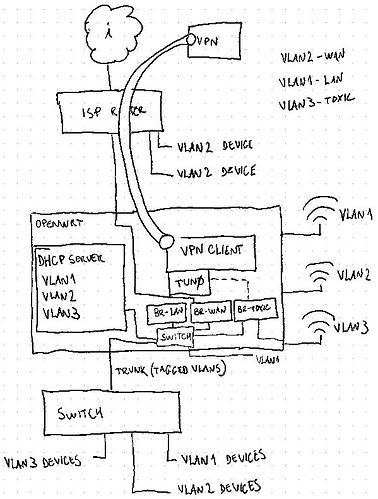
Now, I have configured access to a VPN provider from the OpenWRT router. When connected, the router creates a TUN device and I’m able to get an IP from the VPN provider.
When the VPN is up and running, I’m able to ping servers on the internet from the router, but the devices from VLAN1 and VLAN2 loose internet connectivity (it must be something in the firewall), but that’s kind of fine, because I don’t want all my traffic to go through that tunnel: I’d like to create a 3rd VLAN that is associated to this VPN and only devices from this VLAN will be able to go through the VPN.
So basically, this would be a 3rd VLAN (also with its own dedicated SSID, BTW) where its traffic goes only through the VPN while the VLAN1 and VLAN2 should continue as before. The traffic from the 3rd VLAN shouldn’t reach either VLAN1 or VLAN2 but VLAN2 should be able to reach VLAN3.
What I've done so far:
I’ve created a new bridge and a new interface, dedicated to the new VLAN.
I’ve created a new sub-radio (new SSID) and associated it to the bridge.
I’ve added the DHCP configuration for the new VLAN.
I’ve created a new FW zone.
I’ve added a rule where the traffic from the new VLAN should reach OpenWRT “device”, so dhcpd could assign IPs to this VLAN as well.
What is the current behaviour:
If I connect a WIFI device to the new SSID, it will get an IP from the correct pool. However, it will not have access to the internet, even if the VPN is up (must be something missing in the firewall, but don't know exactly what).
If I connect a wired device to a port that is associated to the 3rd VLAN, I can’t get nothing. Even if I manually assign an IP from the correct network, it will not ping the OpenWRT router. I’ve reviewed the switch configuration several times, so I’m not sure it would be a switch issue or OpenWRT misconfiguration.
Soooo... Any brave expert would be able to point me in the right direction? 
Router details:
Linksys EA8500 WiFi Router
ARMv7 Processor rev 0 (v7l)
OpenWrt 19.07.3 r11063-85e04e9f46 / LuCI openwrt-19.07 branch git-20.136.49537-fb2f363
4.14.180
Bridge config:
root@mojito:/etc/config# brctl show
bridge name bridge id STP enabled interfaces
br-lan 7fff.58ef6858cf9d no eth0.1
wlan0
br-toxic 7fff.58ef6858cfab no eth0
wlan0-2
br-wan 7fff.58ef6858cfaa no eth0.2
wlan0-1
root@mojito:/etc/config#
Network Config:
root@mojito:/etc/config# cat network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'xxxx:xxxx:xxxx::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.2.1'
option igmp_snooping '1'
config device 'lan_dev'
option name 'eth0.1'
option macaddr '58:ef:68:58:xx:xx'
config interface 'wan'
option ifname 'eth0.2'
option proto 'static'
option netmask '255.255.255.0'
option type 'bridge'
option igmp_snooping '1'
option ipaddr '192.168.9.2'
option gateway '192.168.9.1'
list dns '8.8.8.8'
list dns '192.168.9.1'
config device 'wan_dev'
option name 'eth0.2'
option macaddr '58:ef:68:58:xx:xx'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
option auto '0'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 1t 2t'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '2'
option ports '0t 1t 2t 3 4 5'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '99'
option ports '0 1t'
config interface 'toxic'
option proto 'static'
option netmask '255.255.255.0'
option type 'bridge'
option igmp_snooping '1'
option ipaddr '192.168.99.1'
list dns '8.8.8.8'
list dns '192.168.99.1'
option ifname 'eth0'
config device 'toxic_dev'
option name 'eth0.99'
option macaddr '58:ef:68:58:xx:xb'
config interface 'tun1'
option proto 'none'
Firewall Config:
root@mojito:/etc/config# cat firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone 'lan'
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list device 'tun0'
list device 'tun+'
option network 'lan'
config zone 'wan'
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config forwarding 'lan_wan'
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option dest_port '22'
option src 'wan'
option name 'Allow SSH'
option target 'ACCEPT'
option family 'ipv4'
list proto 'tcp'
list dest_ip '192.168.9.2'
config rule
option dest_port '67'
option src 'wan'
option name 'DHCP-Server'
option family 'ipv4'
option target 'ACCEPT'
list proto 'udp'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config rule 'ovpn'
option name 'Allow-OpenVPN'
option src 'wan'
option dest_port '1194'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'toxic'
option mtu_fix '1'
option input 'REJECT'
option forward 'REJECT'
option masq '1'
option output 'ACCEPT'
option network 'toxic tun1'
config forwarding
option dest 'toxic'
option src 'lan'
config forwarding
option dest 'toxic'
option src 'wan'
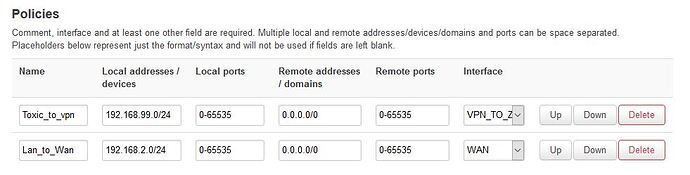
config rule
option target 'ACCEPT'
option src 'toxic'
option name 'toxic access'
config zone
option name 'VPN_TOXIC'
option input 'REJECT'
option network 'toxic'
option output 'ACCEPT'
option masq '1'
option forward 'REJECT'
(I also have openVPN server installed on the router so I can establish VPNs towards my home LAN.)
DHCP config:
root@mojito:/etc/config# cat dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option localservice '1'
option noresolv '1'
option doh_backup_noresolv '-1'
list doh_backup_server '8.8.8.8'
list doh_backup_server '192.168.9.1'
option logqueries '1'
list server '127.0.0.1#5054'
list server '127.0.0.1#5053'
config dhcp 'lan'
option interface 'lan'
option leasetime '12h'
option force '1'
option start '120'
option limit '20'
config dhcp 'wan'
option interface 'wan'
option leasetime '12h'
option force '1'
option start '120'
list dhcp_option '3, 192.168.9.1'
list dhcp_option '6, 192.168.9.1'
option limit '20'
config dhcp 'toxic'
option interface 'toxic'
option leasetime '12h'
option force '1'
option start '120'
list dhcp_option '3, 192.168.99.1'
list dhcp_option '6, 192.168.99.1'
option limit '20'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'