yes just want them as option for install later
Thank you again
@eganov I think I added that source right. Here's the image https://drive.google.com/drive/folders/1KZFzp82FH0Rp-9BygH_0EmxeG-AdC9u4?usp=sharing
Thank you very much
I would post the result soon
I have tried the bin
everything looks good Thank you.
at some point I can't save the config change Via Luci and at Interface packet traffic inticator TX/RX become 0 , but reboot the router fix the issue, I can't replicate the error.
The OpenVPN speed is not what I have expected, got only 50 -60 Mbps (DL) on 260 Mbps line.
edit
after apply
echo 35 > /sys/devices/system/cpu/cpufreq/ondemand/up_threshold
echo 10 > /sys/devices/system/cpu/cpufreq/ondemand/sampling_down_factor
the speed increase to 75-85Mbps (DL)
question for you if this build you already include NSS drivers
like mention at Askey RAC2V1K / RT4230W REV6 Support
who know it could get better performance on VPN,
Thank you again
NSS not work
I tried to get it working but I couldn't get it to compile correctly. I'll take another shot at it soon.
I am doing openssl test, but have strange result where the test with -evp came lower or insignificant increase at some blocks
root@OpenWrt_Askey:/# openssl speed -evp aes-128-cbc -elapsed
You have chosen to measure elapsed time instead of user CPU time.
Doing aes-128-cbc for 3s on 16 size blocks: 9160604 aes-128-cbc's in 3.00s
Doing aes-128-cbc for 3s on 64 size blocks: 3003726 aes-128-cbc's in 3.00s
Doing aes-128-cbc for 3s on 256 size blocks: 825778 aes-128-cbc's in 3.00s
Doing aes-128-cbc for 3s on 1024 size blocks: 211126 aes-128-cbc's in 3.00s
Doing aes-128-cbc for 3s on 8192 size blocks: 26430 aes-128-cbc's in 3.00s
Doing aes-128-cbc for 3s on 16384 size blocks: 13267 aes-128-cbc's in 3.01s
OpenSSL 1.1.1g 21 Apr 2020
built on: Tue Jun 30 04:21:08 2020 UTC
options:bn(64,32) rc4(char) des(long) aes(partial) blowfish(ptr)
compiler: arm-openwrt-linux-muslgnueabi-gcc -fPIC -pthread -Wa,--noexecstack
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes 16384 bytes
aes-128-cbc 48856.55k 64079.49k 70466.39k 72064.34k 72171.52k 72214.79k
root@OpenWrt_Askey:/# openssl speed aes-128-cbc
Doing aes-128 cbc for 3s on 16 size blocks: 10289168 aes-128 cbc's in 2.99s
Doing aes-128 cbc for 3s on 64 size blocks: 2864147 aes-128 cbc's in 3.00s
Doing aes-128 cbc for 3s on 256 size blocks: 743459 aes-128 cbc's in 3.00s
Doing aes-128 cbc for 3s on 1024 size blocks: 187694 aes-128 cbc's in 3.00s
Doing aes-128 cbc for 3s on 8192 size blocks: 23481 aes-128 cbc's in 3.00s
Doing aes-128 cbc for 3s on 16384 size blocks: 11743 aes-128 cbc's in 3.00s
OpenSSL 1.1.1g 21 Apr 2020
built on: Tue Jun 30 04:21:08 2020 UTC
options:bn(64,32) rc4(char) des(long) aes(partial) blowfish(ptr)
compiler: arm-openwrt-linux-muslgnueabi-gcc -fPIC -pthread -Wa,--noexecstack
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes 16384 bytes
aes-128 cbc 55059.09k 61101.80k 63441.83k 64066.22k 64118.78k 64132.44k
root@OpenWrt_Askey:/#
I compare the test with NanoPi R2S (RK3328) from
Where the openssl test with -evp the performance result is way higher than w/o -evp
I also tested with atomic pi ( Intel Atom x5- Z8350), result below
BusyBox v1.31.1 () built-in shell (ash)
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
-----------------------------------------------------
Atomic-Pi SNAPSHOT, r13245-78bebe680f
-----------------------------------------------------
root@OpenWrt:~# openssl speed -evp aes-128-cbc -elapsed
You have chosen to measure elapsed time instead of user CPU time.
Doing aes-128-cbc for 3s on 16 size blocks: 21984147 aes-128-cbc's in 3.00s
Doing aes-128-cbc for 3s on 64 size blocks: 9518017 aes-128-cbc's in 3.00s
Doing aes-128-cbc for 3s on 256 size blocks: 3060657 aes-128-cbc's in 3.00s
Doing aes-128-cbc for 3s on 1024 size blocks: 824183 aes-128-cbc's in 3.00s
Doing aes-128-cbc for 3s on 8192 size blocks: 105300 aes-128-cbc's in 3.00s
Doing aes-128-cbc for 3s on 16384 size blocks: 52729 aes-128-cbc's in 3.00s
OpenSSL 1.1.1g 21 Apr 2020
built on: Sat May 16 02:37:55 2020 UTC
options:bn(64,64) rc4(16x,int) des(int) aes(partial) blowfish(ptr)
compiler: x86_64-openwrt-linux-musl-gcc -fPIC -pthread -m64 -Wa,--noexecstack
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes 16384 bytes
aes-128-cbc 117248.78k 203051.03k 261176.06k 281321.13k 287539.20k 287970.65k
root@OpenWrt:~# openssl speed aes-128-cbc
Doing aes-128 cbc for 3s on 16 size blocks: 8842149 aes-128 cbc's in 3.00s
Doing aes-128 cbc for 3s on 64 size blocks: 2464777 aes-128 cbc's in 3.00s
Doing aes-128 cbc for 3s on 256 size blocks: 638758 aes-128 cbc's in 3.00s
Doing aes-128 cbc for 3s on 1024 size blocks: 161500 aes-128 cbc's in 3.00s
Doing aes-128 cbc for 3s on 8192 size blocks: 20257 aes-128 cbc's in 3.00s
Doing aes-128 cbc for 3s on 16384 size blocks: 10112 aes-128 cbc's in 3.00s
OpenSSL 1.1.1g 21 Apr 2020
built on: Sat May 16 02:37:55 2020 UTC
options:bn(64,64) rc4(16x,int) des(int) aes(partial) blowfish(ptr)
compiler: x86_64-openwrt-linux-musl-gcc -fPIC -pthread -m64 -Wa,--noexecstack
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes 16384 bytes
aes-128 cbc 47158.13k 52581.91k 54507.35k 55125.33k 55315.11k 55225.00k
root@OpenWrt:~#
Surprisingly the test result w/o evp (hardware crypto) IPQ8065 is the higher than Intel Z8350 or RK3328
Just wondering if the kernel if QCE driver is included (?) it could be better outcome,
found from google but don't have idea whether it is related.
https://patchwork.ozlabs.org/project/openwrt/patch/20190920204804.10183-1-cotequeiroz@gmail.com/
and I am expecting that NSS driver also will have an impact on boosting performance for openssl
Please use the "Preformatted text </>" button for logs, scripts, configs and general console output.
![]()
Please edit your post accordingly. Thank you! 
ipq806x does not have the QCE crypto engine. It has the NSS crypto engine.
It performed a lot worst. You can refer to the results I posted here:
Could be the driver not optimised, but at the moment, I have no clue how to improve the performance further. Hopefully I can find a solution in future.
Ouch, Fixed it , sorry
Thanks, can you explain how to apply multi-segment it seems with a software-based crypto engine, your result better than mine
I am switching to Wireguard now, heard that hardware Crypto is not necessary
The multi-segment approach in my post is meant for the NSS crypto drivers. It doesn't apply to OpenSSL per se.
For the better performance from my results, it's most likely due to the OPTIMIZE_FOR_SPEED option in my OpenWrt build. You can turn it on using 'make menuconfig'.
I think this script also helps:
Of course you can force the Krait CPU to it's max clock speed to get the best results.
As for WireGuard, yeah, I switched all my site-to-site VPN to wireguard now. It allows for better latency and thruput as it resides in kernel, so the performance will be much better compared to OpenVPN. Too bad WireGuard only support L3 tunnels. I still rely on OpenVPN when I need a L2 tunnel.
HTH.
I was just delivered this device and it is a miserable castrated thing. I just finished reading this thread beginning to end. Amazing work.
@lmore377 Can I repost your guide?
can you share here your Router info (Factory ID) close to USB and AC adapter port (picture if possible) . I am learning that several version of this router 256MiB / 512MiB Nand
related to Factory ID
Thanks
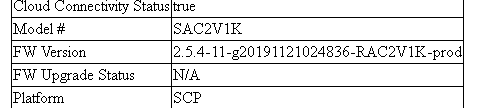
Strange, the Box says RAC2V1K and the status page says SAC2V1K
Refurb?
You picture kind of blurry There is wording Factory ID just right on top USB , if I am guessing you have ID:3
I have same thing but by original firmware RAC you might have the same unit with @lmore377
if you need to flash here the link for saving your time.to set the partition
@lmore377 if you have spare time, can we try to include this?
someone has a better result there
Thanks
@efsg sure, just credit my GitHub or something
@frustro don't flash openwrt onto a device being rented from an ISP. There's no way to go back to stock on these routers because trying to restore the stock firmware just breaks /overlay which makes it enter a boot loop. Also the routers that have sac2v1k are identical to rac2v1k except for the fact that they have a smaller flash since the sac routers have simpler firmware(mainly no web interface for changing settings and a lot less packages)
@eganov I've been busy with stuff but I'll look into it soon