Not entirely sure what "associate" means here.
Not entirely sure what "using IPv4" means here.
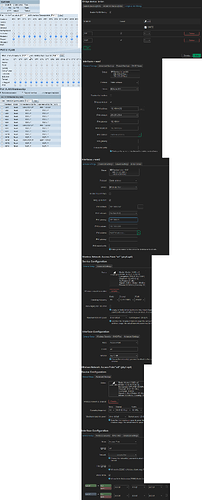
If you want to create Tagged VLANs on an interface, go to:
Network → Interfaces → [Devices] → "br-lan": Configure...
→ [Bridge VLAN filtering]
and hit the Add button twice, give them IDs and mark them T on the port.
Next, you can go to
Network → Interfaces → [Interfaces]
Hit the "Add new interface..." button and you can configure an IP address, gateway and create a firewall zone fx. "wan1".
Repeat to make an IP interface on the other tagged vlan.
If you want to bridge a wifi network with a vlan, go to:
Network → Wireless → "wlan1": Edit
→ "Interface Configuration" → [General Setup]
In the "Network" drop-down, just select the interface you just created.
(Repeat for the other wlan.)
Alternatively, if you want to route a wifi network to a different subnet, that happens to live on a vlan, and you are fresh out of ethernet ports in the router to associate the wifi network with, go to:
Network → Interfaces → [Devices]
Hit the "Add device configuration", select device type "Bridge", and leave the bridge ports empty, just name it "br-wifi1" or something.
Then, you can go to Network → Interfaces → [Interfaces]
Hit the "Add new interface..." button and configure an internal IP address for the wifi network, and setup a DHCP server, and create a "lan1" firewall zone.
Next, go the the wireless network and select the freshly created interface in the "Network" dropdown.
Finally, go to Network → Firewall, under "Zones" find the "lan1" zone you just created, edit it, choose "accept" for input/output/forward, click the "masquerade" checkbox, and select "wan1" under "allow forward to destination zones".
Note: If you go with a routed setup, or rather 2x routed setups in one box, you will need a bit more than this to make sure that each wifi network is routed to their correct gateway etc. OpenWRT per default has just one internal router configured. But it comes with various facilities you can use to ensure correct routing, such as fwmark, ipv4 rules, kmod-vrf etc.
![]()